In this walk through, we will be going through the Cross Site Scripting vulnerability section from Webgoat Labs. We will be exploring and exploiting Cross Site Scripting in various application implementation and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
1. Using Chrome or Firefox to see cookies

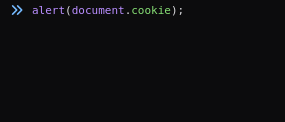
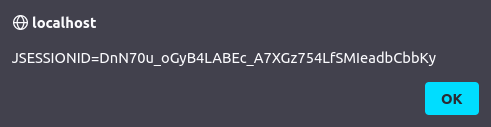
2. Reflected XSS
- In this challenge we have to identify which field is susceptible to XSS.
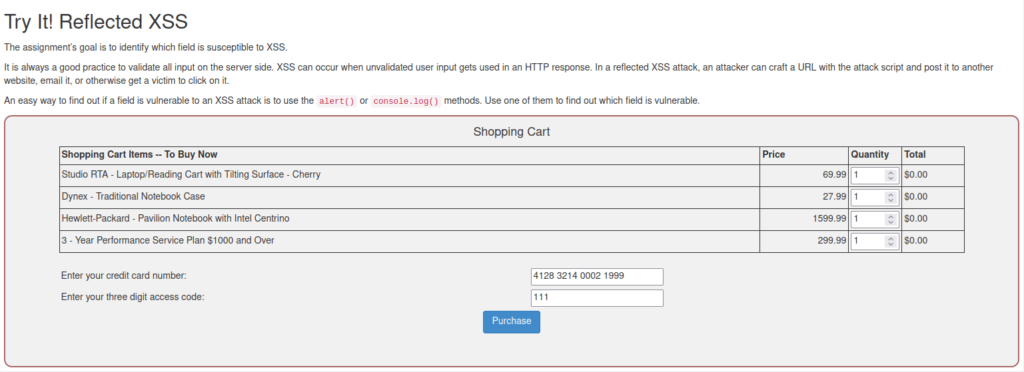
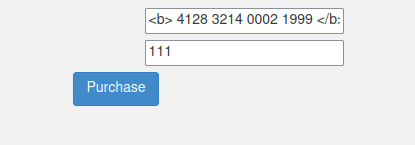
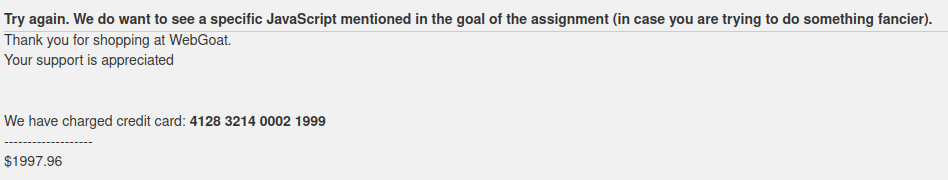
- I used the below HTML bold tag to test if the application is parsing our HTML input or not and it does.
<b> 4128 3214 0002 1999 </b>
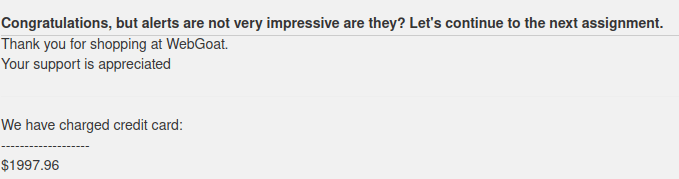
- I used the below payload to pop an alert box and completed the challenge.
<script>alert("Hacked")</script>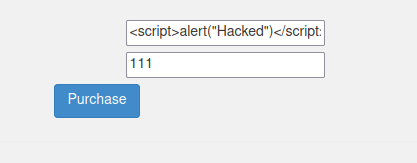

3. Identify potential for DOM-Based XSS
- In this challenge we have to find the base route of the test code that stayed in the app during production.
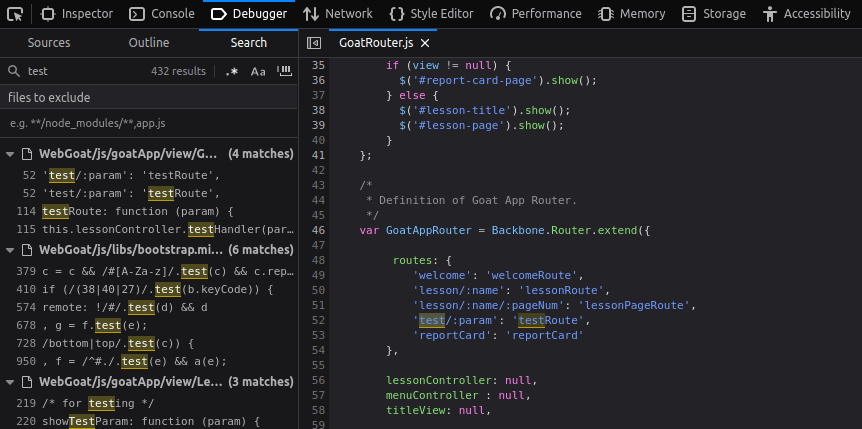
- I opened up the Debugger in dev tools and search for test. Got a parameter test.
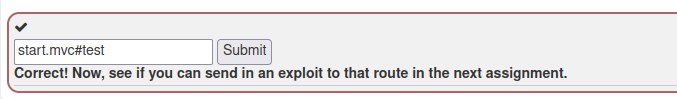
start.mvc#test
4. DOM-Based XSS
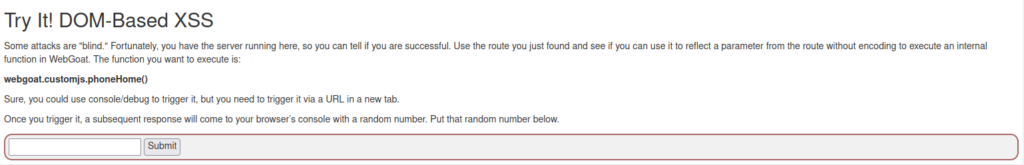
- As we know from the previous challenge we have our base route parameter at.
http://localhost/WebGoat/start.mvc#test/parameter
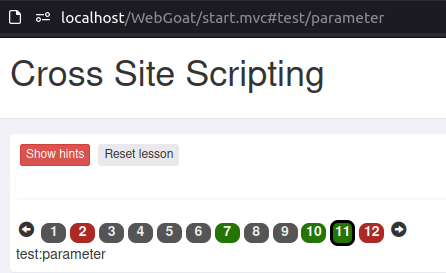
- I used the below payload in place of our parameter value and analyzes the response in Console.
http://localhost/WebGoat/start.mvc#test/<script>webgoat.customjs.phoneHome()</script> %3Cscript%3Ewebgoat%2Ecustomjs%2EphoneHome%28%29%3C%2Fscript%3E%0A
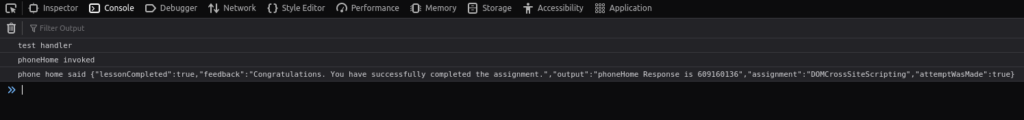
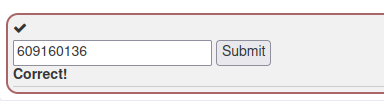
5. The Quiz
Also Read: Webgoat – Authentication Bypasses
Conclusion:

So, we finally completed the Webgoat Cross Site Scripting Vulnerability section. Next, we can mitigate these types of attacks by performing input sanitization on endpoints, whitelist the allowed characters in the input and using a WAF. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




