In this walk through, we will be going through the Vulnerable Components vulnerability section from Webgoat Labs. We will be exploring and exploiting Vulnerable Components and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
1. The exploit is not always in “your” code
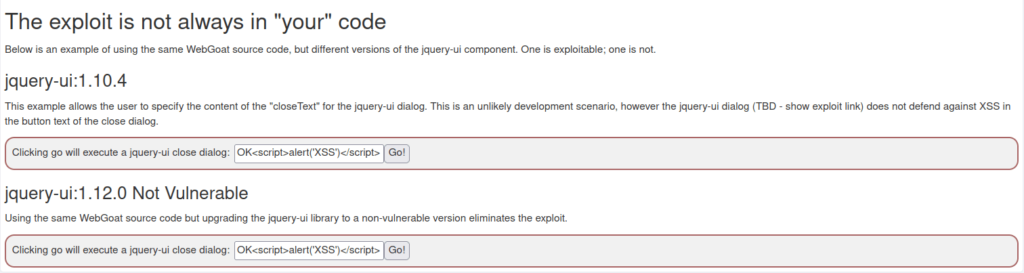
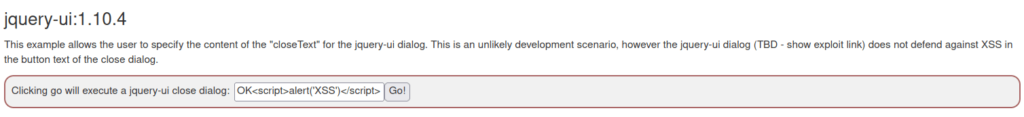

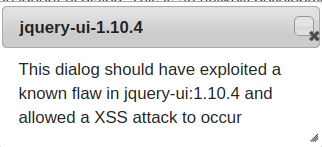
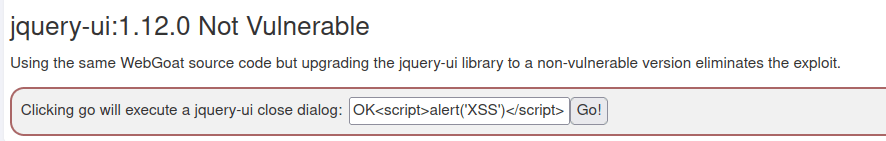
Also Read: Webgoat – SQL Injection (Advanced)
Conclusion:

So, we finally completed the Webgoat Vulnerable Components Vulnerability section. Next, we can mitigate these types of attacks by implementing automated alert and patching tools to ensure a secure software development lifecycle (SDLC) process and give our dev teams a snapshot of potential flaws. Along with that, we must keep a comprehensive inventory of all components used in the application to ensure only approved elements are in place. It also involves continuously reviewing and updating the list. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




