In this walk through, we will be going through the HTML Injection Stored (Blog) vulnerability section from bWAPP Labs. We will be exploring and exploiting Stored HTML Injection vulnerability in Blog implementations and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to low.
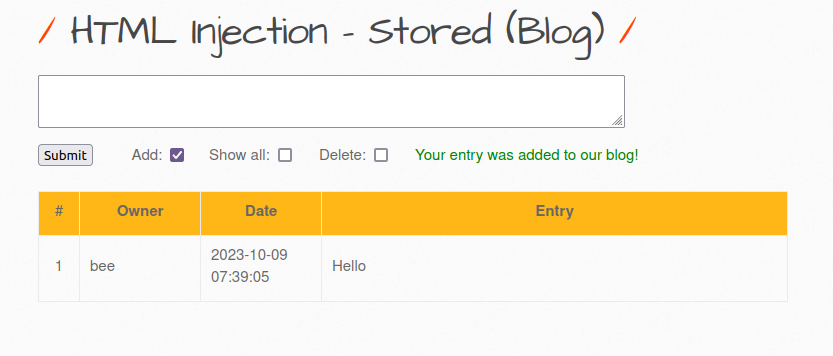
- The application uses a typical blog comment or entry system which is used to submit data/entry to the application database by the users. It uses the post method for the request and has options of show all, adding an entry and deleting an entry.
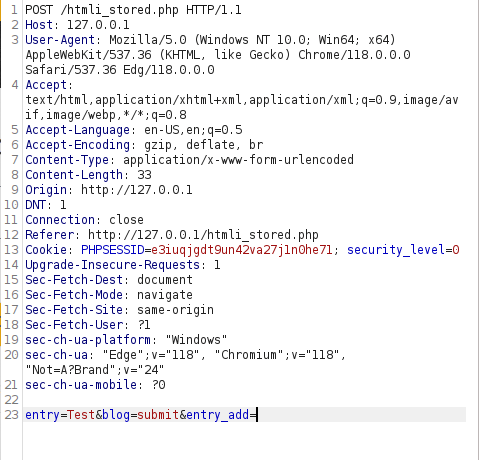
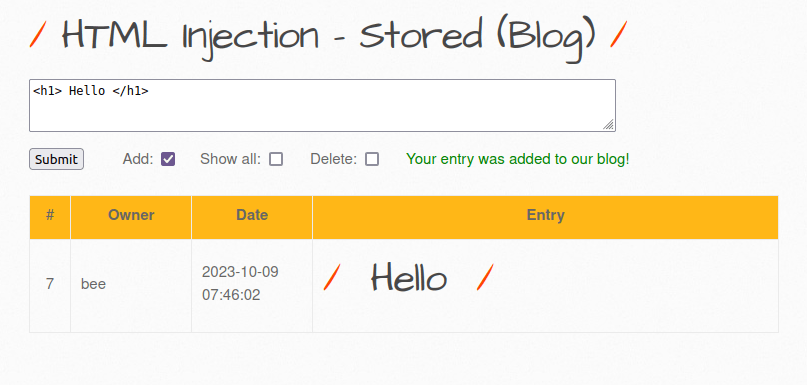
- Let’s see if the application is vulnerable to stored HTML Injection. I used the HTML heading tag for my entry and wallah! it stores my data as a heading that means the application had parsed my input and stored it in database instead of considering it as a string which makes it vulnerable.
- Now, let’s exploit the application by using the below payload. The payload will be stored in the application database and whenever any user visited the comment section, a pop-up will be generated with string “Hacked”
<img src = "x" onerror=alert("Hacked");>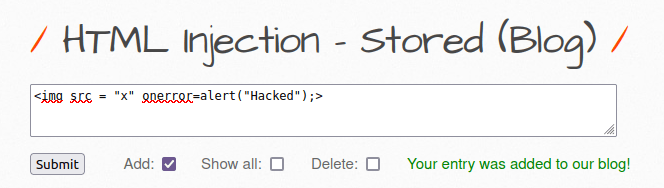

Security: Medium
- Setting the security level to Medium.
- Let’s test if application is still parsing our HTML tags with our entries. The result shows that the application is now sanitizing the input and is not parsing our HTML data.
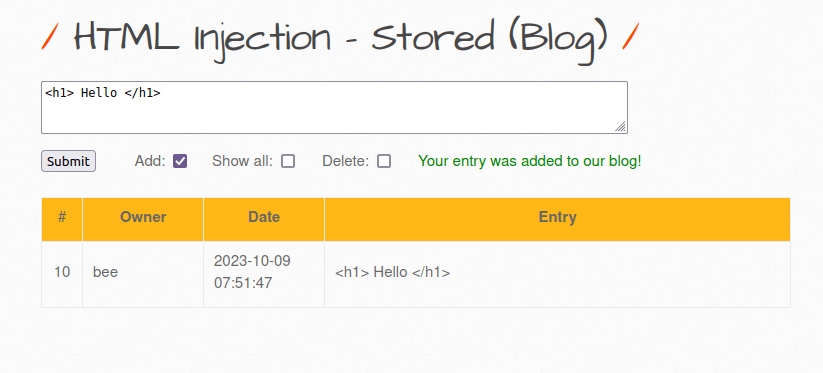
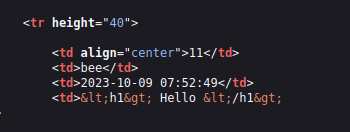
- I checked the page source code of the application and checked our recently made entry. As we can see the application is using HTML entities to replace our HTML tags and sanitize our input. This is a mistake from the developer’s end on this as i have researched online so there is no way we can proceed with the stage however we can manually make changes the htmli_stored.php file then we will be able to complete the stage but that’s not the point then.
Also Read: bWAPP – HTML Injection (Reflected-URL)
Conclusion:
So, we finally completed all the security levels for the bWAPP HTML Injection Stored (Blog) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Stored HTML Injection attacks can be mitigated by performing input sanitization on endpoints, whitelist the allowed characters in the input and using a WAF. Along with that, we can prevent data from any untrusted source to be dynamically written to the HTML document. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.