In this walk through, we will be going through the HTML5 Web Storage (Secret) vulnerability section from bWAPP Labs. We will be exploring and exploiting HTML5 Web Storage and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
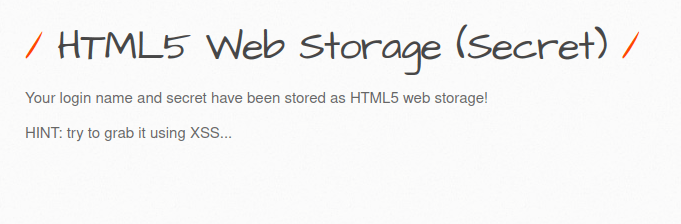
- In this challenge we have to grab the secret of our user which has been stored in the HTML5 Web storage using XSS.
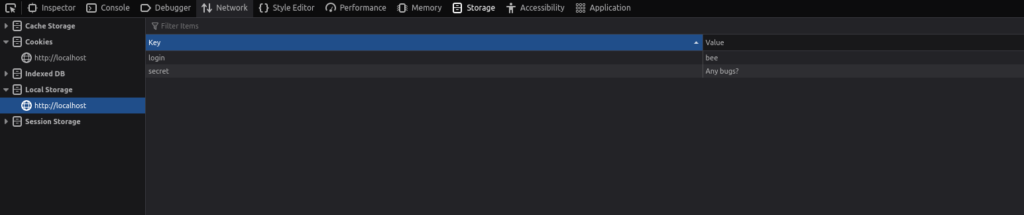
- As we know the web storage data is stored in Dev Tool -> Storage -> Local Storage.
- I used the below payload in Dev tools console to pop up an alert with our secret value.
alert(localStorage.getItem("secret"));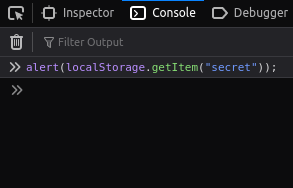

Security: Medium
- Setting the security level to Medium.
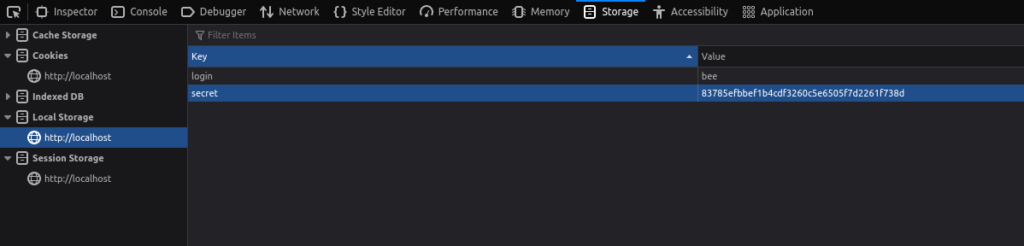
- As we can see this time the value of secret is encrypted.
- I used the below payload again to pop up an alert with our secret value.
alert(localStorage.getItem("secret"));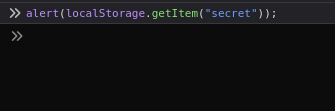
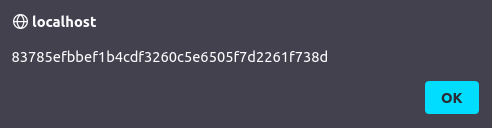
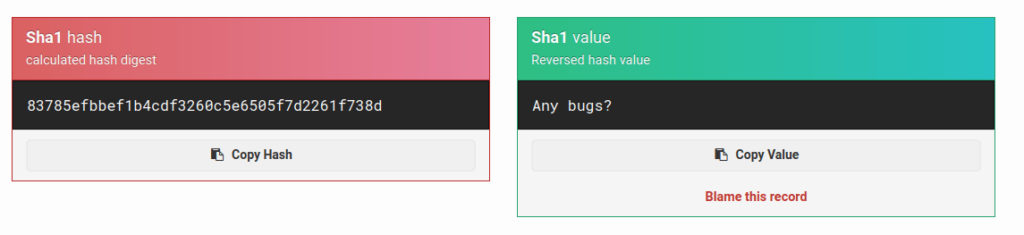
- I decrypted the SHA1 hash and found our secret value.
- Worked same in high level like in medium.
Also Read: bWAPP – HTML Injection (Reflected-GET)
Conclusion:

So, we finally completed all the security levels for the bWAPP HTML5 Web Storage (Secret) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. HTML5 Web Storage attacks can be mitigated by not allowing data from any untrusted source to be placed in HTML5 storage. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




