In this walk through, we will be going through the Algernon room from Proving Grounds. This room is rated as Easy on the platform and it consists of SmarterMail RCE to get root. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Algernon |
| IPaddress | 192.168.166.65 |
| Difficulty | Easy |
| OS | Windows |
| Description | Algernon is an Easy rated Windows machine that leverages SmarterMail RCE exploit to get admin shell on the target. |
Enumeration:
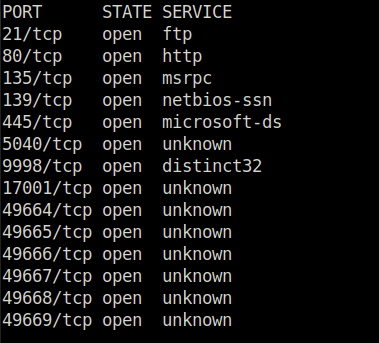
- I started my enumeration with my regular aggressive nmap scan and found a couple of ports opened – 21 (FTP), 80 (HTTP), 139,445 (SMB) and 9998 (HTTP).
$ sudo nmap -A 192.168.166.65 Starting Nmap 7.80 ( https://nmap.org ) at 2024-02-10 16:17 IST Nmap scan report for 192.168.166.65 Host is up (0.27s latency). Not shown: 992 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd 53/tcp filtered domain 80/tcp open http Microsoft IIS httpd 10.0 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 |_http-title: IIS Windows 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds? 1721/tcp filtered caicci 9998/tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 | http-title: Site doesn't have a title (text/html; charset=utf-8). |_Requested resource was /interface/root No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.80%E=4%D=2/10%OT=21%CT=1%CU=30762%PV=Y%DS=4%DC=T%G=Y%TM=65C754A OS:3%P=x86_64-pc-linux-gnu)SEQ(SP=FF%GCD=1%ISR=10E%TS=U)OPS(O1=M54ENW8NNS%O OS:2=M54ENW8NNS%O3=M54ENW8%O4=M54ENW8NNS%O5=M54ENW8NNS%O6=M54ENNS)WIN(W1=FF OS:FF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M5 OS:4ENW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4 OS:(R=N)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T7(R=N)U1(R=Y% OS:DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=9CB8%RUD=G)IE(R=N) Network Distance: 4 hops Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2024-02-10T10:48:57 |_ start_date: N/A TRACEROUTE (using port 1025/tcp) HOP RTT ADDRESS 1 250.35 ms 192.168.45.1 2 250.34 ms 192.168.45.254 3 252.29 ms 192.168.251.1 4 252.35 ms 192.168.166.65 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 123.81 seconds

- Also performed a full TCP ports scan to reveal any ports that was left in the previous scan.
sudo nmap -sS -p- -T5 192.168.166.65
- Next, i moved to FTP to perform my enumeration with anonymous access. Found a bunch of directories but got nothing in them.
$ ftp 192.168.166.65 Connected to 192.168.166.65. 220 Microsoft FTP Service Name (192.168.166.65:wh1terose): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> dir 200 PORT command successful. 150 Opening ASCII mode data connection. 04-29-20 09:31PM <DIR> ImapRetrieval 02-10-24 02:45AM <DIR> Logs 04-29-20 09:31PM <DIR> PopRetrieval 04-29-20 09:32PM <DIR> Spool 226 Transfer complete. ftp> cd ImapRetrieval 250 CWD command successful. ftp> ls 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete. ftp> ls -l 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete. ftp> cd .. 250 CWD command successful. ftp> cd Logs 250 CWD command successful. ftp> ls 200 PORT command successful. 125 Data connection already open; Transfer starting. 04-29-20 10:26PM 582 2020.04.29-delivery.log 04-29-20 10:15PM 0 2020.04.29-profiler.log -- snipped -- 02-10-24 02:46AM 112 2024.02.10-delivery.log 226 Transfer complete. ftp> cd .. 250 CWD command successful. ftp> cd PopRetrieval 250 CWD command successful. ftp> ls 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete. ftp> cd .. 250 CWD command successful. ftp> cd Spool 250 CWD command successful. ftp> ls 200 PORT command successful. 125 Data connection already open; Transfer starting. 04-29-20 09:32PM <DIR> Drop 226 Transfer complete. ftp> cd Drop 250 CWD command successful. ftp> ls 200 PORT command successful. 125 Data connection already open; Transfer starting. 226 Transfer complete. ftp> exit 221 Goodbye.


- Moved to the HTTP next on port 80, found a generic IIS web page. Nothing fancy!
- Fired gobuster on the target to reveal any hidden directories with extension flag set to apsx. Found nothing here as well.
gobuster dir -u http://192.168.166.65/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt -x aspx

- Moving on, performed SMB enumeration but got dead end here as well.
smbclient -L 192.168.166.65 smbmap -H 192.168.166.65

- Finally, moved to the web server on port 9998 and got a login page there. It login screen has a Welcome banner of SmarterMail. Interesting!

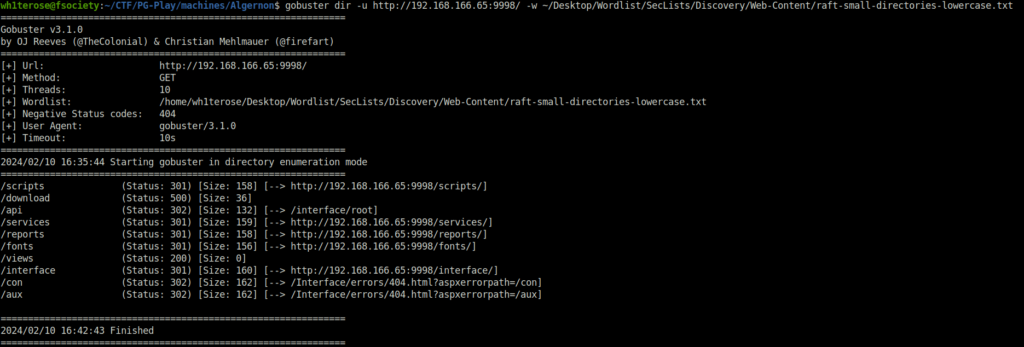
- Fired gobuster on the target server but found nothing juicy.
$ gobuster dir -u http://192.168.166.65:9998/ -w ~/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.166.65:9998/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/SecLists/Discovery/Web-Content/raft-small-directories-lowercase.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2024/02/10 16:35:44 Starting gobuster in directory enumeration mode
===============================================================
/scripts (Status: 301) [Size: 158] [--> http://192.168.166.65:9998/scripts/]
/download (Status: 500) [Size: 36]
/api (Status: 302) [Size: 132] [--> /interface/root]
/services (Status: 301) [Size: 159] [--> http://192.168.166.65:9998/services/]
/reports (Status: 301) [Size: 158] [--> http://192.168.166.65:9998/reports/]
/fonts (Status: 301) [Size: 156] [--> http://192.168.166.65:9998/fonts/]
/views (Status: 200) [Size: 0]
/interface (Status: 301) [Size: 160] [--> http://192.168.166.65:9998/interface/]
/con (Status: 302) [Size: 162] [--> /Interface/errors/404.html?aspxerrorpath=/con]
/aux (Status: 302) [Size: 162] [--> /Interface/errors/404.html?aspxerrorpath=/aux]
===============================================================
2024/02/10 16:42:43 Finished
===============================================================
Exploitation & Getting root:
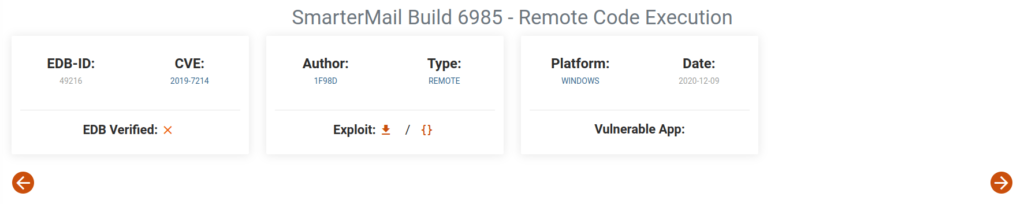
- Searched for any known exploits for SmarterMail and found one that leads to RCE. As per the exploit, it targets the SmarterMail service on port 17001.
Exploit – https://www.exploit-db.com/exploits/49216
- Changed the required information in the exploit code and fired it on the target which grants us shell access as administrator.

python3 49216.py


- Finally, captured the root flag and completed the machine.

Also Read: HTB – UpDown
Conclusion:

So that was “Algernon” for you. We started off with a regular nmap scan and found a port running on 9998. Enumerated the web server running on the same, found a SmarterMail installation. Looked online for any known exploits of the running version and found a RCE one. Finally, used it to get root on the target. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




