In this walkthrough, we will be going through History of Malware room by Tryhackme. This room covers the malwares that were developed back in the time and how they have been transformed in the modern world now. It covers the first worm, virus and Trojans and how they were developed. So, let’s get started.

Task 1 – Introduction

Task 2 – The Creeper Program
Question 1 – Read the above.
Done
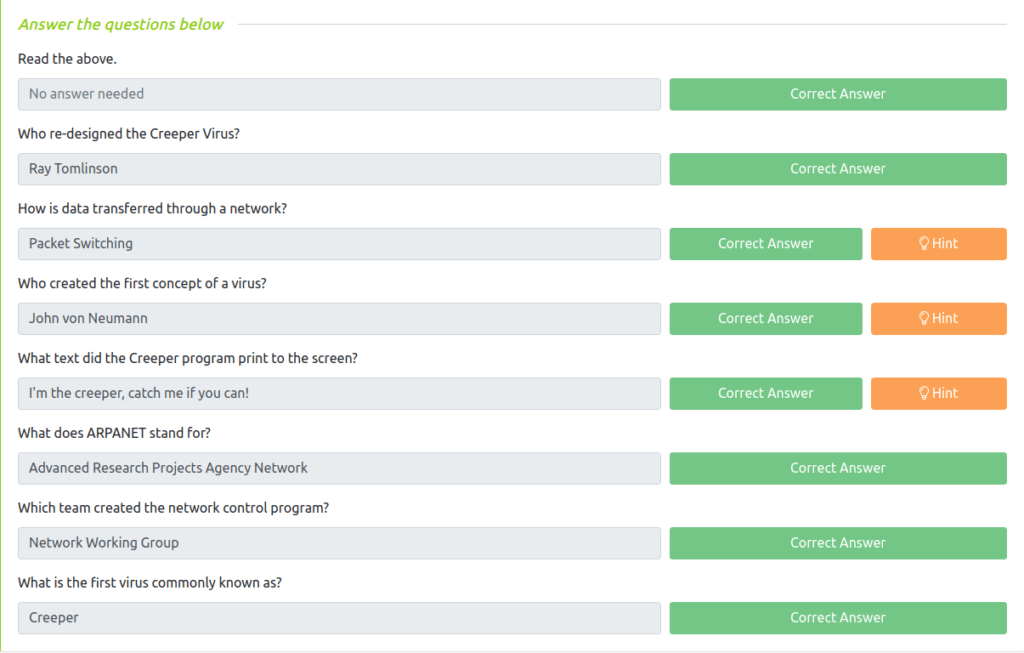
Question 2 – Who re-designed the Creeper Virus?
Ray Tomlinson
Question 3 – How is data transferred through a network?
Packet Switching
Question 4 – Who created the first concept of a virus?
John von Neumann
Question 5 – What text did the Creeper program print to the screen?
I'm the creeper, catch me if you can!
Question 6 – What does ARPANET stand for?
Advanced Research Projects Agency Network
Question 7 – Which team created the network control program?
Network Working Group
Question 8 – What is the first virus commonly known as?
Creeper
Task 3 – Reaper
Question 1 – Read the above.
Done
Question 2 – Who created Reaper?
Ray Tomlinson
Question 3 – What type of malware may Reaper be known as?
nematode
Question 4 – What was the first ever anti-virus program known as?
Reaper
Question 5 – What was Bob Thomas’ main project to develop?
a resource-sharing capability
Question 6 – Research: What does API stand for?
Application Programming Interface

Task 4 – Wabbit
Question 1 – Read the information.
Done
Question 2 – What is a modern day fork bomb also known as?
denial of service attack
Question 3 – Was Rabbit one of the first malicious programs? (Y/N)
Y
Question 4 – What did the name “Wabbit” derive from?
looney tunes cartoons

Task 5 – ANIMAL
Question 1 – Read the above.
Done
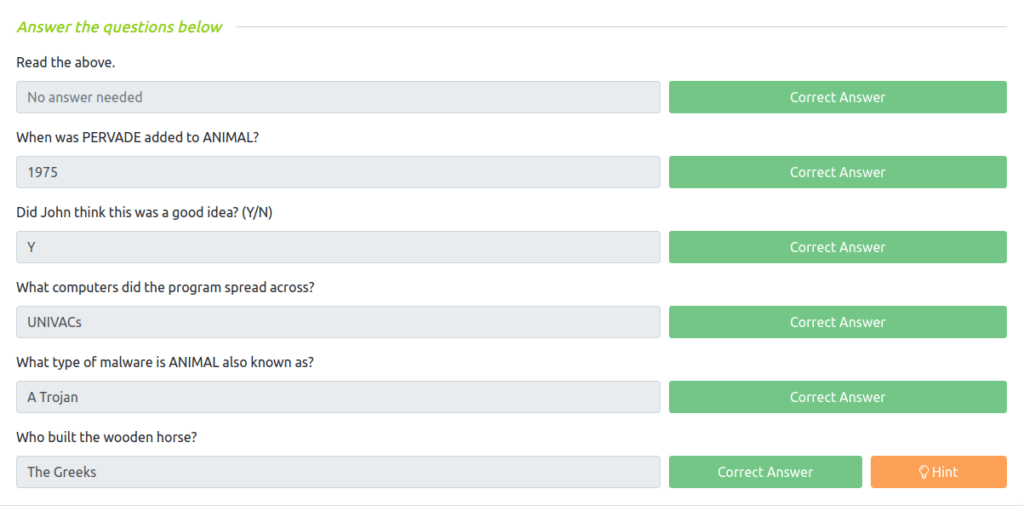
Question 2 – When was PERVADE added to ANIMAL?
1975
Question 3 – Did John think this was a good idea? (Y/N)
Y
Question 4 – What computers did the program spread across?
UNIVACs
Question 5 – What type of malware is ANIMAL also known as?
A Trojan
Question 6 – Who built the wooden horse?
The Greeks
Task 6 – Elk Cloner
Question 1 – Read the above.
Done
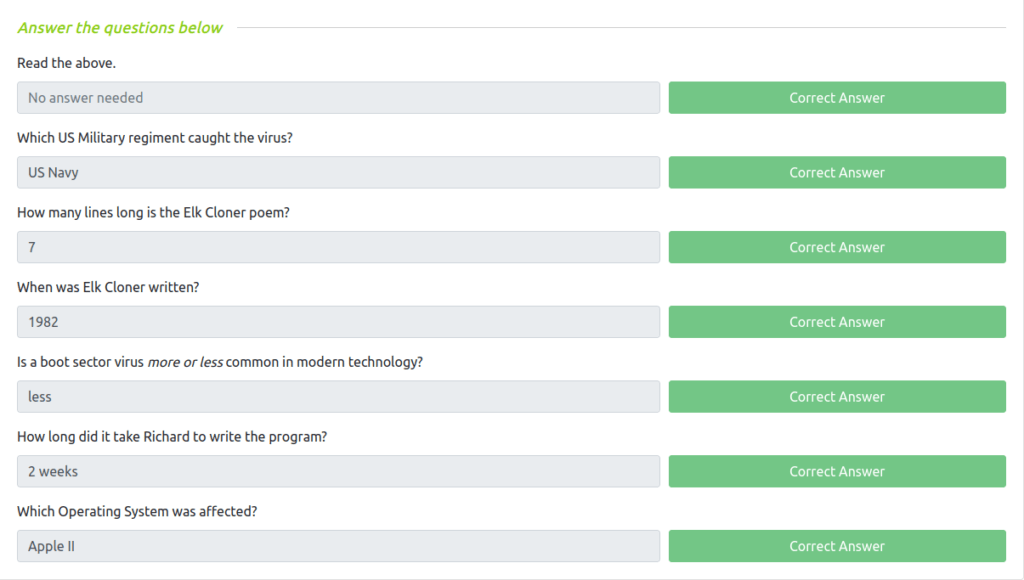
Question 2 – Which US Military regiment caught the virus?
US Navy
Question 3 – How many lines long is the Elk Cloner poem?
7
Question 4 – When was Elk Cloner written?
1982
Question 5 – Is a boot sector virus more or less common in modern technology?
less
Question 6 – How long did it take Richard to write the program?
2 weeks
Question 7 – Which Operating System was affected?
Apple II
Task 7 – The Morris Internet Worm
Question 1 – Read the above.
Done
Question 2 – What commands were a very big way that allowed Morris to access the computers?
Berkeley r-commands
Question 3 – Who was one the first person prosecuted for the computer misuse act?
Robert Tappan Morris
Question 4 – What type of attack is a “Fork Bomb”?
Denial of Service
Question 5 – When was this worm released?
1988
Question 6 – How many computers did it infect within 15 hours?
2000
Question 7 – What does rsh mean?
Remote Shell
Question 8 – Under which act was Morris arrested for?
1986 Computer Fraud and Abuse act

Task 8 – Cascade
Question 1 – Read the above.
Done
Question 2 – What was the name of this virus?
Cascade
Question 3 – What file extensions would this virus infect?
.COM
Question 4 – How many variants of there virus were possibly found?
40
Question 5 – What operating system would the virus run on?
DOS
Question 6 – Which Operating System/Frame Work would Cascade try to avoid?
IBM
Question 7 – How many bytes would be added onto your file if it got infected?
1704

Task 9 – Thanks for reading!

Also Read: Tryhackme – MAL (Malware Introductory)
Conclusion:
That concludes our room based on History of Malware. We looked into the different types of malware and how they evolve. Ranging from harmless worms to stealthy Trojans, we have covered it all. On that note, i will take off from here and will meet you in the next write-up, till then “Hack the Planet”.