In this walk through, we will be going through the Burp suite Repeater room from Tryhackme. This room will dive into one of the more powerful aspects of the framework, namely: the Burp Suite Repeater module. So without any delay, let’s get started.

Task 1 – Outline
Task 2 – What is Repeater?
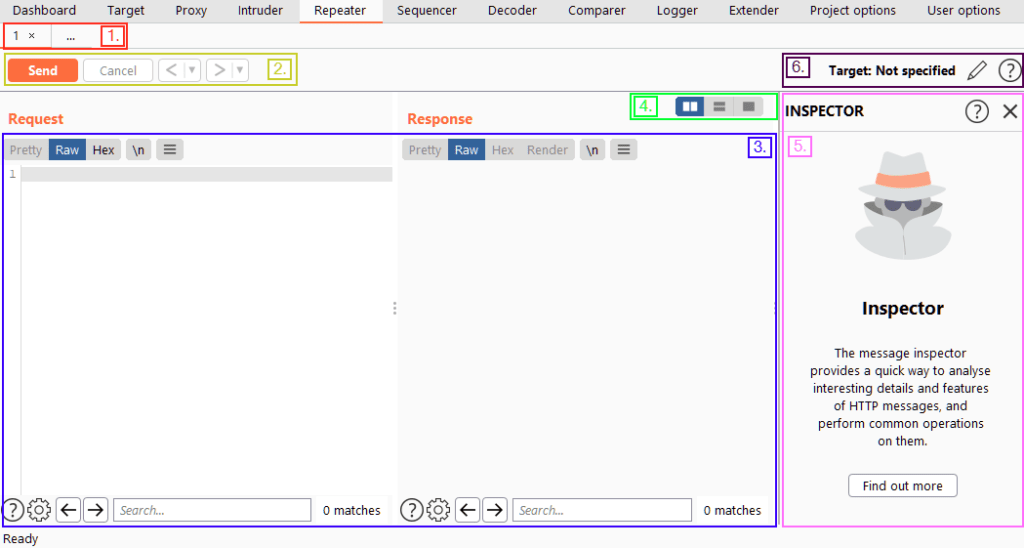
Question 1 – Familiarise yourself with the Repeater interface.
Done
Task 3 – Basic Usage
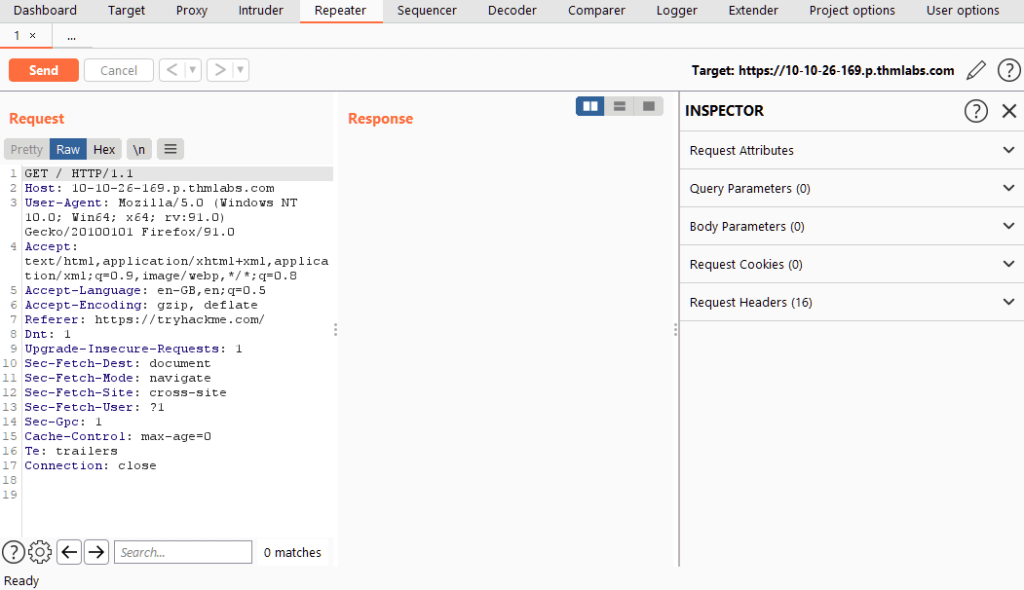
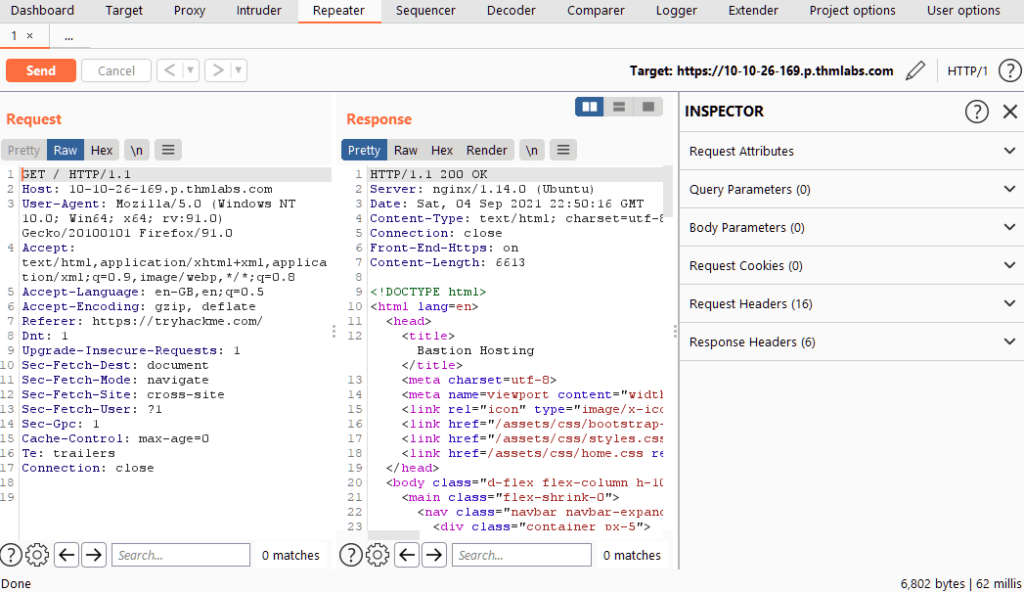
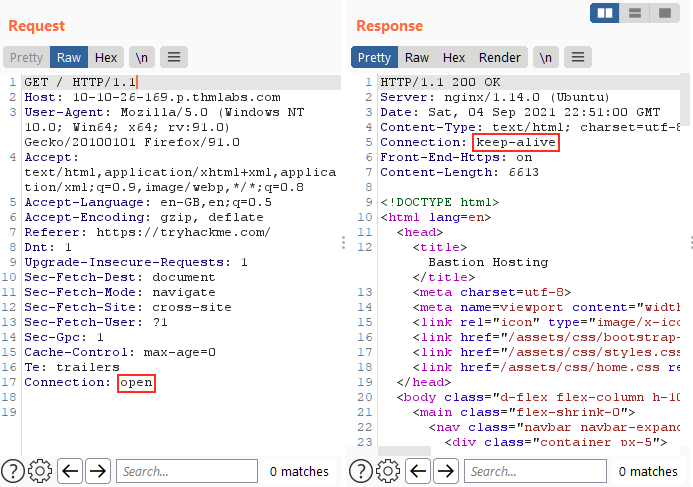
Question 1 – Capture a request to http://10.10.2.107 in the Proxy and send it to Repeater.
Done
Task 4 – Views
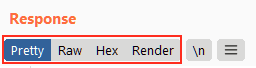
Question 1 – Experiment with the available view options.
Done
Question 2 – Which view option displays the response in the same format as your browser would?
Render
Task 5 – Inspector
Question 1 – Get comfortable with Inspector and practice adding/removing items from the various request sections.
Done
Task 6 – Example
Question 1 – Capture a request to http://10.10.2.107/ in the Proxy and send it to Repeater.
Done
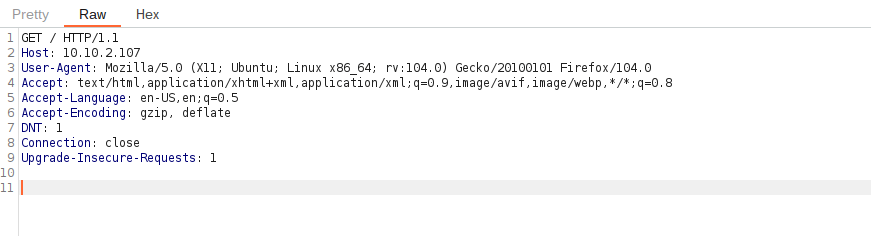
Question 2 – Send the request once from Repeater — you should see the HTML source code for the page you requested in the response tab.
Done
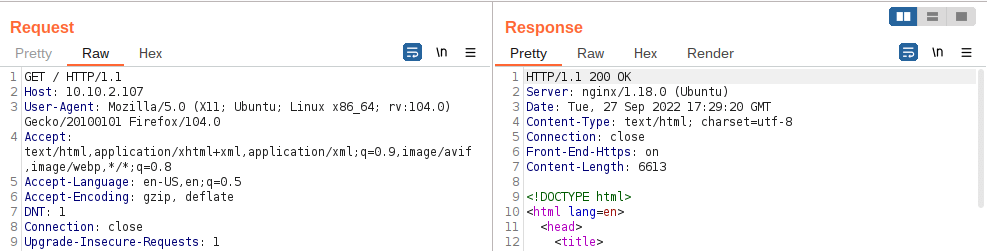
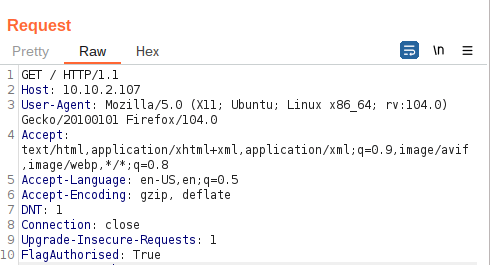
Using Inspector (or manually, if you prefer), add a header called FlagAuthorised and set it to have a value of True. Send the request. What is the flag you receive?
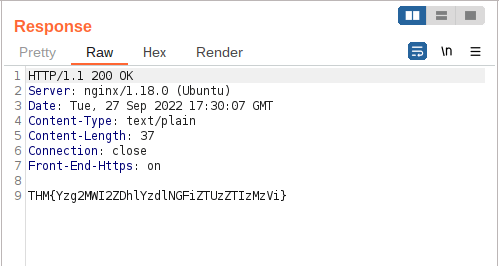
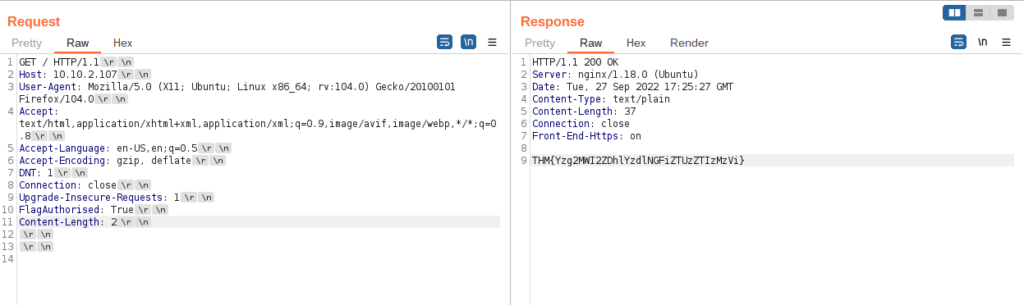
THM{Yzg2MWI2ZDhlYzdlNGFiZTUzZTIzMzVi}
Task 7 – Challenge
Question 1 – Capture a request to one of the numeric products endpoints in the Proxy, then forward it to Repeater.
Done
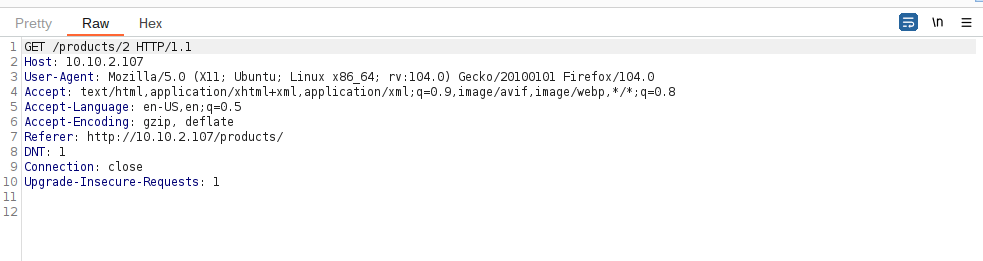
Question 2 – See if you can get the server to error out with a “500 Internal Server Error” code by changing the number at the end of the request to extreme inputs. What is the flag you receive when you cause a 500 error in the endpoint?
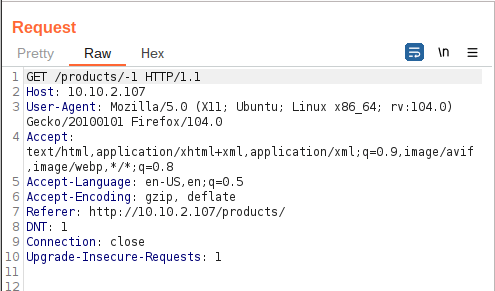
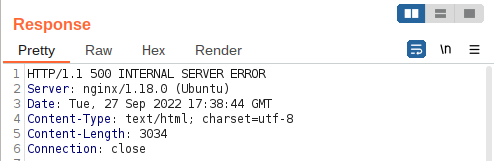
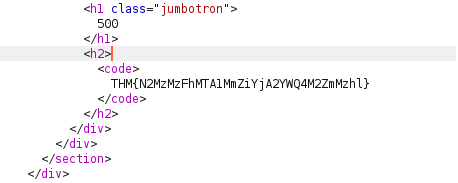
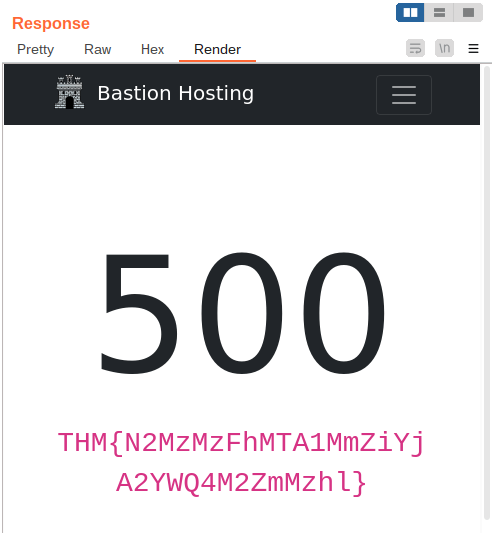
THM{N2MzMzFhMTA1MmZiYjA2YWQ4M2ZmMzhl}
Task 8 – SQLi with Repeater
Question 1 – Let’s start by capturing a request to http://10.10.2.107/about/2 in the Burp Proxy. Once you have captured the request, send it to Repeater with Ctrl + R or by right-clicking and choosing “Send to Repeater”.
Done
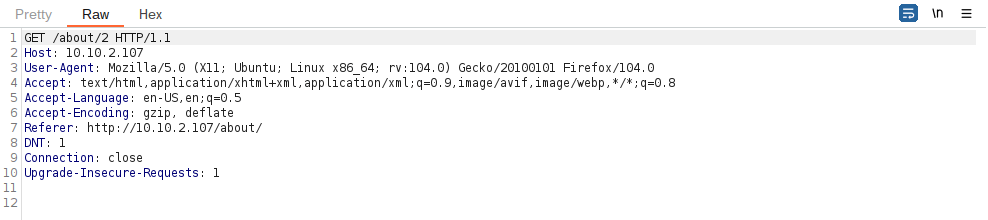
Question 2 – What is the flag?
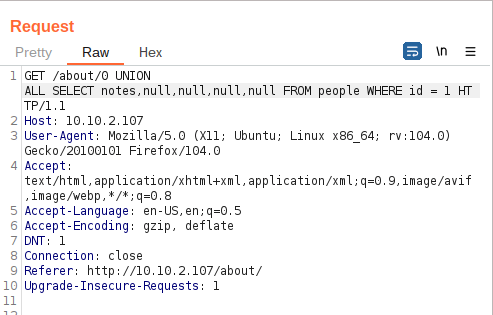
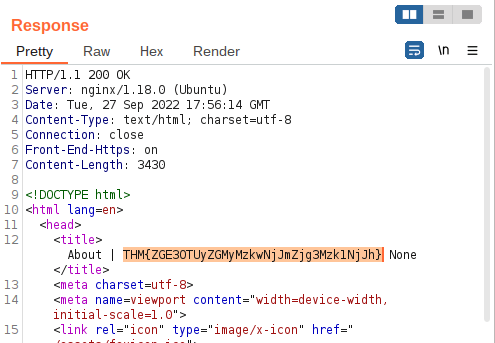
THM{ZGE3OTUyZGMyMzkwNjJmZjg3Mzk1NjJh}
Task 9 – Conclusion
Also Read: Tryhackme – Brute It
Conclusion:

So that was it. The room took us through us the journey of the most used Burpsuite module – Repeater. We understand how to capture and forward request using Repeater. Further we used repeater to manipulate the request and performed SQL injection attack on the target to get some flags. On that note, i will take off for a nap but remember to “Keep hacking”.




