In this walk through, we will be going through the CTF collection Vol.1 room from Tryhackme. This room has 20 tasks which test your basic CTF skills from decoding common encoding schemes to OSINT, this covers it all. So, let’s get started.

Task 1 – Author note
Task 2 – What does the base said?
Question 1 – Can you decode the following?
VEhNe2p1NTdfZDNjMGQzXzdoM19iNDUzfQ==
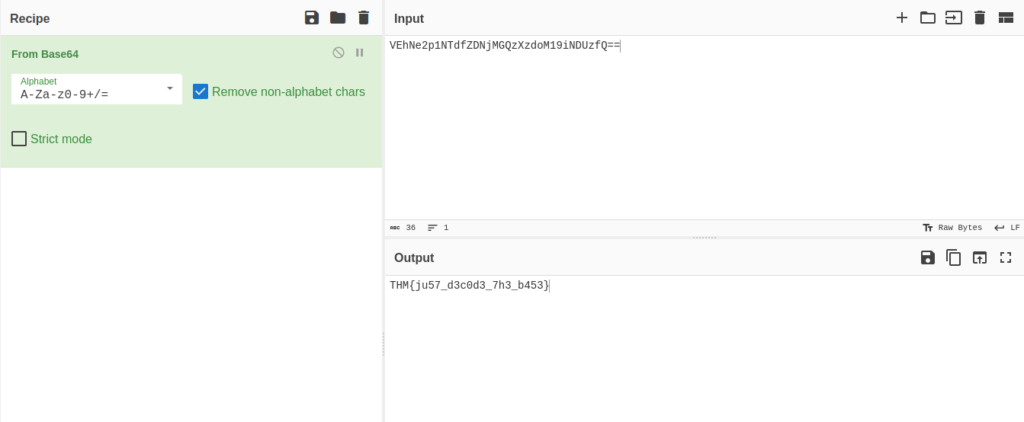
THM{ju57_d3c0d3_7h3_b453}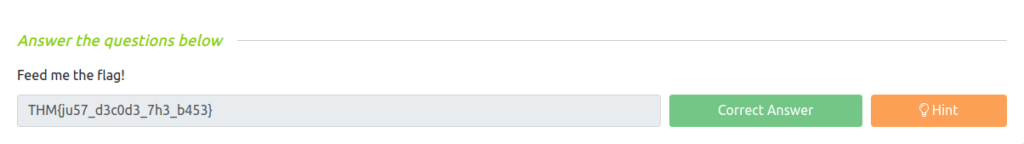
Task 3 – Meta meta
Question 1 – I’m hungry, I need the flag.
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ exiftool Findme.jpg
ExifTool Version Number : 11.88
File Name : Findme.jpg
Directory : .
File Size : 34 kB
File Modification Date/Time : 2023:04:26 22:22:32+05:30
File Access Date/Time : 2023:04:26 22:22:32+05:30
File Inode Change Date/Time : 2023:04:26 22:23:58+05:30
File Permissions : rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
X Resolution : 96
Y Resolution : 96
Exif Byte Order : Big-endian (Motorola, MM)
Resolution Unit : inches
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
Flashpix Version : 0100
Owner Name : THM{3x1f_0r_3x17}
Comment : CREATOR: gd-jpeg v1.0 (using IJG JPEG v62), quality = 60.
Image Width : 800
Image Height : 480
Encoding Process : Progressive DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 800x480
Megapixels : 0.384
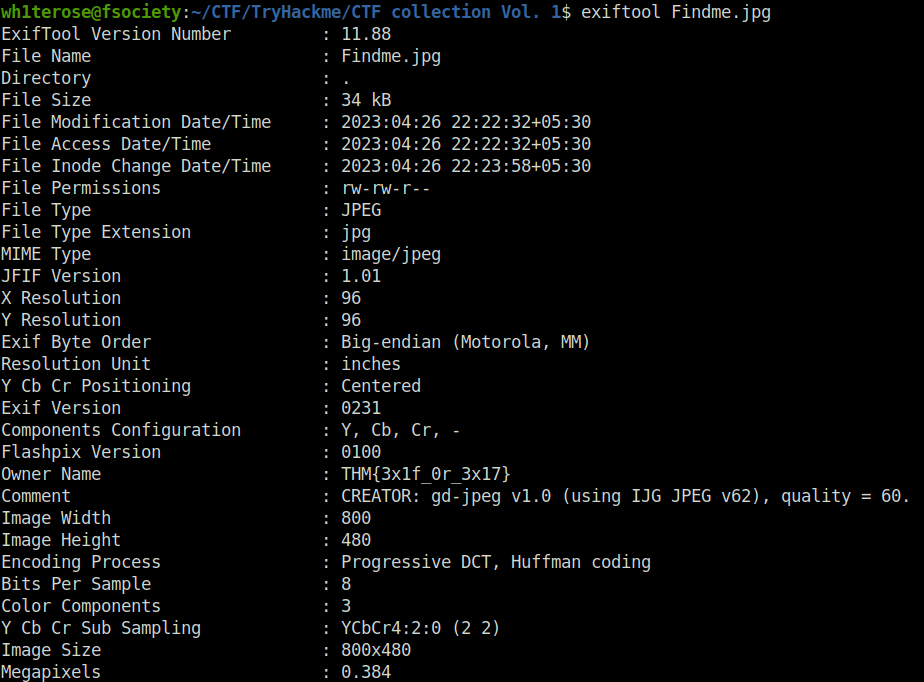
THM{3x1f_0r_3x17}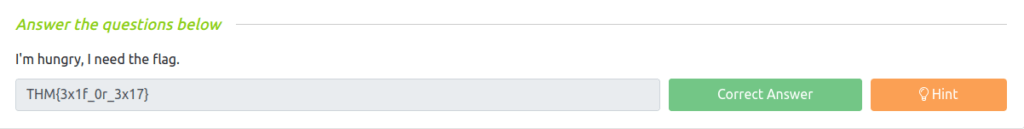
Task 4 – Mon, are we going to be okay?
Question 1 – It is sad. Feed me the flag.
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ steghide --extract -sf Extinction.jpg
Enter passphrase:
wrote extracted data to "Final_message.txt".
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ cat Final_message.txt
It going to be over soon. Sleep my child.
THM{500n3r_0r_l473r_17_15_0ur_7urn}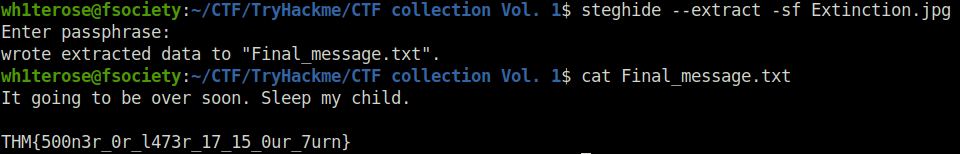
THM{500n3r_0r_l473r_17_15_0ur_7urn}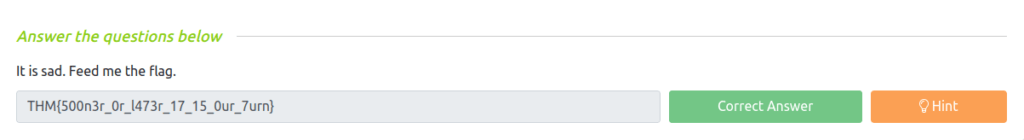
Task 5 – Erm……Magick
Question 1 – Did you find the flag?
THM{wh173_fl46}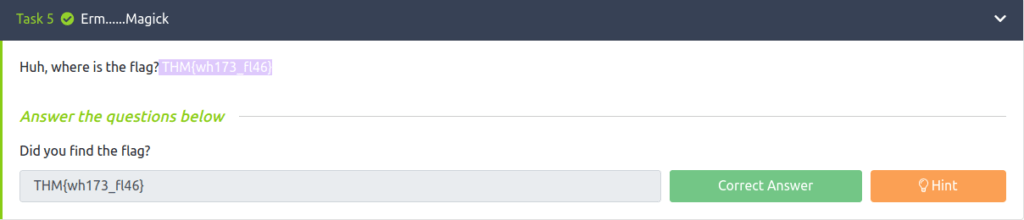
Task 6 – QRrrrr
Question 1 – More flag please!
- Use the following website to get the flag by uploading the QR code image into it – https://qreader.online/
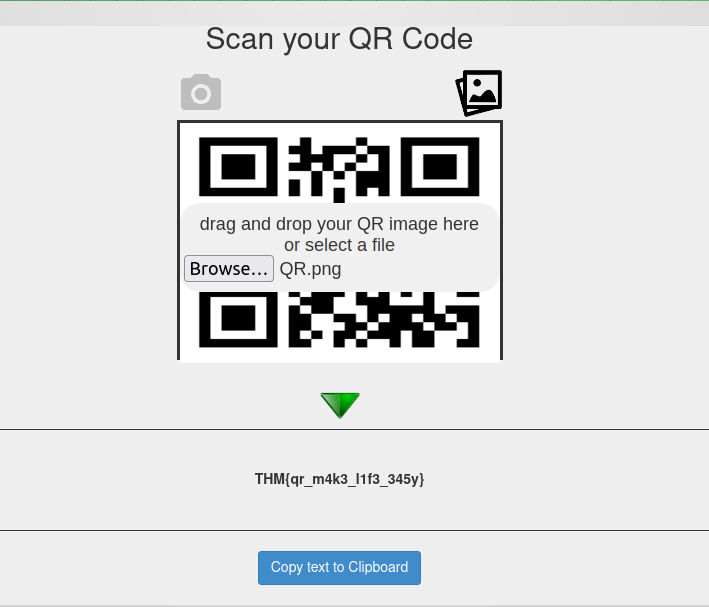
THM{qr_m4k3_l1f3_345y}
Task 7 – Reverse it or read it?
Question 1 – Found the flag?
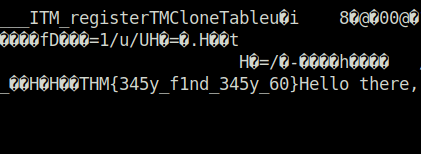
THM{345y_f1nd_345y_60}
Task 8 – Another decoding stuff
3agrSy1CewF9v8ukcSkPSYm3oKUoByUpKG4L
Question 1 – Oh, Oh, Did you get it?
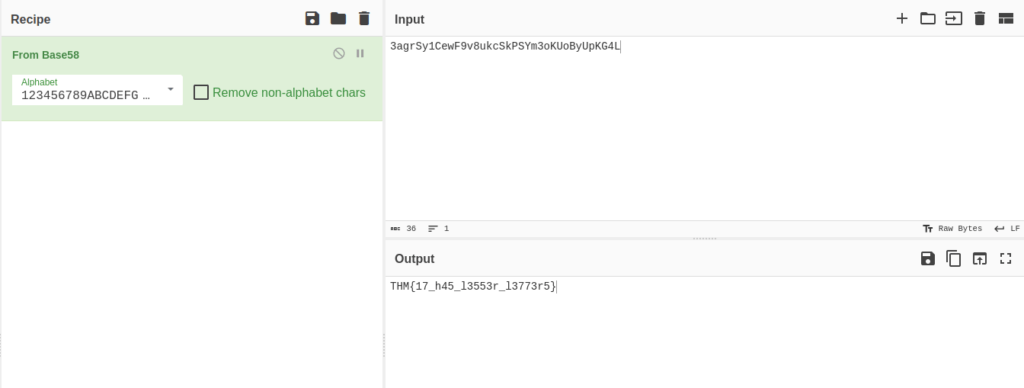
THM{17_h45_l3553r_l3773r5}
Task 9 – Left or right
MAF{atbe_max_vtxltk}
Question 1 – What did you get?
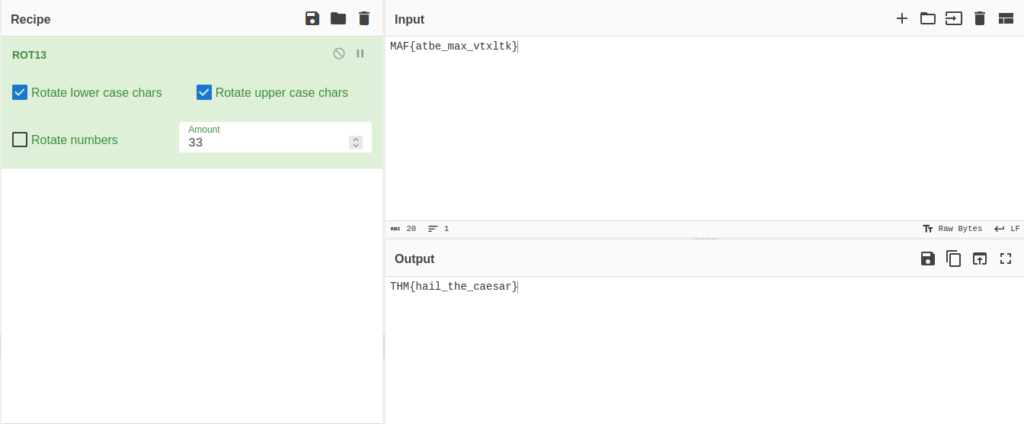
THM{hail_the_caesar}
Task 10 – Make a comment
Question 1 – I’m hungry now… I need the flag
- Using browser’s developer tools to get the required flag.
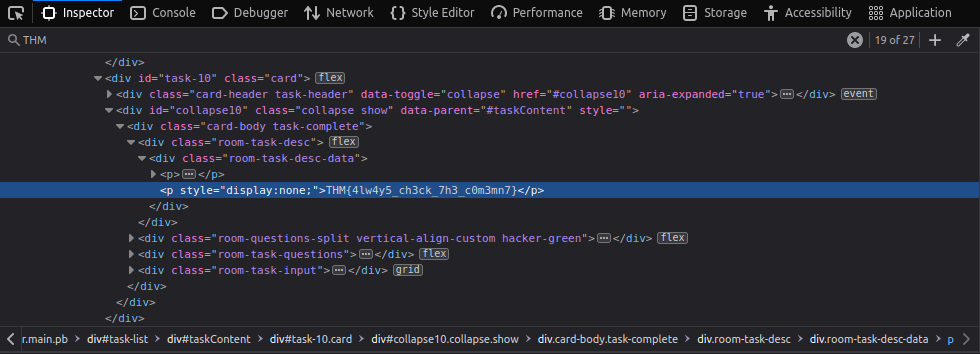
THM{4lw4y5_ch3ck_7h3_c0m3mn7} 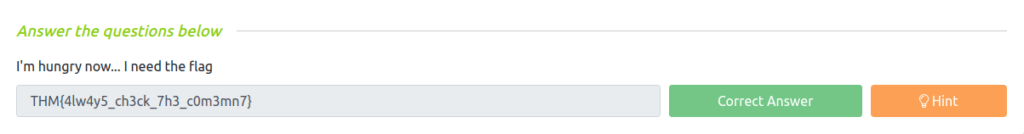
Task 11 – Can you fix it?
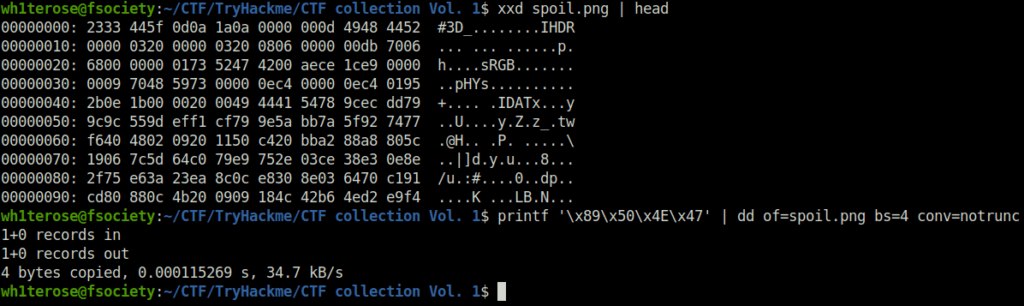
I accidentally messed up with this PNG file. Can you help me fix it? Thanks, ^^
Question 1 – What is the content?
```bash wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ xxd spoil.png | head 00000000: 2333 445f 0d0a 1a0a 0000 000d 4948 4452 #3D_........IHDR 00000010: 0000 0320 0000 0320 0806 0000 00db 7006 ... ... ......p. 00000020: 6800 0000 0173 5247 4200 aece 1ce9 0000 h....sRGB....... 00000030: 0009 7048 5973 0000 0ec4 0000 0ec4 0195 ..pHYs.......... 00000040: 2b0e 1b00 0020 0049 4441 5478 9cec dd79 +.... .IDATx...y 00000050: 9c9c 559d eff1 cf79 9e5a bb7a 5f92 7477 ..U....y.Z.z_.tw 00000060: f640 4802 0920 1150 c420 bba2 88a8 805c .@H.. .P. .....\ 00000070: 1906 7c5d 64c0 79e9 752e 03ce 38e3 0e8e ..|]d.y.u...8... 00000080: 2f75 e63a 23ea 8c0c e830 8e03 6470 c191 /u.:#....0..dp.. 00000090: cd80 880c 4b20 0909 184c 42b6 4ed2 e9f4 ....K ...LB.N... wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ printf '\x89\x50\x4E\x47' | dd of=spoil.png bs=4 conv=notrunc 1+0 records in 1+0 records out 4 bytes copied, 0.000115269 s, 34.7 kB/s

THM{y35_w3_c4n}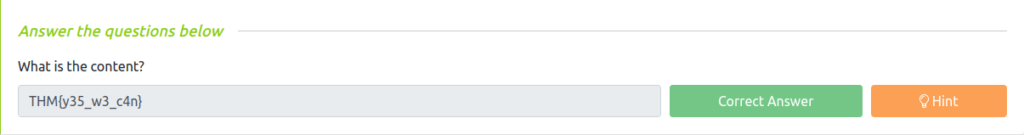
Task 12 – Read it
Some hidden flag inside Tryhackme social account.
Question 1 – Did you found the hidden flag?
- Use the following dork on Google – inurl:”reddit.com” &intext:”THM” & intitle:”tryhackme”
THM{50c14l_4cc0un7_15_p4r7_0f_051n7}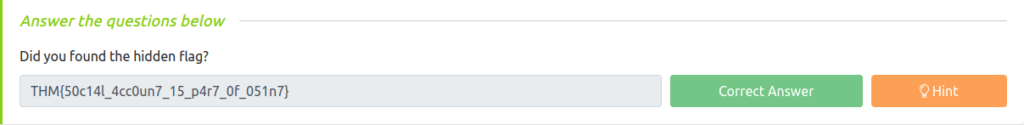
Task 13 – Spin my head
What is this?
++++++++++[>+>+++>+++++++>++++++++++<<<<-]>>>++++++++++++++.————.+++++.>+++++++++++++++++++++++.<<++++++++++++++++++.>>——————-.———.++++++++++++++.++++++++++++.<++++++++++++++++++.+++++++++.<+++.+.>—-.>++++.
Question 1 – Can you decode it?
- Use the following website to decode the brainfuck language and get the flag – https://www.dcode.fr/brainfuck-language
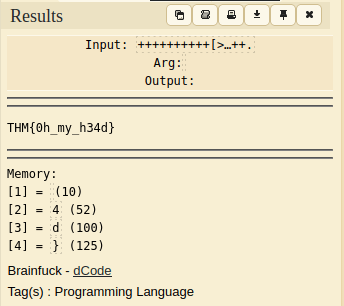
THM{0h_my_h34d}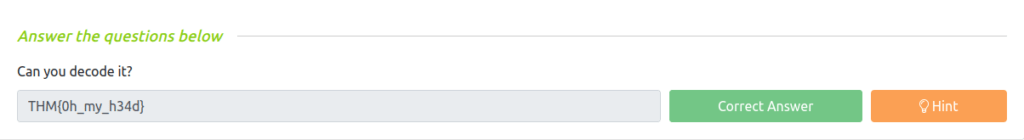
Task 14 – An exclusive!
Exclusive strings for everyone!
S1: 44585d6b2368737c65252166234f20626d
S2: 1010101010101010101010101010101010
Question 1 – Did you crack it? Feed me now!
- Use the following XOR calculator to get the flag. – https://xor.pw/#
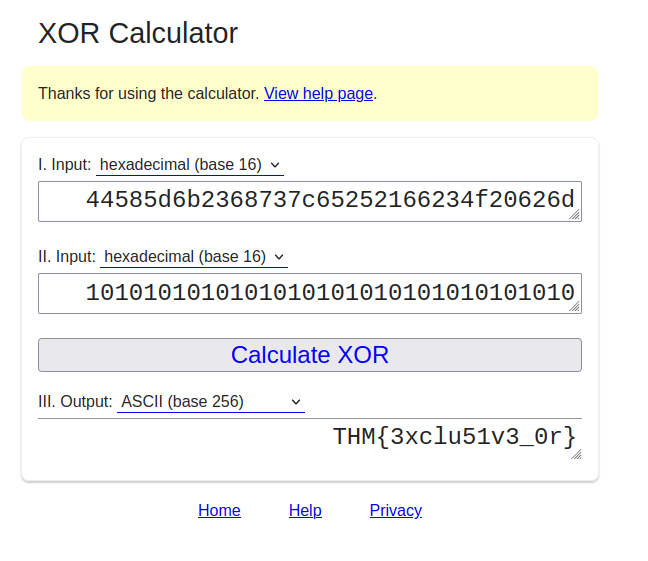
THM{3xclu51v3_0r}
Task 15 – Binary walk
Question 1 – Flag! Flag! Flag!
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ binwalk -e -c hell.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.02
30 0x1E TIFF image data, big-endian, offset of first image directory: 8
265845 0x40E75 Zip archive data, at least v2.0 to extract, uncompressed size: 69, name: hello_there.txt
266099 0x40F73 End of Zip archive, footer length: 22
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ ls
Extinction.jpg Final_message.txt Findme.jpg hell.jpg _hell.jpg-0.extracted _hell.jpg.extracted hello.hello QR.png spoil.png
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ cd _hell.jpg
_hell.jpg-0.extracted/ _hell.jpg.extracted/
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1$ cd _hell.jpg-0.extracted/
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1/_hell.jpg-0.extracted$ ls
40E75.zip hello_there.txt
wh1terose@fsociety:~/CTF/TryHackme/CTF collection Vol. 1/_hell.jpg-0.extracted$ cat hello_there.txt
Thank you for extracting me, you are the best!
THM{y0u_w4lk_m3_0u7}
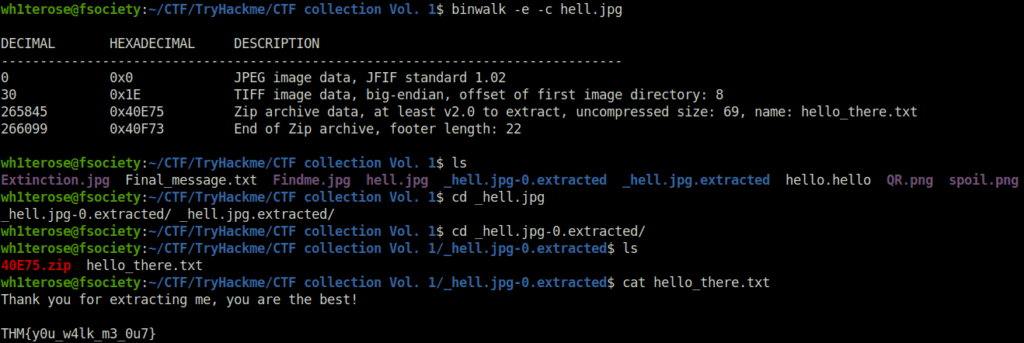
THM{y0u_w4lk_m3_0u7}
Task 16 – Darkness
Question 1 – What does the flag said?
- Download and install stegsolve for this challenge – https://www.aldeid.com/wiki/Stegsolve
java -jar stegsolve.jar
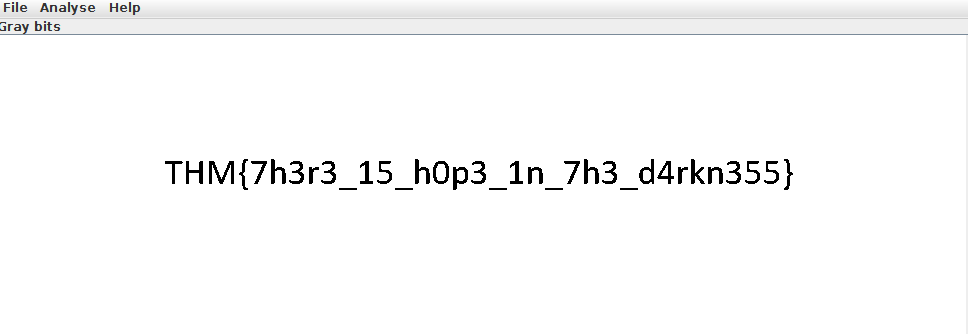
THM{7h3r3_15_h0p3_1n_7h3_d4rkn355}
Task 17 – A sounding QR
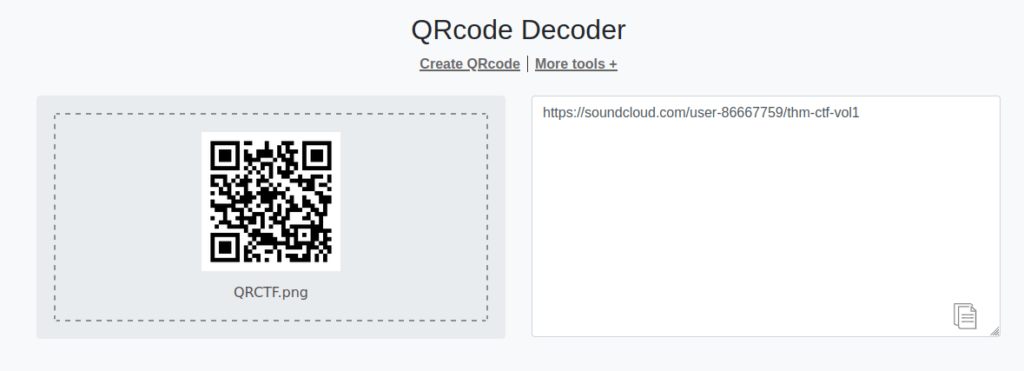
Question 1 – What does the bot said?
- Use the following resource to get the URL from the QR code – https://qrcode-decoder.com/
- Visit the following link and listen the audio carefully to get the flag. – https://soundcloud.com/user-86667759/thm-ctf-vol1
THM{SOUNDINGQR}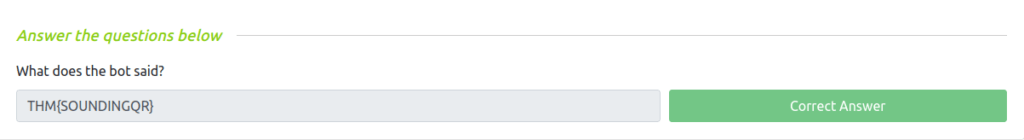
Task 18 – Dig up the past
Question 1 – Did you found my past?
- Use the wayback machine to capture the flag – https://web.archive.org/web/20200102131252/https://www.embeddedhacker.com/
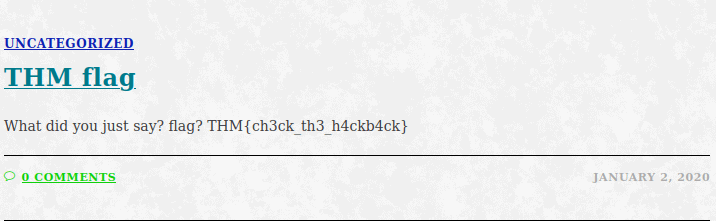
THM{ch3ck_th3_h4ckb4ck} 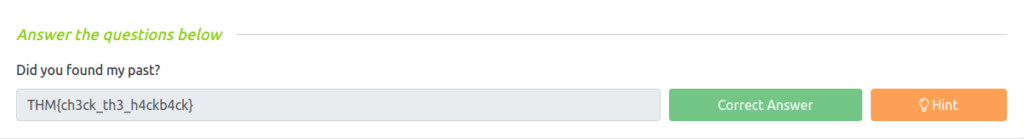
Task 19 – Uncrackable!
Can you solve the following? By the way, I lost the key. Sorry >.<
MYKAHODTQ{RVG_YVGGK_FAL_WXF}
Flag format: TRYHACKME{FLAG IN ALL CAP}
Question 1 – The deciphered text
- Use the following resource to crack the vigenere cipher – https://www.boxentriq.com/code-breaking/vigenere-cipher
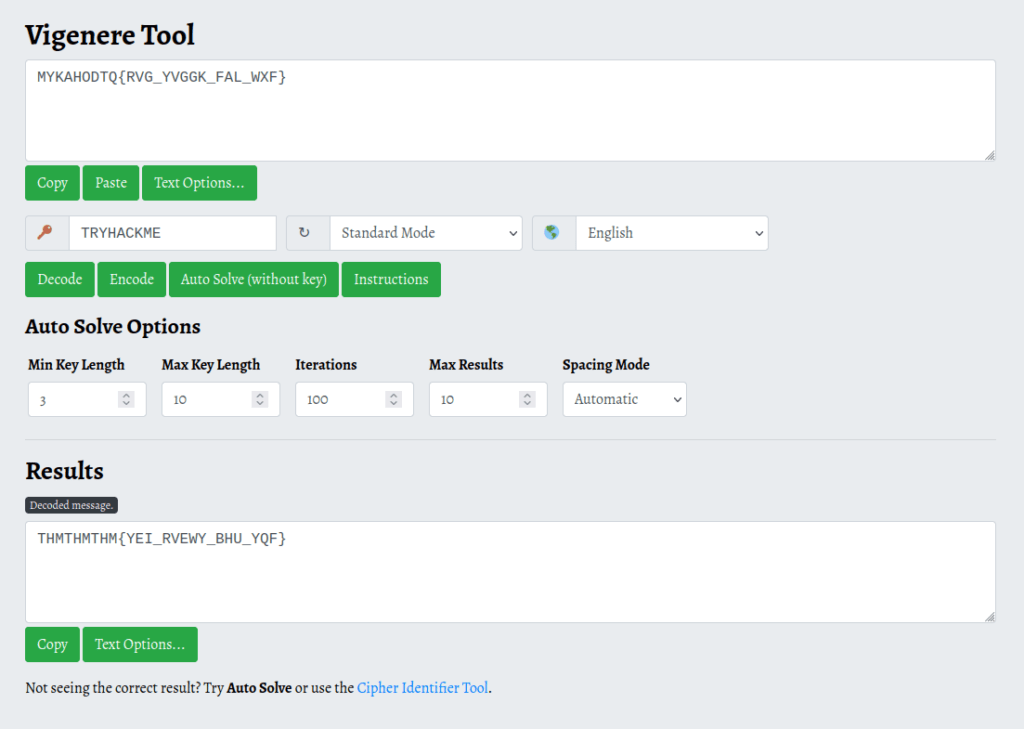
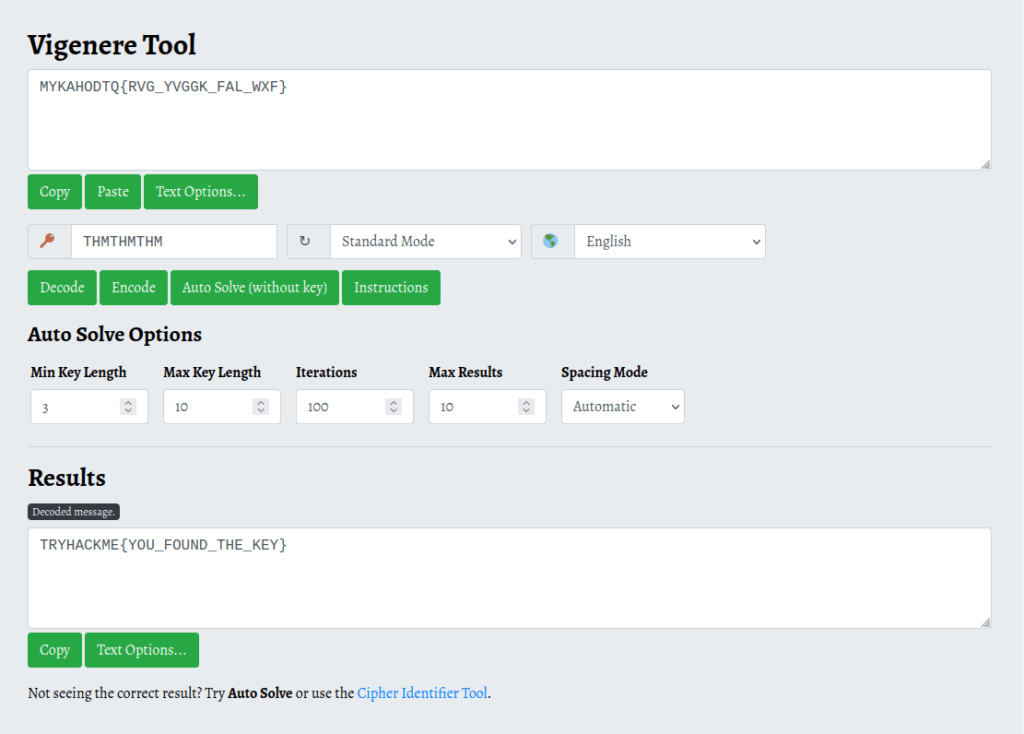
TRYHACKME{YOU_FOUND_THE_KEY}
Task 20 – Small bases
Decode the following text.
581695969015253365094191591547859387620042736036246486373595515576333693
Question 1 – What is the flag?
- Use the following decimal to Hexadecimal convertor to reveal the flag. – https://www.rapidtables.com/convert
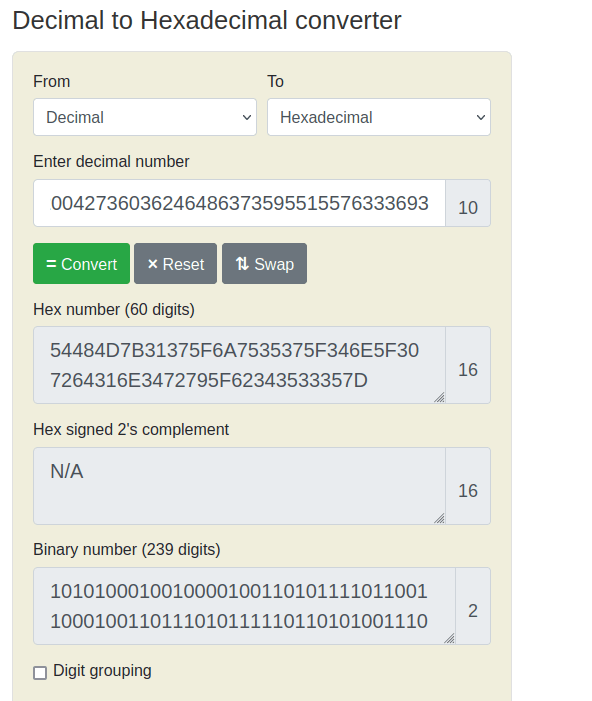
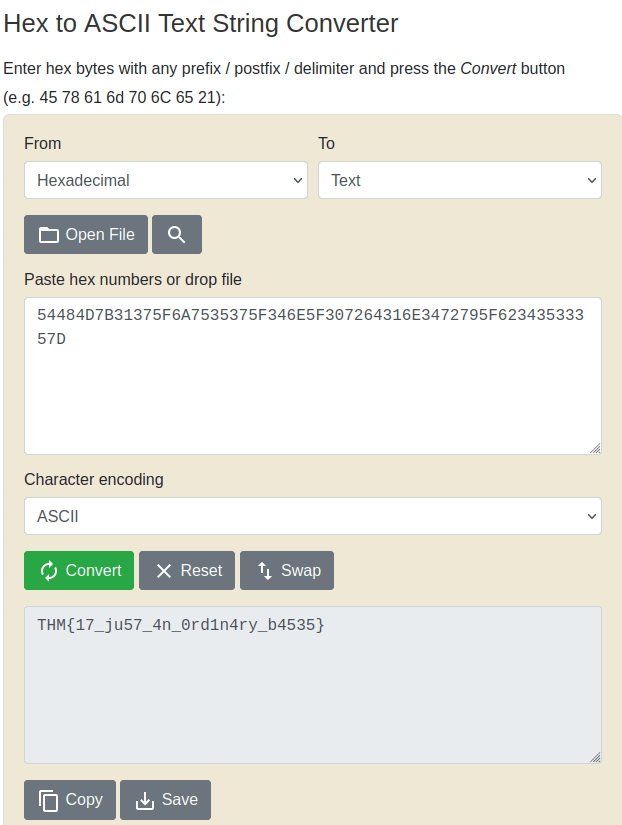
THM{17_ju57_4n_0rd1n4ry_b4535}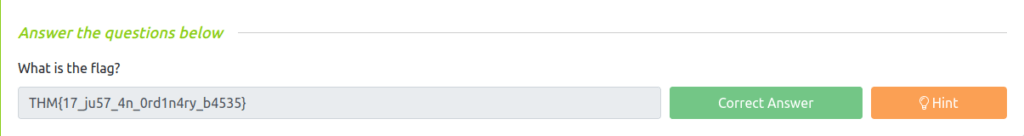
Task 21 – Read the packet
Question 1 – Did you captured my neighbor’s flag?
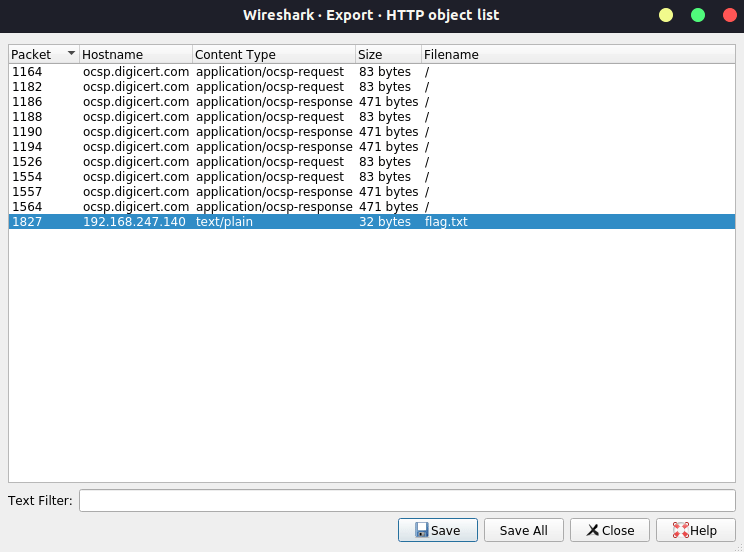
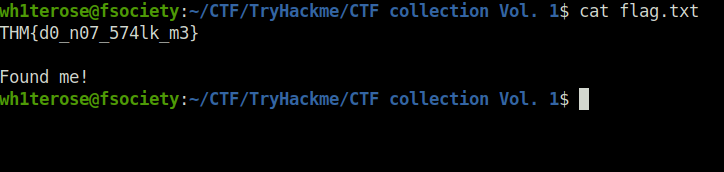
THM{d0_n07_574lk_m3}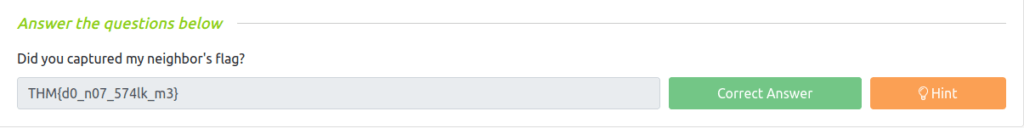
Also Read: Tryhackme – Content Discovery
Conclusion:

So this was the “CTF Collection Vol 1” room for you. This room was a bit long however was easy on the difficult part. Summing it up in a nutshell, we learned various basic topics that we come across in most of the CTF like machines. We saw encoding/decoding, OSINT, source code, strings and binary analysis and many more. Hope this room had exposed you to some of the techniques or things which were not familiar with. On that note, i will take your leave for now but you remember to “Hack the Planet”.




