In this walk through, we will be going through the Introduction to Antivirus room from Tryhackme. In this room, we will understand how antivirus software works and what detection techniques are used to bypass malicious file checks. So, let’s get started without any delay.
Table of Contents
Task 1 – Introduction
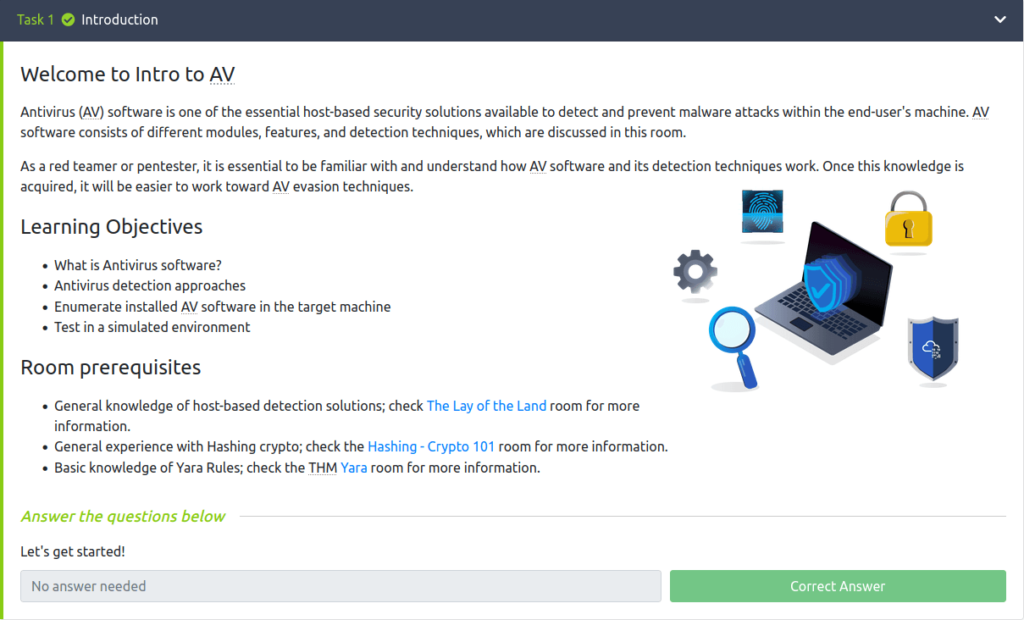
Task 2 – Antivirus Software
Question 1 – What does AV mean?
AntivirusQuestion 2 – Which PC Antivirus vendor implemented the first AV software on the market?
McAfeeQuestion 3 – Antivirus software is a _-based security solution.
Host
Task 3 – Antivirus Features
Question 1 – Which AV feature analyzes malware in a safe and isolated environment?
EmulatorQuestion 2 – An _ feature is a process of restoring or decrypting the compressed executable files to the original.
UnpackersQuestion 3 – Read the above to proceed to the next task, where we discuss the AV detection techniques.
Done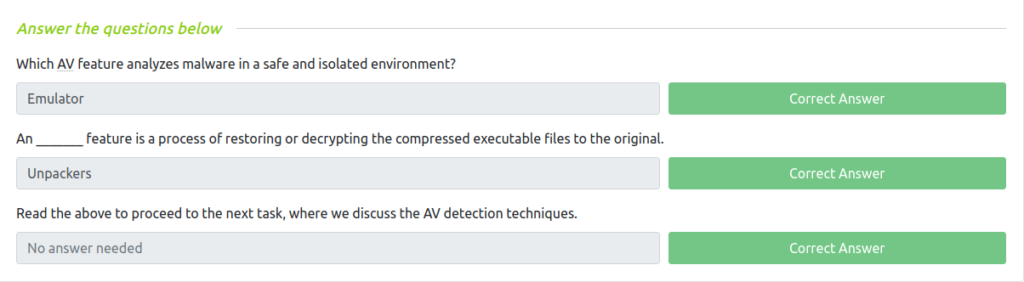
Task 4 – Deploy the VM
Question 1 – Once you’ve deployed the VM, it will take a few minutes to boot up. Then, progress to the next task!
Done
Task 5 – AV Static Detection
Question 1 – What is the sigtool tool output to generate an MD5 of the AV-Check.exe binary?
"c:\Program Files\ClamAV\sigtool.exe" --md5 AV-Check.exe
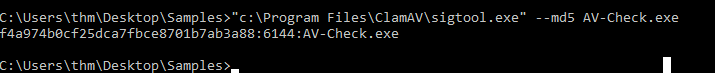
f4a974b0cf25dca7fbce8701b7ab3a88:6144:AV-Check.exeQuestion 2 – Use the strings tool to list all human-readable strings of the AV-Check binary. What is the flag?
strings AV-Check.exe
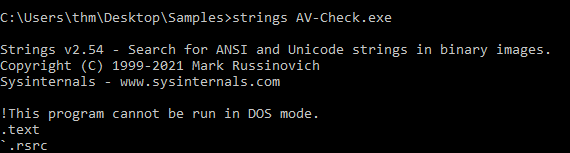
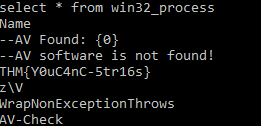
THM{Y0uC4nC-5tr16s}
Task 6 – Other Detection Techniques
Question 1 – Which detection method is used to analyze malicious software inside virtual environments?
Dynamic Detection
Task 7 – AV Testing and Fingerprinting
Question 1 – For the C# AV fingerprint, try to rewrite the code in a different language, such as Python, and check whether VirusTotal flag it as malicious.
DoneQuestion 2 – Read the Above!
Done
Task 8 – Conclusion
Also Read: DVWA – Weak Session IDs (Low/Med/High)
So that was “Introduction to Antivirus” for you. We looked into the basics of Anti-virus software and how it works. Post that, we took a deep dive into static malware detection and At last, completed the room by looking into Other detection techniques, malware testing and fingerprinting. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




