In this walk through, we will be going through the Introductory Researching room from Tryhackme. This room will serve as a brief overview of some of the most important resources available for recon ranging from Google Searching, vulnerability searching and linux manual pages. On that note, let’s get started.
Task 1 – Introduction
Task 2 – Example Research Question
Question 1 – In the Burp Suite Program that ships with Kali Linux, what mode would you use to manually send a request (often repeating a captured request numerous times)?
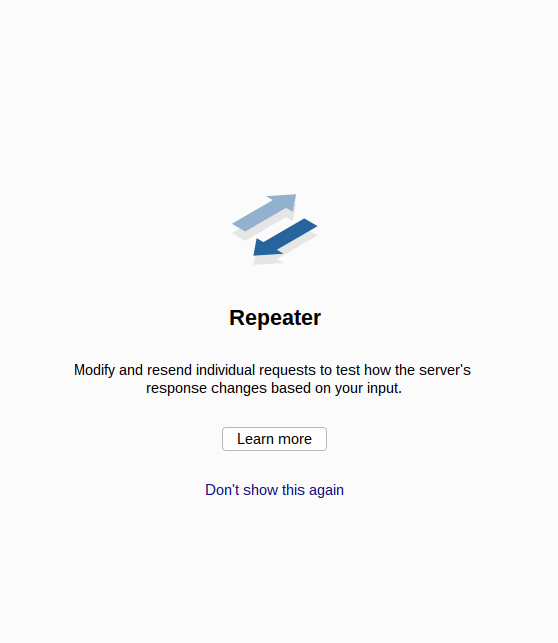
repeaterQuestion 2 – What hash format are modern Windows login passwords stored in?
NTLMQuestion 3 – What are automated tasks called in Linux?
cron jobsQuestion 4 – What number base could you use as a shorthand for base 2 (binary)?
base 16Question 5 – If a password hash starts with $6$, what format is it (Unix variant)?
SHA512crypt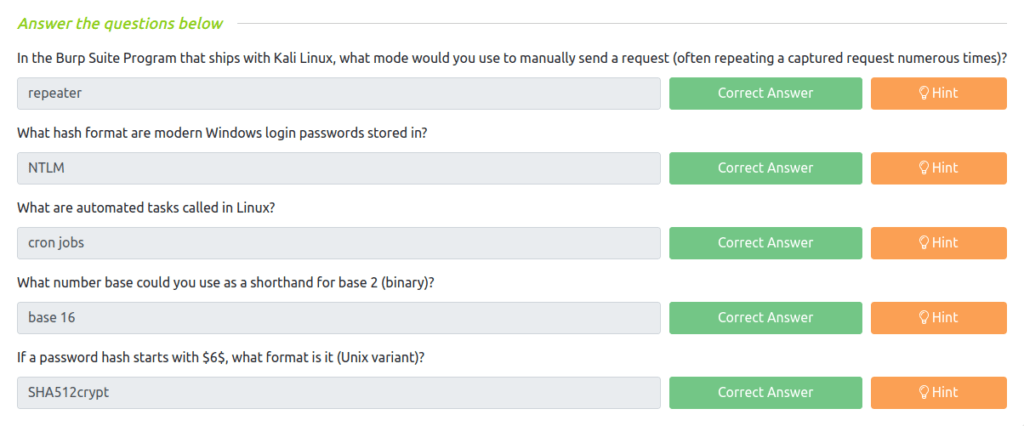
Task 3 – Vulnerability Searching
Question 1 – What is the CVE for the 2020 Cross-Site Scripting (XSS) vulnerability found in WPForms?
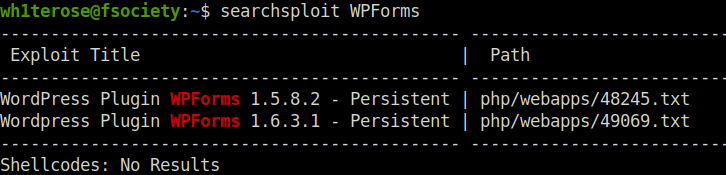
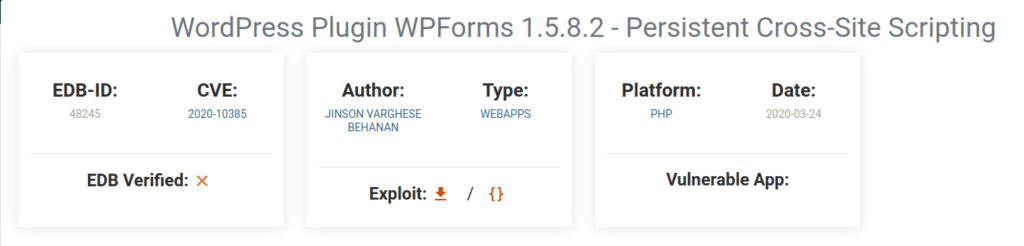
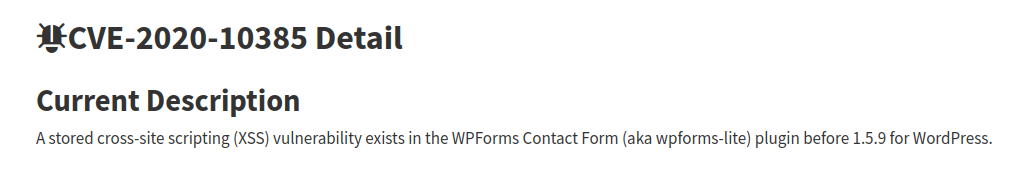
CVE-2020-10385Question 2 – There was a Local Privilege Escalation vulnerability found in the Debian version of Apache Tomcat, back in 2016. What’s the CVE for this vulnerability?
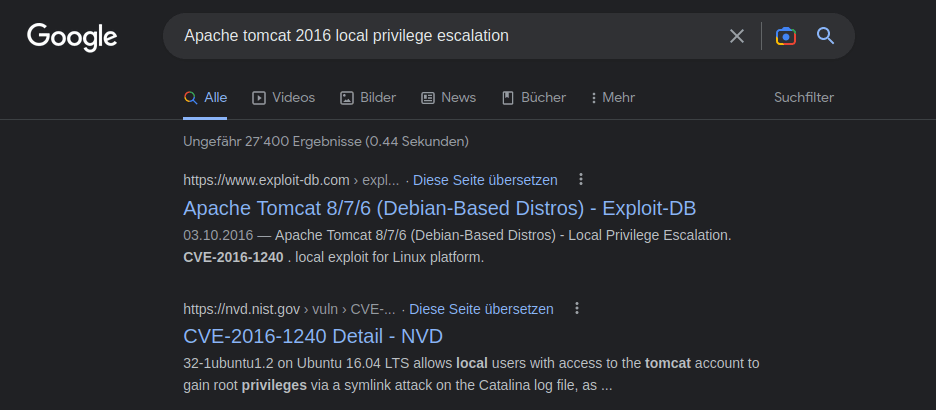
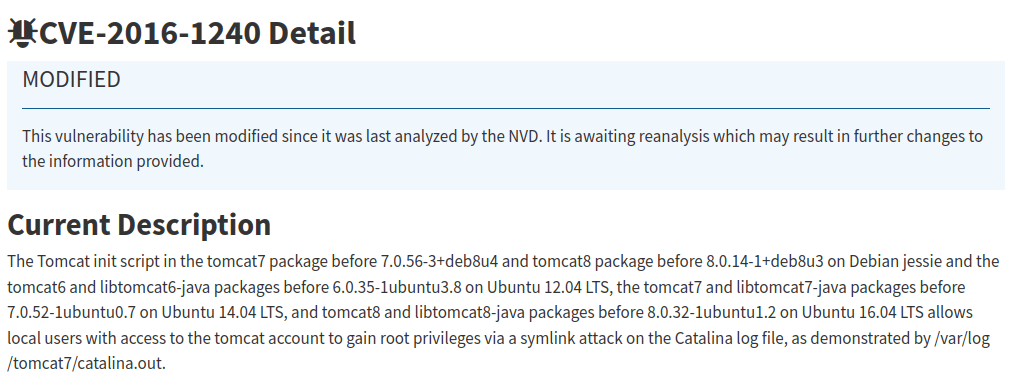
CVE-2016-1240Question 3 – What is the very first CVE found in the VLC media player?
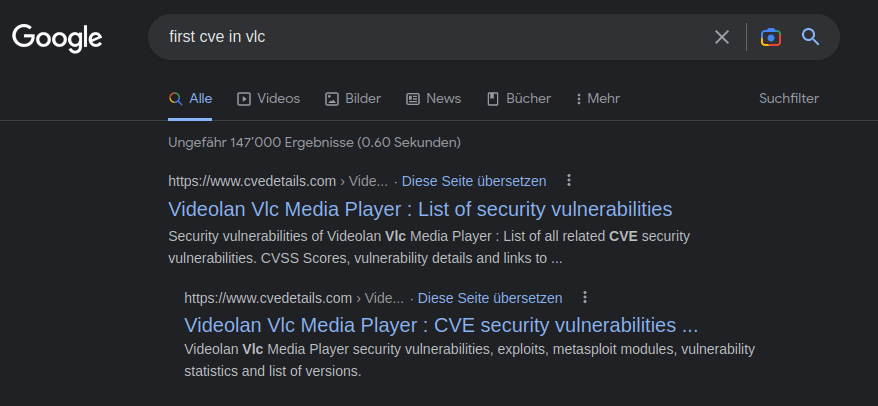
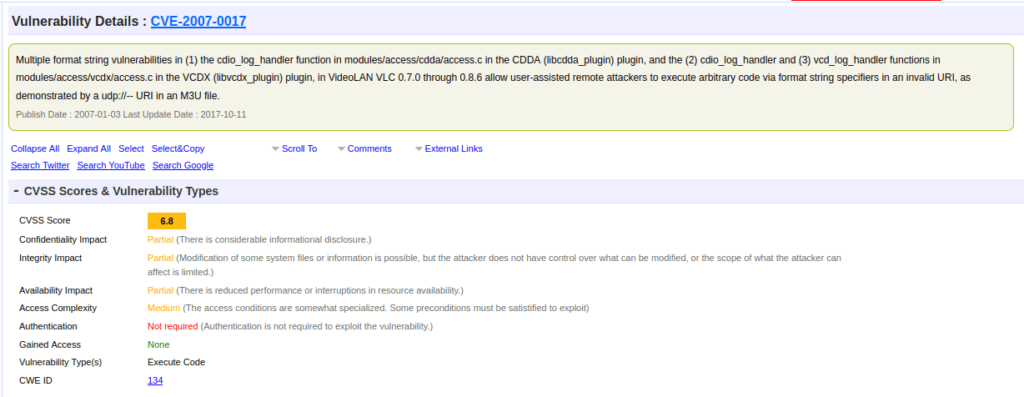
CVE-2007-0017Question 4 – If you wanted to exploit a 2020 buffer overflow in the sudo program, which CVE would you use?
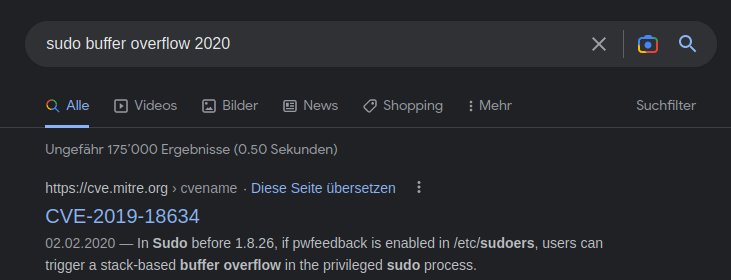
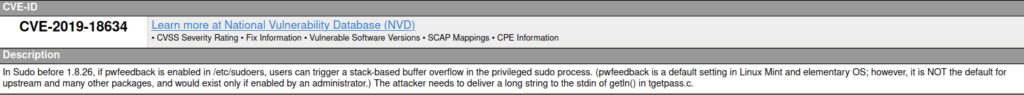
CVE-2019-18634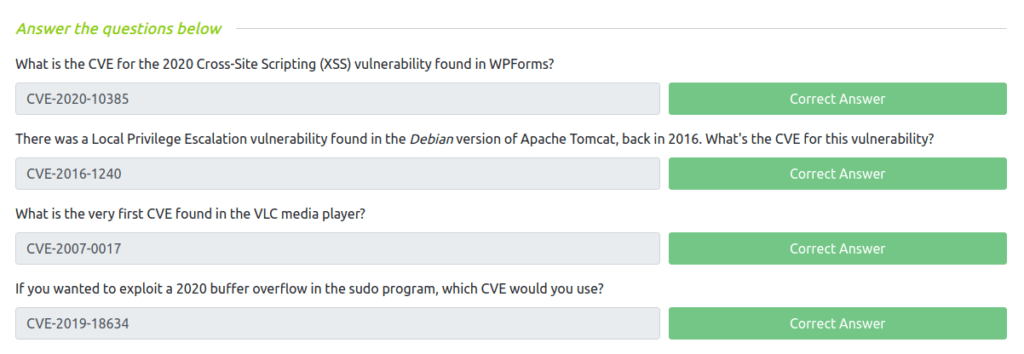
Task 4 – Manual Pages
Question 1 – SCP is a tool used to copy files from one computer to another.
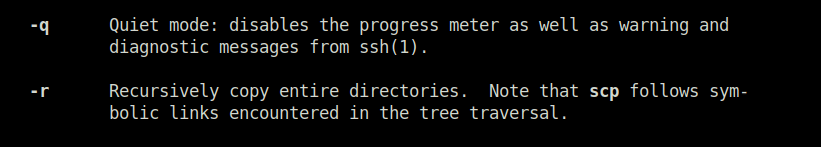
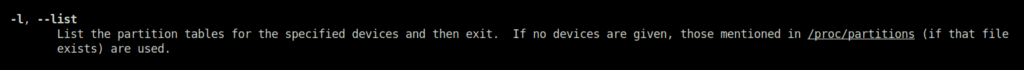
-rQuestion 2 – What switch would you use to list the current partitions?
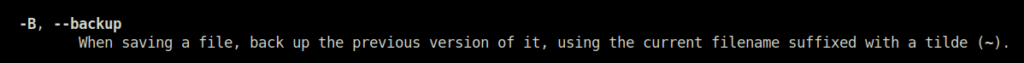
-lQuestion 3 – What switch would you use to make a backup when opening a file with nano?
-BQuestion 4 – What command would you use to start netcat in listen mode, using port 12345?


nc -lv -p 12345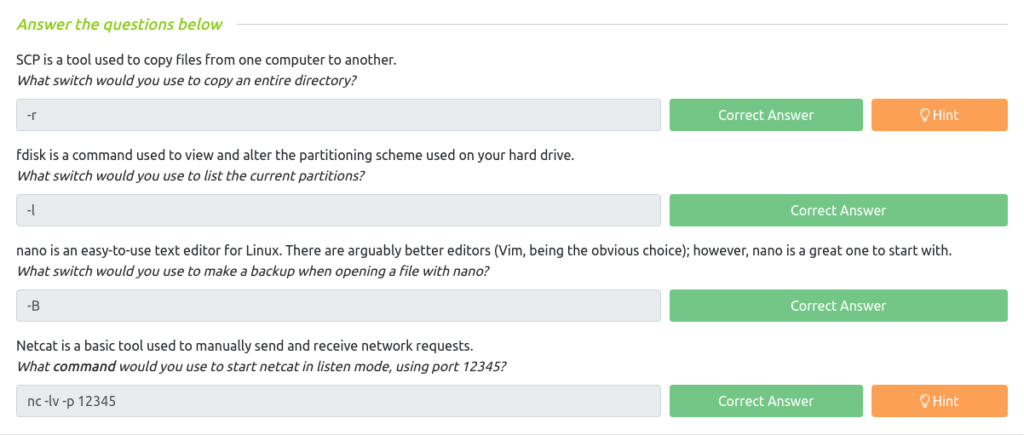
Task 5 – Final Thoughts
Also Read: Tryhackme – Introduction to SIEM
So that was “Introductory Researching” for you. We have covered the basics of recon and wet our feet with some Google Searching. Later, we looked on how we can investigate vulnerabilities and find exploits regarding the same. At last, we looked into some man pages which we can used while using common commands and tools. On that note, , allow me to take your leave. I will meet you in the next one, till then “Keep Researching”.




