In this walkthrough, we will be going through Mal (Malware Introductory) room by Tryhackme. After completing this room, you will be able to perform static and dynamic analysis using various tools out there. This room will covers the basics of practical malware analysis and how we can approach a live malware sample in the wild, if it required anywhere in our journey. Malware analysis is mostly done by Digital Forensics Investigators and Blue Team people. So, if you want to join the defensive unit of the workforce, this room is for you. So, let’s get started.

Task 1 – What is the Purpose of Malware Analysis?

Task 2 – Understanding Malware Campaigns
Question 1 – What is the famous example of a targeted attack-esque Malware that targeted Iran?
Stuxnet
Question 2 – What is the name of the Ransomware that used the Eternalblue exploit in a “Mass Campaign” attack?
Wannacry
Task 3 – Identifying if a Malware Attack has Happened
Question 1 – Name the first essential step of a Malware Attack?
Delivery
Question 2 – Now name the second essential step of a Malware Attack?
Execution
Question 3 – What type of signature is used to classify remnants of infection on a host?
Host-based Signatures
Question 4 – What is the name of the other classification of signature used after a Malware attack?
Network-based Signatures

Task 4 – Static Vs. Dynamic Analysis
Question 1 – I understand the two broad categories employed when analysing potential malware!
Done
Task 5 – Discussion of Provided Tools & Their Uses
Question 1 – Lets proceed
Done
Task 6 – Connecting to the Windows Analysis Environment (Deploy)
Question 1 – I’ve logged in!
Done
Task 7 – Obtaining MD5 Checksums of Provided Files
Question 1 – The MD5 Checksum of aws.exe

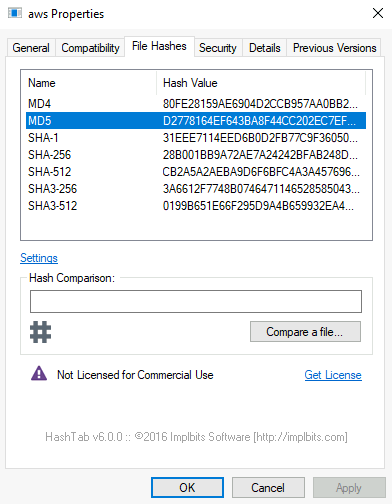
D2778164EF643BA8F44CC202EC7EF157
Question 2 – The MD5 Checksum of Netlogo.exe
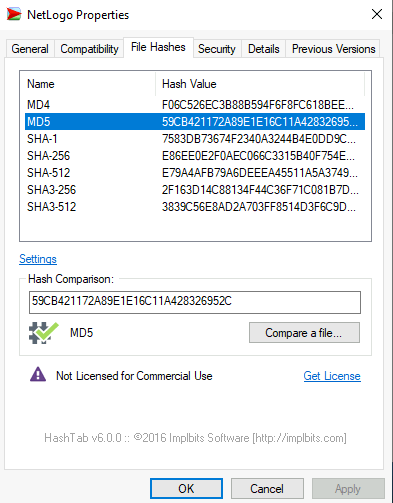
59CB421172A89E1E16C11A428326952C
Question 3 – The MD5 Checksum of vlc.exe

5416BE1B8B04B1681CB39CF0E2CAAD9F

Task 8 – Now lets see if the MD5 Checksums have been analysed before
Question 1 – Does Virustotal report this MD5 Checksum / file aws.exe as malicious? (Yay/Nay)

Nay
Question 2 – Does Virustotal report this MD5 Checksum / file Netlogo.exe as malicious? (Yay/Nay)
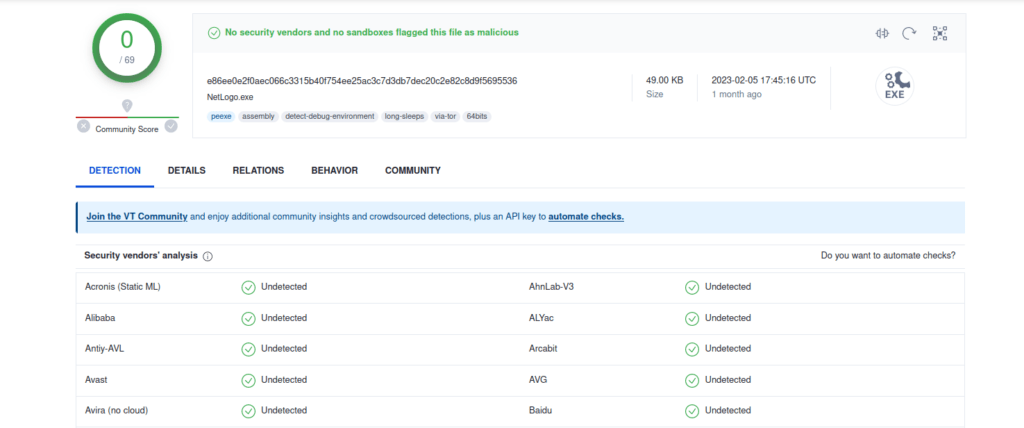
Nay
Question 3 – Does Virustotal report this MD5 Checksum / file vlc.exe as malicious? (Yay/Nay)

Nay

Task 9 – Identifying if the Executables are obfuscated / packed
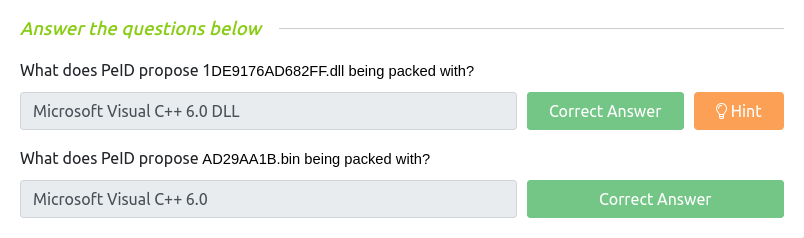
Question 1 – What does PeID propose 1DE9176AD682FF.dll being packed with?

Microsoft Visual C++ 6.0 DLL
Question 2 – What does PeID propose AD29AA1B.bin being packed with?
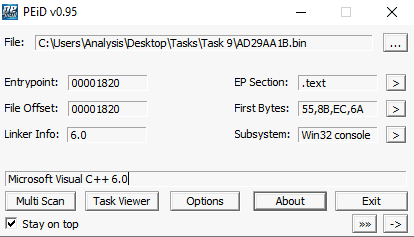
Microsoft Visual C++ 6.0
Task 10 – What is Obfuscation / Packing?
Question 1 – What packer does PeID report file “6F431F46547DB2628” to be packed with?

FSG 1.0 -> dulek/xt

Task 11 – Visualising the Differences Between Packed & Non-Packed Code
Question 1 – Cursed obfuscation!
Done

Task 12 – Introduction to Strings
Question 1 – What is the URL that is outputted after using “strings”
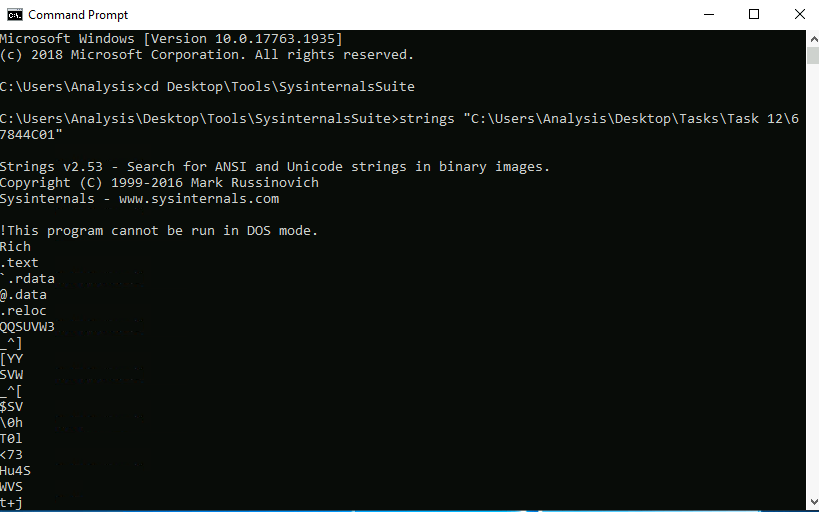
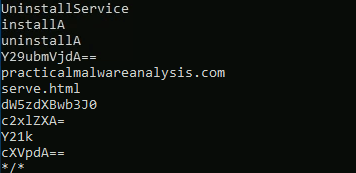
practicalmalwareanalysis.com
Question 2 – How many unique “Imports” are there?
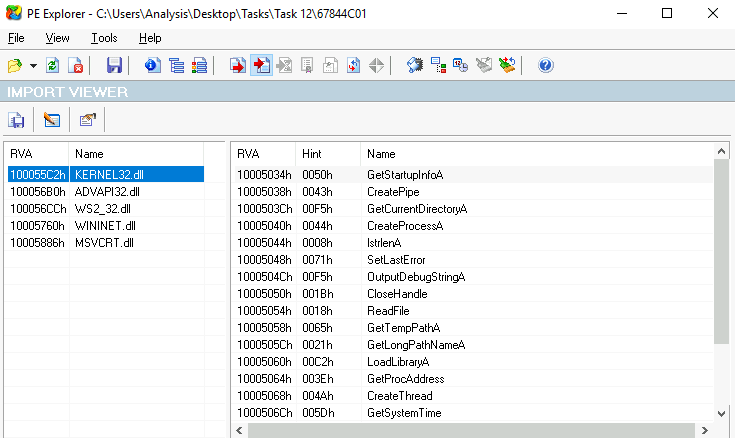
5
Task 13 – Introduction to Imports
Question 1 – How many references are there to the library “msi” in the “Imports” tab of IDA Freeware for “install.exe“

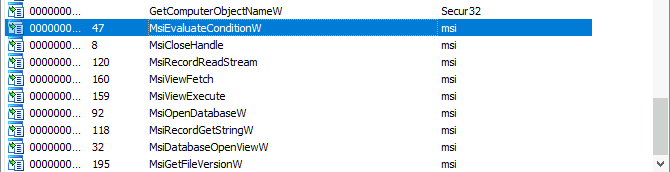
9

Task 14 – Practical Summary
Question 1 – What is the MD5 Checksum of the file?
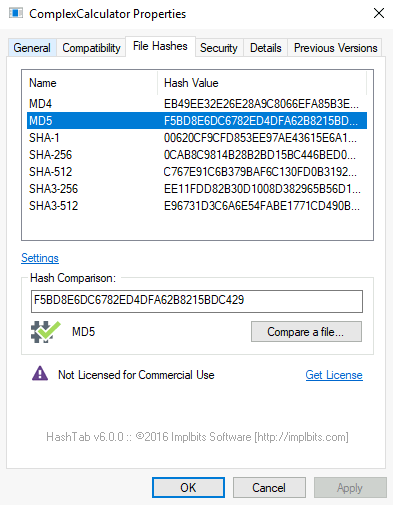
F5BD8E6DC6782ED4DFA62B8215BDC429
Question 2 – Does Virustotal report this file as malicious? (Yay/Nay)

Yay
Question 3 – What is the last string outputted?

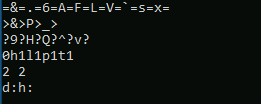
d:h:
Question 4 – What is the output of PeID when trying to detect what packer is used by the file?

Nothing found *

Also read: Tryhackme – Crack the hash
Conclusion:

In this room, we started with the basics of Malware analysis and its types. Then we moved ahead and looked some of the commonly used tools in the task. Further, we first learned how to get an executable hash and get it verified via Virustotal. After that, we had a short dive in Obfuscation and packing techniques. Getting over it, we learned a few tricks to check the hidden strings within binaries. Lastly, we finished with imports and a practical exercise to test out our newly acquired skills. On that note, i will take your leave till the next episode, till then “Hack the planet”.