In this walkthrough, we will be going through Linux Strength Training room by Tryhackme.This room is specifically designed to harden our linux command line skills and is a continuation to the Tryhackme’s Linux fundamentals series. After completing this room, you will be navigating on the linux terminal like ninja. The content of the room covers finding files and working with files, cracking hashes and decoding base 64 strings, followed by some interesting challenges. So, let’s get started.

Task 1 – Intro
Task 2 – Finding your way around linux – overview
Question 1 – I have read and understood
Done
Question 2 – What is the correct option for finding files based on group
-group
Question 3 – What is format for finding a file with the user named Francis and with a size of 52 kilobytes in the directory /home/francis/
find /home/francis -type f -user francis -size 50k
Question 4 – SSH as topson using his password topson. Go to the /home/topson/chatlogs directory and type the following: grep -iRl ‘keyword’. What is the name of the file that you found using this command?

2019-10-11
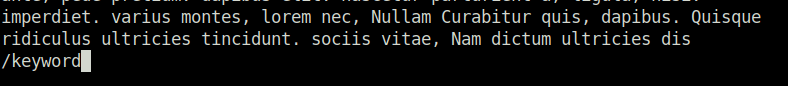
Question 5 – Type: less [filename] to open the file. Then, before anything, type / before typing: keyword followed by [ENTER]. Notice how that allowed us to search for the first instance of that word in the entire document. For much larger documents this can be useful and if there are many more instances of that word in the document, we would be able to hit enter again to find the next instance in the document.

Done
Question 6 – What are the characters subsequent to the word you found?
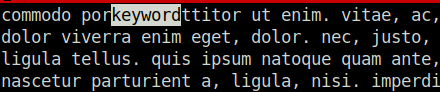
ttitor
Question 7 – Read the file named ‘ReadMeIfStuck.txt’. What is the Flag?
We will start with finding the text file using the command given below. Here, we are specifying the type as “file” and name to search for is “ReadmeIfStuck.txt”.
find -type f -name ReadMeIfStuck.txt
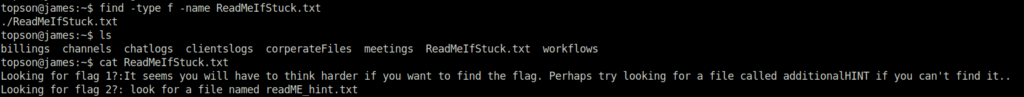
Looks like, this is only a clue. As per the text, we have to find and read file named “additionalHINT”. So, let’s do it by following the given command below.
find -type f -name additionalHINT
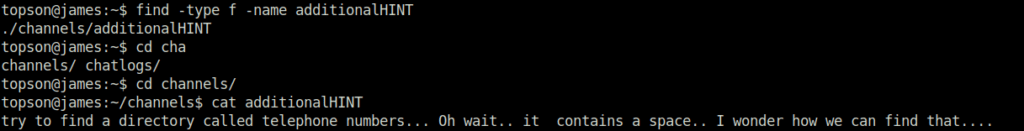
Now, we have to find a directory named telephone numbers. We will do it using the given below command, where we have specified the type as “directory” and name as “telephone numbers”.
find -type d -name 'telephone numbers'

As per the readME.txt in telephone numbers directory, we have to find a file with a modified date of 2016-09-12 from the /workflows directory. This can be achieved by following the given command below. Let me break it down for you. Firstly we are specifying the type as “file”, then we are specifying the start modified date following the end modified date. This command will exclude all the files before the start date and after the end date. As per the task, we have to find a file with a modified date of 2016-09-12. For which, we have selected the start date as 2016-09-11 and end date as 2016-09-13.
find -type f -newermt 2016-09-11 ! -newermt 2016-09-13

Checking the content of the file with “less”, followed with a search of the keyword “Flag” gives us our first flag.
less xft/eBQRhHvx


Flag{81726350827fe53g}
Task 3 – Working with files
Question 1 – Hypothetically, you find yourself in a directory with many files and want to move all these files to the directory of /home/francis/logs. What is the correct command to do this?
mv * /home/francis/logs
Question 2 – Hypothetically, you want to transfer a file from your /home/james/Desktop/ with the name script.py to the remote machine (192.168.10.5) directory of /home/john/scripts using the username of john. What would be the full command to do this?
scp /home/james/Desktop/script.py john@192.168.10.5:/home/john/scripts
Question 3 – How would you rename a folder named -logs to -newlogs
mv -- -logs -newlogs
Question 4 – How would you copy the file named encryption keys to the directory of /home/john/logs
mv "encryption keys" /home/john/logs
Question 5 – Find a file named readME_hint.txt inside topson’s directory and read it. Using the instructions it gives you, get the second flag.
find -type -f -name readME_hint.txt

mv -- -MoveMe.txt "-march folder"/
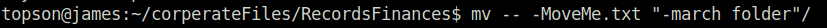
cd -- -march\ folder/

Flag{234@i4s87u5hbn$3}
Task 4 – Hashing – introduction
Question 1 – Download the hash file attached to this task and attempt to crack the MD5 hash. What is the password?
john --format=raw-md5 hash1.txt

secret123
Question 2 – What is the hash type stored in the file hashA.txt
find -type f -name hashA.txt
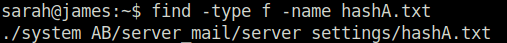

Using hash-identifier to identify the hash found in hashA.txt
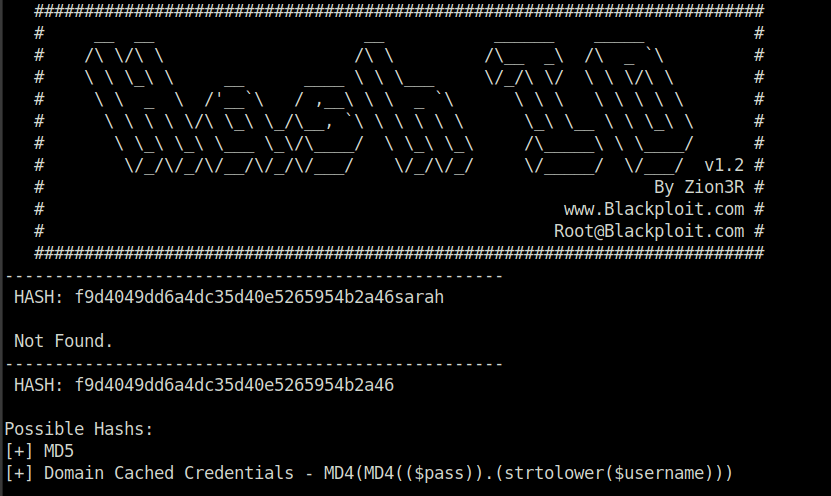
MD4
Question 3 – Crack hashA.txt using john the ripper, what is the password?
john --format=raw-md4 MD4_hash.txt

admin
Question 4 – What is the hash type stored in the file hashB.txt
find -type f -name hashB.txt


SHA-1
Question 5 – Find a wordlist with the file extention of ‘.mnf’ and use it to crack the hash with the filename hashC.txt. What is the password?
We will start with finding the file hashC.txt using the given command below. Later, we will use hash-identifier to identify the hash inside the file.
find -type f -name hashC.txt

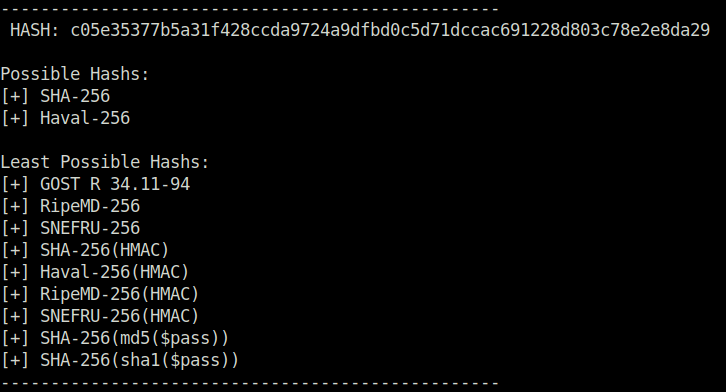
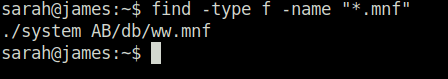
Next, we will find the wordlist we need for this task using the following command. Once find, we will download it to in our system using wget. For that we have to start a python server in the tryhackme box using – python3 -m http.server and downloading the file in our system using – wget http://<Tryhackme Box IP>:8000/ww.mnf
find -type f -name "*.mnf"
Finally, cracking the hash using John the ripper and the downloaded wordlist.
john --format=raw-sha256 SHA_hash.txt --wordlist=ww.mnf
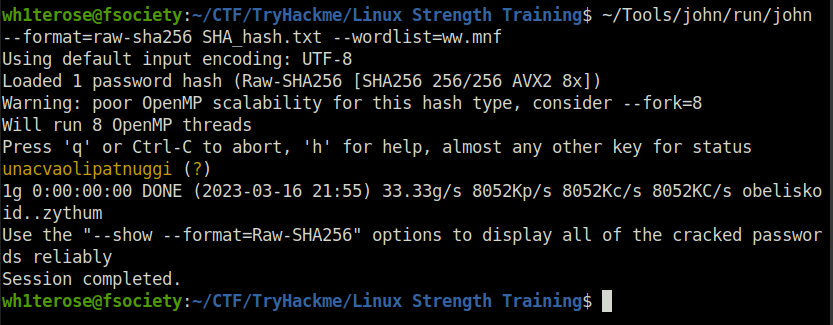
unacvaolipatnuggi
Question 6 – Crack hashB.txt using john the ripper, what is the password?
john --format=raw-sha1 SHA1.txt
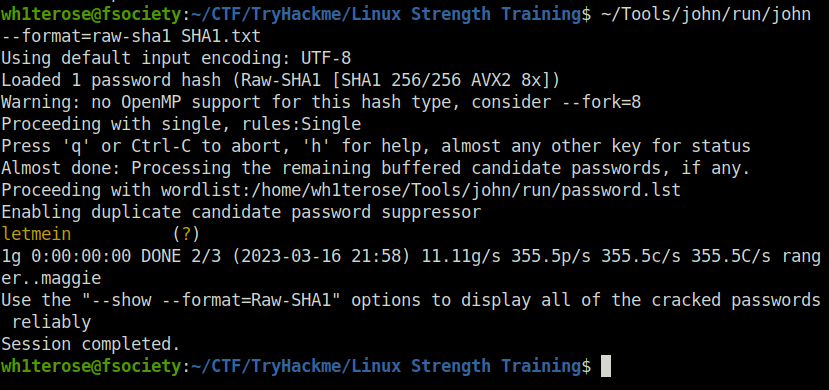
letmein
Also read: Tryhackme – Crack the hash
Task 5 – Decoding base64
Question 1 – what is the name of the tool which allows us to decode base64 strings?
base64
Question 2 – find a file called encoded.txt. What is the special answer?
find -type f -name encoded.txt

less system\ AB/managed/encoded.txt | base64 -d > decoded.txt cat decoded.txt | grep "special"
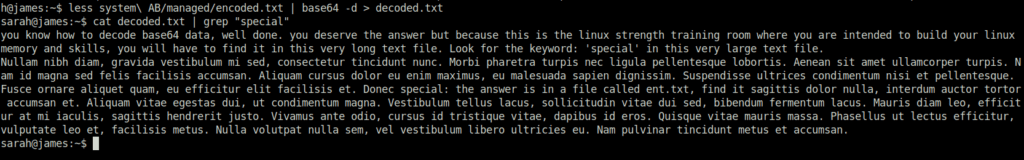
As per the decoded text, we will get the answer in a file named “ent.txt”. Next, we will find the file using the given command below. Reading it will gives us a hashed string.
find -type f -name ent.txt

Using Crackstation to crack the hashed string gives us our answer for the question.

john
Task 6 – Encryption/Decryption using gpg
Question 1 – Now try it for yourself. Make a random text file and enter some readable sentences in there before encrypting and decrypting it as illustrated above.
Done
gpg --cipher-algo AES-256 --symmetric message.txt
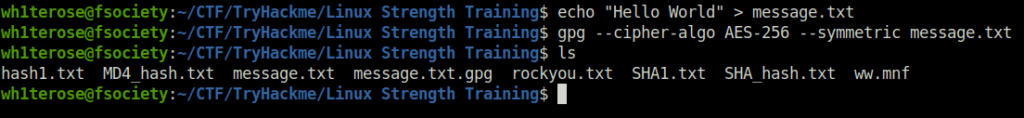
gpg message.txt.gpg
Question 2 – You wish to encrypt a file called history_logs.txt using the AES-128 scheme. What is the full command to do this?
gpg -cipher-algo AES-128 symmetric history_logs.txt
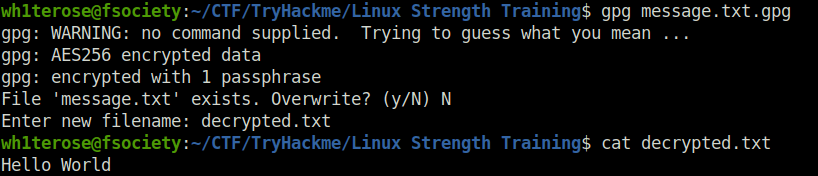
Question 3 – What is the command to decrypt the file you just encrypted?
gpg history_logs.txt.gpg
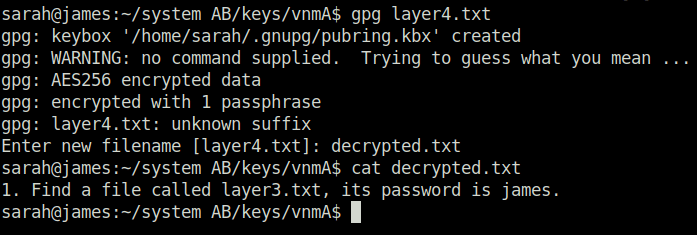
Question 4 – Find an encrypted file called layer4.txt, its password is bob. Use this to locate the flag. What is the flag?
find -type f -name layer4.txt

gpg layer4.txt
find -type f -name layer3.txt

gpg layer3.txt

find -type f -name layer2.txt
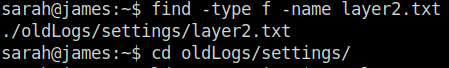
gpg layer2.txt

Seems like a base 64 encoded string. We can decode it using Cyberchef. Doing that, we got our next clue.

find -type f -name layer1.txt
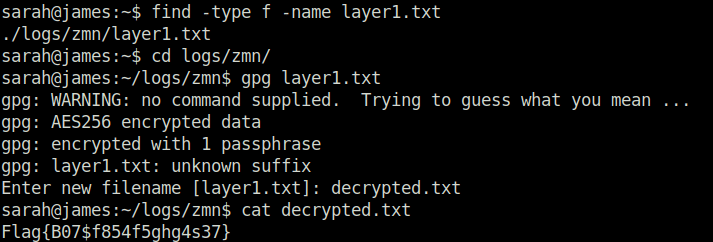
Flag{B07$f854f5ghg4s37}
Task 7 – Cracking encrypted gpg files
Question 1 – Now try it yourself! Encrypt a file and use a common password contained in the wordlist you wish to use. Follow the instructions above to decrypt as if you are a hacker. If it worked, well done.
Done
gpg2john message.txt.gpg > john_gpg

john --format=gpg john_gpg

Question 2 – Find an encrypted file called personal.txt.gpg and find a wordlist called data.txt. Use tac to reverse the wordlist before brute-forcing it against the encrypted file. What is the password to the encrypted file?
find -type f -name personal.txt.gpg

find -type f -name data.txt

tac data.txt > data1.txt

gpg2john personal.txt.gpg > personal_hash
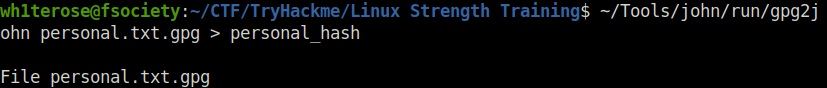
john --format=gpg personal_hash --wordlist=data1.txt

valamanezivonia
Question 3 – What is written in this now decrypted file?
gpg personal.txt.gpg
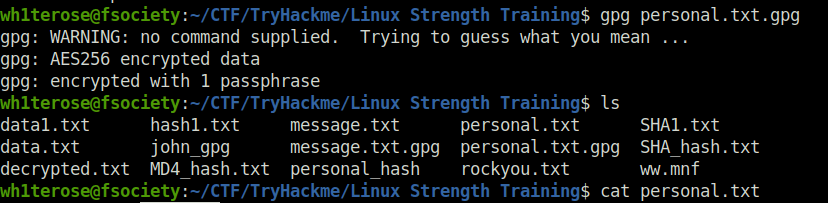

Getting stronger Linux
Task 8 – Reading SQL databases
Question 1 – Find a file called employees.sql and read the SQL database. (Sarah and Sameer can log both into mysql using the password: password). Find the flag contained in one of the tables. What is the flag?
find -type f -name employees.sql
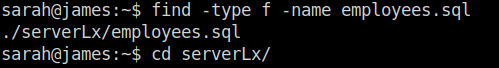
mysql -u sarah -p source employees.sql

show databases; use employees; show tables;

describe employees; select * from employees where first_name like "Lobel";


Flag{13490AB8}
Task 9 – Final Challenge
Question 1 – Go to the /home/shared/chatlogs directory and read the first chat log named: LpnQ. Use this to help you to proceed to the next task.
Done
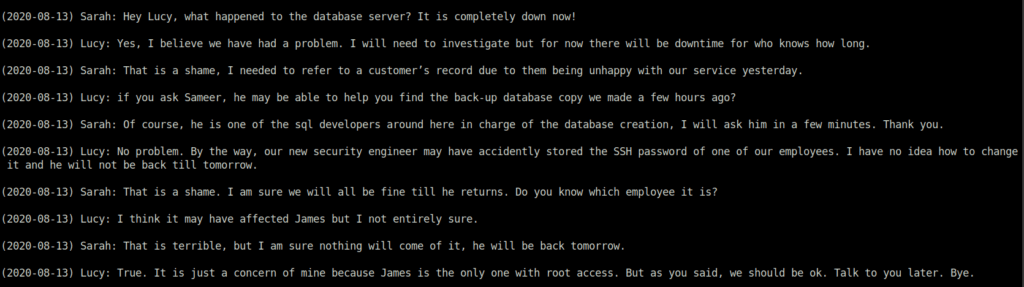
By reading LpnQ, we came to know that Sarah and Lucy is talking about an employee’s SSH password that is unchanged mistakenly.
less LpnQ
Question 2 – What is Sameer’s SSH password?
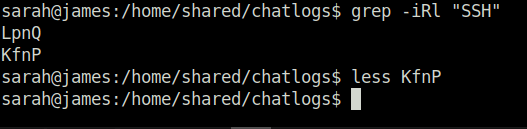
Next, we tried to find Sameer’s SSH password using command given below. Result shows two files, that has a occurrence of the word “SSH” in it. We have already read the contents of the file LpnQ. So, we’ll get into the another one – KfnP for getting the password.
grep -iRl "SSH"
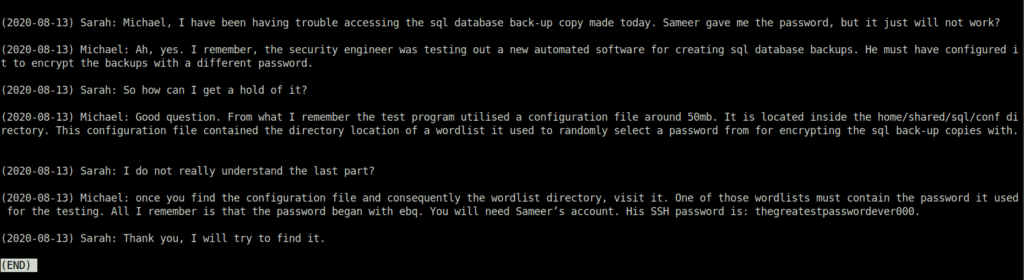
thegreatestpasswordever000
Question 3 – What is the password for the sql database back-up copy
Next, in the above content, we can see that Michael is talking about a wordlist file that contain password for the sql database backup copy. So, we’ll start with finding the same.
grep -iRl "wordlist"

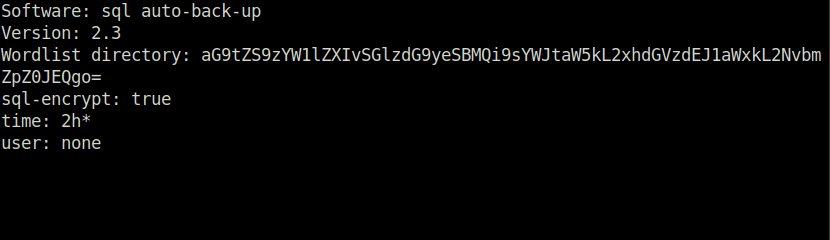
Reading out the file we found, we got a string in place of the Wordlist directory path. Seems like a base 64 encoded string, we can decode it using Cyberchef. That gives us, the directory of the wordlist.

As per the above text, the password did start with “ebq”. So, we will try to find files that has a word starting with the former.
grep -iRl "ebq"

less Ulpsmt

ebqattle
Question 4 – Find the SSH password of the user James. What is the password?
We will start with decrypting the sql backup password, we have found earlier.
gpg 2020-08-13.zip.gpg unzip 2020-08-13.zip
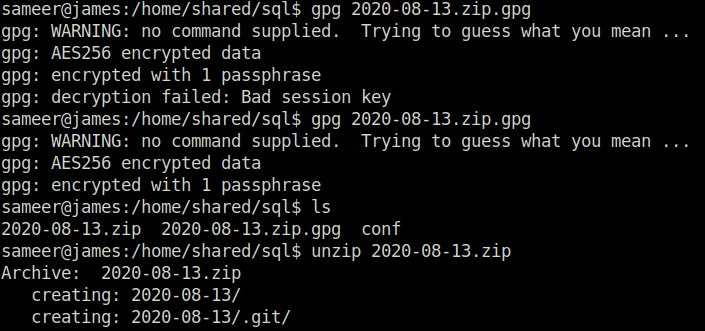
mysql -u sameer -p
Password to login in the Mysql database – password
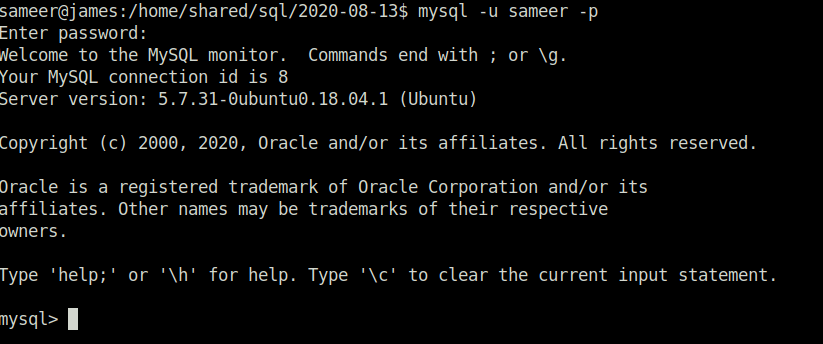
source employees.sql show databases; use employees; show tables;
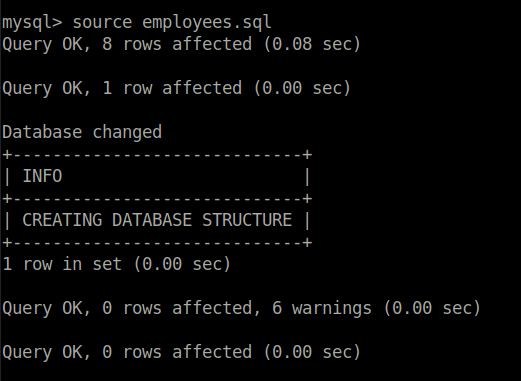

select * from employees where first_name like "james";
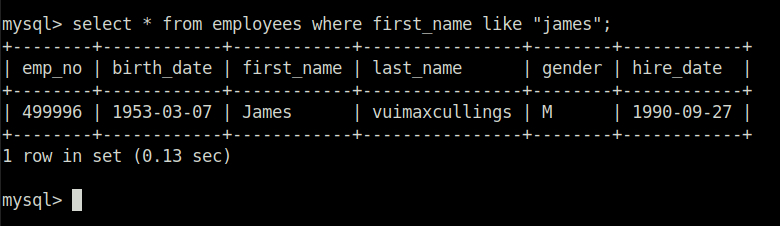
vuimaxcullings
Question 5 – SSH as james and change the user to root?
Done
sudo su

Question 6 – What is the root flag?
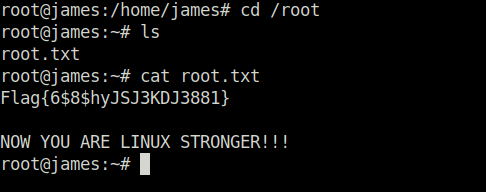
Flag{6$8$hyJSJ3KDJ3881}
Conclusion:

So, that was it. We conquered this room as well. Summarizing the above room, we first start with finding files using the “find” command and then slowly navigates into the system. Further, we have a introduction on the topics of hashes. Moving ahead, we identify and crack the hashes. Along with that, we wet our feet in some base64 decoding followed by the encryption and decryption of some gpg files. Next, we learned how we can read the sql databases using the command line. Finally, we completed the room with a final challenge, which test our skills on all the above mentioned topics. On that note, i will bid a goodbye but remember always to “Hack the Planet”.




