In this walkthrough, we will be going through Crack the hash room by Tryhackme. After completing this room, we will know different hash types and techniques on how to crack them. This room is specifically designed to learn offline password cracking which mostly comes in handy in post-exploitation phase while pentesting. So, let’s get started.

Tools used:
- Offline – Haiti, Hash-identifier and Hashcat
- Online – Crackstation.net and Hashes.com
Task 1 – Level 1
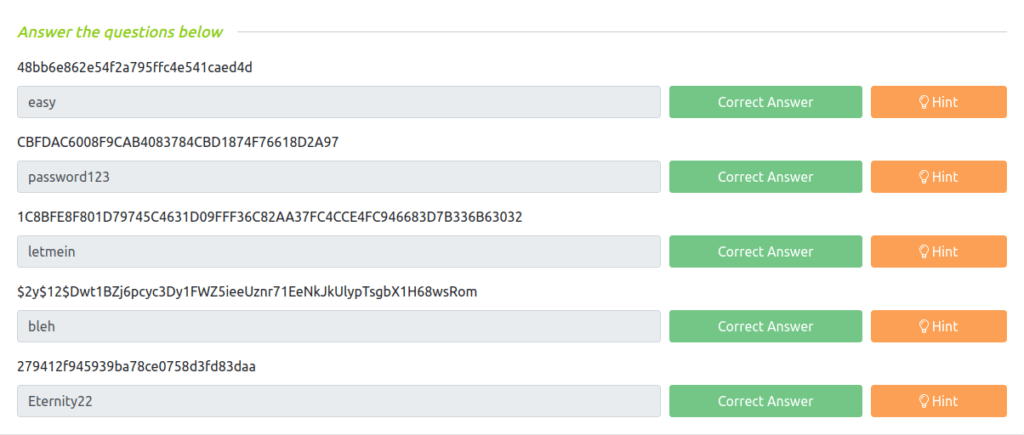
Question 1 – 48bb6e862e54f2a795ffc4e541caed4d
Using Haiti to identify the hash type. We got it confirmed, its an MD5 hash.
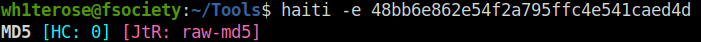
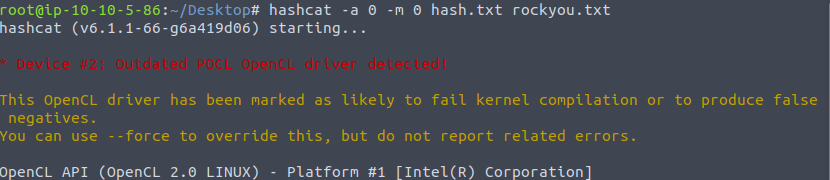
Now, we’ll be using Hashcat to crack the target hash. Hashcat use specific numbers for all the hash types out there. While cracking, we will us these numbers which can be easily grep out from the hashcat help to proceed with our attack. The attack mode here we are using is bruteforce attack, which is specified “-a” for attack mode and “0” to specify the bruteforce attack.
hashcat -a 0 -m 0 hash.txt rockyou.txt
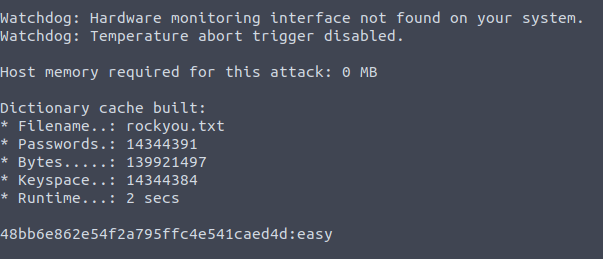
easy
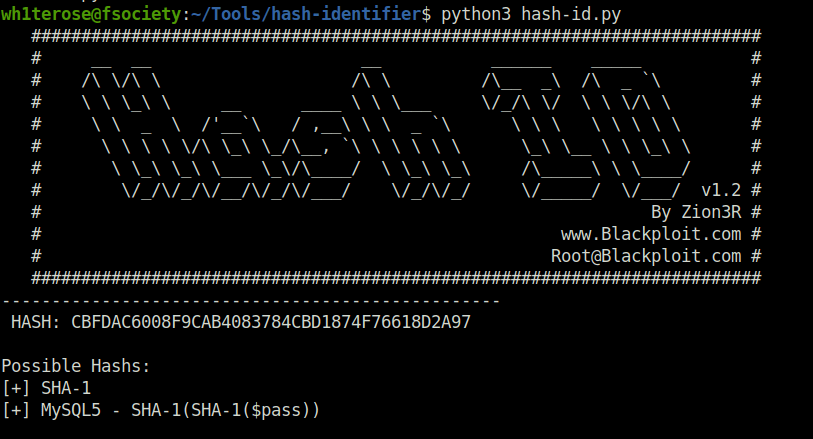
Question 2 – CBFDAC6008F9CAB4083784CBD1874F76618D2A97
Using Hash-identifier to identify the target hash. We got a potential result of SHA-1 hash.
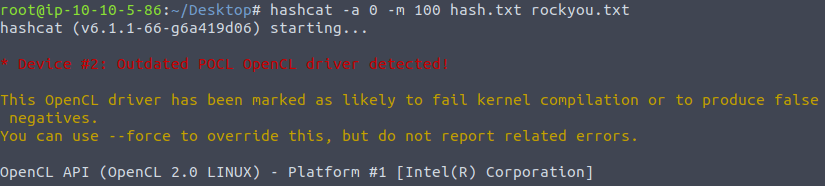
Moving ahead with our cracking using Hashcat. We first grab the hash target mode which is “100” from the hashcat documentation and then use rockyou wordlist to get the machine roll for the cracking.
hashcat -a 0 -m 100 hash.txt rockyou.txt
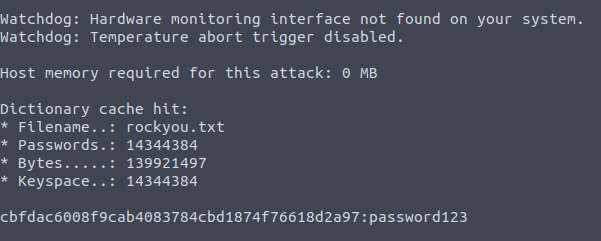
password123
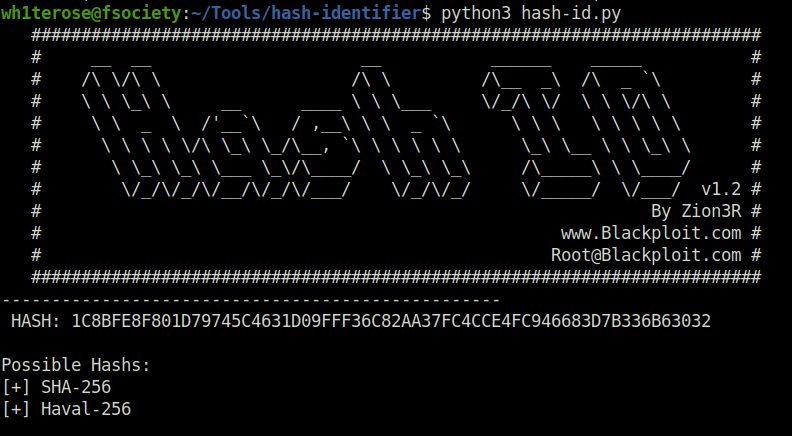
Question 3 – 1C8BFE8F801D79745C4631D09FFF36C82AA37FC4CCE4FC946683D7B336B63032
Using Hash-identifier to identify the target hash. We got a potential result of SHA-256 hash.
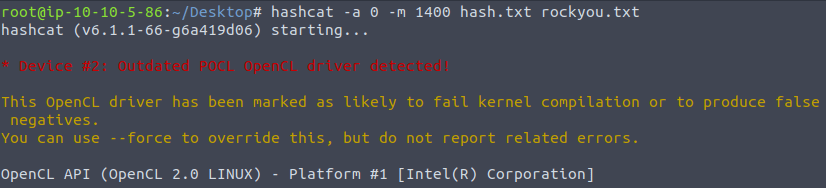
The attack mode for SHA-256 is “1400” as per the hashcat documentation. Firing hashcat on the target hash using the wordlist rockyou gives us the target hash within no time.
hashcat -a 0 -m 1400 hash.txt rockyou.txt
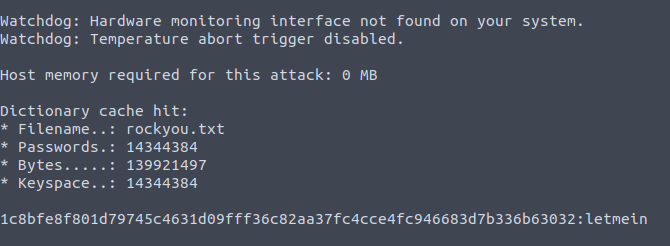
letmein
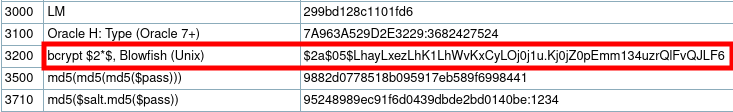
Question 4 – $2y$12$Dwt1BZj6pcyc3Dy1FWZ5ieeUznr71EeNkJkUlypTsgbX1H68wsRom
For this particular hash, I was unable to find any potential hash using Haiti or Hash-identifier. As per the hint provided hint, i tried to search the hash initials in the online hashcat example documentation found here. Try searching – “$2”, you will get the target hash for this task which will be “bcrypt” and its attack number “3200”.
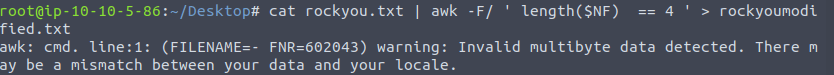
Next in order to crack this hash, we first have to modify our existing rockyou wordlist. We only need four alphabets password for this task. We can modify the rockyou wordlist as per requirement by following the command given below.
cat rockyou.txt | awk -F/ ' length($NF) == 4 ' > rockyoumodified.txt
Once we are done using our modification on your wordlist. We will start with our cracking using hashcat.
hashcat -a 0 -m 3200 hash.txt rockyoumodified.txt
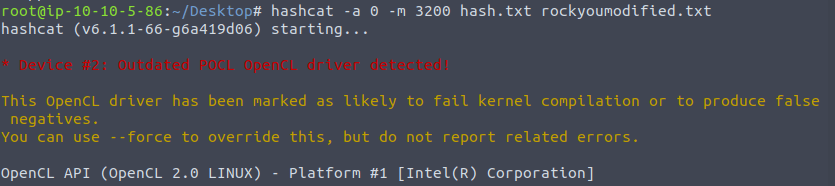
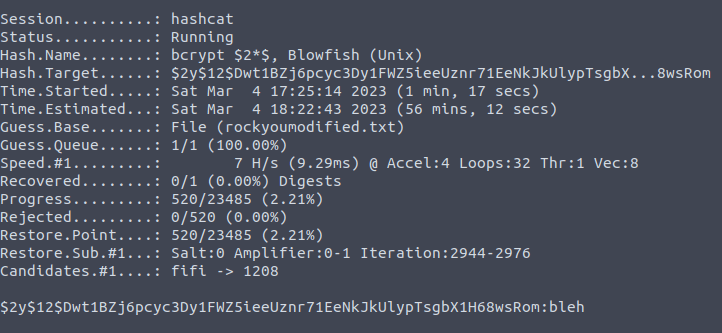
bleh
Question 5 – 279412f945939ba78ce0758d3fd83daa
For this hash, when i use Hash-identifier to identify it, the result shows the potential hash is MD5 and MD4.
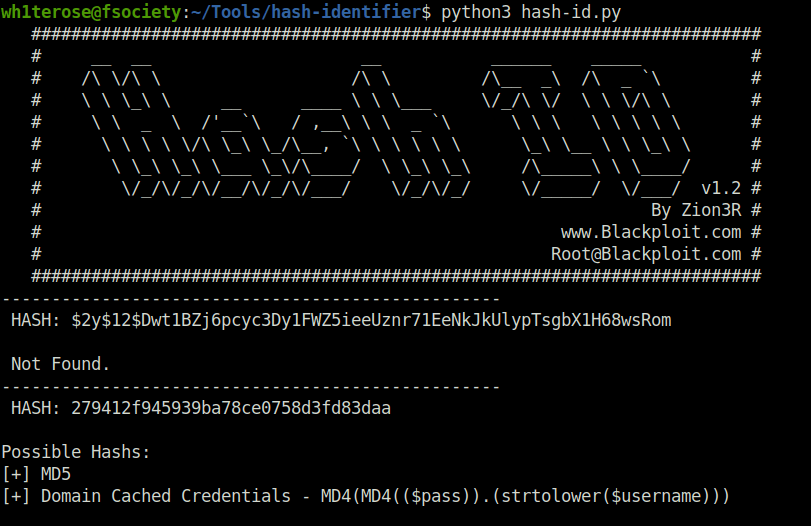
Further, when i tried to crack the hash using MD4 attack mode, it failed. Then, i tried Crackstation in order to crack the hash and it went through.
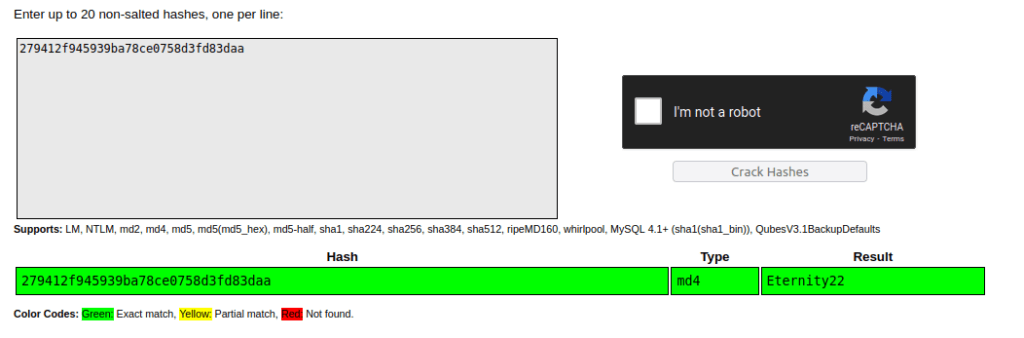
Eternity22
Task 2 – Level 2
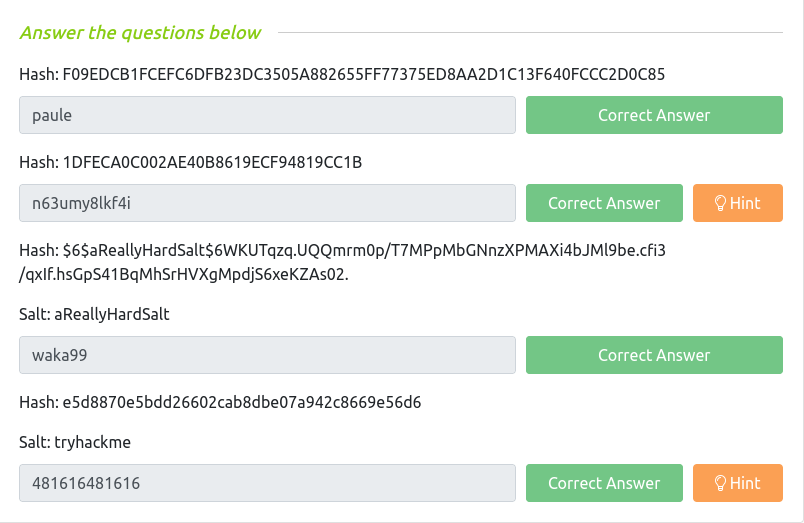
Question 1 – Hash: F09EDCB1FCEFC6DFB23DC3505A882655FF77375ED8AA2D1C13F640FCCC2D0C85
We will start with our usual drill with Hash-identifier, we got the hash type confirmed – SHA-256
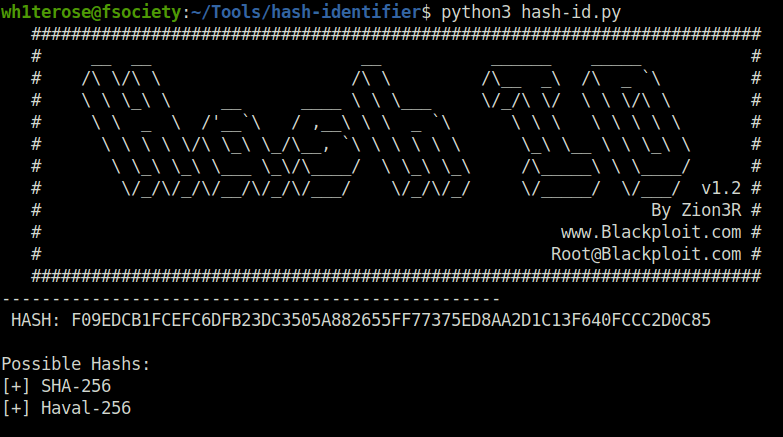
Next, i used hashcat documentation to identify the attack mode for SHA-256 and got “1400”.
hashcat -a 0 -m 1400 hash.txt rockyou.txt
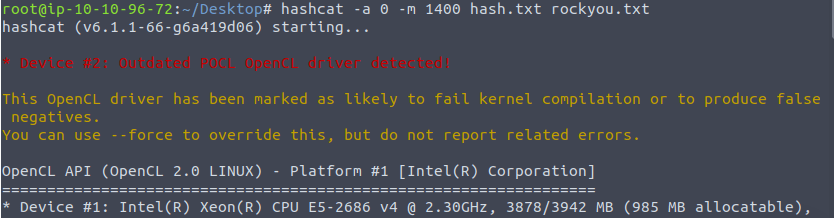
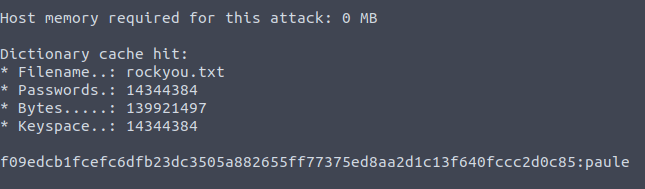
paule
Question 2 – Hash: 1DFECA0C002AE40B8619ECF94819CC1B
For this hash, i first used Hash-idenifier and got the confirmation that the potential hash type is MD5. However when tried to crack it using usual MD5 attack mode, it failed. Then, i tried MD4 but no luck. At last, i tried Crackstation again and i was able to crack it however the hash type which crackstation showed was NTLM. That was no way near the hashes which we found earlier.
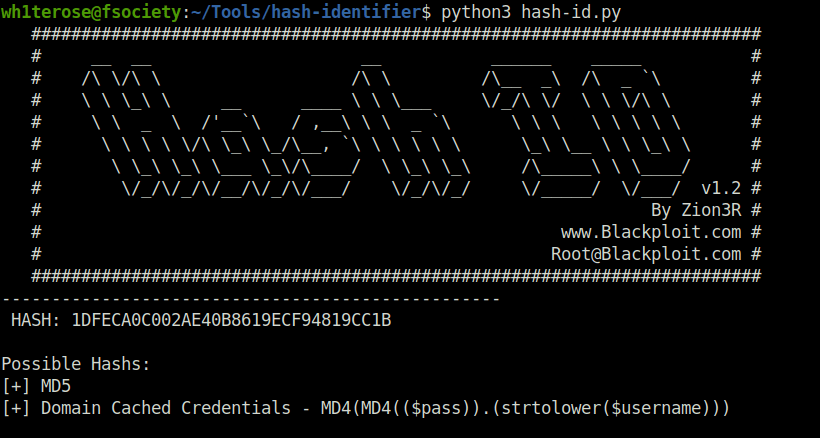
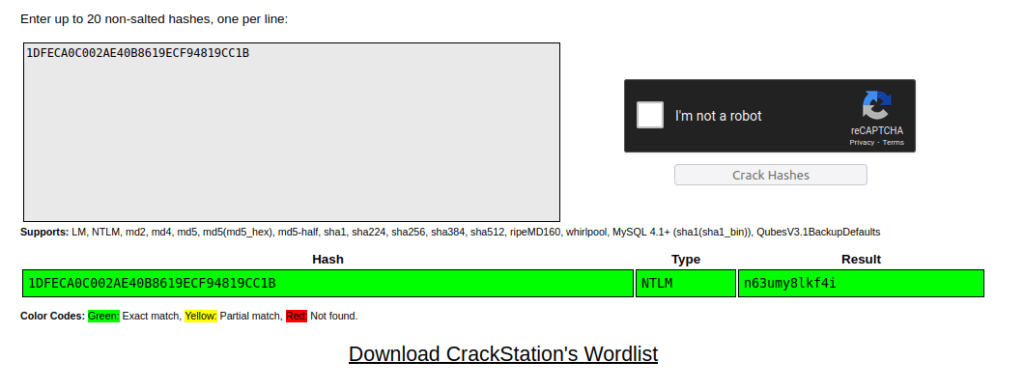
n63umy8lkf4i
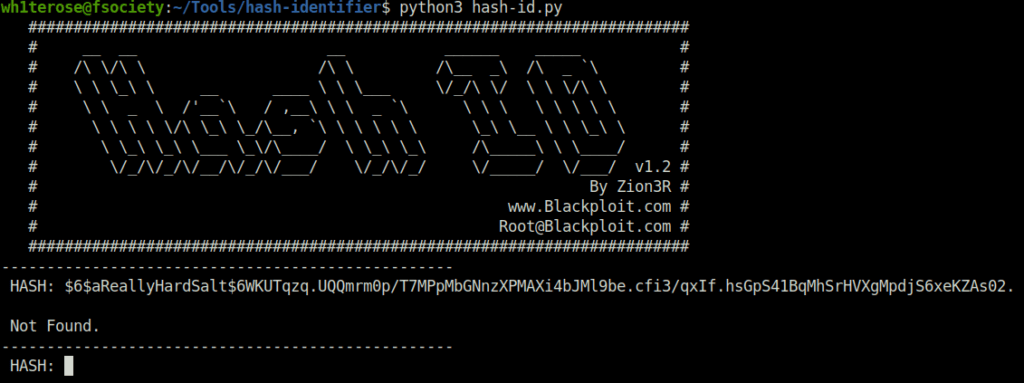
Question 3 – Hash: $6$aReallyHardSalt$6WKUTqzq.UQQmrm0p/T7MPpMbGNnzXPMAXi4bJMl9be.cfi3/qxIf.hsGpS41BqMhSrHVXgMpdjS6xeKZAs02.
Now this was one that boggles me a bit. I tried the usual route of Hash-identifier and Haiti but returned empty handed. Then i tried googling the initial of the hash and got the confirmation in a quora post that the hash type is “SHA512crypt“. I tried cracking it with hashcat but it was taking a long time and i honestly don’t had the patience to roll my eyes on a status screen. So, i tried one of the online decryption website, Hashes.com and got my hash cracked with a blink of an eye. For others, who want to try out the hashcat route, use the command given below.
hashcat -a 0 -m 1800 hash.txt rockyou.txt
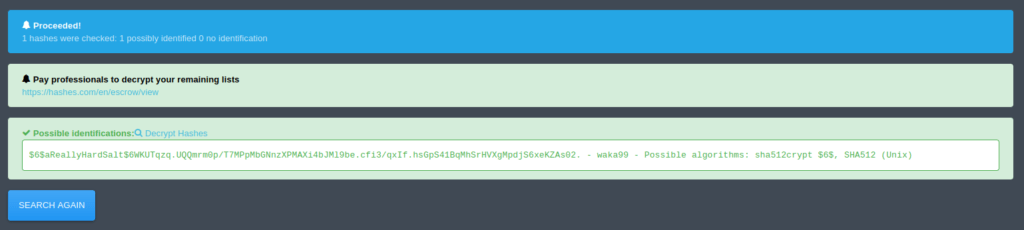
waka99
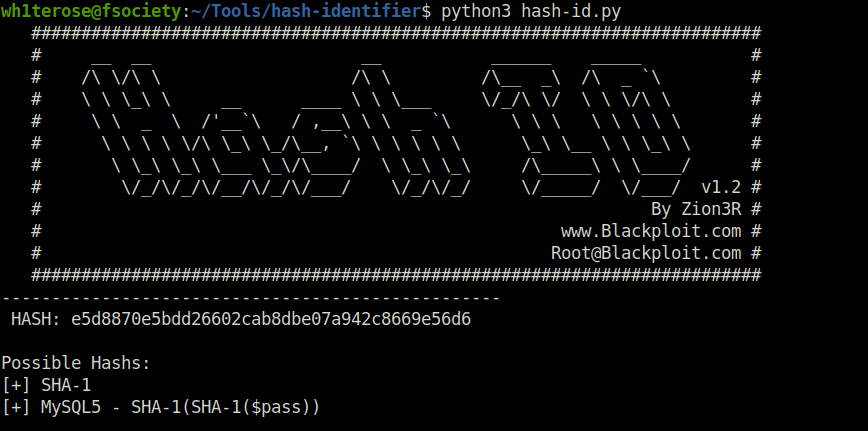
Question 4 – Hash: e5d8870e5bdd26602cab8dbe07a942c8669e56d6
Tried Hash-identifier on this one too. Got the hash confirmed “SHA-1”. This one was also taking too much time using hashcat. So, I tried Hashes.com and got my final hash cracked.
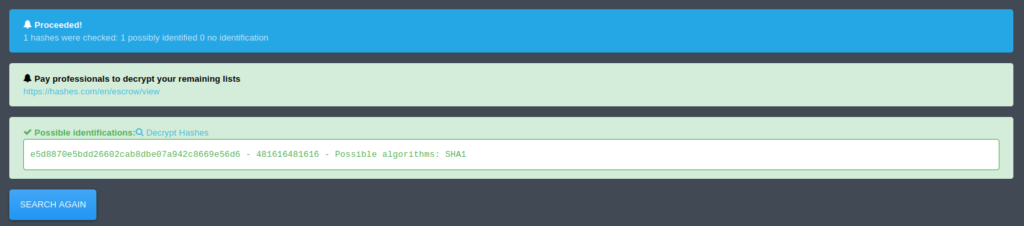
481616481616
Also Read: Tryhackme – Attacktive Directory
Conclusion:

In this room, we moved from identifying hashes using Hash-identifier and Haiti to cracking them using hashcat. Some of the hashes was a bit difficult to crack and the process was not too straight forward. We also tried alternate online options to crack some of the hashes. Cracking password is a vital step when we have a foothold in the target system. Weak passwords poses a bigger threat here as they are easily crack-able by mere bruteforce with hashcat. On that note, I’ll bid goodbye but remember to “Hack the planet” in my absence.




