In this walk through, we will be going through the Snort Challenge – Live Attacks room from Tryhackme. This room will put our snort skills into practice by defending against live attacks. On that note, let’s get started.
Table of Contents
Task 1 – Introduction
Task 2 – Scenario 1 | Brute-Force
Question 1 – Stop the attack and get the flag (which will appear on your Desktop)
sudo gedit /etc/snort/rules/local.rules
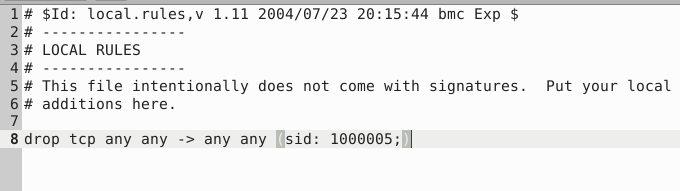
sudo snort -c /etc/snort/snort.conf -q -Q --daq afpacket -i eth0:eth1 -A full
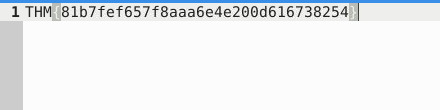
THM{81b7fef657f8aaa6e4e200d616738254}Question 2 – What is the name of the service under attack?
sudo snort -c /etc/snort/snort.conf -q -Q --daq afpacket -i eth0:eth1 -A console
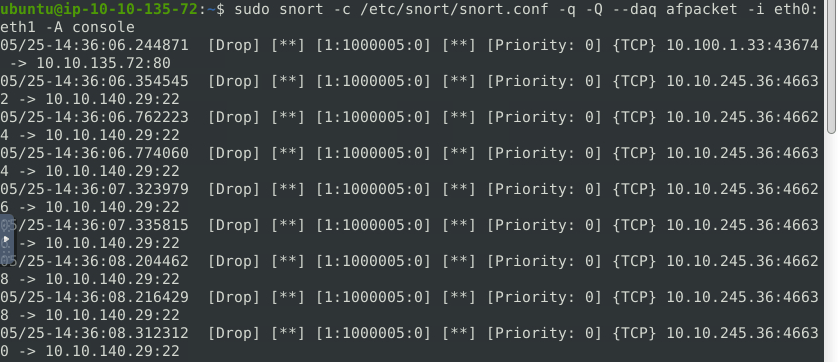
SSHQuestion 3 – What is the used protocol/port in the attack?
TCP/22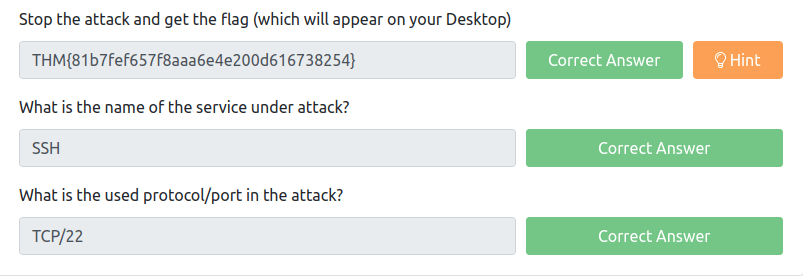
Task 3 – Scenario 2 | Reverse-Shell
Question 1 – Stop the attack and get the flag (which will appear on your Desktop)
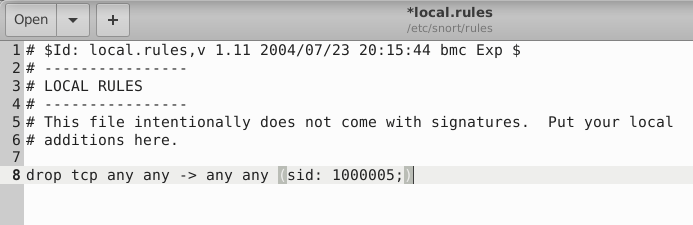
sudo nano /etc/snort/rules/local.rules drop tcp any any -> any any (sid: 1000005;)
sudo snort -c /etc/snort/snort.conf -q -Q --daq afpacket -i eth0:eth1 -A full
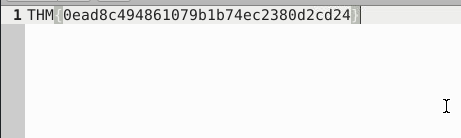
THM{0ead8c494861079b1b74ec2380d2cd24}Question 2 – What is the used protocol/port in the attack?
sudo snort -c /etc/snort/snort.conf -q -Q --daq afpacket -i eth0:eth1 -A console
TCP/4444Question 3 – Which tool is highly associated with this specific port number?
Metasploit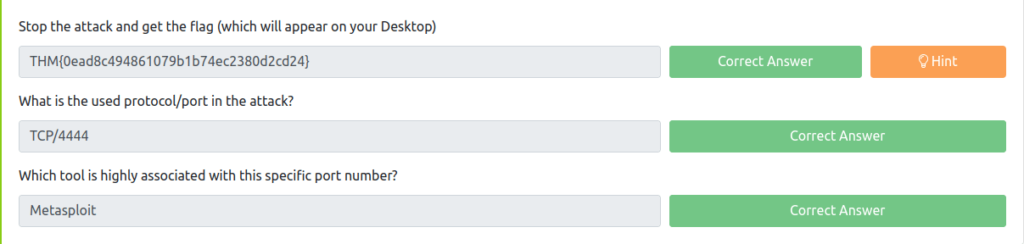
Also Read: Tryhackme – Simple CTF
So that was “Snort Challenge – Live Attacks” for you. In this room, we have practiced and tested our skills with snort by defending against the live attacks based on common scenarios like Bruteforce and Reverse Shell uploads. On that note, i will take your leave but stay tuned for the next one and till then, remember to “Hack the planet”.




