In this walk through, we will be going through the Secure Passwords vulnerability section from Webgoat Labs. We will be exploring password strengths and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

- In this challenge, we will test the strength of a password using the given application. The application takes a password as an input and checks for its length, estimated guesses to crack and the estimated cracking time. At last, it provides with a score out of 4 and highlight the strong password in green.
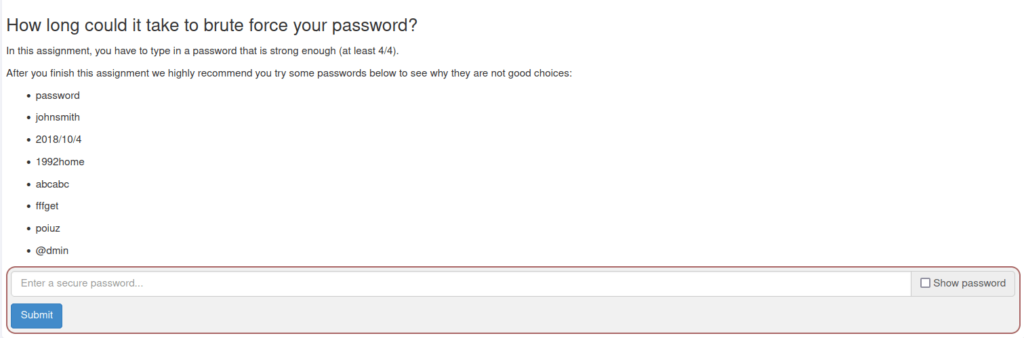
- I entered the below password and it checks all marks and got a 4/4 result.
password: @JesusismyN3ighbour&heisaHax0r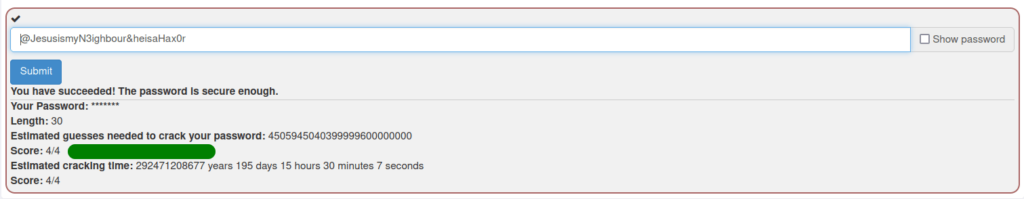
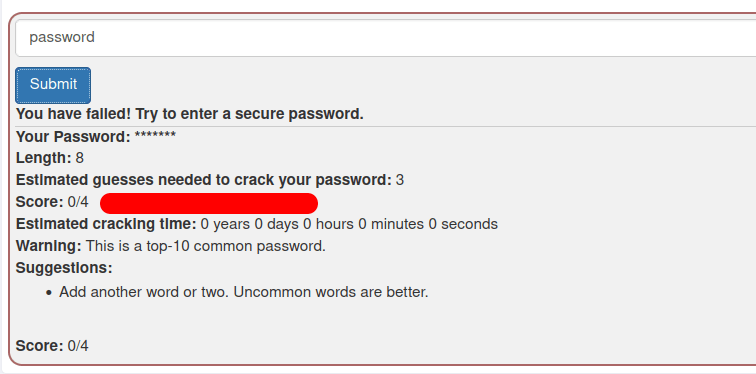
- A weak password like before will definitely failed the password. The applications also provided suggestions on how we can improve the password strength.
Also Read: Webgoat – Missing Function Level Access Control
Conclusion:

So, we finally completed the Webgoat Secure Passwords Vulnerability section. Next, we can mitigate these types of attacks by implementing a strong password policy and avoiding default or commonly used password. Along with that, a lockout mechanism on the login panel will be beneficial in case of bruteforce attacks. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




