In this walk through, we will be going through the Crypto Basics vulnerability section from Webgoat Labs. We will be exploring and exploiting Cryptographic related vulnerabilities and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Crypto Basics
1. Base64 Encoding
- In this challenge we have to decode a base64 string in order to reveal the username and password combo.
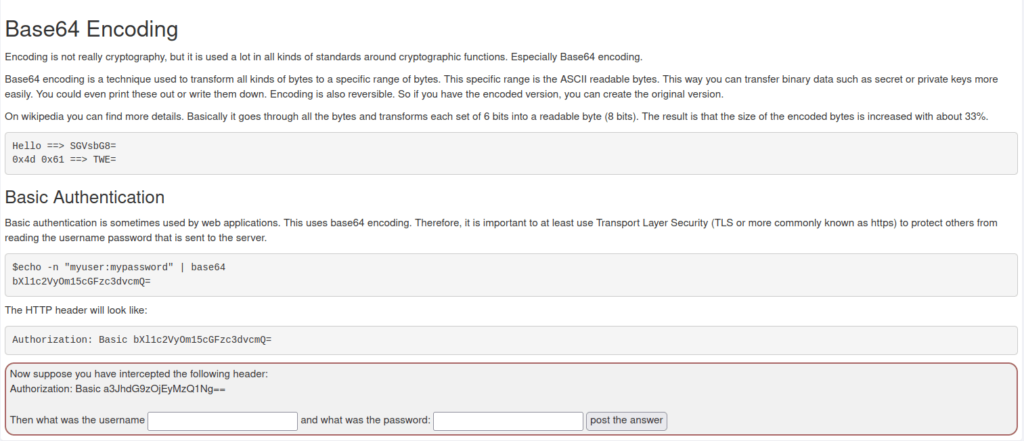
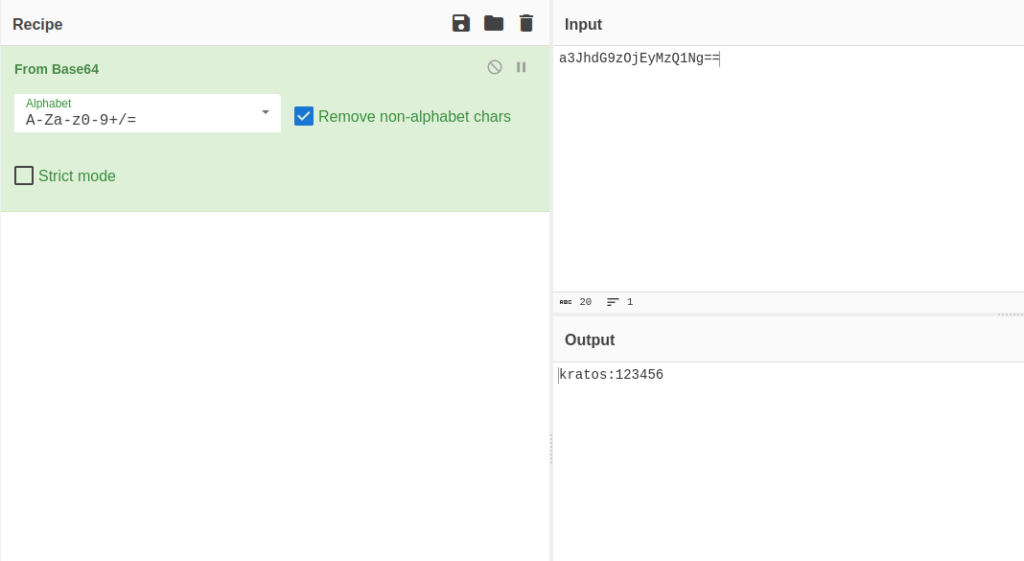
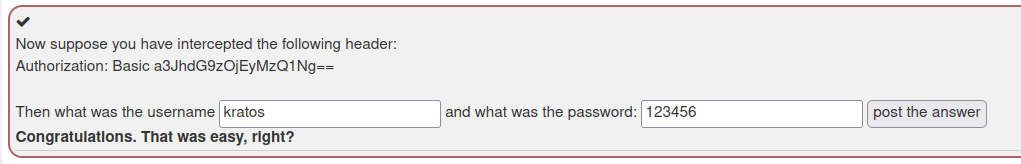
- I used cyberchef to decode the string and got credentials – kratos:123456
2. Other Encoding
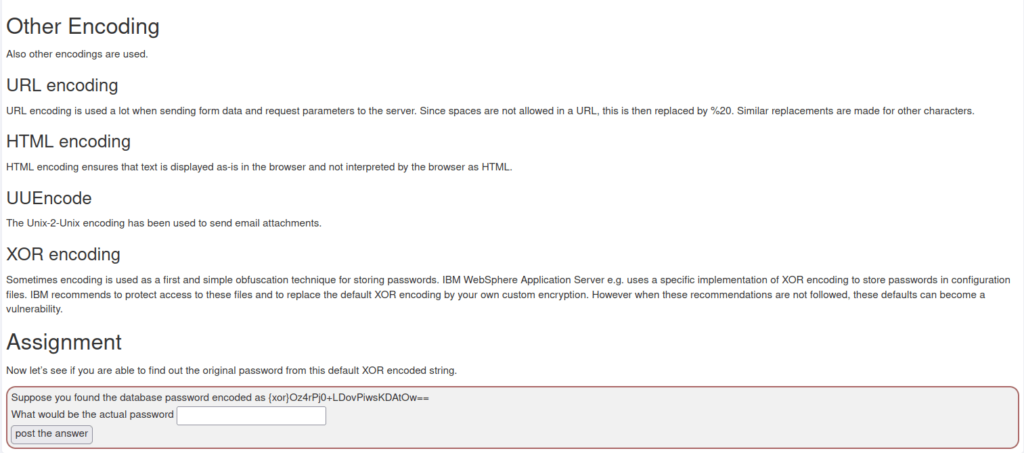
- In this challenge we have to find out the original password from the given default XOR encoded string.
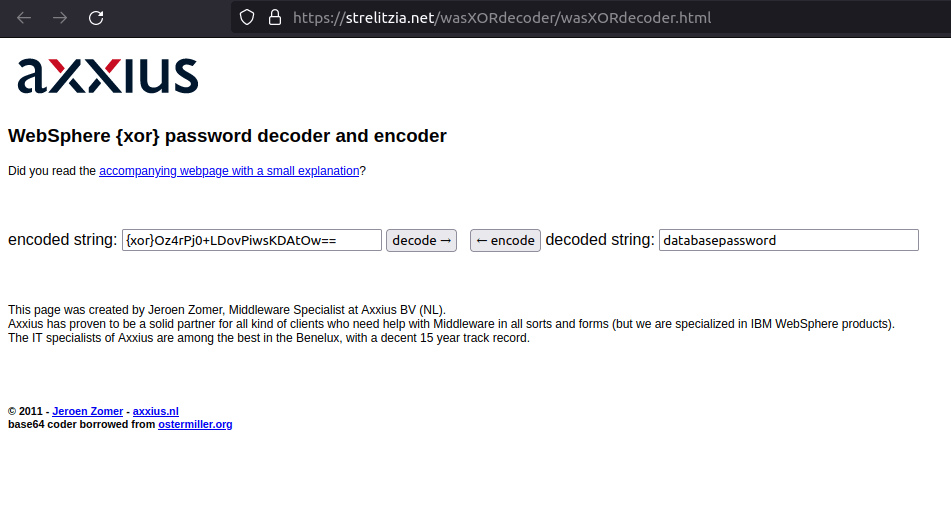
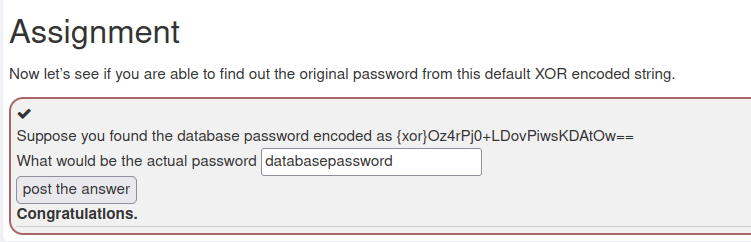
- I used the below WebSphere xor decoder to reveal the DB password.
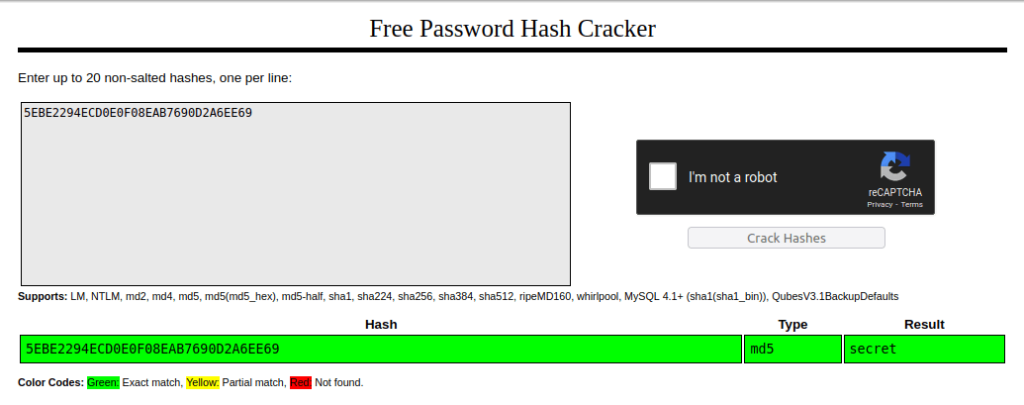
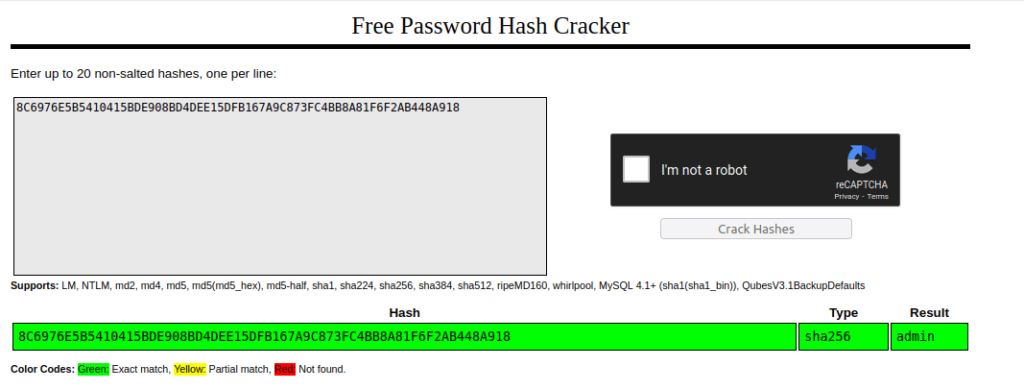
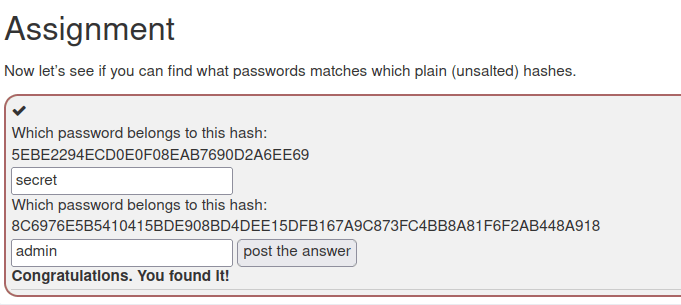
3. Plain Hashing
- In this challenge we have to decrypt given password hashes.
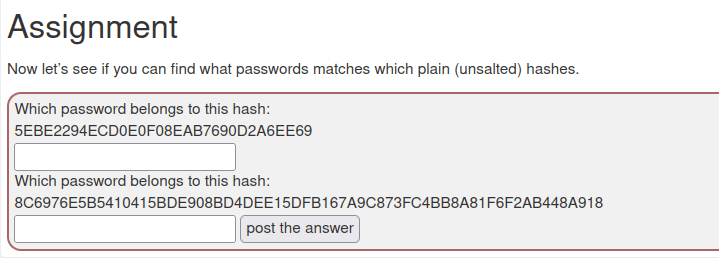
- I used crackstation to reveal the password of the given hashes.
4. Symmetric and Asymmetric encryption
5. Cryptographic signature
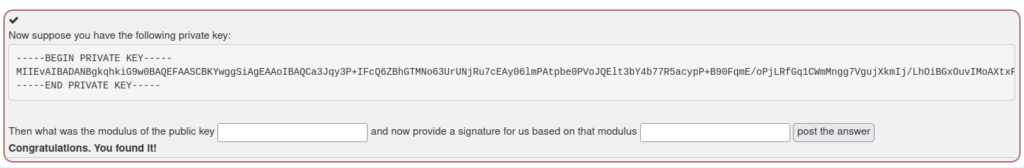
- In this challenge, we have to determine the modulus of the RSA key as a hex string, and calculate a signature for that hex string using the key.
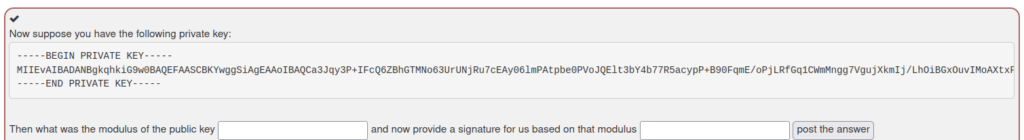
- I saved the given key to a file in my local machine naming private.key
- Next, i derived the public key from the private key. Post that, calculated the modulus with our public key. Moving on, used the modulus to sign the private key and get a signed.key file and at last encoded it with base64.
$ openssl rsa -in private.key -pubout > test.pub writing RSA key $ cat test.pub -----BEGIN PUBLIC KEY----- MIIBITANBgkqhkiG9w0BAQEFAAOCAQ4AMIIBCQKCAQEAmtyastz/iBXEOmQYRkzD aOt1K1DY0bu3BAMtOpZjwLaW3tD1aCUBJbd22OG++0eWnMqT/gfdBaphP6D4y0Xx qtQlpjJ4IO1YLo15JiI/y4TogRsTrryDKAF7cT9eqw29UbsRU6BOPNb7PmMWTgBe qfaRbXKD5J+Ew2sv2nIaE/4E3/86aELQhm8J2QpAnz0f+Wp+F1qRDClKbybDQzee bopfxRk3+KLvQGsxCuYkOuW3xnIUWeqhAQXl4OxvQs0v81kvYBqoe/CrSj3fIlaP wDHNFyA2U9tlNQleoSZMkbqKXYBt8xnOY7I3JO4aIUH7EfhYs75sOtRVnjGJjvgc rwICAQE= -----END PUBLIC KEY----- $ openssl rsa -in test.pub -pubin -modulus -noout Modulus=9ADC9AB2DCFF8815C43A6418464CC368EB752B50D8D1BBB704032D3A9663C0B696DED0F568250125B776D8E1BEFB47969CCA93FE07DD05AA613FA0F8CB45F1AAD425A6327820ED582E8D7926223FCB84E8811B13AEBC8328017B713F5EAB0DBD51BB1153A04E3CD6FB3E63164E005EA9F6916D7283E49F84C36B2FDA721A13FE04DFFF3A6842D0866F09D90A409F3D1FF96A7E175A910C294A6F26C343379E6E8A5FC51937F8A2EF406B310AE6243AE5B7C6721459EAA10105E5E0EC6F42CD2FF3592F601AA87BF0AB4A3DDF22568FC031CD17203653DB6535095EA1264C91BA8A5D806DF319CE63B23724EE1A2141FB11F858B3BE6C3AD4559E31898EF81CAF $ echo -n "9ADC9AB2DCFF8815C43A6418464CC368EB752B50D8D1BBB704032D3A9663C0B696DED0F568250125B776D8E1BEFB47969CCA93FE07DD05AA613FA0F8CB45F1AAD425A6327820ED582E8D7926223FCB84E8811B13AEBC8328017B713F5EAB0DBD51BB1153A04E3CD6FB3E63164E005EA9F6916D7283E49F84C36B2FDA721A13FE04DFFF3A6842D0866F09D90A409F3D1FF96A7E175A910C294A6F26C343379E6E8A5FC51937F8A2EF406B310AE6243AE5B7C6721459EAA10105E5E0EC6F42CD2FF3592F601AA87BF0AB4A3DDF22568FC031CD17203653DB6535095EA1264C91BA8A5D806DF319CE63B23724EE1A2141FB11F858B3BE6C3AD4559E31898EF81CAF" | openssl dgst -sign private.key -sha256 -out signed.key $ openssl enc -base64 -in signed.key -out final.key $ cat final.key kuUlJw0GgwqHbgpZkfWmeonIh0ESrS5c65peaNUzIwfv1Dl1s4ggKDcbvvakFypU Mzse4t2iw1/thdWwBk9NOX7nBuSSsWZ/Hzz16PMAaLI9JuB1wwHnpyytWXoyeqhz xOhXgj16BaG5HT9F918nXd36hkKEadYKErtMarNbRVPbtk87Bye3U/7DwcLUS0oK C+GZf8ls9k3lL0DyjnQkan8eBMhfqwctgjj+kJ8z9A+jBty8Rd7L6KchhTcVuRhl fszPO58fdjMSocLseNs097wh6cNr2A2NlaU+CwYUaBiuUY/l6O8ji0aA8OISQpCG y5O7xDD/cFY1liVmJ5BGsQ==
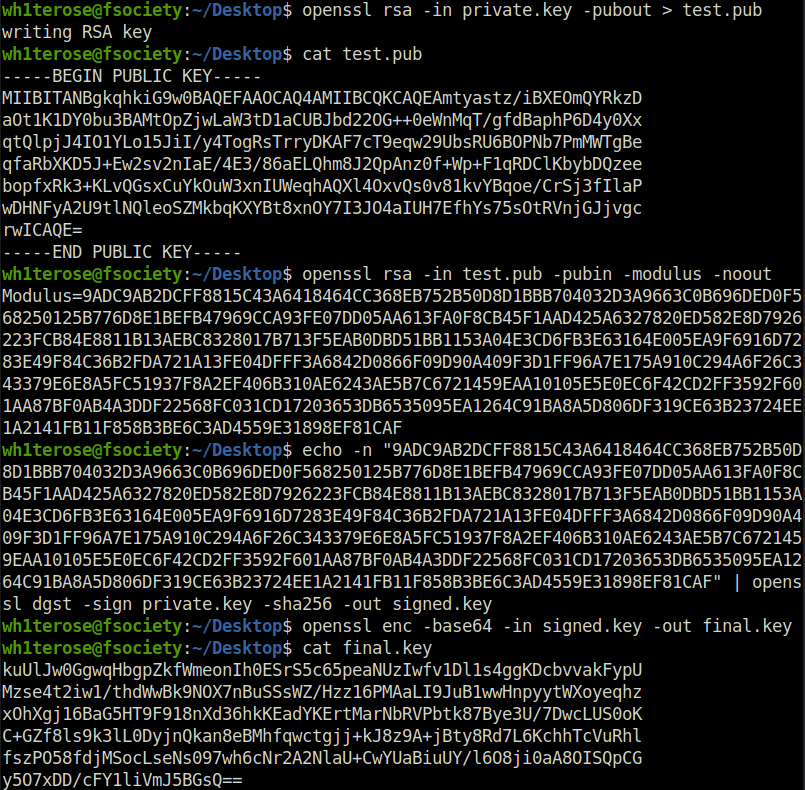
Modulus: 9ADC9AB2DCFF8815C43A6418464CC368EB752B50D8D1BBB704032D3A9663C0B696DED0F568250125B776D8E1BEFB47969CCA93FE07DD05AA613FA0F8CB45F1AAD425A6327820ED582E8D7926223FCB84E8811B13AEBC8328017B713F5EAB0DBD51BB1153A04E3CD6FB3E63164E005EA9F6916D7283E49F84C36B2FDA721A13FE04DFFF3A6842D0866F09D90A409F3D1FF96A7E175A910C294A6F26C343379E6E8A5FC51937F8A2EF406B310AE6243AE5B7C6721459EAA10105E5E0EC6F42CD2FF3592F601AA87BF0AB4A3DDF22568FC031CD17203653DB6535095EA1264C91BA8A5D806DF319CE63B23724EE1A2141FB11F858B3BE6C3AD4559E31898EF81CAF Signature: kuUlJw0GgwqHbgpZkfWmeonIh0ESrS5c65peaNUzIwfv1Dl1s4ggKDcbvvakFypU Mzse4t2iw1/thdWwBk9NOX7nBuSSsWZ/Hzz16PMAaLI9JuB1wwHnpyytWXoyeqhz xOhXgj16BaG5HT9F918nXd36hkKEadYKErtMarNbRVPbtk87Bye3U/7DwcLUS0oK C+GZf8ls9k3lL0DyjnQkan8eBMhfqwctgjj+kJ8z9A+jBty8Rd7L6KchhTcVuRhl fszPO58fdjMSocLseNs097wh6cNr2A2NlaU+CwYUaBiuUY/l6O8ji0aA8OISQpCG y5O7xDD/cFY1liVmJ5BGsQ==
6. Keystores
7. Revealing Certs
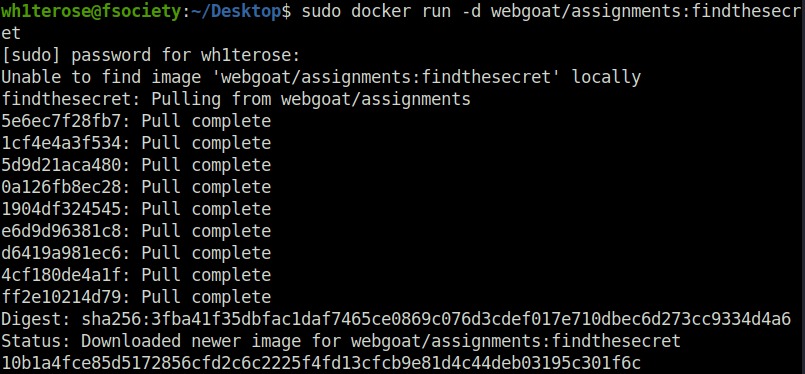
- In this challenge we have to find the secret which has been accidentally left inside a docker image. We first initialize the docker image by below command.
$ sudo docker run -d webgoat/assignments:findthesecret [sudo] password for wh1terose: Unable to find image 'webgoat/assignments:findthesecret' locally findthesecret: Pulling from webgoat/assignments 5e6ec7f28fb7: Pull complete 1cf4e4a3f534: Pull complete 5d9d21aca480: Pull complete 0a126fb8ec28: Pull complete 1904df324545: Pull complete e6d9d96381c8: Pull complete d6419a981ec6: Pull complete 4cf180de4a1f: Pull complete ff2e10214d79: Pull complete Digest: sha256:3fba41f35dbfac1daf7465ce0869c076d3cdef017e710dbec6d273cc9334d4a6 Status: Downloaded newer image for webgoat/assignments:findthesecret 10b1a4fce85d5172856cfd2c6c2225f4fd13cfcb9e81d4c44deb03195c301f6c
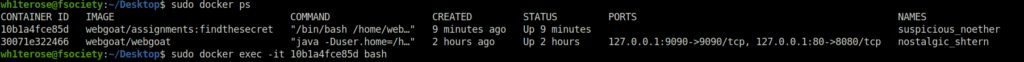
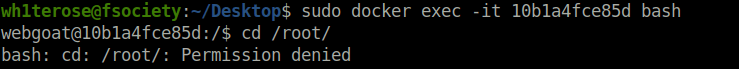
- Next, logged into the image but was unable to locate to /root. Tried to escalate it with “su -“ however no luck.
$ sudo docker ps CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES 10b1a4fce85d webgoat/assignments:findthesecret "/bin/bash /home/web…" 9 minutes ago Up 9 minutes suspicious_noether 30071e322466 webgoat/webgoat "java -Duser.home=/h…" 2 hours ago Up 2 hours 127.0.0.1:9090->9090/tcp, 127.0.0.1:80->8080/tcp nostalgic_shtern $ sudo docker exec -it 10b1a4fce85d bash $ cd /root/ bash: cd: /root/: Permission denied $ su - Password: su: Authentication failure
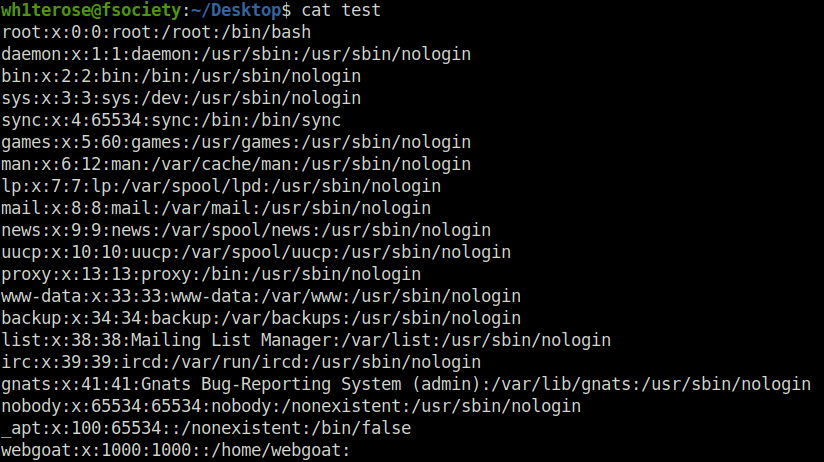
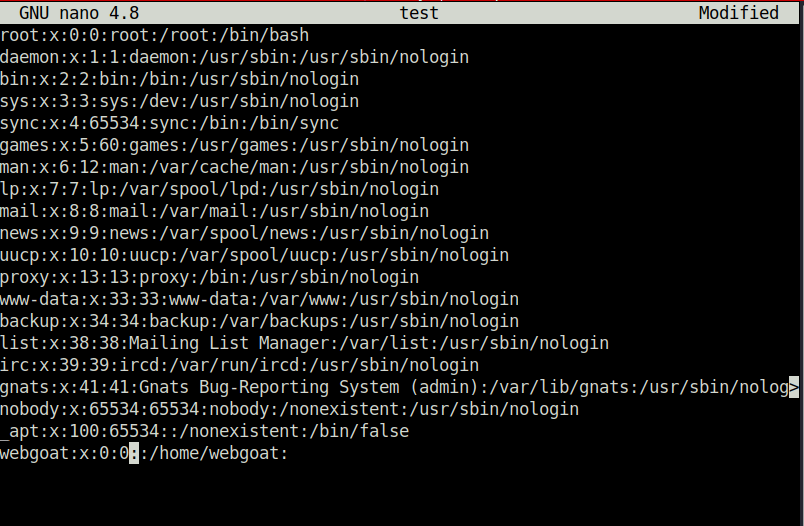
- Next, i copied the /etc/passwd file to my local system and changed the webgoat UID and GID to 0 in it.
$ sudo docker cp 10b1a4fce85d:/etc/passwd test Successfully copied 2.56kB to /home/wh1terose/Desktop/test wh1terose@fsociety:~/Desktop$ cat test root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/bin/false webgoat:x:1000:1000::/home/webgoat:
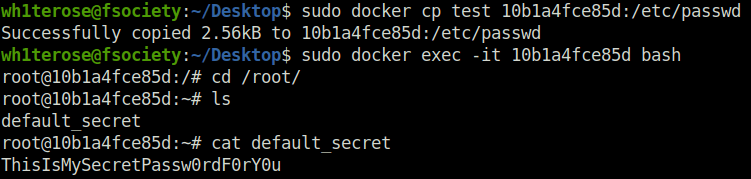
- Copy the file back to the docker image which makes us root. At last, we found the password in the default_secret file and then used the base64 string to reveal the secret.
$ sudo docker cp test 10b1a4fce85d:/etc/passwd Successfully copied 2.56kB to 10b1a4fce85d:/etc/passwd $ sudo docker exec -it 10b1a4fce85d bash root@10b1a4fce85d:/# cd /root/ root@10b1a4fce85d:~# ls default_secret root@10b1a4fce85d:~# cat default_secret ThisIsMySecretPassw0rdF0rY0u root@10b1a4fce85d:~# echo "U2FsdGVkX199jgh5oANElFdtCxIEvdEvciLi+v+5loE+VCuy6Ii0b+5byb5DXp32RPmT02Ek1pf55ctQN+DHbwCPiVRfFQamDmbHBUpD7as=" | openssl enc -aes-256-cbc -d -a -kfile default_secret Leaving passwords in docker images is not so secure
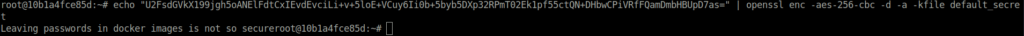
Unencrypted message: Leaving passwords in docker images is not so secure File name: default_secret
Also Read: Webgoat – Cross Site Scripting
Conclusion:

So, we finally completed the Webgoat Crypto Basics Vulnerability section. Next, we can mitigate these types of attacks by using strong encryption algorithm and properly managing encryption keys. Along with that, there should be a use of valid random numbers for session keys and other cryptographic material, the libraries must be up to date and parties should be authenticated properly. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




